Detailed Explanation of Secret Network: What is a Programmable Privacy Public Chain?
Written by: 0x76/Rhythm BlockBeats
In the blockchain industry, privacy has always been a rather chaotic concept. Therefore, before we truly begin to introduce today's privacy project, Secret Network, it is necessary to first clarify the concepts related to privacy.
This article will be divided into two parts. The first part will reanalyze privacy and the main related concepts. In the second part, we will directly get hands-on and see how the first truly usable public chain supporting privacy programming, Secret Network, differs from other public chains in practice.
What are we really discussing when we talk about privacy?
Privacy has been a label surrounding the crypto industry since the birth of Bitcoin. Satoshi Nakamoto even dedicated a chapter in the Bitcoin white paper to discuss privacy issues. However, is the privacy provided by Bitcoin really what we mean by privacy in our daily lives?
Naturally Anonymous Accounts
We know that the mainstream blockchain networks represented by Bitcoin and Ethereum have one of their most important features: all transaction records are completely public and verifiable. The only reason users can maintain a certain level of privacy in such an extremely transparent environment is due to their unique account registration mechanism.
For any account system, the most important task is to prevent duplicate account names. Once duplicates occur, the information related to them, including asset ownership, will become contentious, leading to serious chaos in the entire system. Just like the primary key in each table of a database, accounts in a system must ensure uniqueness to allow the system to function properly.
Therefore, in a typical account system, there must be a centralized node responsible for registering new accounts to ensure the uniqueness of each account in the system. However, Bitcoin, needing to achieve complete decentralization, must adopt other solutions.
As we know, Satoshi Nakamoto's final answer was for each user to independently generate addresses through a random algorithm. But how does the random algorithm prevent address duplication? The answer is that it fundamentally cannot. What we can do is to reduce the probability of address duplication to a sufficiently low level, ultimately using this decentralized probabilistic certainty to replace the final certainty of a centralized registration mechanism.
Due to this completely random generation mechanism, all addresses possess inherent anonymity. This anonymity is what we often referred to as privacy in the early days.
However, there are two significant drawbacks to protecting privacy through address anonymity. One is the irreversibility of anonymity; once the true identity of an address is exposed, the loss of that anonymity is irreversible.
Another characteristic is that maintaining address anonymity is entirely an off-chain matter. In other words, after the address is generated, the responsibility for maintaining anonymity lies with the off-chain holder, and the blockchain system knows nothing and can do nothing about it.
In this context, early on-chain privacy solutions could only help users restore anonymity by continuously deleting and re-registering accounts, severing the connection between new anonymous addresses and old addresses.
The early privacy projects we are familiar with, such as Tornado.cash, as well as Dash, Monero (XMR), Zcash (ZEC), and other privacy public chains, were fundamentally designed around this idea.
The Collapse of the Anonymous Account System
However, as blockchain technology gradually transitioned from the Bitcoin era to the smart contract era represented by Ethereum, the impact of newly emerging applications on the original anonymous account system has become increasingly significant.
In the early days, addresses were merely used to store purchased cryptocurrencies. Today, we need to use these addresses to purchase NFT avatars, associate social accounts, hold domain names, retain game items, and even publish Mirror articles. All these activities have made it increasingly costly to maintain the anonymity of these addresses, and the process of deleting and re-registering accounts has become so complex that it is nearly unfeasible.
Thus, we suddenly realize that simple anonymous addresses can no longer meet the usage needs of users in the new era; we need more advanced privacy solutions.
What is True Privacy?
We will not engage in any academic discussions about the definition of privacy here; instead, we will directly use the commonly accepted understanding of privacy in daily life. The privacy we refer to in our daily lives does not mean that people live with masks every day, but rather that even if we disclose our identities, we can still have our private space and conduct private transactions when needed.
Correspondingly, the privacy we need in blockchain should ideally take this form: even if my address is a publicly identifiable address, I can choose to hide the amount of assets I hold based on my needs, interact with DeFi protocols without worrying about information being disclosed, and although the NFTs I purchase exist in my address, I can choose whether to publicly display them according to my will.
For this need, traditional privacy public chains that cannot support smart contracts are clearly powerless. We need new programmable privacy public chains to fulfill this mission.
Programmable Privacy Public Chains
Currently, in the entire market, there are two public chains that support smart contracts and allow for customized privacy options for transactions on the public chain: one is the Cipher Paratime for privacy programming launched by Oasis Labs, and the other is the privacy public chain Secret Network within the Cosmos ecosystem.
Of course, we will focus on Secret Network, which has already formed a scalable and usable ecosystem. As for Oasis Labs' privacy products, we can only introduce them later when there are available applications.
(Note: The Oasis network has different Paratimes. Readers unfamiliar with the concept of Paratime can simply understand it as different Rollups on Ethereum. Many users have only encountered the EVM-compatible Emerald Paratime, while the Cipher Paratime that truly supports privacy programming is still not mature.)
Development History of Secret Network: From Ethereum to Cosmos Ecosystem Application Chain
The Secret Network project was originally named Enigma and initially hoped to develop within the Ethereum ecosystem. However, after encountering performance bottlenecks, it adjusted its technical route and switched to developing an independent public chain that supports privacy computing through the Cosmos SDK. This public chain is now known as Secret Network.
As a member of the Cosmos ecosystem, Secret Network can seamlessly integrate with the IBC cross-chain protocol, allowing for easy interaction with other public chains in the Cosmos ecosystem.
Practical Privacy Features of Secret Network
Many previous articles introducing privacy projects often like to use some seemingly grand concepts, not to clarify matters but to muddy the waters. Therefore, in the latter part of this article, we will directly introduce readers to what programmable privacy really is through hands-on practice.
First, like any other smart contract platform public chain, Secret has its own native token: SCRT. This token can be used to pay transaction fees on the Secret network and participate in PoS staking. Like other smart contract platforms (such as Juno), the transfer records of SCRT are completely transparent and publicly verifiable, so there are no privacy attributes.
However, unlike Juno, Secret Network has a special privacy token, which we call sToken. Every ordinary token can be packaged into an sToken to gain privacy attributes.
