OKX & SlowMist Joint Release|Bom Malware Sweeps Thousands of Users, Stealing Assets Exceeding 1.82 Million USD
On February 14, 2025, multiple users reported that their wallet assets were stolen. Through on-chain data analysis, the stolen cases all exhibited characteristics of mnemonic phrase/private key leakage. Further follow-up with the affected users revealed that most of them had installed and used an application called BOM. In-depth investigation indicated that this application was actually a carefully disguised scam software, through which criminals induced users to authorize access, illegally obtaining mnemonic phrase/private key permissions, and subsequently executing systematic asset transfers and concealment. Therefore, the SlowMist AML team and the OKX Web3 security team investigated and disclosed the methods used by this malicious software, conducting on-chain tracking analysis in hopes of providing safety warnings and advice to more users.

1. Malware Analysis (OKX)
With user consent, the OKX Web3 security team collected some APK files of the BOM application from users' phones for analysis. The specific details are as follows:
(1) Conclusion
- The malicious app, upon entering the contract page, deceives users into authorizing local file and photo album permissions under the pretext of needing these permissions for the app to function.
- After obtaining user authorization, the application scans and collects media files from the device's photo album in the background, packaging and uploading them to the server. If the user's files or album contain mnemonic phrases or private key-related information, criminals may use the information collected by the application to steal the user's wallet assets.
(2) Analysis Process
1. Preliminary Sample Analysis
1) Application Signature Analysis
The signature subject is irregular, parsed as adminwkhvjv, which is a meaningless string of random characters; normal applications typically have a meaningful combination of letters.

2) Malicious Permission Analysis
In the AndroidManifest file of the application, a large number of permissions are registered, including some sensitive permissions such as reading and writing local files, reading media files, and accessing the photo album.

2. Dynamic Analysis
Due to the app's backend service being offline during the analysis, the app could not run normally, and dynamic analysis could not be performed.
3. Decompilation Analysis
After decompilation, it was found that the number of classes in the app's dex was very small, and static analysis was conducted on these classes.

The main logic involves decrypting some files and loading the application:

In the assets directory, uniapp product files were found, indicating that the app was developed using the cross-platform framework uniapp:

The main logic of applications developed under the uniapp framework is in the product file app-service.js, with some key code encrypted in app-confusion.js. We primarily started the analysis from app-service.js.
1) Trigger Entry
At the entry of each registered page, an entry named contract page was found.
The corresponding function index is 6596.

2) Device Information Initialization Reporting
The callback onLoad() after the contract page loads will call doContract().

In doContract(), initUploadData() will be called.

In initUploadData(), it first checks the network status and also checks whether the image and video lists are empty. Finally, it calls the callback e().

