First-Class Cabin In-Depth Report: Mask Network
Source: First Class Cabin Blockchain Research Institute
Project Overview:
The core vision of Mask Network is to become a portal that helps users seamlessly transition from Web 2.0 to Web 3.0, building a bridge to a new type of open network on the current internet. The team's vision is ambitious, but in the current industry, projects often need to focus on a specific point to gain a competitive advantage.
Currently, there are two main products: Maskbook and TesserPG. Maskbook integrates seamlessly with mainstream social software in the form of a plugin for Twitter/Facebook, enabling features such as sending encrypted messages, encrypted red envelopes, market display, and Uniswap trading integration, aiming to create an application ecosystem based on the Web 3.0 world.
In terms of usability, it continues the UI/UX of internet products, being user-friendly and lightweight. Early in the project's launch, it garnered attention and recognition from several opinion leaders in the blockchain industry, achieving a successful cold start. TesserPG is a cryptographic identity management system that can encrypt chat messages by using a mobile input method that encrypts user information in real-time; however, the project is currently on hold due to the team's development roadmap.
In terms of progress, Mask Network's code submission is good, and the product is undergoing continuous iteration.
Additionally, it should be noted that, according to official sources, Mask Network is expected to issue its governance token in early 2021. The value of the token can only be assessed after the team releases a specific economic model.
Currently, the Web 3.0 track is in its early stages, and there are no established, validated best practices. Although Mask Network appears to be of good quality overall, it still requires continuous attention to changes in this track and the competitive landscape.
1. Basic Overview
1.1 Project Introduction
Mask Network^[1]^ aims to be the bridge between Web 2.0 and Web 3.0 (with subfields of Web 3.0 including DID, NFT, DAO, DeFi, cross-chain, etc.), but it is still in a relatively early stage.
Unlike some projects, Mask Network does not attempt to "disrupt" existing centralized giants directly; instead, it provides tools that give the massive user base of existing giant platforms (such as Twitter and Facebook) an additional choice. It hopes to facilitate a smoother transition for users from Web 2.0 to the Web 3.0 era.
Strictly speaking, Mask Network is not a traditional blockchain project at this stage; it has no tokens and no chain. However, it is uniquely connected to blockchain and will be built on the Ethereum ecosystem in the future.
The vision of Web 3.0 has significant overlap with blockchain: embracing decentralization, power decentralization, resisting censorship, and data sovereignty. It involves utilizing existing networks and new decentralized network architectures (such as decentralized alternatives to HTTP and DNS) in a decentralized manner.
Mask Network has chosen several key directions to focus on within Web 3.0 (including but not limited to):
- Establishing decentralized digital identities to protect data ownership and usage rights;
- Ensuring the storage, privacy, and dissemination of text, images, and other information and files through cryptography and blockchain technology;
- Lowering the barriers to acquiring and managing digital assets, enhancing payment freedom, etc.
^[1]^ Mask Network was originally named "Maskbook," but due to brand restructuring and other reasons, it no longer uses "Maskbook" as the project name. The term "Maskbook" mentioned in this article refers to its plugin product.
1.2 Basic Information

2. Project Details
2.1 Team
The official website has not disclosed team members, but according to LinkedIn, its parent company Dimension has a total of 9 people, most of whom studied at the University of Illinois at Urbana-Champaign (UIUC).
2.2 Funding
Figure 2-1 Mask Network Investment Institutions
According to Block123, there are currently 21 investment institutions/individuals in Mask Network. In January and November 2018, investments were made by Fengrui Capital, Li Feng, and NGC/XOrder, Tony Tao, with specific investment amounts unknown. Additionally, the team completed a new round of financing led by HashKey and Hash Global on November 3, 2020, with the official disclosure stating that this financing was for 2 million USD.