In the Keplr wallet, we can also find that unlike other public chains that only have Stake and Governance options, there is a Secret SCRT button under the governance tab in the Secret Network section. Clicking it will take you to the conversion page from Secret to sSecret.
On this interface, we can directly convert the non-privacy SCRT tokens held in our wallet into privacy-enabled sSCRT tokens.
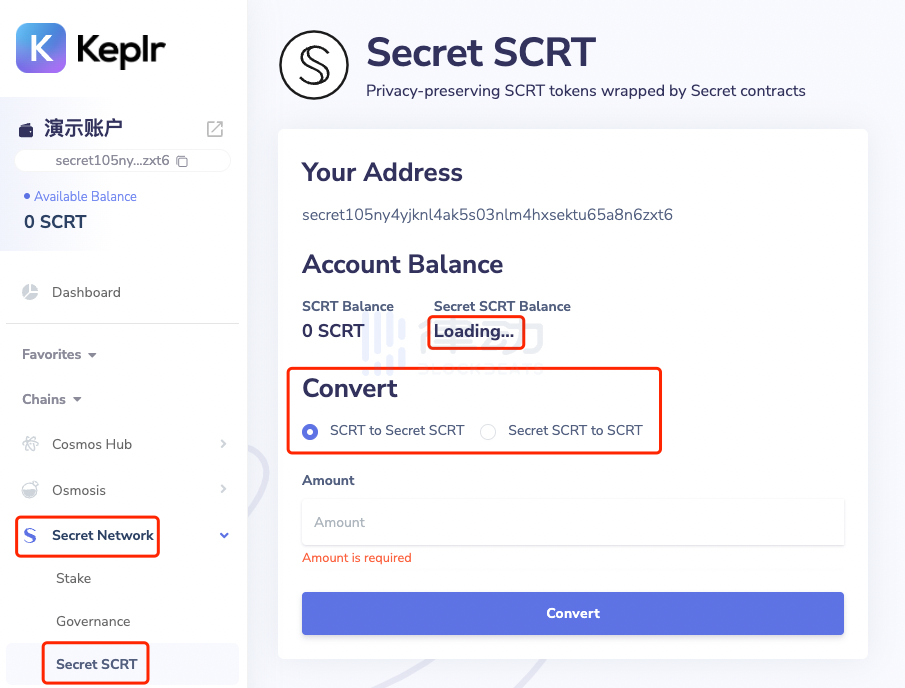
However, if you are using sSCRT for the first time, you will find that after the conversion is complete, the wallet interface does not directly display the balance of sSCRT but shows a Loading… status.
This is because, in Secret Network, any sToken is by default invisible to any visitor, including the address holder. If you want to see the balance of sToken, you need to first sign a transaction to generate a Viewing Key.
If we refresh this page, the system will automatically pop up the following Add Token transaction signing interface. Here, Add Token refers to adding the sSCRT token, and the contract address displayed at the top of the interface is the contract address of sSCRT.
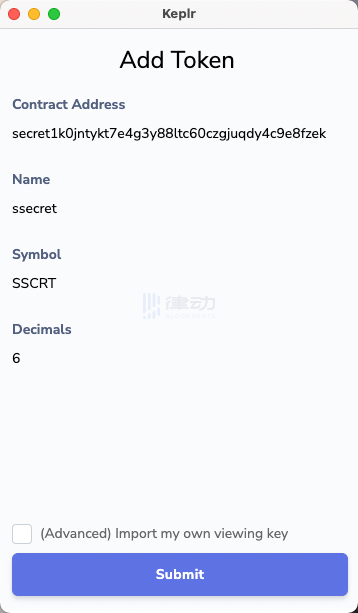
After clicking Submit, you will enter the transaction signing interface. Note that signing any transaction requires SCRT to pay gas fees; sSCRT cannot be used as gas. Therefore, when you are exchanging for sSCRT, remember to keep some SCRT balance.
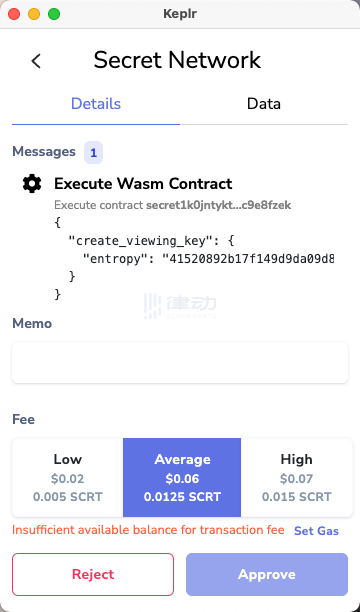
After signing, the system will generate a Viewing Key for your wallet. A wallet that has obtained the corresponding Viewing Key will have the permission to query, transfer, and perform various operations on the corresponding sToken. Moreover, the addition of the Viewing Key is one-time; as long as you do not change wallets, you will not need to recalculate the Viewing Key.
Just as SCRT has a uniquely corresponding privacy token sSCRT in Secret Network, any other token entering Secret Network can generate a separate privacy token sToken, and each sToken corresponds to a unique contract address.
Similarly, when an account first receives a new sToken, it also needs to sign a transaction to generate a new Viewing Key; otherwise, the balance of the sToken cannot be displayed properly.
So how does sToken protect users' privacy during use? Below, we will verify some common transactions using the Mintscan explorer.
(1) Sending and Receiving sToken
When an address pays sToken, a transaction record will be left in the explorer. Taking the payment of sSCRT as an example, the payer's address is publicly visible in the explorer, and we can also see that this transaction involves interaction with the sSCRT contract, but the payee and transaction amount are not visible.
