Fairyproof: 2023 Blockchain Ecosystem Security Annual Report
Author: Fairyproof

Overview of Perspectives
Compared to 2022, the state of the crypto market in 2023 has significantly improved, with a notable increase in the overall market value of crypto assets. At the same time, the occurrence of security incidents has also seen a substantial rise.
In a survey of 489 typical cases conducted by Fairyproof, nearly $1.23 billion worth of crypto assets was stolen.
With the rapid growth of Bitcoin, especially in the inscription ecosystem, the security risks in this ecosystem have become increasingly prominent, with 13 attacks targeting the Bitcoin ecosystem, particularly inscription facilities, occurring in 2023.
Attacks initiated due to private key leaks resulted in losses of $518 million in crypto assets, accounting for 45.07% of all losses caused by hacker attacks. Safely and securely managing private keys has always been a top priority for all blockchain users.
In 2023, Fairyproof extensively researched technologies and applications related to zero-knowledge proofs[1], becoming familiar with mainstream solutions and application scenarios in the industry. In terms of development, Fairyproof has refined a complete process and model, enabling rapid research, development, and deployment of solutions based on user needs and application scenarios. In auditing, Fairyproof has accumulated rich experience, capable of proficiently converting target issues into zero-knowledge circuits and professionally auditing circuits, proof generation, proof verification, etc. Additionally, Fairyproof has optimized the implementation solutions for zero-knowledge applications, developing its own system, which is superior in security and decentralization compared to existing popular solutions.
In 2023, Fairyproof also made bold strides in multi-party computation[2] (MPC) technology, establishing its own complete development process and model, enabling rapid development and deployment of MPC solutions in response to customer needs and scenario requirements.
Background Introduction
Before presenting the results of Fairyproof's research report in detail, it is necessary to explain and clarify the relevant terms used in this report.
CCBS
CCBS refers to "Centralized Crypto Asset or Blockchain Service Institutions." It typically refers to off-chain service platforms managed by human operations, whose core technology mainly relies on traditional centralized technologies, with daily operational activities primarily being off-chain. Traditional crypto asset exchanges (such as Binance) and crypto asset issuance and acceptance platforms (such as Tether) are typical examples.
Flash Loan
A flash loan is a common and popular method used by hackers to attack smart contracts on the Ethereum Virtual Machine platform. Flash loans are a contract calling method invented by the well-known DeFi application AAVE[3]. This contract call allows users to borrow crypto assets directly from DeFi applications that support this feature without any collateral, as long as the user repays the asset within a single block transaction to make the transaction valid[4]. Initially, this feature was invented to provide DeFi users with a more flexible and convenient means to conduct various on-chain financial activities. However, later on, due to its high flexibility, the most common scenario for using flash loans became hackers borrowing ERC-20[5] tokens to carry out attacks. Before initiating a flash loan, users need to clearly describe the logic for borrowing (assets) and repaying (assets, interest, and related fees) in a contract, and then call that contract to initiate the flash loan.
Cross-Chain Bridge
A cross-chain bridge is an infrastructure that connects multiple independent blockchains, allowing tokens deployed on different blockchains to circulate among them.
As more and more blockchains have their own ecosystems, applications, and crypto assets, the demand for cross-chain communication and transactions has significantly increased. This has also made cross-chain bridges popular targets for hackers.
Key Points of the Report
Fairyproof conducted a detailed study of 489 typical security incidents that occurred in 2023, statistically analyzing various factors such as the amount of losses caused by these incidents and their causes, and providing corresponding prevention suggestions and measures.
Statistics and Analysis of Security Incidents in 2023
The Fairyproof research team conducted a detailed study of 489 prominent security incidents in 2023, listing statistical results from both the targets that suffered attacks and the root causes of the attacks.
In the entire year of 2023, the total loss of crypto assets caused by these 489 security incidents reached $1.23 billion, while the total value of mainstream crypto assets displayed by Tradingview reached $1.62 trillion. The proportion of lost assets to the total market value is 0.08%.
Security Incidents Classified by Victim
The security incidents studied by Fairyproof can be classified into the following four categories based on their victims:
- Centralized Crypto Asset or Blockchain Service Institutions (CCBS, hereafter referred to as CCBS)
- Blockchains
- Decentralized Applications (dApps)
- Cross-Chain Bridges
The CCBS security incidents referred to in this report are those where the attacked or damaged object is a CCBS system. In these incidents, assets held by the CCBS are stolen or services operated by it are forced to shut down.
Blockchain security incidents refer to attacks or damages to the mainnet, sidechains, or second-layer expansion systems that depend on the blockchain mainnet. Typically, in these incidents, hackers launch attacks from within the system, outside the system, or both, leading to malfunctions in the system's software or hardware and asset losses.
dApp security incidents refer to attacks on dApps that prevent them from functioning normally, thereby giving hackers the opportunity to steal the crypto assets managed within the dApp.
Cross-chain bridge security incidents refer to attacks on cross-chain bridges that prevent them from functioning normally, even leading to the theft of crypto assets involved in transactions handled by them.