2.3 Code
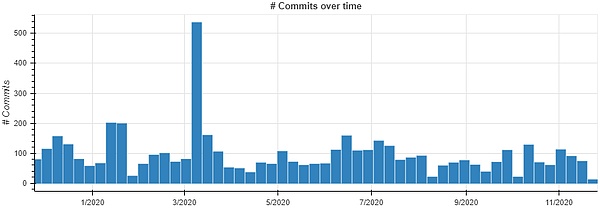
Figure 2-2 Mask Network Code Submission Status
From the above Figure 2-2, it is evident that Mask Network's code is updated frequently, maintaining a stable update pace over the long term, with Maskbook written in Typescript. Holoflows-Kit and Maskbook are both open-sourced under the AGPL V3 license.
2.4 Products
Mask Network has currently released two products, both of which are third-party plugin applications that can be used on internet giant platforms (such as Facebook, Twitter, WeChat) (the team refers to them as: DApplet, Decentralized Applet), with the main paradigm being to selectively encrypt content and information on the platform.
This achieves the effect of protecting users' private data, ensuring content and information are resistant to censorship and can be disseminated more freely. At the same time, it utilizes Holoflows-kit^[1]^ (a toolkit for developing browser extensions) to enhance interaction capabilities with the web.
In the initial design phase, Mask Network considered the current difficulty users face in leaving traditional social media, thus helping users achieve end-to-end encryption on any platform through the use of third-party plugins on traditional platforms.
This way, users do not need to leave their preferred software/platform and can leverage these existing social network platforms to complete a cold start, embedding privacy protection features. Mask Network applies blockchain technology, P2P networks, and does not rely on centralized APIs to ensure that the platform cannot be shut down and does not require permission from any platform.
Currently, based on this concept, there are two products: Maskbook and TesserPG.
Maskbook
Maskbook and TesserPG initially focused on encrypting text information and controlling access permissions, with the difference lying in the different stages of the information flow: Maskbook's encryption is in the front-end display, while TesserPG's encryption is in the upstream input stage. Later, Maskbook developed several other features based on this foundation: cryptocurrency wallet, Poll (voting), market display, and Uniswap trading access.
Maskbook is a browser plugin for private chatting, achieving data encryption through the encryption of chat messages. It has also added payment (sending red envelopes) and the ability to view CoinMarketCap market data and conduct Uniswap trades directly on Twitter.
Encrypted Communication
Currently, Maskbook has enabled users to send and receive encrypted posts with access control on Twitter and Facebook. Access control means that the information publisher can choose specific individuals to interpret their information. For those outside the selected range, they can only see meaningless ciphertext.
The encryption method uses mature encryption algorithms to ensure that the original information cannot be cracked for a considerable period in the future. By using asymmetric encryption algorithms, the target individuals provide their public keys for encryption, and specifically, the information receiver must also install the Maskbook plugin. Considering the regulated nature of ciphertext (from third-party platforms) and aesthetics, the team has also introduced ciphertext in the form of images and emojis.
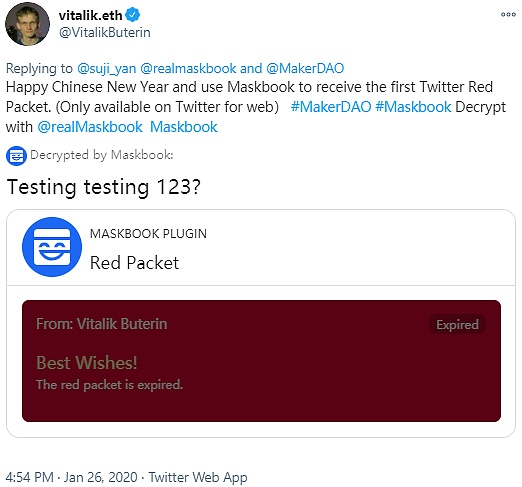
Figure 2-5 Vitalik Buterin Using Maskbook
Through practical testing, the red envelope sending feature of Maskbook is generally smooth, although it is limited by the congestion of the Ethereum network. Currently, the official has not disclosed public data on the frequency of red envelope usage.
Moreover, Vitalik Buterin used Mask Network to send ETH red envelopes during the Lunar New Year in 2020, bringing a wave of popularity to the project. Additionally, according to official team disclosures, many Mask users access through Twidere^[1]^, Mastodon^[2]^ and various third-party clients, having a large user base, although First Class Cabin has not yet obtained specific usage data for this part.