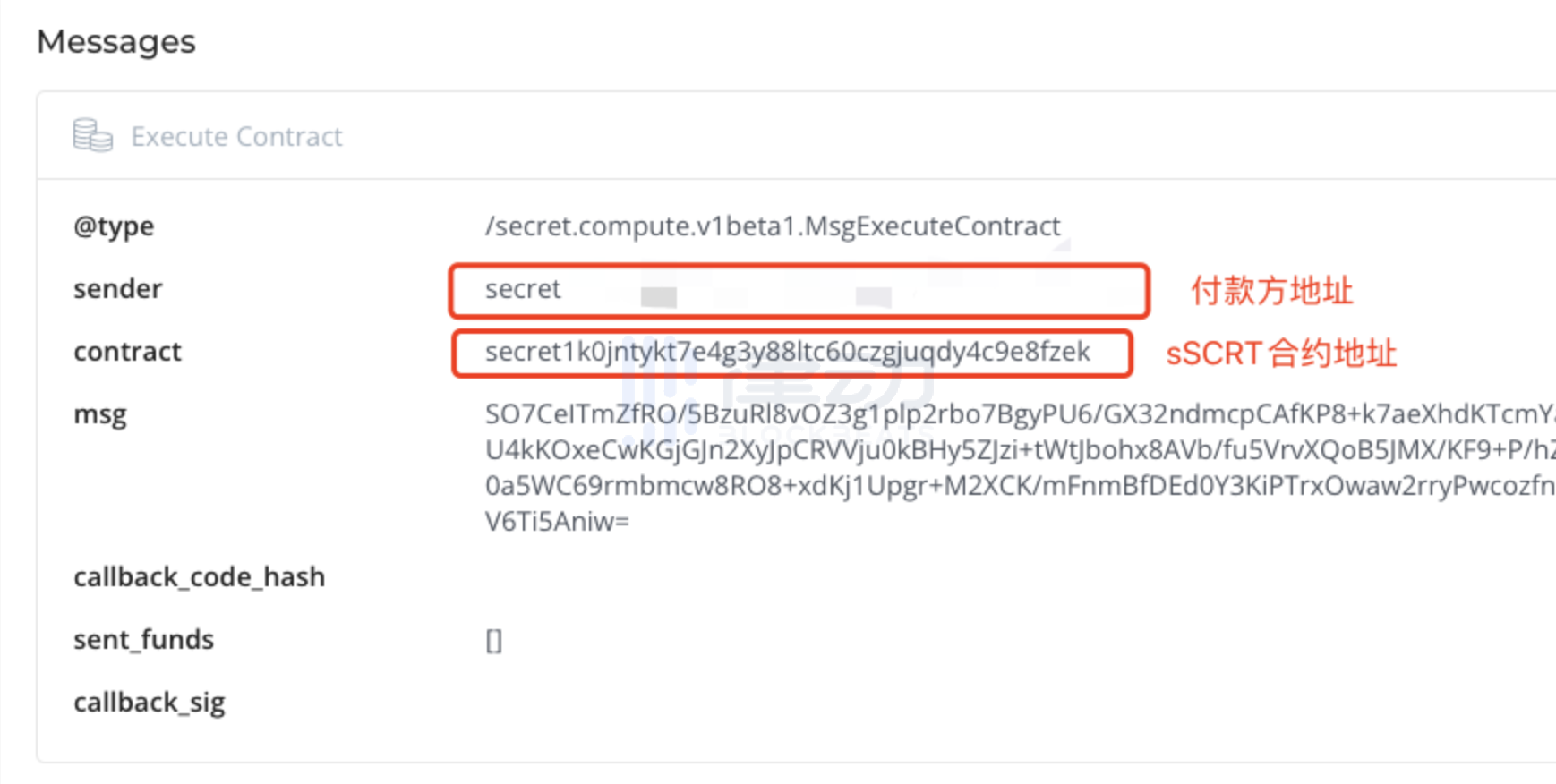
Now let's look at the status of the payee. When we confirm that the funds have been received in the wallet and then open Mintscan, we find that the transaction history does not show any new transactions. Therefore, no one can find out how much sToken an address has received through public information.
(2) Transactions and Exchanges
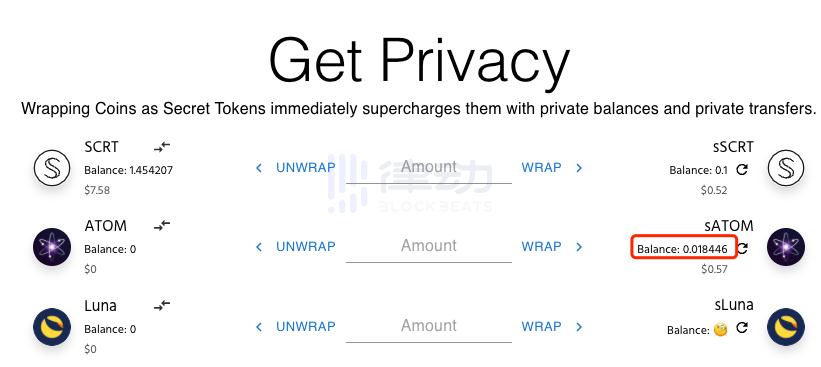
We use the native trading platform SecretSwap in Secret Network to exchange 0.1 sSCRT for sATOM.
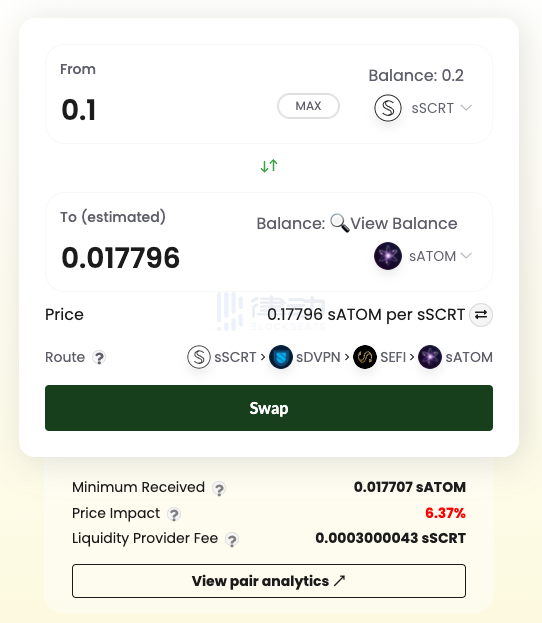
The following is the record of this transaction in the explorer. It can be seen that we can still see the payer's address, and we can also infer that they interacted with the sSCRT contract, but what they did, which tokens were exchanged, and the amounts cannot be verified from the public records.