The callback e() is getAllAndIOS().
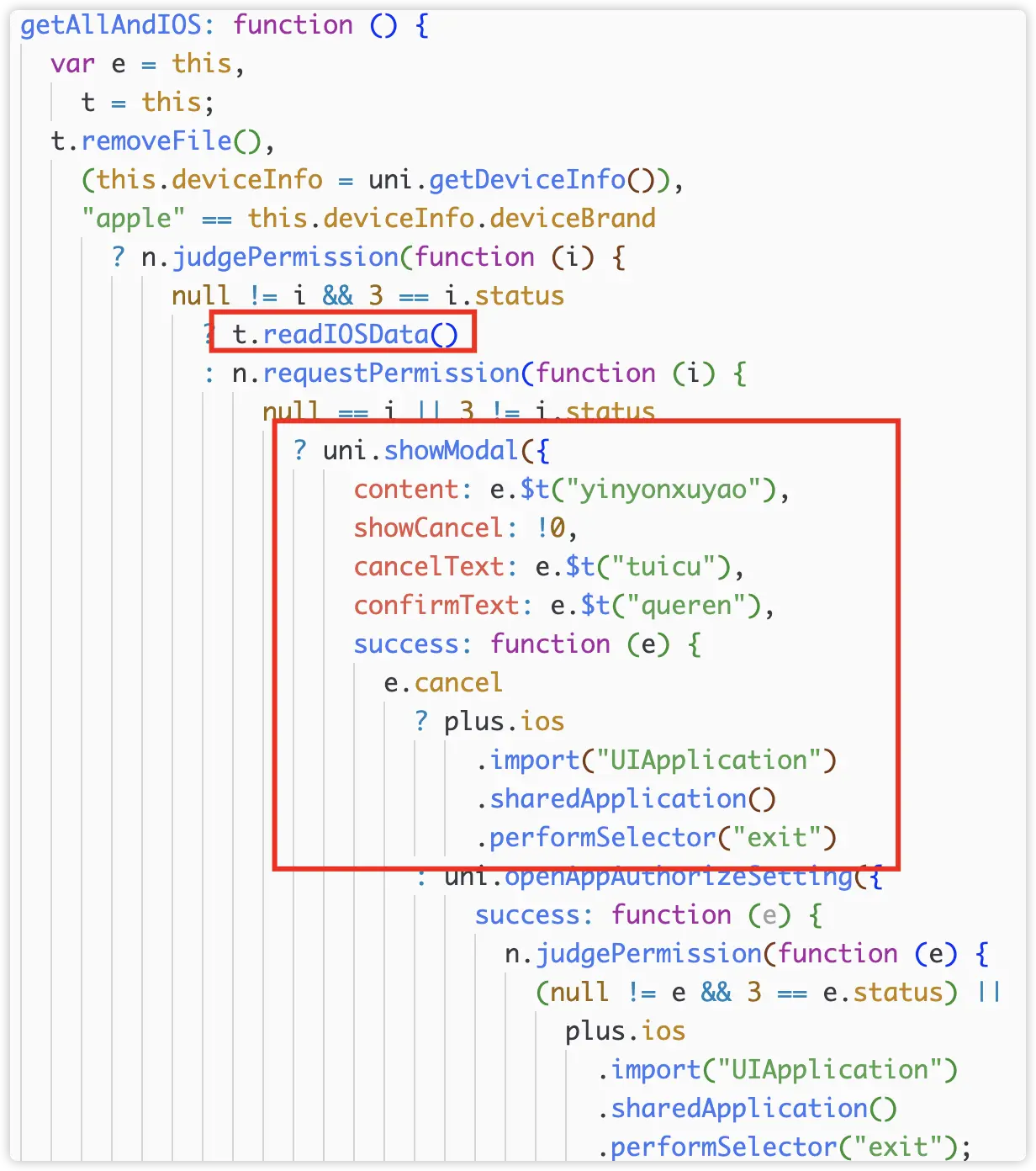
3) Check and Request Permissions
Here, on iOS, it first requests permissions and deceives users into agreeing with wording that suggests the app needs these permissions to function normally. This request for authorization is quite suspicious; as a blockchain-related application, its normal operation is not inherently linked to photo album permissions, and this request clearly exceeds the normal requirements for app operation.

On Android, it similarly checks and requests photo album permissions.