On the entry side, Maskbook has developed multiple adapted versions for different parts of the current internet ecosystem. Maskbook currently has first-party Chrome/Firefox extensions^[3]^, as well as Android and iOS applications.
There are also third-party social clients integrated into Mask Network, such as the Twitter third-party client Twidere; distributed social network Mastodon has two nodes^[mstdn.jp^]. In addition, the team will continue to seek third-party social network clients to integrate Maskbook.
Integration of Market Candlestick and Trading Based on Uniswap and 0x
Currently, Mask Network is enabling another new feature that allows users to view token price trends on CoinMarketCap or CoinGecko directly on Twitter and conduct Uniswap and 0x trades by connecting their wallets (as of now, most features have been implemented).

Figure 2-8 Maskbook New Feature Operation Example
Decentralized File Storage and Sharing Functionality
Users can upload and share all file types through Maskbook on Twitter and Facebook, permanently storing them in an encrypted form on Arweave (currently, Arweave's decentralized file storage function has been integrated into the Twitter plugin, and the team has also reached a preliminary cooperation with Sia recently).
The official statement indicates that this feature helps users share and communicate data more securely, conveniently, and quickly on social networks. Similarly, it can protect important user information, such as identity privacy and sensitive files, and Maskbook will also upgrade to unlock paid features in the future.

Figure 2-11 Maskbook Image Steganography
The above Figure 2-11 is an example of Maskbook image steganography, where the black dots in the background of the image represent the encrypted content.
Additionally, during the open-source summer event held by the Chinese Academy of Sciences, the image steganography of Maskbook was optimized by students from the University of Chicago. The image steganography function will be upgraded in the future to support users uploading any image for steganography.
TesserPG
TesserPG^[2]^ is a cryptographic identity management system that can encrypt chat messages by using a mobile input method that encrypts user information in real-time, essentially a mobile version of PGP. Currently, the project is temporarily on hold due to the team's development roadmap, but further development will occur in the future.
For example, when chatting on WeChat, you can use the TesserPG input method to first encrypt the message into garbled text before sending it through WeChat. The recipient copying the encrypted message will trigger the input method to automatically complete the decryption.
Then, the correct information will be displayed. This interaction scheme utilizes a native API on mobile devices, allowing the input method to remain in a floating layer, capable of detecting encrypted messages copied to the clipboard at any time. The encryption and decryption principles are identical to those of the Maskbook plugin.
^[2]^ Originally named TesserCube. The Mask team first used TesserCube as the project name to obtain Mozilla's Summer Grant, being the only domestic project to receive the grant. TesserPG is a product developed and iterated based on TesserCube.
^[3]^ ECMA International is an international membership organization for information and telecommunications standards, making significant contributions to global standardization in the information technology and telecommunications fields. Over its forty years, Ecma has established many standards for information and telecommunications technologies.
This includes the standard for JavaScript, the most important programming language in web development: ECMA Script. Additionally, hundreds of standards such as C#, Dart, and CD-ROM have also been established by Ecma. Approximately two-thirds of Ecma standards have been approved as ISO standards. Its members include Google, Intel, IBM, Microsoft, Apple, and others.
3. Future
Infrastructure Development
The team has basically built the infrastructure for Mask Network, which can now be put into practical use, but it has not yet reached a perfect state. Before it expands its ecosystem and gains widespread application, several challenges need to be addressed:
1) The high transaction fees and slow transaction speeds on Ethereum after going on-chain;
2) Using smart wallets to solve the new user experience challenges caused by private keys;
The team's future development roadmap is to create an application ecosystem based on the Web 3.0 world, similar to the current Chrome Web applications and WeChat mini-program ecosystem.
Personal Finance
In the future, the team plans to further introduce DeFi applications on platforms like Facebook and Twitter, enabling users to conduct virtual currency transactions, loans, copy trading, participate in token public offerings, issue personal tokens, and enjoy professional portfolio analysis without leaving traditional social networks.
The first version of the Mask Network financial application was launched on Twitter on September 24, which is a small plugin that integrates CMC price icons and Uniswap trading functions. The second version is expected to be released in December 2020, with new features including Initial Twitter Offering (ITO) on Twitter, yield aggregators, and portfolio analysis.
