Next bull market highlights: privacy public chain narrative and potential projects
Author: Biteye Core Contributor Fishery Isla
Editor: Biteye Core Contributor Crush
Many excellent teams have launched scaling solutions for Ethereum and the broader blockchain narrative, and scaling is not the only issue that needs to be addressed.
The next key feature to be implemented is privacy, which has recently become a hot topic in the primary market infrastructure investments.
This article will introduce two popular privacy chain technology routes: Zero Knowledge Proof (ZKP) and Fully Homomorphic Encryption (FHE), as well as potential projects worth following.
First, let's discuss a question: Does Web3 have any application scenarios for privacy?
01 Why Does Web3 Need Privacy?
Existing mainstream chains are public ledgers, where all transactions occur on-chain, meaning that state changes containing asset information related to addresses or accounts are publicly transparent.
Initially, information transparency was merely an ancillary feature set for supervising consensus security. However, as the industry has developed, consensus mechanisms have gradually been optimized for reliability, and public ledgers have increasingly become a feature serving technical arbitrage:
Miners can selectively package transactions based on fees, leading to lower-fee transactions having a lower likelihood of being processed, thus forcing users to increase Gas fees. More concerning is that miners or block producers can conduct front-running and censorship attacks by monitoring the public ledger.
By monitoring buy orders on the chain and placing their own buy orders before retail orders are filled, this leads to significant security issues. In the past year, MEV has successfully extracted nearly $2 billion from the market.
Such a massive and continuous outflow of funds poses a significant risk to the development of the crypto market.
At the same time, the lack of privacy support means users lose data ownership. Asset information and transaction details related to addresses can be monitored and exploited. This is contrary to the vision of Web3.
Therefore, once the scaling issue is resolved, privacy smart contract chains become the next urgent feature to be implemented.
To achieve privacy smart contracts, three technical routes are currently being pursued:
1) The TEE (Trusted Execution Environment) solutions represented by Secret Network and Oasis Network, which are already online but not very popular;
2) The zkVM solution that has entered the public eye through Ethereum zk-rollup based on the principle of ZK (Zero Knowledge Proof);
3) The FHE (Fully Homomorphic Encryption) solution that has only recently entered the market.
TEE technology is the most mature, with many related documents available. Interested readers can learn more on their own or experience the projects mentioned above. Therefore, this article will focus on the more talked-about zkVM and FHE solutions.
02 Zero Knowledge Proof
zkEVM vs. zkVM
Most ZK solutions fall into two camps: one built on Ethereum (zkEVM) and the other custom-built (zkVM), thus potentially choosing to construct a different underlying trade-off and foundational parameters.
zkEVM is a virtual machine compatible with the Ethereum Virtual Machine and friendly to zero-knowledge proofs, ensuring the correctness of programs, operations, inputs, and outputs.
By being built on the Ethereum blockchain, the zkEVM model absorbs both the advantages and disadvantages of Ethereum.
Since it optimizes compatibility with the Ethereum network, it benefits from Ethereum's large user base, making it easier for developers to build on this foundation (due to the large number of Solidity developers and the shared infrastructure, including execution clients).
However, this also means that its ability to integrate zero-knowledge proofs and other privacy measures is limited to the built-in constraints of the Ethereum network.
The closer the zkEVM model is to fully simulating the Ethereum model, the more performance trade-offs are required, as generating proofs takes longer.
Since all computations are completed on-chain, every transaction is completely public and transparent, which is beneficial for some applications but unreasonable or unsafe for others (e.g., applications related to sensitive personal financial information).
zkVM is a virtual machine that guarantees secure and verifiable trustworthiness through zero-knowledge proofs—when you input the old state and program, it will return the new state in a trustworthy manner. It can optimize the environment, making the integration of zero-knowledge proofs into on-chain transactions cheaper, more efficient, and even easier.
Essentially, the right zkVM allows all its applications to relatively easily use zero-knowledge proofs in every transaction. A true zkVM is built on a ZK-first principle and integrates it into every part of the tech stack.
Ethereum is originally a completely public and transparent blockchain; if developers now try to introduce privacy, its performance will certainly not match that of blockchains that have supported privacy from the start.
From an engineering perspective, this is challenging because developers must code programs that were not designed to run in such types of fields, leading to larger and more complex circuits.
Thus, the performance of zkVM will outperform zkEVM, making it a very worthwhile technology solution to watch.
Currently, there are already some projects using zkVM solutions that are emerging, such as L1: Aleo, Mina, etc.; L2: Aztec, etc. These projects have relatively high market expectations, and their participation cost-effectiveness is not high. Below is a more suitable zkVM project to watch.