4) Collect and Read Photo Album Files
Then, in androidDoingUp, it reads images and videos and packages them.
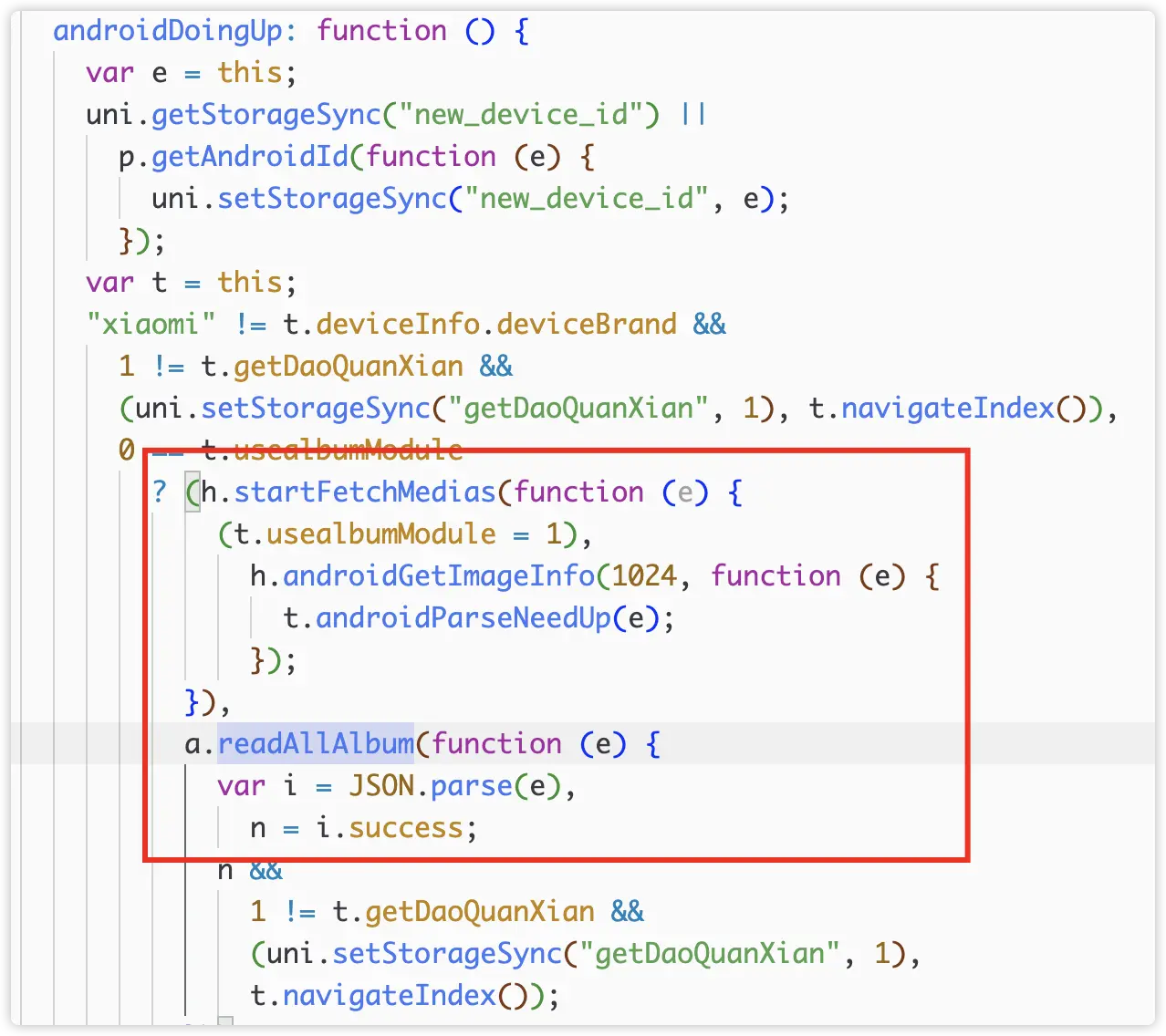
5) Upload Photo Album Files
Finally, in uploadBinFa(), uploadZipBinFa(), and uploadDigui(), the upload is performed, and it can be seen that the upload interface path is also a string of random characters.


The iOS process is similar; after obtaining permissions, it starts collecting and uploading content through getScreeshotAndShouchang().

6) Upload Interface
The commonUrl domain in the reported URL comes from the return of the /api/bf9023/c99so interface.

The domain of this interface comes from the local cache of uniapp.

No code for writing to the cache was found; it may be encrypted and obfuscated in app-confusion.js. During a historical run, this domain was seen in the application cache.

2. On-Chain Fund Analysis (SlowMist)
According to analysis by SlowMist AML's on-chain tracking and anti-money laundering tool MistTrack, the main address for stealing coins (0x49aDd3E8329f2A2f507238b0A684d03EAE205aab) has stolen funds from at least 13,000 users, profiting over $1.82 million.

(https://dune.com/queries/4721460)

The first transaction of address 0x49aDd3E8329f2A2f507238b0A684d03EAE205aab appeared on February 12, 2025, with an initial fund of 0.001 BNB transferred from address 0x9AEf1CA082c17f9D52Aa98ca861b50c776dECC35:

Analyzing address 0x9AEf1CA082c17f9D52Aa98ca861b50c776dECC35, its first transaction also occurred on February 12, 2025, with initial funds coming from an address marked by MistTrack as "Theft-盗取私钥" (theft of private keys) 0x71552085c854EeF431EE55Da5B024F9d845EC976:

Continuing to analyze the flow of funds from the initial hacker address 0x49aDd3E8329f2A2f507238b0A684d03EAE205aab:
BSC: Profiting approximately $37,000, including USDC, USDT, WBTC, etc., frequently using PancakeSwap to exchange some tokens for BNB:

Currently, the address has a balance of 611 BNB and tokens worth approximately $120,000, such as USDT, DOGE, and FIL.