E-commerce
In the future, multimedia content and artworks are likely to be converted into different NFTs and stored in decentralized networks through decentralized storage solutions.
Therefore, the team plans to combine decentralized payment and decentralized storage functions (the team is currently storing data in Arweave, with specific implementation plans yet to be disclosed) and introduce privacy controls and anti-censorship features to promote changes in the distribution of multimedia content and the e-commerce model on the internet, further decentralizing user power.
Currently, NFT functionality has been preliminarily implemented, and the team has also conducted two activities: one is the NFT for the US election, and in early December, a design innovation exchange event between China and the Netherlands, where the team created an NFT promotional video for this event and posted it on Twitter. Additionally, the team will collaborate with Rarible in the future.
Strategic Partnerships
Mask Network recently announced partnerships with Phala Network (a privacy computing project based on Substrate), OmniLAB (best known for issuing the largest stablecoin USDT using OmniLayer), Loopring, Coinmarketcap, Arweave, Sia, 0x, and PlatON.
Multi-platform
Products like Maskbook may later integrate with well-known platforms like Reddit and Instagram to cover more Web 2.0 projects and users.
ITO (Initial Twitter Offering)
The team will also launch ITO—a product that allows institutions/individuals to issue tokens directly on Twitter, which will soon begin internal testing. Additionally, the team's future tokens may be issued directly on this application. This infrastructure allows any dapp to connect to existing web-based social networks.
Summary: Mask Network is developing well overall, with continuous product iteration. From the future path disclosed by the team, Mask Network is not just creating an encryption tool; it is currently developing more mini-programs to build an application ecosystem based on the Web 3.0 world.
4. Economic Model
Mask Network has not yet released an independent public chain, and according to official sources, it is expected to issue its governance token in early 2021, with specific details yet to be disclosed.
From the current major development direction of Mask Network, its vision has significant overlap with blockchain, so it may release a blockchain in the future, but the compatibility of its products/business with blockchain will be a test. In the DEFI market from Q2 to Q3 of 2020, we saw that some wallets, front-end displays, information aggregation tools provided users with practical and friendly functions and services.
One commonality among these tools is that their business serves other blockchain services but does not require them to create a blockchain to provide that service. Therefore, when considering the phenomenon of launching chains and tokens for such tools, we believe it is essential to focus on the compatibility of the released blockchain with the product and business itself, as well as its ability to capture business value through its tokens. The value of the tokens can only be assessed after the specific economic model design is released.
5. Competition
5.1 Industry Analysis
Overview
Mask Network is a bridge between Web 2.0 and Web 3.0. Its core is to help users seamlessly transition from Web 2.0 to Web 3.0, building a bridge to a new type of open network on the current internet.
A common explanation of Web 3.0 is that the information within websites can directly interact with information from other websites, allowing for the simultaneous integration of information from multiple websites through third-party information platforms; users own their data on the internet and can use it across different websites; fully based on the web.
Complex system functions that previously required system programs can now be achieved through a browser; user data is audited and synchronized with network data. The vision of Web 3.0 is to enable everyone to control their (digital) identity, assets, and data, thereby controlling their destiny.
Current Situation
The team's current approach resembles developing individual Dapplets (similar to WeChat mini-programs) and then integrating them into their platform in the future, much like the current Chrome Web applications and WeChat mini-program ecosystem. Currently, Mask Network's plugin applications are innovative, but there are too many innovative Dapps on the market, and how to convert its advantages into more significant industry competitiveness to accumulate a larger user base and become a traffic entry point for future Web 3.0 is key.
Mask Network's vision is great but ambitious. In the current Web 3.0 ecosystem, it encompasses decentralized digital identity (DID), decentralized applications (Dapp), decentralized autonomous organizations (DAO), decentralized storage, decentralized communication and computing, cross-chain, and other fields.
In the current industry, projects often need to focus on a specific point to gain a competitive advantage. The team is involved in a wide range of fields, but currently, only the decentralized digital identity (Decentralized Identity, DID) track within the Web 3.0 field has a certain competitive edge. Other fields are still in the exploratory phase. Therefore, this chapter will focus on the competitive situation in the DID track.