Fairyproof categorized the total of 489 incidents according to the above four categories, and the distribution chart is shown below:
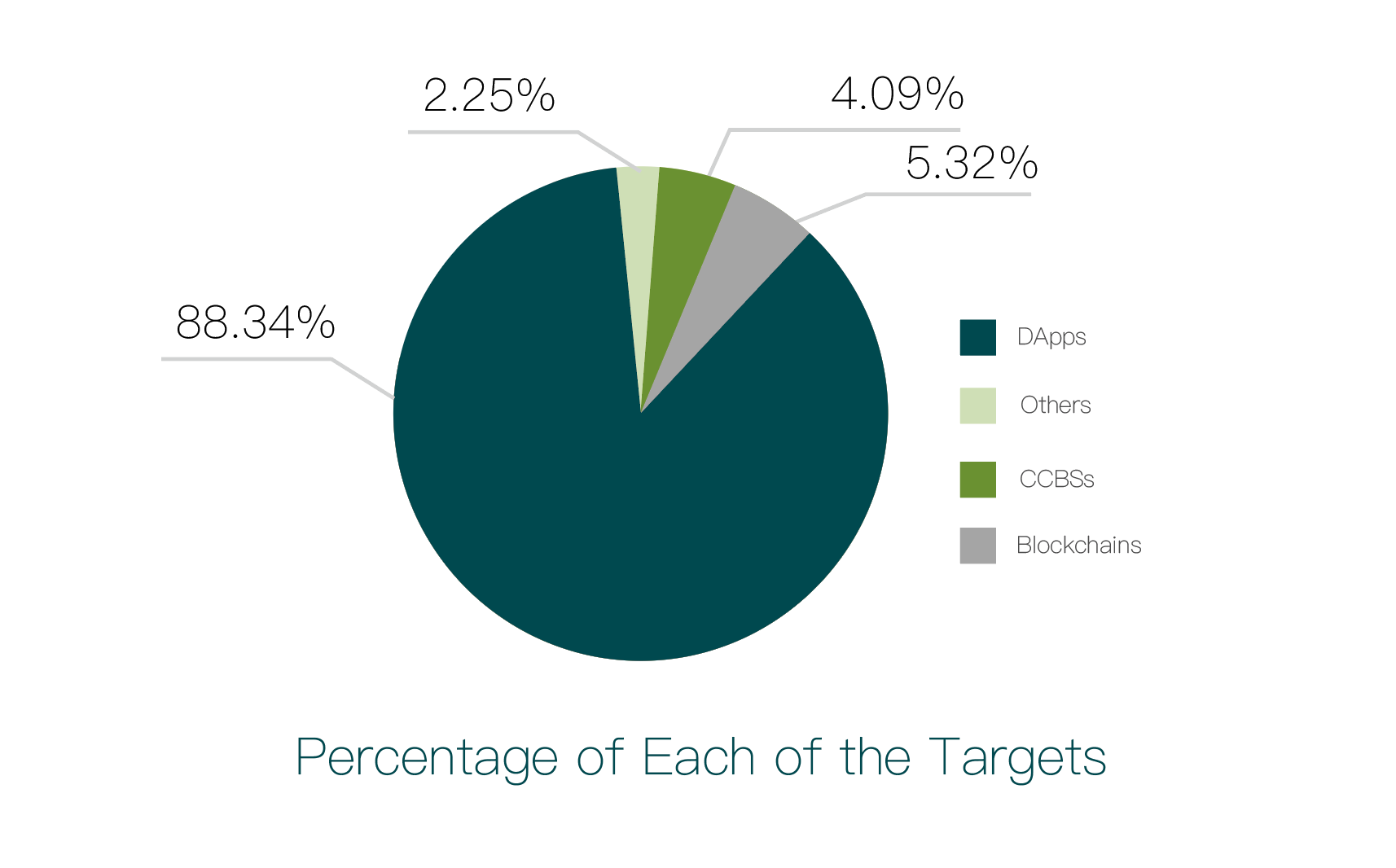
From the chart, it can be seen that dApp security incidents account for 88.34% of the total. Among them, there are 20 CCBS security incidents, 26 blockchain security incidents, and 432 dApp security incidents.
Blockchain Security Incidents
Security incidents involving blockchains can be further subdivided into the following three categories:
- Blockchain Mainnets
- Sidechains
- Layer 2 Solutions
Blockchain mainnets, also known as Layer 1, are independent blockchains with their own networks, protocols, consensus mechanisms, and validators. Blockchain mainnets can validate transactions, data, and blocks, all of which are verified by their own validators to achieve consensus. Bitcoin and Ethereum are typical examples of blockchain mainnets.
Sidechains are separate blockchains that operate in parallel with the blockchain mainnet. They also have their own consensus mechanisms and validators, but they connect to the blockchain mainnet in some way (e.g., through two-way pegs[6]).
Layer 2 solutions rely on blockchain mainnets and require them to provide security and finality[7]. They are primarily designed to address the scalability of blockchain mainnets, allowing transactions to be processed at lower costs and prices. Since 2021, Layer 2 solutions dependent on Ethereum have developed rapidly.
Both sidechains and Layer 2 solutions aim to solve the scalability issues of blockchain mainnets. The main difference is that sidechains do not rely on blockchain mainnets for security and consistency, while Layer 2 solutions do.
In 2023, there were a total of 26 security incidents related to blockchains. The chart below shows the proportions of incidents involving blockchain mainnets, sidechains, and Layer 2 solutions.