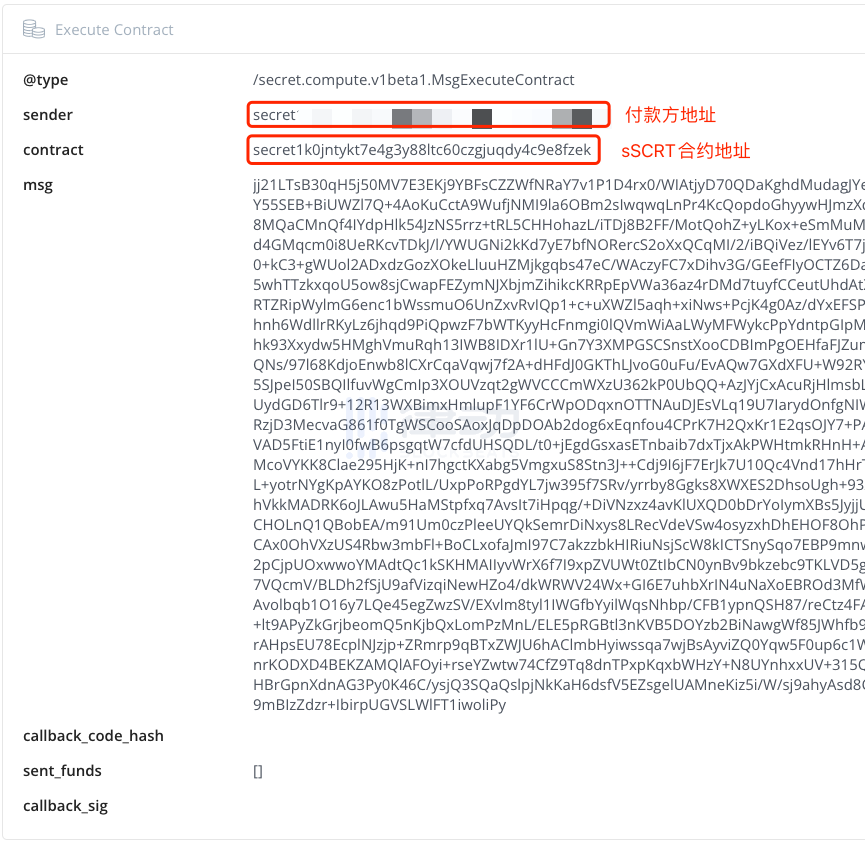 However, since this is our first time holding sATOM, we cannot directly see the amount of sATOM we just purchased in the wallet interface; we need to sign another transaction to create a Viewing Key for sATOM to continue operating our purchased asset.
However, since this is our first time holding sATOM, we cannot directly see the amount of sATOM we just purchased in the wallet interface; we need to sign another transaction to create a Viewing Key for sATOM to continue operating our purchased asset.
We go directly to the dedicated website for converting sTokens provided by Secret Network (wrap.scrt.network) and connect our Keplr wallet.
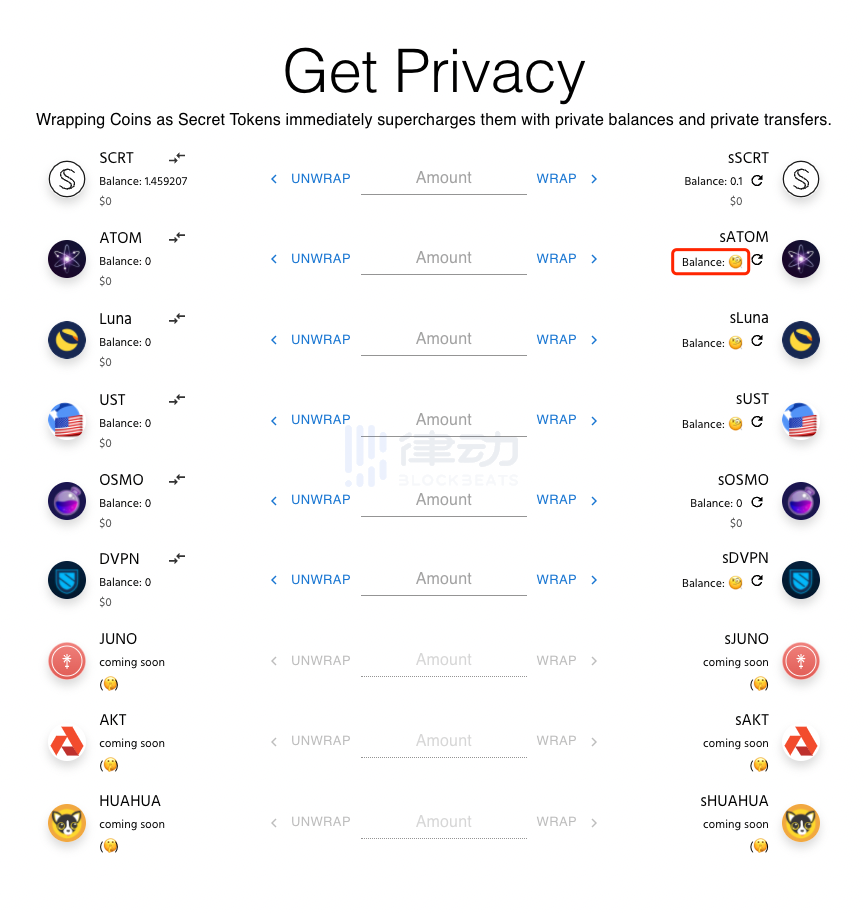 We can see that in the right sATOM balance section, a yellow icon indicates that the Viewing Key has not yet been created. Clicking here will pop up the transaction signing interface to create the Viewing Key.
We can see that in the right sATOM balance section, a yellow icon indicates that the Viewing Key has not yet been created. Clicking here will pop up the transaction signing interface to create the Viewing Key.