5.2 Competitive Project Comparison
Due to the broad scope of Web 3.0, the competitive products section only lists the areas currently primarily involved by Mask Network for comparison.
MetaMask
Currently, when discussing wallet plugins, one cannot overlook MetaMask. MetaMask is a multifunctional browser-based wallet, RPC client, and basic contract browser. It can be used on Chrome, Firefox, Opera, and Brave Browser.
At first glance, MetaMask appears to be a browser-based wallet. However, unlike other browser wallets, MetaMask injects Web 3.0 instances into the browser, serving as an RPC client connected to various Ethereum blockchains. It can inject Web 3.0 instances and act as an entry point for external RPC services, making MetaMask a very powerful tool for developers and users^[1]^.
Currently, Mask Network is still some distance away from leading plugin wallets like MetaMask. However, Mask Network's clever point is that it has not directly competed with ecosystems like Ethereum but has chosen to build user-friendly tools and services within the ecosystem first.
From the initially complex and difficult-to-use Bitcoin full node wallet to the PC-based Metamask, and then to more simplified mobile products like the Metamask mobile app and imToken, the form of cryptocurrency wallets has continuously evolved with the industry's development needs. We cannot predict which will be superior in the future, but one thing is certain: products are continuously iterating, and only those that can adapt to user needs are good products.
To compete with leading projects, the primary focus must be on having a core product that accumulates users.
Decentralized Digital Identity (DID)
With the continuous integration of digital life and the physical world, we can obtain vast amounts of free information daily, supported by the internet infrastructure that enables numerous powerful applications, connecting the entire world.
However, the current web also has some issues: user data is fragmented across isolated islands, requiring repeated authentication across different institutions; personal data is stored on centralized servers of institutions, making it vulnerable to personal identity data leaks, etc.
Therefore, it is essential for users to manage their digital identities themselves, possessing a unified and unique DID. Compared to traditional web, the advantages of DID lie in its decentralized nature, with personal identity data stored in a distributed manner, avoiding control by a single centralized institution; identity is self-sovereign, based on DPKI (Distributed Public Key Infrastructure).
Individuals can autonomously manage their identity data; trustworthy data exchange allows users to upload their identity data to the blockchain, breaking the traditional internet data island problem and achieving data interoperability across multiple information systems without requiring users to repeat authentication.
Both DID and the core goals of Web 3.0 aim to allow users to control their data, protect their privacy, and ultimately ensure their freedom through an open, censorship-resistant network, thereby empowering users. DID serves as an identity card in the blockchain world and may become the infrastructure of blockchain, enabling more people to own and use DID, which is beneficial for understanding and utilizing blockchain technology.
DID has evolved and derived from traditional centralized identities. The transition from centralized identity to DID has gone through the following four stages^[2]^:
The first stage: "Centralized Identity," where data is managed and controlled by a single central institution;
The second stage: "Federated Identity," where multiple institutions or alliances jointly manage user identities;
The third stage: "User-Centric Identity," where the core principle is that everyone should have the right to control their digital identity, currently at this stage, but in reality, users have not fully gained control over their identity;
The fourth stage: "Decentralized Digital Identity (DID)," where a trusted environment is created based on blockchain's distributed ledger and cryptographic algorithms, allowing users to fully control their identity data and provide trusted identities to others.
Overall, DID is still in a very early industry stage and has not received much attention in the blockchain field. Compared to the hype surrounding expansion, cross-chain, and DeFi this year, its popularity is incomparable. However, as one of the core applications of Web 3.0, DID has certain potential for the future.
According to relevant research institutions, in 2018, the market size for identity management based on blockchain technology was approximately 107 million USD. It is expected that from 2020 to 2024, the global blockchain identity management market will grow to 4.61 billion USD, with a compound annual growth rate of 82% during this forecast period.
The main driving factors for the market include increasing concerns about the security of existing models globally, growing demand for vertical industry blockchain identity solutions, and heightened awareness of self-sovereign identity.