Ola Network
Ola is a scalable privacy-preserving and compliance-optimized ZKVM Rollup platform, focusing on programmable privacy, scalability, and multi-language compatibility. Ola aims to become a universal Layer2 scaling solution that adds privacy protection and scalability capabilities to various programmable Layer1 blockchains.
Ola recently raised $3 million in seed funding, led by Web3 Ventures and Foresight Ventures, with participation from Token Metrics Ventures, J17 Capital, Skyland Ventures, LD Capital, and CatcherVC.
Ola's main products include the ZK-optimized virtual machine Ola-VM and the smart contract language Ola-lang.
Ola-lang is a general-purpose language developed based on ZK-VM, offering higher programmability. Developers can flexibly deploy any type of smart contract using Ola-lang, whether on public chains or enterprise-level private chains.
The ZK-optimized virtual machine Ola-VM uses a streamlined instruction set architecture, achieving better performance through complete ZK support and non-deterministic computation.
In simple terms, Ola is building a Layer2 infrastructure that combines optional privacy and programmability.
It allows public chains to inherit network security while obtaining privacy protection and performance scalability by deploying corresponding verification contracts.
This approach avoids sacrificing the programmability and decentralization features of public chains. Developers can add privacy and scalability solutions to different public chains as needed without making any changes on-chain.
This provides customizable privacy and scalability while maintaining the openness of public chains.
Currently, Ola has launched tasks in Ola Gala, allowing participants to gain eligibility for the 2024 Ola Public Testnet and receive rewards such as NFTs.
Additionally, on November 10, Ola's official website opened applications for the Devnet testnet. Developers may want to pay attention to this application, as selected participants can receive rewards, technical assistance, developer resources, and opportunities to deploy DApps on the Ola mainnet.
03 Fully Homomorphic Encryption
Fully Homomorphic Encryption is a new technology applied to blockchain and is one of the public chain solutions that institutions are particularly keen on following the recent popularity of ZK. As a new concept, there are currently few projects, and they are all in the early stages, making them very worthwhile to watch.
Fully Homomorphic Encryption is a publicly posed problem in the cryptography community that was raised long ago. As early as 1978, Rivest, Adleman, and Dertouzos proposed this concept with banking as the application background.
Compared to general encryption schemes that focus on data storage security, the most interesting aspect of homomorphic encryption schemes is that they focus on data processing security.
Specifically, homomorphic encryption provides a function for encrypting and processing private data. In a homomorphic encryption scheme, other participants can process private data, but the processing does not leak any original content. Users with the key can decrypt the processed data and obtain the correct result.
For example, if ALICE buys a gold bar and wants the worker to turn it into a necklace, is there a way for the worker to process the gold bar without getting any gold?
To solve this problem, ALICE can lock the gold bar in a sealed box with her only key. This box has two holes, each fitted with a glove, allowing the worker to process the gold bar inside the box while being unable to steal any gold.
Once the processing is complete, ALICE retrieves the entire box, unlocks it, and obtains the finished necklace.
Here, the box corresponds to the fully homomorphic encryption algorithm, while the worker's processing corresponds to executing homomorphic operations on the data without being able to access it.
Homomorphic Encryption Application Scenarios
In Web2, homomorphic encryption is almost tailor-made for cloud computing. Consider the following scenario: a user wants to process data, but their computer's computing power is too weak to obtain results in a timely manner. The user can use the concept of cloud computing to let the cloud help process the data and obtain results.
However, if the user directly hands over the data to the cloud, security cannot be guaranteed. Therefore, they can first use homomorphic encryption to encrypt the data and then allow the cloud to process the encrypted data directly, returning the processing results to the user.
In this way, the user pays the cloud service provider and receives the processed results, while the cloud service provider earns a fee. However, Fully Homomorphic Encryption also has limitations due to computational power:
High computational cost: Compared to traditional encryption, Fully Homomorphic Encryption requires more complex mathematical algorithms and larger ciphertexts, making operations on encrypted data slower and more resource-intensive.
Low computational efficiency: FHE (Fully Homomorphic Encryption) only supports arithmetic operations on encrypted data, such as addition, multiplication, and exponentiation. More complex functions, such as sorting, searching, or string operations, require more cumbersome processing before they can be executed, demanding high computational power.
Fortunately, we are in an era of explosive computational power. With the advancement of FHE and Web3 development, computational performance and costs are expected to align with the requirements of FHE. Thus, now is a good time to watch the FHE track.
Fhenix
Fhenix is the first blockchain to adopt Fully Homomorphic Encryption technology, providing encrypted data computation capabilities for EVM smart contracts.

