Spend a little to catch a big fish: Unveiling the 1155 WBTC fishing incident
Authors: Liz, Zero, Keywolf, Slow Mist Technology
Background
On May 3, according to monitoring by the Web3 anti-fraud platform Scam Sniffer, a whale fell victim to a phishing attack involving addresses with the same starting and ending digits, resulting in the loss of 1155 WBTC, worth approximately 70 million USD. Although this phishing method has been around for a long time, the scale of the losses in this incident is still shocking. This article will analyze the key points of the same starting and ending digit address phishing attack, the flow of funds, hacker characteristics, and provide recommendations to prevent such phishing attacks.

(https://twitter.com/realScamSniffer/status/1786374327740543464)
Key Points of the Attack
Victim's address:
0x1E227979f0b5BC691a70DEAed2e0F39a6F538FD5
Victim's target transfer address:
0xd9A1b0B1e1aE382DbDc898Ea68012FfcB2853a91
Phishing address:
0xd9A1C3788D81257612E2581A6ea0aDa244853a91
1. Collision to generate phishing addresses: The hacker pre-generates a large number of phishing addresses in batches, and after deploying the batch program, they initiate phishing attacks on target transfer addresses based on on-chain user dynamics. In this incident, the hacker used addresses that matched the first 4 digits and the last 6 digits (after removing 0x) of the victim's target transfer address.
2. Follow-up transaction: After the user makes a transfer, the hacker immediately follows up with a transaction using the generated phishing address (approximately 3 minutes later) (the phishing address sent 0 ETH to the user's address), causing the phishing address to appear in the user's transaction history.

(https://etherscan.io/txs?a=0x1E227979f0b5BC691a70DEAed2e0F39a6F538FD5\&p=2)
3. Baiting the user: Since users are accustomed to copying recent transfer information from their wallet history, they did not carefully check whether the copied address was correct after seeing this follow-up phishing transaction, resulting in the accidental transfer of 1155 WBTC to the phishing address!
MistTrack Analysis
Using the on-chain tracking tool MistTrack, it was found that the hacker had exchanged 1155 WBTC for 22955 ETH and transferred it to the following 10 addresses.

On May 7, the hacker began transferring ETH from these 10 addresses, with a funding transfer pattern that generally left no more than 100 ETH in the current address, then roughly averaged the remaining funds before transferring to the next layer of addresses. Currently, these funds have not been exchanged for other cryptocurrencies or transferred to platforms. The following image shows the fund transfer situation on 0x32ea020a7bb80c5892df94c6e491e8914cce2641; you can view a high-definition image by opening the link in your browser:

(https://misttrack.io/s/1cJlL)
Next, we used MistTrack to query the initial phishing address in this incident, 0xd9A1C3788D81257612E2581A6ea0aDa244853a91, and found that the transaction fee source for this address was 0xdcddc9287e59b5df08d17148a078bd181313eacc.

(https://dashboard.misttrack.io/address/WBTC-ERC20/0xd9A1C3788D81257612E2581A6ea0aDa244853a91)
Following up on this fee address, we can see that between April 19 and May 3, this address initiated over 20,000 small transactions, distributing small amounts of ETH to different addresses for phishing purposes.

(https://etherscan.io/address/0xdcddc9287e59b5df08d17148a078bd181313eacc)
From the above image, it can be seen that the hacker adopted a wide-net approach, so there are definitely more than one victim. Through large-scale scanning, we also found other related phishing incidents; here are some examples:

Taking the phishing address from the second incident in the above image, 0xbba8a3cc45c6b28d823ca6e6422fbae656d103a6, as an example, we traced the fee addresses upward and found that these addresses overlapped with the fee source address of the 1155 WBTC phishing incident, indicating they are likely from the same hacker.

By analyzing the hacker's transfer of other profit funds (from the end of March to now), we also summarized another money laundering characteristic of the hacker: converting funds on the ETH chain into Monero or cross-chain to Tron and then transferring to suspected OTC addresses. Therefore, there is a possibility that the hacker will use the same method to transfer the profits from the 1155 WBTC phishing incident.
Hacker Characteristics
Based on Slow Mist's threat intelligence network, we discovered suspected hacker mobile base station IPs located in Hong Kong (excluding the possibility of VPN):
- 182.xxx.xxx.228
- 182.xxx.xx.18
- 182.xxx.xx.51
- 182.xxx.xxx.64
- 182.xxx.xx.154
- 182.xxx.xxx.199
- 182.xxx.xx.42
- 182.xxx.xx.68
- 182.xxx.xxx.66
- 182.xxx.xxx.207
It is worth noting that even after stealing 1155 WBTC, the hacker does not seem to have any intention of stopping.
Following up on the previously collected three phishing address parent addresses (used to provide fees for numerous phishing addresses), their common characteristic is that the amount of the last transaction is significantly larger than previous ones, indicating the hacker's operation of stopping the current address and transferring funds to new phishing address parent addresses. Currently, the three newly activated addresses are still making high-frequency transfers.