BlockStack
The BlockStack project is a distributed computing network built on the Bitcoin blockchain, overcoming the limitations of the Bitcoin blockchain and establishing a new distributed naming and storage system. Decentralized applications (DApps) built on BlockStack primarily perform most of their business logic and data processing on the client side.
Rather than on centralized servers. The BlockStack team is dedicated to creating a complete ecosystem for decentralized digital identity and decentralized personal data storage based on Web 3.0. Its fundraising complies with US SEC regulations, and according to its official data, there are currently over a million registered users on BlockStack, with hundreds of Dapps, but most of these Dapps are simple applications like gambling games and do not represent true Dapps.
Related Technologies
The Stacks blockchain serves as the foundation for the entire network, employing a tunable proof-of-work mechanism and optimizing security and predictability using a new smart contract language, allowing for static analysis of all transactions.
Gaia is a highly scalable and high-performance decentralized storage system that provides users with a private data locker; the BlockStack authentication protocol is a decentralized authentication protocol within the system, allowing users to authenticate using their ID and set which Gaia server to use for data storage; SDKs and developer tools simplify DApp development, allowing developers to avoid concerns about server or database operation issues.
MY KEY
MYKEY is a self-sovereign identity system based on multiple public blockchains, built on the Key ID self-sovereign identity protocol.
Related Technologies
MYKEY has three main functions: multi-chain wallet, trust network, and reliable data storage.
1) Multi-chain wallet: MYKEY is a multi-chain wallet (currently, due to the immaturity of cross-chain technology, MyKey primarily uses centralized cross-chain methods. It involves a centralized third party pledging assets on one chain and issuing assets on another chain, with the cross-chain process occurring when the third party pledges and issues assets, without any message exchange between the two chains), allowing users to fully control their assets and freeze and recover accounts if they lose their private keys;
2) Trust network: In the trust network, each identity account will receive several verifiable claims from other identity accounts and can also make any number of verifiable claims about other identity accounts. Through these verifiable claims, identity accounts can mutually verify each other, ultimately forming a unified trust network;
3) Reliable data storage: User data is based on decentralized storage technology and controlled by smart contracts. User data is entirely controlled by the owner of the identity account, and others cannot access it without permission.
MYKEY aims to return data sovereignty to users, fundamentally protecting user privacy.
Microsoft DID
In May 2019, Microsoft launched Microsoft DID on the Bitcoin network, aiming to better prove user identities through blockchain technology.
Related Technologies
The Microsoft DID solution can be broken down into three parts: Sidetree, ION, and DID, corresponding to the protocol layer, network layer, and application layer, respectively, with a hierarchical construction relationship.
1) Sidetree: Protocol layer, which can be deployed on the Bitcoin and Ethereum networks, as well as other blockchain networks. Currently, it is only deployed on the Bitcoin network;
2) ION: An open-source network based on the Sidetree protocol, ION merges a large number of DID operations into a single on-chain operation through batch merging on a Layer 2 network, and achieves trusted storage of DID data by storing data in IPFS and placing the hash of the data on the Bitcoin network;
3) Application layer: Unique identifier (a unique identifier); associated DID document (an associated DID Document). The former is a label for the latter, which contains information such as what the DID can authorize and in which services the DID can be used.
5.3 Web 3.0 Related Technologies
Currently, many projects have emerged in the Web 3.0 track, and this article only lists a few of the aforementioned projects for illustrative purposes. Overall, the Web 3.0 track is still in a relatively early stage, and the corresponding infrastructure has not been fully established.
The author personally believes that the future development of the Web 3.0 track is positively correlated with the development of decentralized storage, privacy computing, and cross-chain technologies to some extent. Non-technical aspects must also consider regulatory issues, shifts in user ideology, and business models.
Decentralized Storage
Digital identity is a concept in cyberspace, referring to a set of data that describes a person or thing, or the totality of all information available about a person on the internet. It is an online identity adopted by individuals, organizations, or electronic devices in the network, or a network identity. The data related to Web 3.0 requires suitable storage methods for trusted storage.
Traditional data storage methods face data security and privacy issues associated with centralized identity management, and decentralized cloud storage is one of the solutions to this problem.