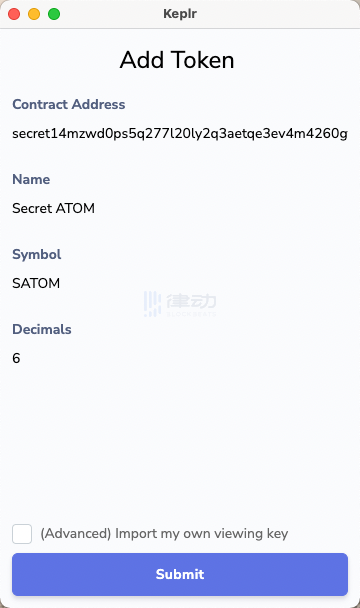
After signing successfully, we can now see the balance of sATOM in the interface and the Keplr wallet plugin.
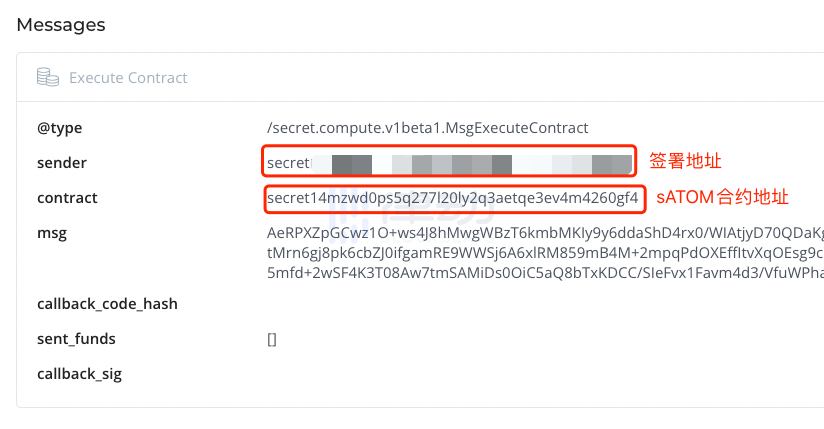
At the same time, the signing operation just now will leave a public transaction record, showing that your address has interacted with the sATOM contract address, but it is impossible to determine the specific content of the interaction.
 The above is the public information generated when using sToken for payments and transactions on Secret Network. It can be seen that by using sToken, users can selectively hide key information about their transactions, protecting the privacy and security of key information.
The above is the public information generated when using sToken for payments and transactions on Secret Network. It can be seen that by using sToken, users can selectively hide key information about their transactions, protecting the privacy and security of key information.
Bridging Non-Privacy Assets
As we just saw, Secret Network can convert any asset into a privacy token, thereby hiding related transaction information. If users want their Ethereum or other public chain assets to also have this privacy protection feature, they need to use a cross-chain bridge for asset transfer.
The official cross-chain bridge of Secret Network consists of two important components: one is the IBC cross-chain packaging bridge, and the other is the official bridge supporting Ethereum, BSC, and Monero cross-chain.
(1) IBC Cross-Chain Packaging Bridge (https://wrap.scrt.network/)
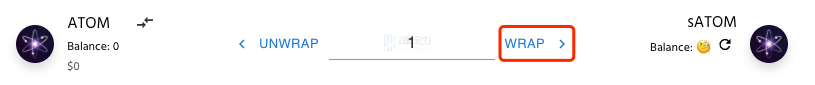
This bridge is the application we just used to query the sATOM address. It can help users quickly package ordinary tokens into privacy tokens (the red box in the middle) and also facilitate rapid asset cross-chain transfers between different Cosmos public chains through the IBC protocol (the left red box).
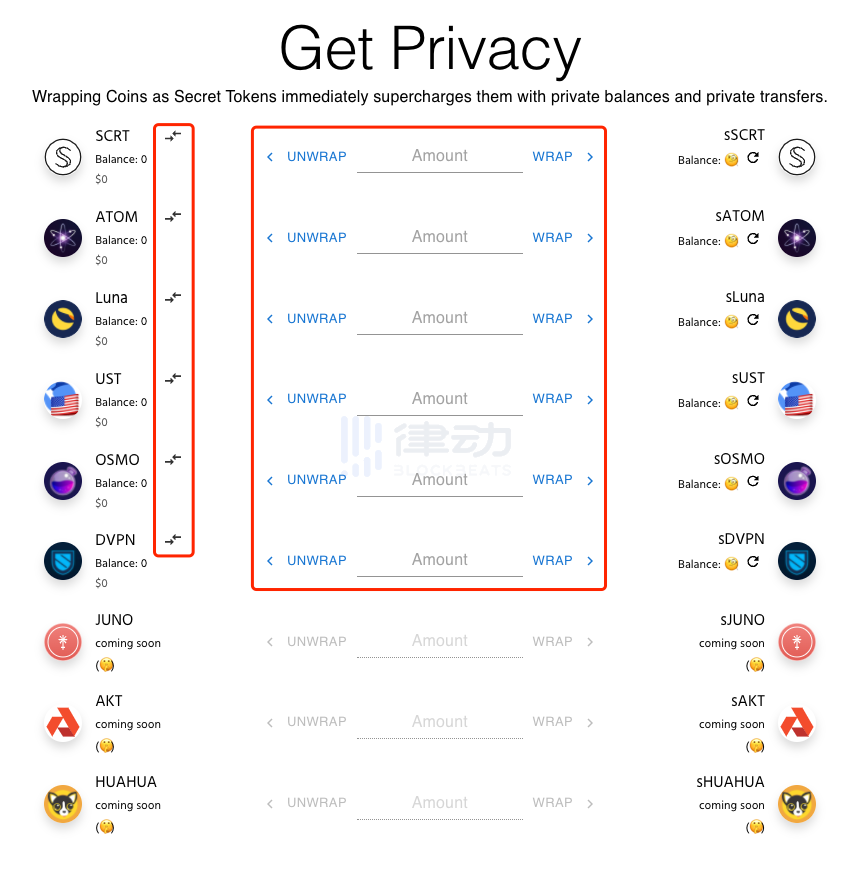 We click the bidirectional arrow button on the left side of the interface to directly bring up the IBC cross-chain interface, where we can operate assets to enter and exit Secret.
