Slow Fog: X Account Security Inspection and Reinforcement Guide
Author: Yao, Slow Mist Technology
Background Overview
Recently, there have been frequent incidents of Web3 project teams / celebrities having their X accounts hacked and used to send phishing tweets. Hackers are adept at using various methods to steal user accounts, with common tactics including:
- Inducing users to click on fake Calendly/Kakao meeting appointment links to steal user account authorization or control user devices;
- Direct messaging to trick users into downloading trojan programs (fake games, meeting apps, etc.), which not only steal private keys / recovery phrases but may also compromise X account permissions;
- Utilizing SIM Swap attacks to steal X account permissions that rely on phone numbers.
The Slow Mist security team has assisted in resolving multiple similar incidents. For example, on July 20, the X account of the TinTinLand project was hacked, and the attacker pinned a tweet containing a phishing link. With the assistance of the Slow Mist security team, TinTinLand promptly resolved the account theft issue and conducted authorization reviews and security hardening for the X account.

Considering the repeated emergence of victims, many users are not well-informed about how to enhance the security of their X accounts. The Slow Mist security team will explain how to conduct authorization checks and security settings for X accounts in this article, with the following specific operational steps.
Authorization Check
Taking the web version as an example, after opening the x.com page, click on "More" in the sidebar, and find the "Settings and privacy" option, which is mainly used to set account security and privacy.


After entering the "Settings" section, select "Security and account access" to set up account security and authorized access.

View Authorized Applications
Many phishing methods exploit users mistakenly clicking on authorized application links, resulting in the authorization of tweet permissions for the X account, which is then used to send phishing information.
Check method: Select the "Apps and sessions" section to see which applications the account has authorized. As shown in the image below, the demo account has authorized these 3 applications.
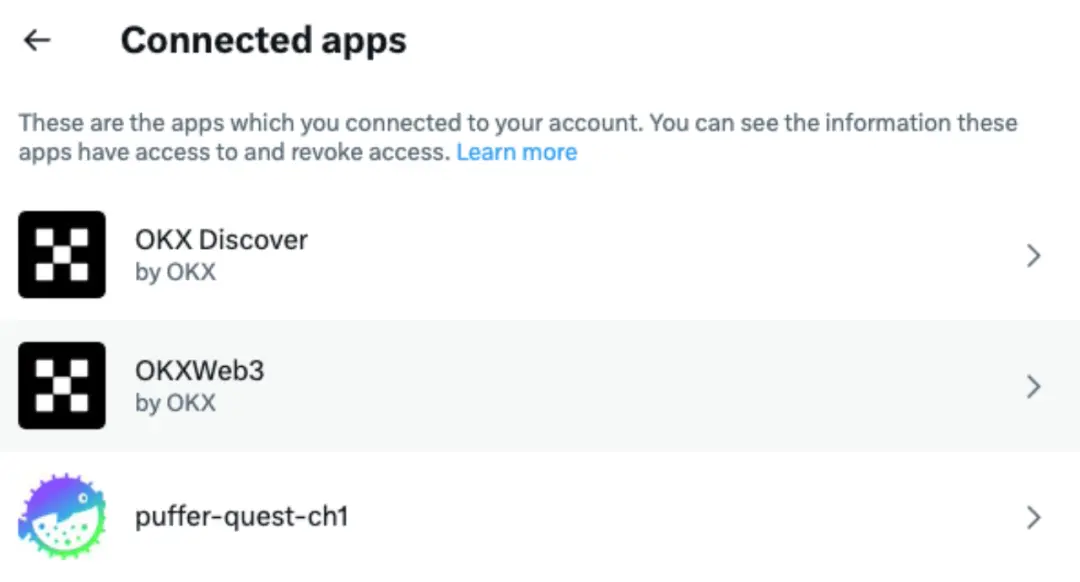
After selecting a specific application, you can see the corresponding permissions. Users can remove permissions through "Revoke app permissions."

View Delegation Status
Check method: Settings → Security and account access → Delegate

If you find that the current account has allowed invitation management, you need to enter "Members you've delegated" to see which accounts the current account has shared with. If sharing is no longer needed, you should cancel the delegation immediately.

View Abnormal Login Logs
If users suspect that their account has been maliciously logged in, they can check the login logs to see the devices, dates, and locations of abnormal logins.
Check method: Settings → Security and account access → Apps and sessions → Account access history

As shown in the image below, entering Account access history allows you to view the model of the login device, login date, IP, and region. If you find abnormal login information, it indicates that the account may have been stolen.

View Login Devices
If the X account is stolen and malicious logins occur, users can check the current account's login devices and kick off the malicious login devices.
Check method: Select "Log out the device shown" to log the account out from a specific device.


Security Settings
2FA Verification
Users can enable 2FA verification to add an extra layer of security to their accounts, preventing the risk of account takeover after password leakage.
Configuration method: Settings → Security and account access → Security → Two-factor authentication

You can set up the following 2FA methods to enhance account security, such as SMS verification codes, authenticator apps, and security keys.

Additional Password Protection
In addition to setting an account password and 2FA, users can also enable additional password protection to further enhance the security of their X accounts.
Configuration method: Settings → Security and account access → Security → Additional password protection

Conclusion
Regularly checking authorized applications and login activities is key to ensuring account security. The Slow Mist security team recommends that users periodically conduct authorization checks on their X accounts based on the inspection steps to strengthen account security and reduce the risk of being attacked by hackers. If you find that your account has been hacked, take immediate action to change your account password, conduct authorization checks, revoke suspicious authorizations, and implement security enhancement settings for your account.