Currently, First Class Cabin has identified four projects capable of storing data in the decentralized cloud storage track: Filecoin, Storj, Arweave, and SiaCoin^[1]^ . These projects are still primarily in the development stage. As an important component of Web 3.0, the development of decentralized cloud storage technology will have a certain impact on the implementation of Web 3.0.
Currently, all files uploaded and shared by Maskbook on Twitter and Facebook are permanently stored in an encrypted form on Arweave.
Privacy Computing
At this stage, the cryptographic aspects of privacy computing mainly include three major technical directions: Full Homomorphic Encryption (FHE), Secure Multi-Party Computation (sMPC), and Zero-Knowledge Proof (ZKP). Additionally, there are directions such as Trusted Execution Environment and Indistinguishability Obfuscation.
Security is the primary issue that needs to be addressed for the development of blockchain and Web 3.0. Web 3.0 needs to develop usability based on data security. Privacy computing transforms data through cryptographic means to prevent leaks, ensuring efficient data flow while addressing the current issue of data exposure on the internet. However, overall, privacy computing technology currently has low efficiency, and practical commercial applications are limited.
Cross-Chain
Currently, users' digital identity information is often stored in different departments/industries/enterprises, and their respective digital identity systems are not interconnected.
The same person's information is in an "information island" phase across different centralized systems. Based on the current development of blockchain and distributed ledgers, it is foreseeable that breaking down "information islands" and achieving interaction between different chains will be inevitable in the future. How Web 3.0 meets users' cross-chain interaction needs will depend to some extent on the development of cross-chain infrastructure.
From the perspective of cross-chain infrastructure development, Web 3.0 has various technical solutions for handling cross-chain asset transfers. In the future, it is also expected to gain support from cross-chain networks like Cosmos and Polkadot for achieving cross-chain connectivity between businesses and information.
5.4 Competitive Analysis
Mask Network belongs to the Web 3.0 project, and it is not appropriate to directly compare it horizontally with other blockchain Web 3.0 projects.
We believe that Web 3.0 will be a very important infrastructure in the future blockchain world, and there are currently no established, validated best practices. We view it as similar to the Lego blocks of DEFI; smart Web 3.0 projects will choose to connect to large ecosystems in the early stages rather than create their own ecosystem (based on this, we do not favor projects following the BlockStack route), to assist rather than compete.
Because given the current scale of Web 3.0, it is difficult and insufficient to compete directly with traditional Web and win mainstream user recognition. Mask Network and My Key have not directly competed with ecosystems like Ethereum but have chosen to build user-friendly tools and services within the ecosystem first.
Moreover, a crucial element of Web 3.0 is the user base. From this perspective, Mask Network and My Key each start from plugin tools and wallets, accumulating user bases and industry recognition, which is a good initial strategy. The Web 3.0 track is in its early stages, and projects like Mask are continuously iterating, requiring ongoing attention to changes in the track and competitive landscape.
5.5 Industry Outlook
For decades, the internet has been developing towards increasing centralization and monopoly. Now, as people slowly realize that free platforms like Facebook, which profit through advertising, are manipulating and exploiting users, the awareness of user-centric approaches to liberate the Web from the control of giant corporations and address current issues of privacy, security, and performance through decentralized networks is growing.
The decentralized and open internet of Web 3.0 is a future worth pursuing and has attracted countless developers to strive for it. Although the Web 3.0 industry is still immature and faces numerous challenges and difficulties, this does not overshadow the immense potential of the industry.
Its development momentum is undeniable, and the shift in global user preferences will drive Web 3.0 to a turning point. Perhaps at some point in the future, we will witness a large-scale migration of users from currently dominant monopolistic platforms to distributed consensus systems.
The future of the Web 3.0 industry is promising. Finally, returning to Mask Network, its continuous innovation in launching various Dapplets certainly has its considerations.
However, how to secure a place in the Web 3.0 ecosystem should focus more on "point-to-surface" rather than "surface-to-point." How to form its core competitiveness, retain more users on its platform, become an entry-level application for Web 3.0, and design a complete business model are all key points for future development.