(https://etherscan.io/address/0xa84aa841e2a9bdc06c71438c46b941dc29517312)

In subsequent large-scale scans, we also discovered two deactivated phishing address parent addresses, and tracing them revealed a connection to this hacker, which will not be elaborated here.
- 0xa5cef461646012abd0981a19d62661838e62cf27
- 0x2bb7848Cf4193a264EA134c66bEC99A157985Fb8
At this point, we also raised the question of where the hacker's funds on the ETH chain came from. After tracking and analyzing by the Slow Mist security team, we found that the hacker initially implemented the same starting and ending digit address phishing attack on Tron, profiting before targeting ETH chain users, transferring the profits from Tron to ETH chain to begin phishing. The following image shows an example of the hacker's phishing on Tron:

(https://tronscan.org/#/address/TY3QQP24RCHgm5Qohcfu1nHJknVA1XF2zY/transfers)
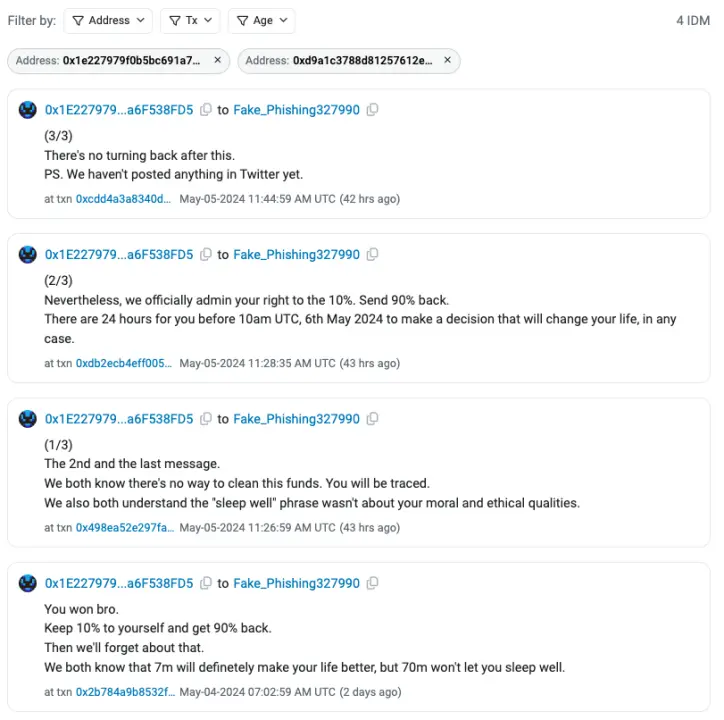
On May 4, the victim conveyed the following message to the hacker on-chain: "You won, brother. You can keep 10% and return 90%, and we can act like nothing happened." We all know that 7 million dollars is enough for you to live well, but 70 million dollars will make you sleep poorly.
On May 5, the victim continued to call out to the hacker on-chain but has not received a response yet.
(https://etherscan.io/idm?addresses=0x1e227979f0b5bc691a70deaed2e0f39a6f538fd5,0xd9a1c3788d81257612e2581a6ea0ada244853a91\&type=1)
How to Defend
- Whitelist mechanism: It is recommended that users save the target address in their wallet's address book, so that the next time they make a transfer, they can find the target address from the wallet's address book.
- Enable small amount filtering function in the wallet: It is recommended that users enable the small amount filtering function in their wallets to block such zero transfers and reduce the risk of phishing. The Slow Mist security team analyzed this type of phishing method in 2022; interested readers can click the links to view (Slow Mist: Beware of TransferFrom Zero Transfer Scam, Slow Mist: Beware of Same Ending Digit Airdrop Scam).

- Carefully verify if the address is correct: It is recommended that users check at least the first 6 digits and the last 8 digits (excluding the leading 0x) when confirming the address; of course, it is best to check every digit.
- Small amount transfer test: If the user's wallet only displays the first 4 digits and the last 4 digits of the address by default, and the user insists on using this wallet, they can consider conducting a small amount transfer test. If they unfortunately fall victim, it will still be a small loss.
Conclusion
This article mainly introduced the phishing attack method using addresses with the same starting and ending digits, analyzed the characteristics of the hacker and the fund transfer patterns, and provided recommendations to prevent such phishing attacks. The Slow Mist security team reminds users that since blockchain technology is immutable and on-chain operations are irreversible, please be sure to carefully verify addresses before conducting any operations to avoid asset losses.