From the chart, it can be seen that blockchain mainnets and Layer 2 solutions account for 84.62% (22 incidents) and 15.38% (4 incidents), respectively, with no significant sidechain incidents occurring. The 4 incidents involving Ethereum Layer 2 solutions were Metis[8], zkLink[9], Boba[10], and Arbitrum[11]. Among the incidents involving blockchain mainnets, the attack on Mixin resulted in the largest losses, while other attacks on mainnet projects were primarily social engineering attacks, which did not cause significant asset losses.
dApp Security Incidents
Among the 432 security incidents involving dApps, 45 were exit scams, 263 were collateral damage, and 124 were direct attacks. Direct attacks on dApps typically involve three aspects: the dApp's frontend, backend, and smart contracts. Therefore, we categorize the 124 directly attacked incidents into the following three categories:
- dApp Frontend
- dApp Backend
- dApp Contracts
In incidents where the dApp frontend was attacked, hackers primarily exploited frontend vulnerabilities to steal assets or paralyze services.
In incidents where the dApp backend was attacked, hackers primarily exploited backend vulnerabilities, such as hijacking communication between the backend and contracts, stealing assets, or paralyzing services.
In incidents where the dApp contracts were attacked, hackers primarily exploited contract vulnerabilities to steal assets or paralyze services.
The chart below shows the proportions of incidents in these three categories:

As shown in the chart, the proportions of attacks on contracts, backends, and frontends are 95.16%, 0%, and 4.84%, respectively. Among the total of 124 incidents, 6 involved frontend attacks, while 118 involved contract attacks.
We further researched the amounts of crypto asset losses caused by each type of incident. The losses from frontend attacks amounted to $238,000, while losses from contract attacks reached $542 million.
Clearly, contract security remains the biggest issue. Among the various contract vulnerabilities, logical flaws, private key leaks, flash loan attacks, and reentrancy attacks are typical vulnerabilities.
We studied 118 security incidents involving contract attacks and obtained the following proportion chart:
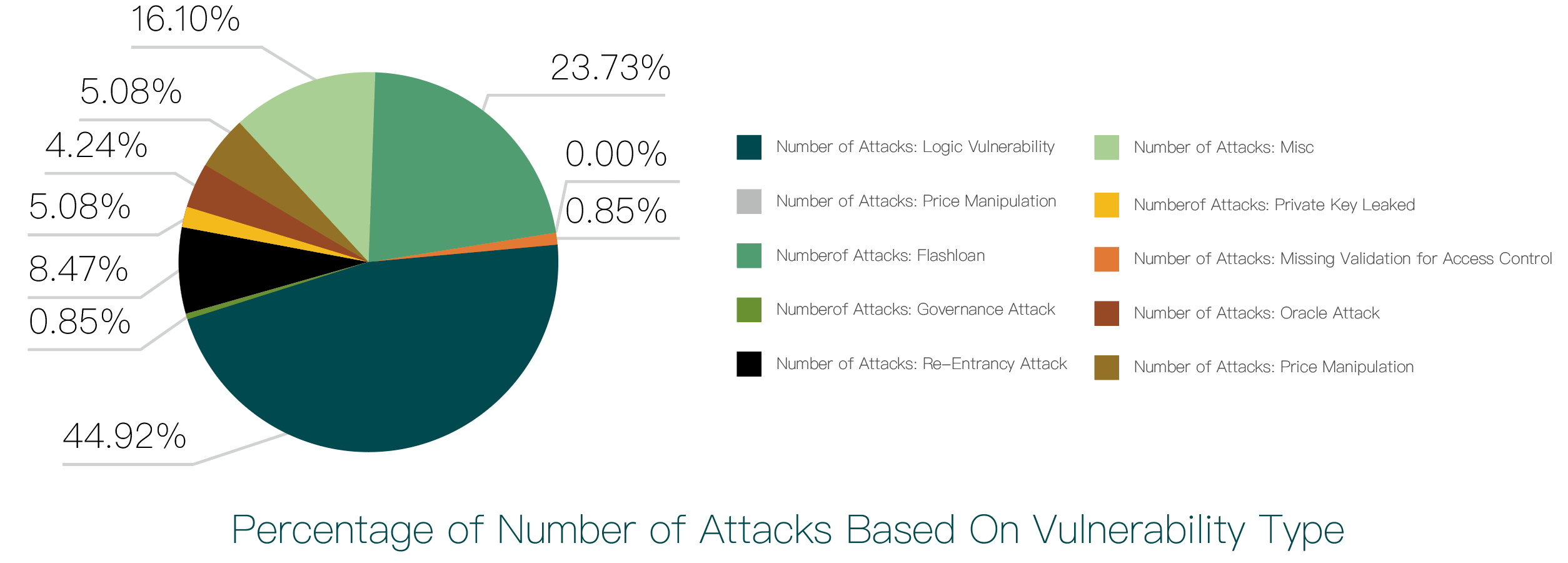
As shown in the chart, logical flaws account for the highest proportion of contract security incidents, followed by flash loan attacks. Logical flaws typically include missing parameter validation, lack of permission verification, etc. There were 53 incidents due to logical flaws and 28 incidents due to flash loans.