We click the bidirectional arrow button on the left side of the interface to directly bring up the IBC cross-chain interface, where we can operate assets to enter and exit Secret.
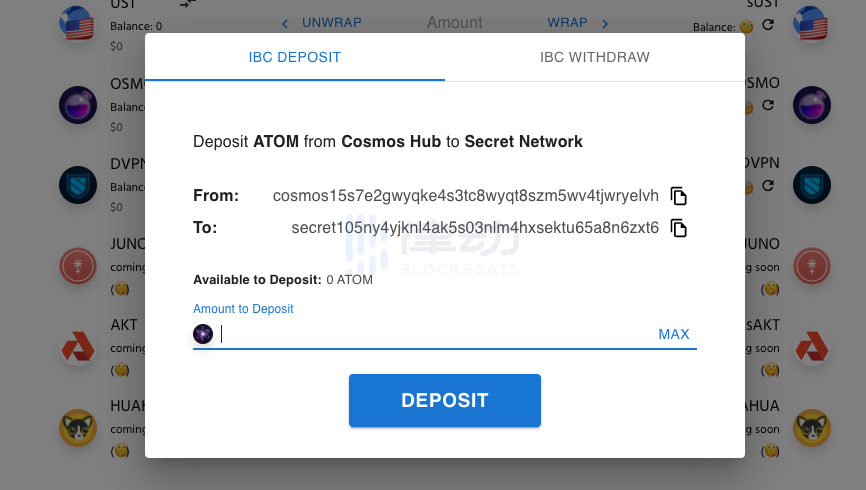
After depositing assets, you can directly click the WRAP button on the right to convert them into the privacy version of sToken.
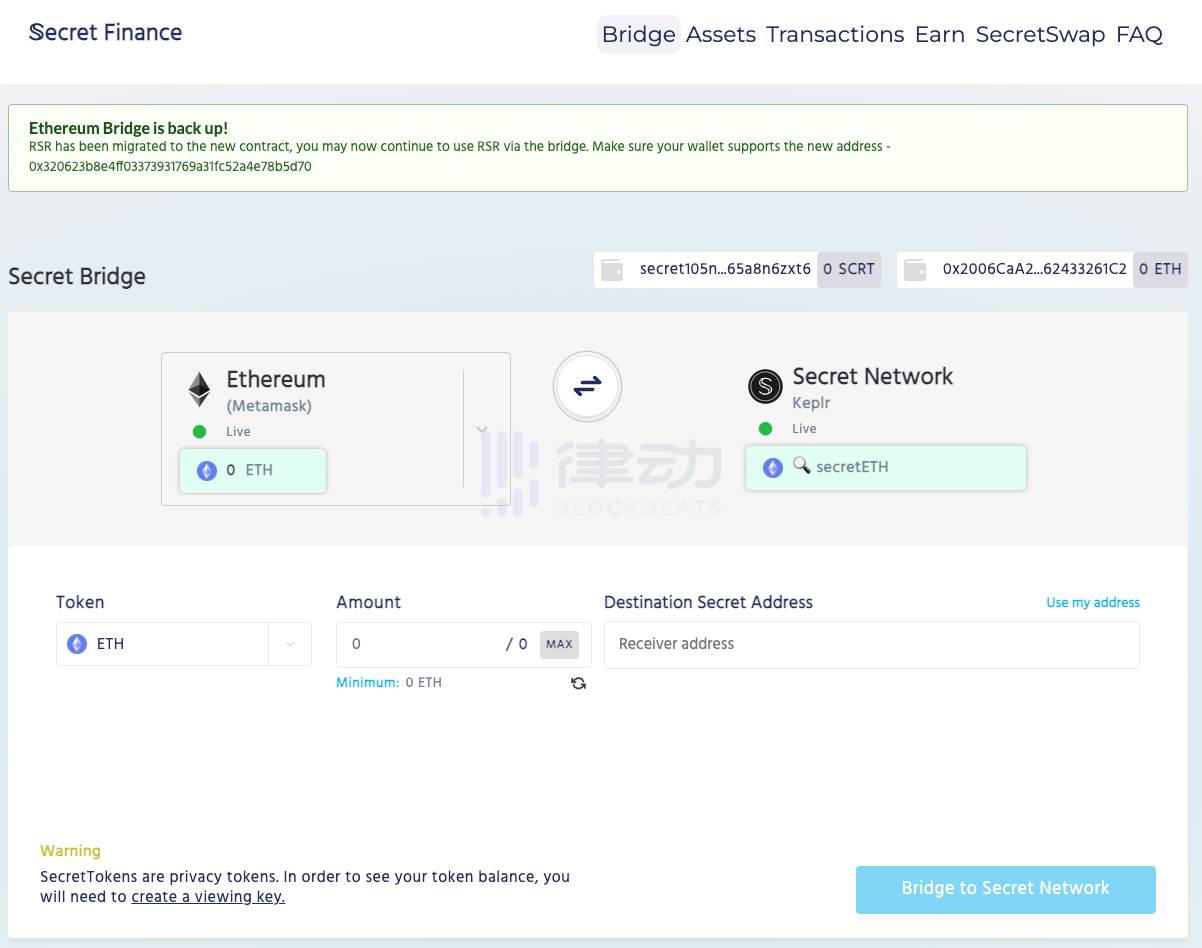
(2) Official Bridge (https://bridge.scrt.network/)
The official cross-chain bridge of Secret Network has already supported cross-chain assets from Ethereum, BSC, and Monero, and its cross-chain method is similar to that of ordinary cross-chain bridges, so we will not demonstrate it here.
Token Standards
Secret Network has established a unique privacy token standard, SNIP-20, which is modified from the CW-20 standard of the Cosmos ecosystem, primarily enhancing the privacy features of the original standard. Additionally, there is a SNIP-721 standard that supports privacy features for issuing privacy NFTs.
What is the Use of Programmable Privacy?
After the simple experience we just had, many readers may have noticed an important issue: operating these privacy applications is quite cumbersome.