Ethereum: Profiting approximately $280,000, mostly from ETH transferred from other chains, then transferring 100 ETH to 0x7438666a4f60c4eedc471fa679a43d8660b856e0. This address also received 160 ETH transferred from the aforementioned address 0x71552085c854EeF431EE55Da5B024F9d845EC976, totaling 260 ETH that has not yet been transferred out.
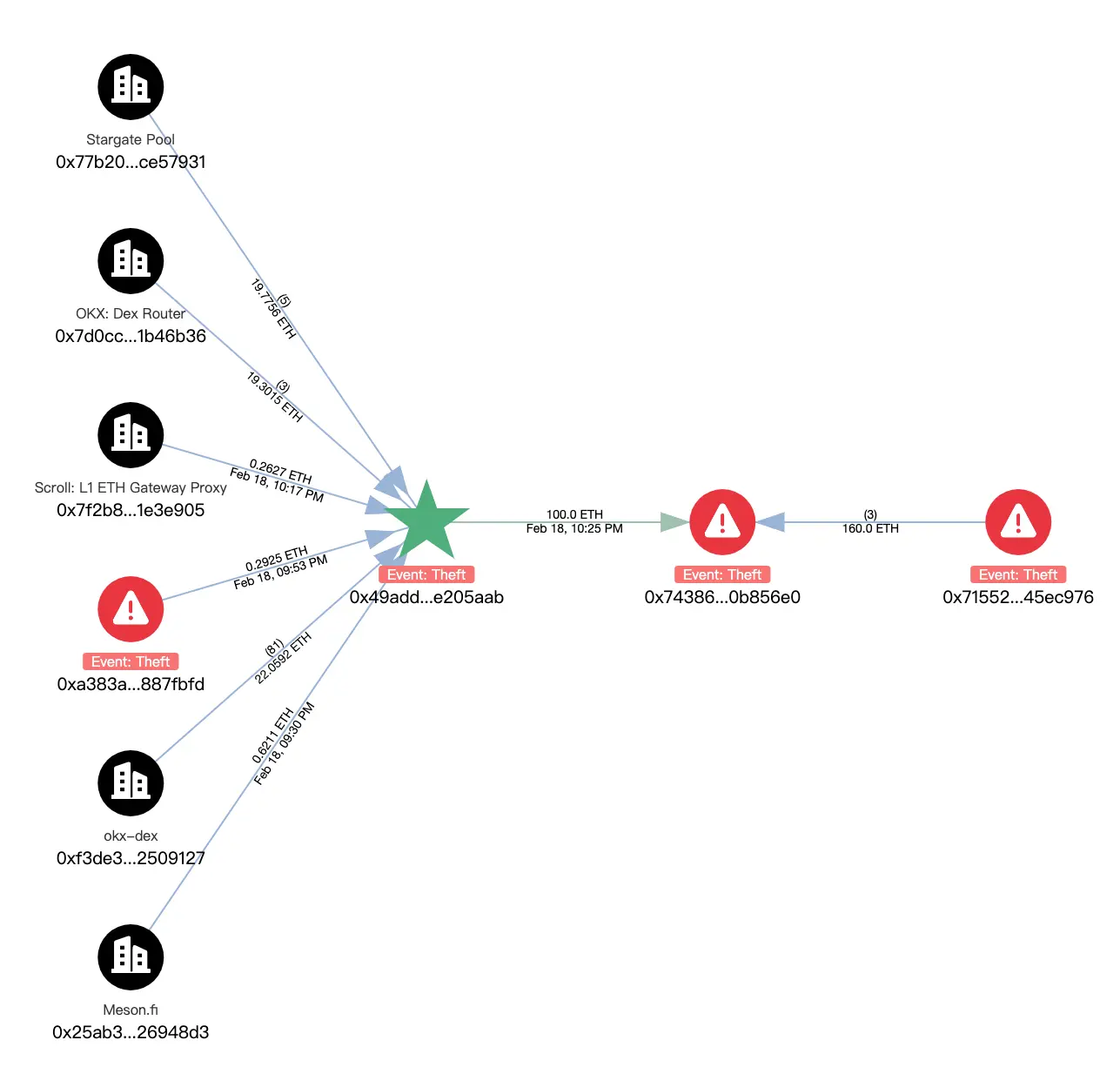
Polygon: Profiting approximately $37,000 or $65,000, including WBTC, SAND, STG, etc. Most tokens have been exchanged for 66,986 POL through OKX-DEX. The current balance of the hacker address is as follows:

Arbitrum: Profiting approximately $37,000, including USDC, USDT, WBTC, etc. Tokens were exchanged for ETH, with a total of 14 ETH transferred across chains to Ethereum via OKX-DEX:

Base: Profiting approximately $12,000, including FLOCK, USDT, MOLLY, etc. Tokens were exchanged for ETH, with a total of 4.5 ETH transferred across chains to Ethereum via OKX-DEX:

Other chains will not be elaborated on. We also conducted a brief analysis of another hacker address provided by victims.
The hacker address 0xcb6573E878d1510212e84a85D4f93Fd5494f6EA0 had its first transaction on February 13, 2025, profiting approximately $650,000, involving multiple chains. The related USDT was transferred across chains to the TRON address TFW52pZ3GPPUNW847rdefZjqtTRxTCsdDx:

Address TFW52pZ3GPPUNW847rdefZjqtTRxTCsdDx received a total of 703,119.2422 USDT, with a balance of 288,169.2422 USDT, of which 83,000 USDT was transferred to address TZJiMbiqBBxDXhZXbrtyTYZjVDA2jd4eus and has not been transferred out. The remaining 331,950 USDT was transferred to an address that had previously interacted with Huionepay, THKqT6PybrzcxkpFBGSPyE11kemRNRmDDz.

We will continue to monitor the relevant balance addresses.
3. Security Recommendations
To help users enhance their protective awareness, the SlowMist AML team and the OKX Web3 security team have compiled the following security recommendations:
- Never download software from unknown sources (including so-called "arbitrage tools" and any software from unknown issuers).
- Do not trust download links for software recommended by friends or communities; always download from official channels.
- Download and install apps from legitimate channels, such as Google Play, App Store, and major official app stores.
- Properly store mnemonic phrases; do not use screenshots, photos, notes, cloud storage, etc., as storage methods. The OKX wallet mobile app has already prohibited screenshots of private key and mnemonic phrase pages.
- Use physical methods to store mnemonic phrases, such as writing them down on paper, storing them in hardware wallets, or segmenting storage (splitting mnemonic phrases/private keys and storing them in different locations).
- Regularly change wallets; periodically changing wallets can help eliminate potential security risks.
- Utilize professional on-chain tracking tools, such as MistTrack(https://misttrack.io/), to monitor and analyze funds, reducing the risk of encountering scams or phishing incidents and better safeguarding asset security.
- Strongly recommend reading the ++"Blockchain Dark Forest Self-Defense Manual"++ written by SlowMist founder Yu Xian. Link.
Disclaimer
This content is for reference only and does not constitute or should not be viewed as (i) investment advice or recommendations, (ii) an offer or solicitation to buy, sell, or hold digital assets, or (iii) financial, accounting, legal, or tax advice. We do not guarantee the accuracy, completeness, or usefulness of such information. Digital assets (including stablecoins and NFTs) are subject to market fluctuations, involve high risks, and may depreciate, even becoming worthless. You should carefully consider whether trading or holding digital assets is suitable for you based on your financial situation and risk tolerance. For your specific circumstances, please consult your legal/tax/investment professionals. Not all products are available in all regions. For more details, please refer to OKX's Terms of Service and Risk Disclosure & Disclaimer. The OKX Web3 mobile wallet and its derivative services are governed by separate terms of service. You are responsible for understanding and complying with applicable local laws and regulations.