The chart below shows the loss amounts caused by various vulnerabilities:
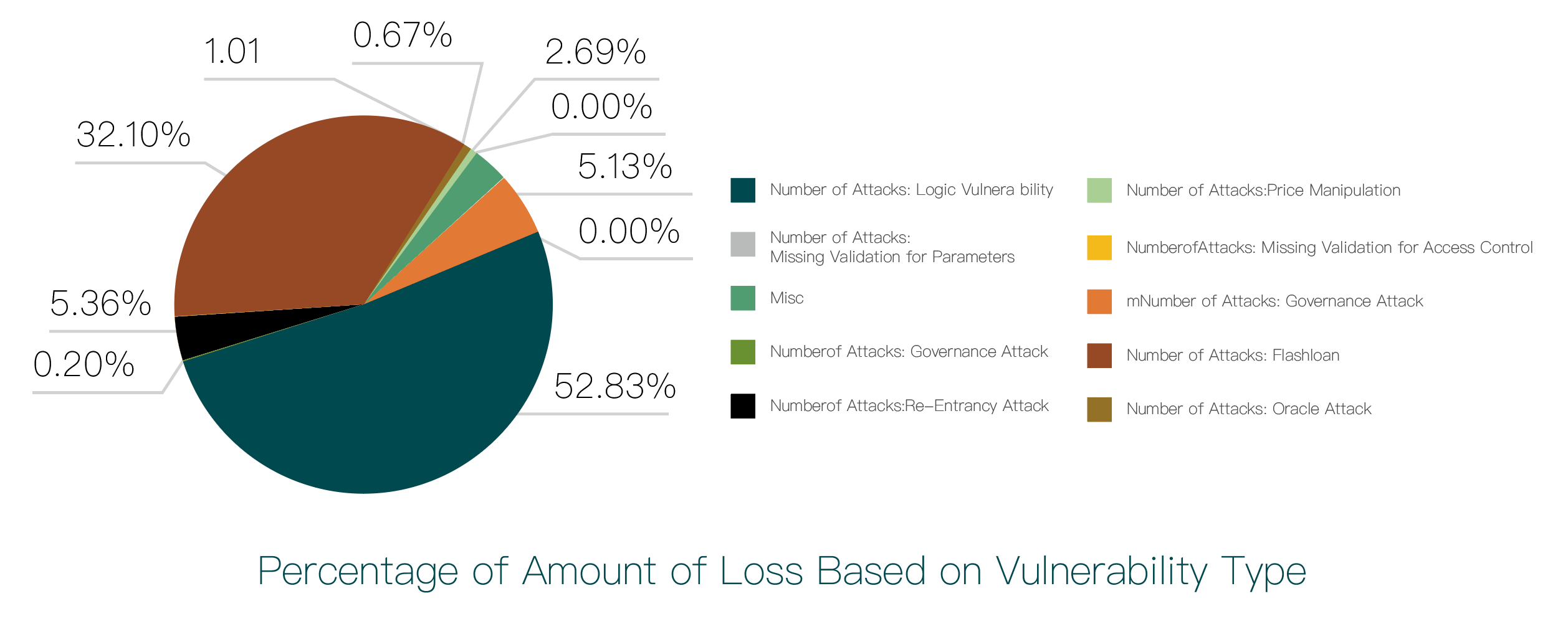
From the chart, it can be seen that losses caused by logical flaws rank first among all categories, with 53 security incidents resulting in losses of $286 million, accounting for 52.83% of the total amount; losses caused by private key leaks rank second, with 6 incidents resulting in losses of $174 million, accounting for 32.1%; losses caused by reentrancy attacks rank third, with 10 security incidents resulting in losses of $29.06 million, accounting for 5.36%.
Security Incidents Classified by Cause
Based on the causes of blockchain security incidents, we categorize the incidents into three types:
- Caused by hacker attacks
- Exit scams
- Others
Our research results are shown in the chart below:
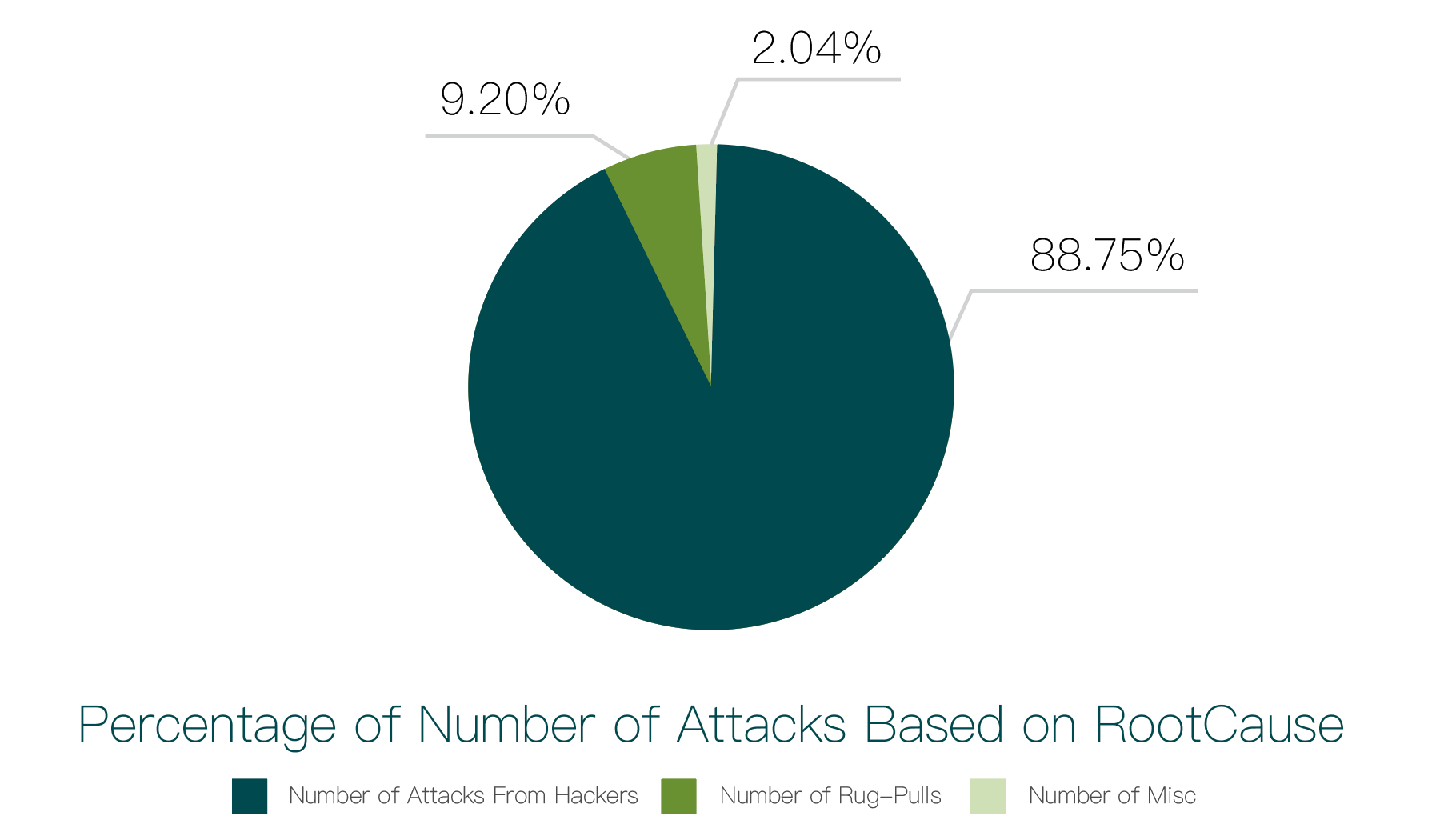
As shown in the chart, security incidents caused by hacker attacks and exit scams account for 88.75% (434 incidents) and 9.2% (45 incidents), respectively.
We studied the losses caused by these causes, as shown in the chart below:
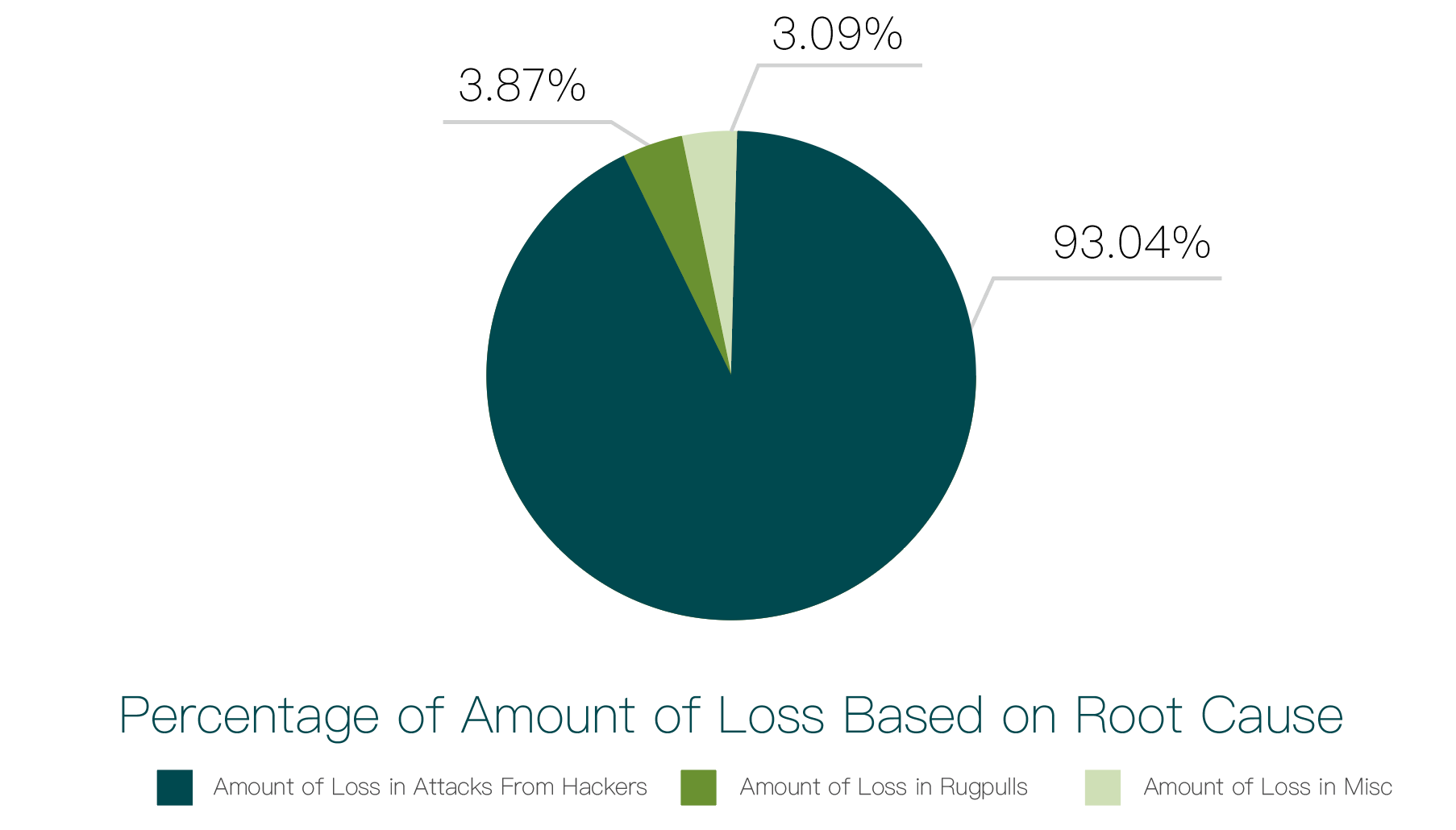
As shown in the chart, the loss amounts caused by hacker attacks and exit scams account for 93.04% and 3.87%, respectively, with the former causing losses of $1.15 billion and the latter causing losses of $47.76 million. This indicates that in 2023, hacker attacks remain the primary threat to industry security.