The fhEVM used by Fhenix was initially developed by Zama, a cryptographic company building open-source encryption solutions for blockchain and artificial intelligence, and was integrated with Fhenix Network after a strategic partnership.
Additionally, Fhenix also utilizes Arbitrum's Nitro validators and Zama's fully homomorphic ring encryption Rust library tfhe-rsr, demonstrating the close relationship between Zama and Fhenix.
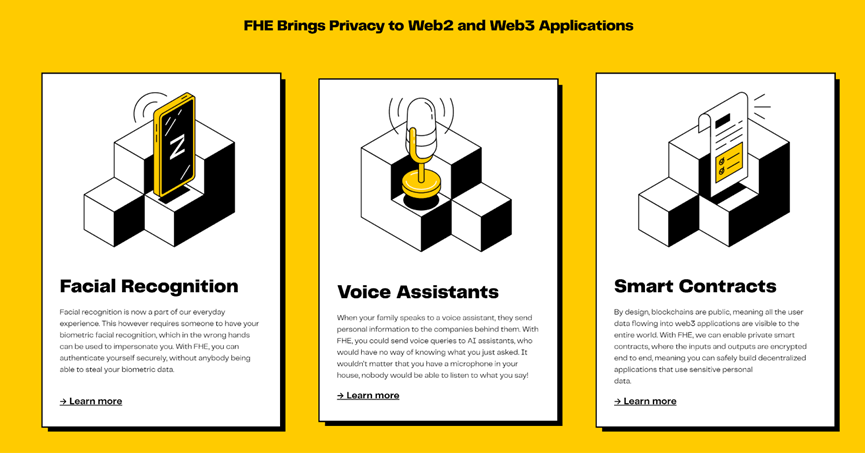
According to Zama's official website, the company is providing FHE-based Web3 solutions for some cutting-edge Web2 use cases, such as facial recognition, voice recognition, and smart contracts (which is what Fhenix is currently working on). We can expect Zama to integrate these applications into the Fhenix ecosystem in the future.
In September of this year, Fhenix raised $7 million in seed funding, led by Multicoin Capital and Collider Ventures, with participation from Node Capital, Bankless, HackVC, TaneLabs, Metaplanet, and Robot Ventures, including Tarun Chitra and Robert Leshner.
Compared to ZK, which can only verify the segments of data it encrypts and cannot merge private data from multiple parties, thus failing to facilitate most encrypted computations, FHE allows for a higher level of data security and supports unprecedented use cases through its "whole" encryption capabilities.
Therefore, having the ability to maintain privacy in Fhenix not only solves privacy issues but also paves the way for hundreds of new use cases—blind auctions, on-chain identity verification and KYC, tokenization of real-world assets, private voting for DAOs, and more.
04 Summary: Comparing ZK and FHE
After understanding the two cutting-edge privacy smart contract solutions, many readers may still be confused about the differences between Zero Knowledge Proof (ZK) and Fully Homomorphic Encryption (FHE).
The differences between the two, in addition to the flexibility of encryption mentioned above, also manifest in:
From a technical perspective, ZK focuses on proving correctness while protecting the privacy of statements; FHE emphasizes performing computations without decryption, protecting the privacy of data.
From the perspective of blockchain industry development, projects using ZK technology have developed earlier, from ZCash, which only had transfer functions, to the zkVM blockchain currently under development that supports smart contracts, compared to FHE, which has more technical accumulation in the blockchain industry; whereas FHE was theorized much later than ZK and has been a hot topic in academia, with Web3 projects using FHE technology for funding only emerging recently, thus starting its development later than ZK.
Both share a commonality in relying on the development of computational power, and the development of the privacy track enjoys the dividends of computational power explosion. It is precisely due to the increase in computational power in recent years that these cutting-edge technologies can truly reach users.
References
[01] Beyond ZK: The Definitive Guide to Web3 Privacy (Part 2)
https://scrt.network/blog/beyond-zk-guide-to-web3-privacy-part-2/
[02] Introduction to FHE: What is FHE, how does FHE work, how is it connected to ZK and MPC, what are the FHE use cases in and outside of the blockchain, etc.
https://taiko.mirror.xyz/2O9rJeB-1PalQeYQlZkn4vgRNr_PgzaO8TWUOM5wf3M
[03] Ola: A ZKVM-based, High-performance and Privacy-focused Layer2 platform
https://ethresear.ch/t/ola-a-zkvm-based-high-performance-and-privacy-focusedlayer2-platform/15248
[04] FHE-Rollups: Scaling Confidential Smart Contracts On Ethereum And Beyond -- Whitepaper
https://www.fhenix.io/fhe-rollups-scaling-confidential-smart-contracts-on-ethereum-and-beyond-whitepaper/