We not only need to frequently transfer between the original Token and sToken but also constantly sign transactions to add Viewing Keys. But what is the purpose of all this complexity? Besides hiding how much money I have in my wallet (which seems unnecessary since I don't have much money), what else can Secret Network's privacy computing bring us?
1. Resistance to MEV
If you have ever traded on Ethereum, you must have heard of sandwich attacks. This occurs when you sign a transaction, and because the transaction is publicly visible in the mempool before it is packaged, miners and arbitrageurs can buy in before your transaction and sell after it, increasing your transaction costs.
In Secret Network, however, because transaction instructions can be hidden, neither miners nor arbitrage bots can extract MEV, resulting in users being able to buy the assets they need at truly fair prices.
2. Privacy NFTs
Privacy NFTs on Secret Network can similarly provide functions similar to sToken. For example, if you purchase a very valuable NFT, similar to CryptoPunk, and you are concerned about being targeted by phishing attacks after being discovered, you can choose to hide it to ensure the security of your asset, making it invisible to others at your public address.
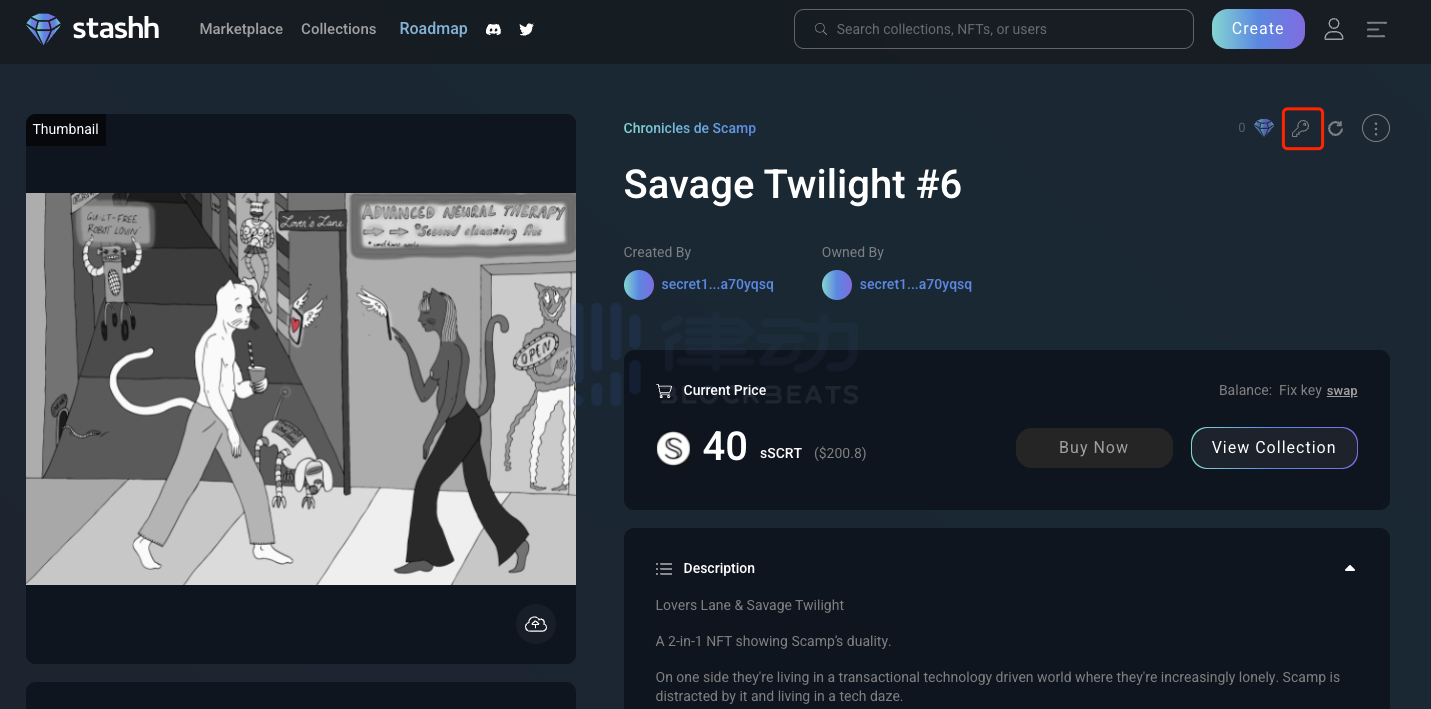
(Click the key button on the right side of the NFT you purchased to adjust whether to display ownership of this NFT)
At the same time, NFTs on Secret Network can also choose to encrypt the on-chain metadata. The NFT creator can specify that only the holder of the NFT can see the actual metadata address, displaying a clear image, while other addresses can only see a blurred image.
For example, on stashh, the largest NFT trading platform on Secret Network, we can click the age verification button on the left to browse privacy NFTs.