Hacker Attack Incidents
We studied hacker attack incidents, as shown in the chart below:
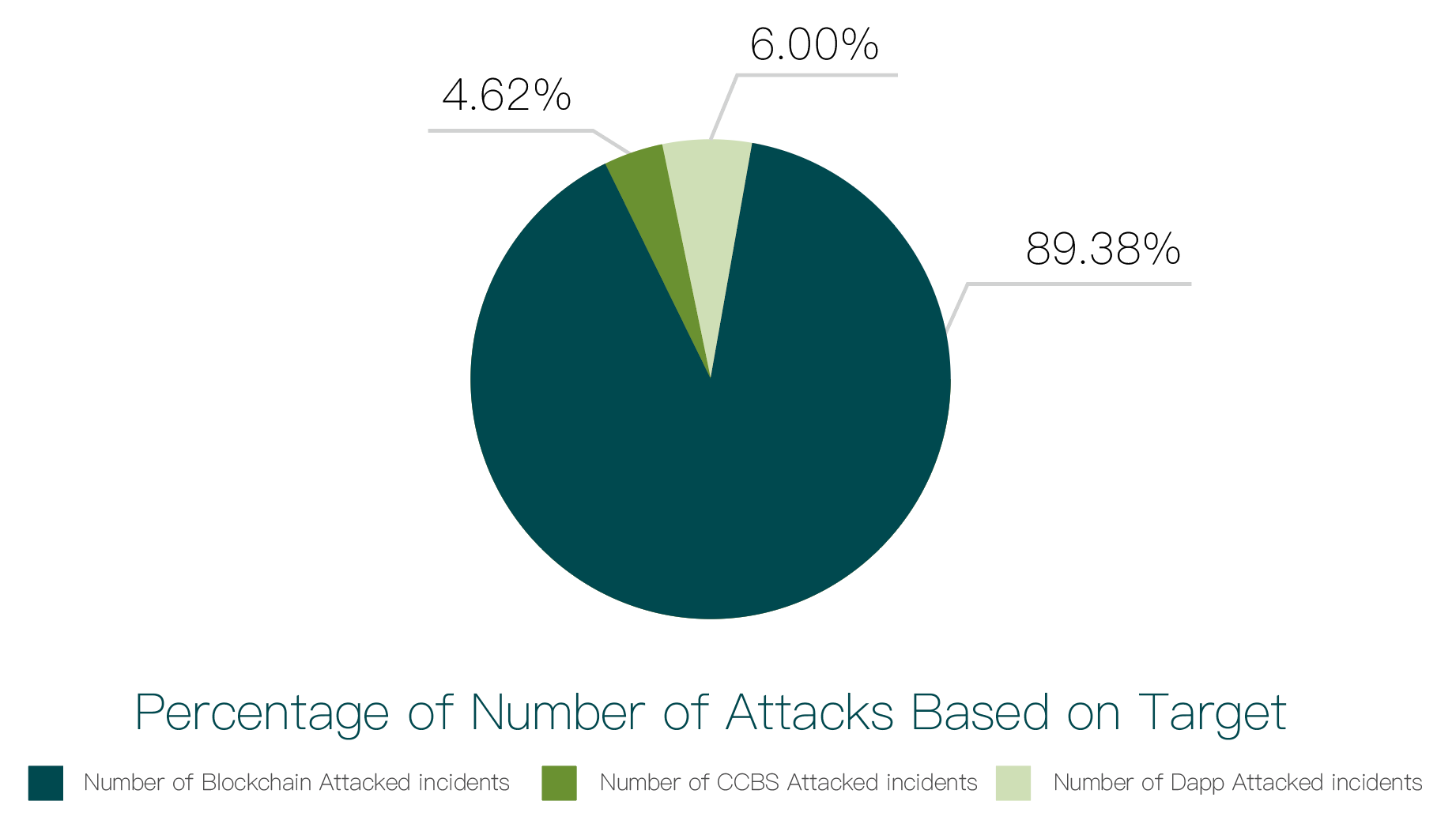
As shown in the chart, incidents of hackers attacking dApps, CCBS, and blockchains account for 89.38% (387 incidents), 4.62% (20 incidents), and 6% (26 incidents), respectively.
