ZachXBT: Infiltrate before attacking, uncovering the unknown behind North Korean crypto hackers
Author: ZachXBT, Crypto Detective;
Translation: Jinse Finance xiaozou
Recently, a team sought my help because someone had stolen $1.3 million from their vault using malicious code.
What this team did not know was that they had hired several North Korean IT personnel with fake identities as developers.
I then discovered that there have been at least 25 active crypto projects associated with these developers since June 2024.


The money laundering route of the incident is as follows:
1) Transfer $1.3 million to the theft address
2) Bridge $1.3 million from Solana to Ethereum via deBridge
3) Deposit 50.2 ETH into Tornado
4) Transfer 16.5 ETH to two exchanges
The theft address is:
6USfQ9BX33LNvuR44TXr8XKzyEgervPcF4QtZZfWMnet

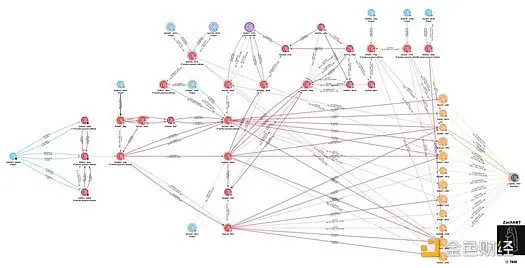
With the help of multiple payment addresses from 21 developers, I was able to map out a recent cluster of payments totaling approximately $375,000 over the past month.
0 xb721adfc3d9fe01e9b3332183665a503447b1d35
In the past week, you may have also seen that I asked these projects to contact me directly.

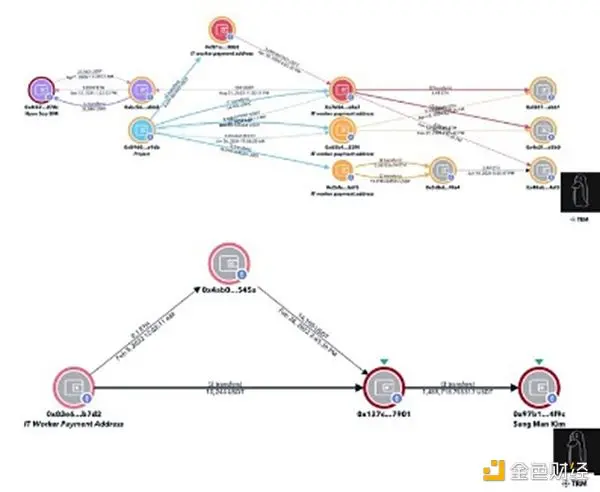
Previously, $5.5 million flowed into a forex deposit address, which included funds received by North Korean IT personnel from July 2023 to 2024, and this address is related to OFAC-sanctioned individual Sim Hyon Sop.
0x8f0212b1a77af1573c6ccdd8775ac3fd09acf014


Some interesting findings during the investigation:
Russian telecom IPs were used by developers from the United States and Malaysia.
In their development records, they accidentally leaked other identities they had on their notepad.
The payment addresses for development involved Sang Man Kim and Sim Hyon Sop, who are on the OFAC sanctions list.
Some developers were arranged by recruitment companies.
Multiple projects had more than three mutually recommended IT personnel.

Many experienced teams have hired these developers, so it is unfair to consider them the culprits.
Some indicators that teams can focus on in the future include:
1) Their mutually recommended roles
2) Impressive resumes/GitHub activity, although sometimes they may falsify work experience.
3) Generally appearing willing to accept KYC but submitting fake IDs, hoping the team won't investigate further.
4) Asking specific questions about their claimed places of origin.
5) A developer was fired, but several new job-seeking accounts appeared immediately.
6) They may seem like excellent developers at first glance, but often perform poorly in work.
7) Checking logs
8) Preferring to use popular NFT pfps
9) Asian accents
In case you are the type who blames everything on North Korea and calls it a grand conspiracy.
In any case, this research proves:
In Asia, an entity can engage in more than 25 projects simultaneously using fake identities, earning between $300,000 to $500,000 per month.
Follow-up:
Shortly after this article was published, another project discovered that they had hired a North Korean IT personnel listed in my report (Naoki Murano), and the project manager shared my article in their chat.

The result was that within two minutes, Naoki left the chat and deleted his Github.