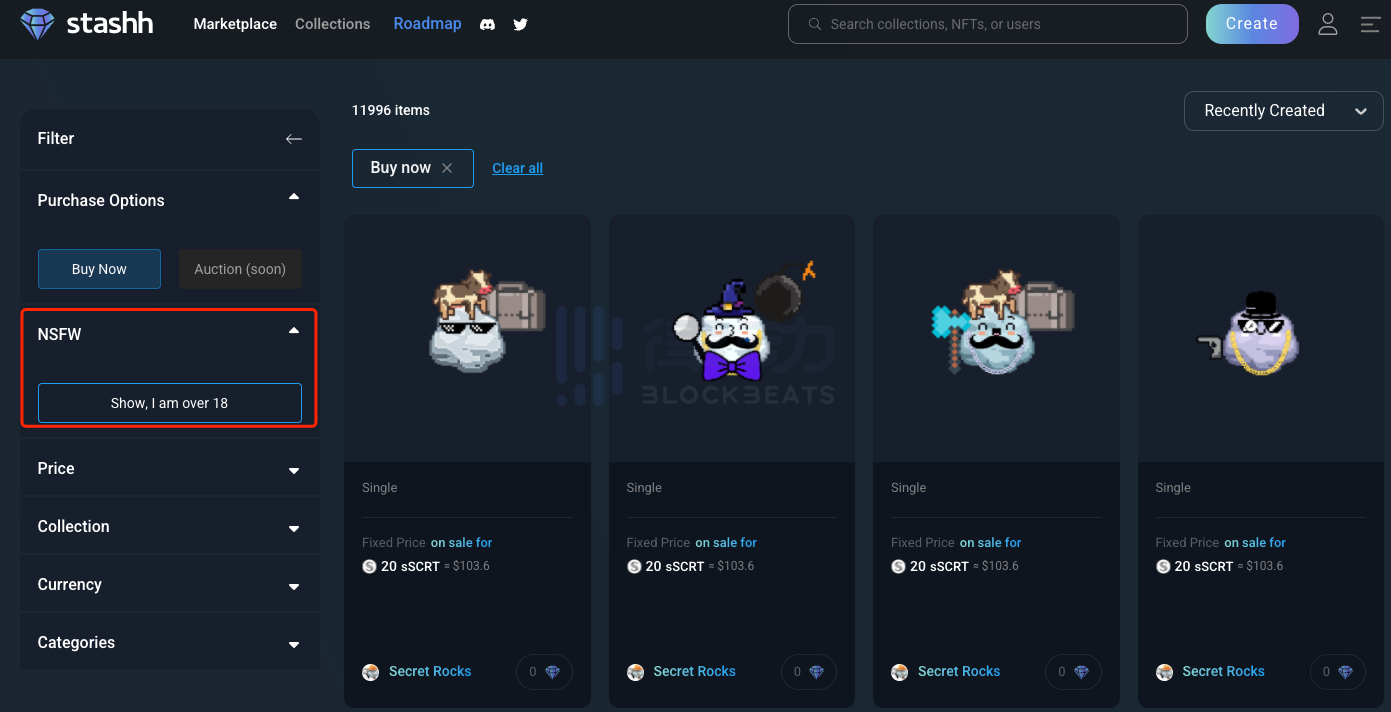
Before purchasing this type of NFT, users can only view a blurred image, and only after actually purchasing can they see the complete NFT metadata.
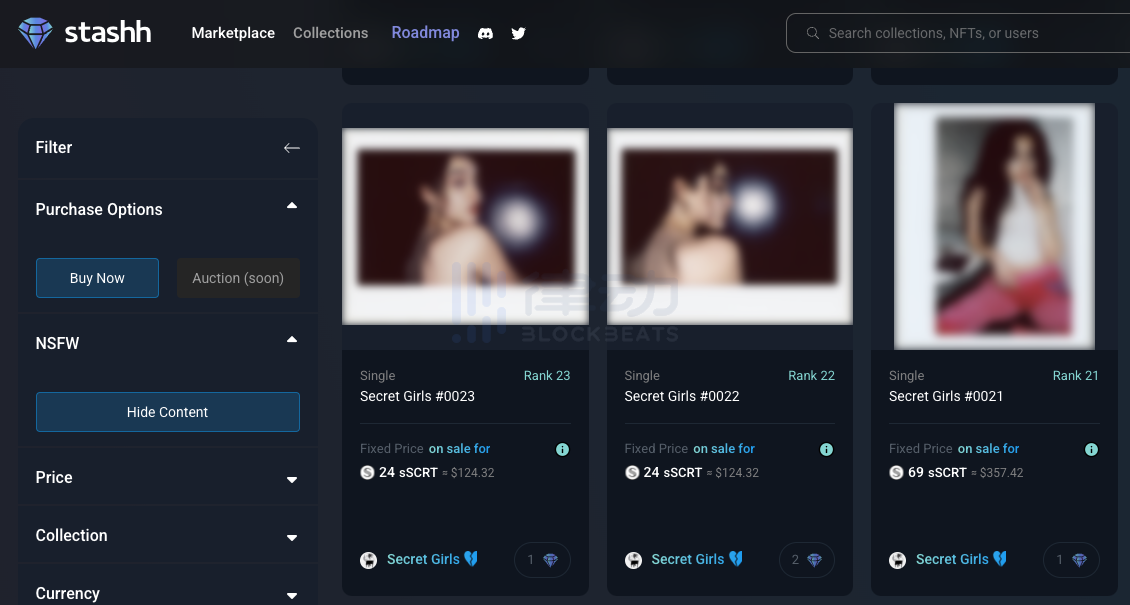
However, since these products are not cheap, I will not buy them here to demonstrate. Lastly, I would like to remind users who want to try to be cautious of scams, as the metadata of these NFTs is completely hidden, so you cannot know what is inside before purchasing.
What Are the Main Issues with Secret Network?
After the simple experience above, we have gained a relatively intuitive understanding of Secret Network. First of all, Secret Network has the basic functions that any smart contract platform possesses and also supports the deployment of common applications.
Currently, the Secret Network ecosystem includes decentralized trading platforms, various DeFi applications, as well as NFT minting and trading markets. If we do not consider the privacy token sToken, the experience is basically no different from traditional smart contract public chains.
However, its shortcomings are also quite evident: the sToken used to protect privacy has a significant impact on the user interaction experience. New users not only need to understand various new concepts related to privacy but also need to frequently switch between privacy tokens and non-privacy tokens. Without clear incentives or usage needs, ordinary users may find it difficult to continue using it.
Additionally, just recently, the DeFi application Shade Protocol on Secret Network distributed airdrops. As a result, it directly clogged the Secret Network, causing slow transaction confirmation speeds on the mainnet, and many users who withdrew SCRT from Osmosis to claim airdrops did not receive their cross-chain assets for one or two days.
One side had already paid the SCRT in Osmosis, while the other side could not receive it for a long time. This was also my first experience with such poor performance using IBC cross-chain (of course, this is mainly the responsibility of Secret Network). Although the team quickly conducted an emergency update, such transaction processing capability is still far from true large-scale usage.
In summary, Secret Network is still a public chain that is overall in the early stages of development. The ecosystem applications on it allow users to initially experience privacy computing products that can truly be implemented. However, the interaction experience still has many shortcomings and requires continuous development and improvement.