We studied the loss amounts caused by each type of incident, as shown in the chart below:
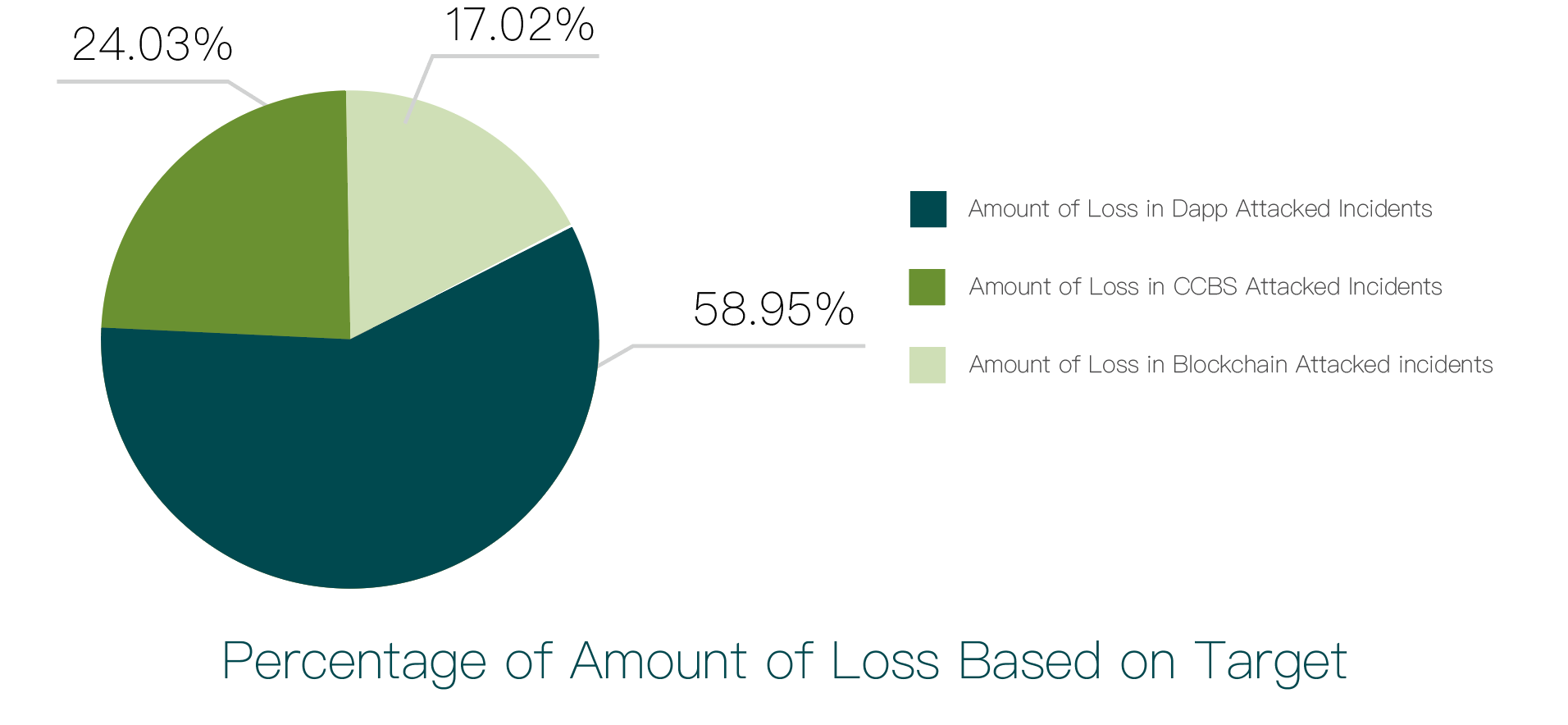
The asset losses caused by hackers attacking dApps, CCBS, and blockchains account for 58.95%, 24.03%, and 17.02%, respectively, with specific loss amounts of $694 million, $283 million, and $200 million.
Exit Scam Incidents
The exit scam incidents that occurred in 2023 primarily took place in dApp projects. A total of 45 exit scam incidents resulted in losses of $47.76 million. This loss amount is significantly smaller compared to the losses caused by hacker attacks.
Research Findings
From our statistical data, it is evident that in 2023, hackers still favored attacking dApp projects, with incidents targeting dApps far exceeding those targeting any other objects, resulting in the highest asset losses of $694 million, accounting for 58.95% of the total amount of all attack incidents. This indicates that the current security status of dApps poses considerable concerns and is a key issue that needs attention in the overall blockchain ecosystem's security.
For the entire blockchain ecosystem, hackers remain the greatest security threat, both in terms of the number of security incidents caused and the asset losses incurred. The number of security incidents caused by hacker attacks accounts for over 88.75% of all security incidents, and the amount of asset losses caused by these attacks accounts for over 93.04% of all losses, far exceeding the threat posed by exit scams.
In 2023, the number and amount of losses from attacks on Layer 2 solutions were lower than in 2022. We believe this is a result of the maturation of Layer 2 technology and increased attention to security.
A typical dApp consists of three parts: frontend, backend, and smart contracts. When hackers attack a dApp, they may target one part or multiple parts simultaneously. According to our statistical data, attacks on smart contracts far exceed attacks on frontends and backends in both quantity and amount. This indicates that smart contracts remain the primary target for hackers when attacking dApps.
The typical exit scam incidents that occurred in 2023 were all related to dApp projects. This indicates that exit scams in dApps remain a key risk that users need to guard against.
In incidents where smart contracts were attacked by hackers, logical flaws were the leading cause in terms of both the number of attack incidents and the amount of losses incurred, far exceeding other categories.
Exploration and Reflection
An increasing number of entrepreneurial teams have already entered and are planning to enter the application fields related to zero-knowledge proofs, including Ethereum-based ZK Layer 2 solutions and ZK-based social applications. We believe that with the explosion and emergence of these applications, the demand for development and auditing based on ZK systems will grow rapidly.
Practical Solutions and Measures for Preventing Security Incidents
In this section, we will summarize some solutions and measures to help blockchain developers and users manage and prevent blockchain risks based on the characteristics of security incidents that occurred in 2023. We recommend that both blockchain developers and users actively implement and practice these solutions and measures in their daily operations and work to maximize the protection of project security and crypto asset safety.
Note: "Blockchain developers" refers to both the development engineers of blockchain projects themselves and developers related to or extending from blockchain systems (such as crypto assets, etc.). "Blockchain users" refers to all users participating in activities within the blockchain system (such as management, operation, maintenance, etc.) or engaging in crypto asset trading.
For Blockchain Developers
Developers of cross-chain bridges need to pay close attention to the security of cross-chain bridges. Cross-chain bridge solutions generally include both on-chain operations and off-chain operations. Off-chain operations are relatively more susceptible to hacker attacks, so cross-chain bridges need to pay special attention to the security and reliability of off-chain operations.
Although the losses caused by attacks on Layer 2 solutions in 2023 were relatively small compared to cross-chain bridges, their security is equally important. This is because the upcoming development and implementation of Layer 2 solutions will see a surge, and research on the security of these solutions will be a significant challenge for the industry.
In blockchain applications, after a project has been deployed and running stably for a period, it is essential to transfer the permissions for controlling critical operations within the project to a multi-signature wallet or DAO organization for management.
When hackers discover vulnerabilities in smart contracts, they often exploit flash loans to attack the contracts. These potentially exploitable vulnerabilities typically include reentrancy vulnerabilities, logical flaws (such as lack of permission verification, incorrect pricing algorithms), etc. Vigilantly preventing and addressing these vulnerabilities should always be a top priority for smart contract developers.
Our statistical data also shows that an increasing number of hackers are launching phishing attacks via social media platforms (such as Discord, Twitter, etc.). This phenomenon persisted throughout 2022, resulting in losses for many users. Project teams need to implement strict and comprehensive management of their operational social media and deploy appropriate security measures to ensure the safety and stability of their social media operations, preventing exploitation by hackers.
For Blockchain Users
An increasing number of users are participating in various blockchain ecosystem activities and holding various blockchain ecosystem assets. In this process, cross-chain trading activities are also rapidly increasing. When users engage in cross-chain transactions, they need to interact with cross-chain bridges, which are often targeted by hackers. Therefore, before initiating a cross-chain transaction, users should thoroughly investigate and understand the security and operational status of the cross-chain bridge they are using to ensure its safety, stability, and reliability.
When users interact with dApps, they must pay close attention to the quality and security of the smart contracts involved, as well as the security of the dApp frontend. Any suspicious or dubious information, prompts, or dialogues appearing on the frontend should be handled with caution, and users should avoid clicking or following any instructions without careful consideration.
We strongly recommend that users carefully check and read the audit reports of any blockchain project before interacting with it or investing in it. For projects without audit reports or with questionable reports, users should participate with caution.
We advise users to use cold wallets or multi-signature wallets to manage large assets or assets not used for frequent trading whenever possible. Users should always be vigilant about the operational security of hot wallets and ensure that the hardware platform on which the hot wallet is installed is secure, reliable, and stable.
Users need to conduct a certain level of investigation and understanding of the team background behind blockchain projects. They should be cautious of teams with vague backgrounds or lacking credibility. Such projects may pose exit scam risks. For frequently used centralized exchanges, users should pay even more attention to their backgrounds and credibility, verifying these exchanges' backgrounds, information, and data from multiple third-party sources to ensure their long-term secure operation.
References
[1] zero-knowledge proof. https://en.wikipedia.org/wiki/Zero-knowledge_proof
[2] MPC. https://en.wikipedia.org/wiki/Securemulti-partycomputation
[3] Aave. https://aave.com/
[4] Flash-loans. https://aave.com/flash-loans/
[5] ERC-20 TOKEN STANDARD. https://ethereum.org/en/developers/docs/standards/tokens/erc-20/
[6] Sidechains. https://ethereum.org/en/developers/docs/scaling/sidechains/
[7] Layer-2. https://academy.binance.com/en/glossary/layer-2
[8] Metis. https://www.metis.io/
[9] zkLink. https://zk.link/
[10] Boba. https://boba.network/
[11] Arbitrum. https://arbitrum.io/









