Q3 Security Quarterly Report Revealed | On-chain losses across the network reached 740 million USD, with nearly 50% stemming from phishing scams
Author: OKChain
In Q3 2024, the total losses across the network amounted to approximately $743 million, an increase of 58% compared to the previous quarter. A total of 110 major attack incidents occurred, including 61 cases of fraud and phishing, resulting in losses of $340 million, accounting for 46.03% of the total.
According to OKLink data, losses due to private key leakage amounted to approximately $270 million, accounting for 36.06%. REKT incidents resulted in losses of about $80.42 million, accounting for 10.78%. RugPull incidents caused losses of approximately $4.61 million, accounting for 0.62%.

During July and August, there were significant losses of about $300 million each month, while total losses in September suddenly dropped by 57%. Nevertheless, challenges remain due to security risks such as phishing incidents and private key leaks, which pose significant threats due to their high randomness. OKLink reminds everyone to enhance their security awareness and not to trust any unverified signature requests, especially when authorizing "Permit" or involving fund transfers, and to always verify the authenticity of signatures.
At the same time, properly safeguard your private keys and mnemonic phrases, and never disclose them to anyone, nor store them through screenshots or on insecure devices.

Largest Security Incident - Phishing Scam
On August 19, a potential victim reportedly lost 4,064 BTC, worth approximately $238 million, due to a phishing attack. This substantial amount was quickly transferred through multiple platforms such as ThorChain, eXch, Kucoin, ChangeNow, Railgun, and Avalanche Bridge after being stolen.
Largest Security Incident - Private Key Leakage
On July 18, WazirX exchange suffered a loss of approximately $235 million due to the leakage of multi-signature wallet private keys.
Largest Security Incident - REKT
On September 3, Penpie was attacked due to a reentrancy vulnerability in its reward protocol, resulting in losses of approximately $27.34 million.
Largest Security Incident - RugPull
On July 21, ETHTrustFund experienced a RugPull, stealing approximately $2 million worth of cryptocurrency on Base.
Case Analysis
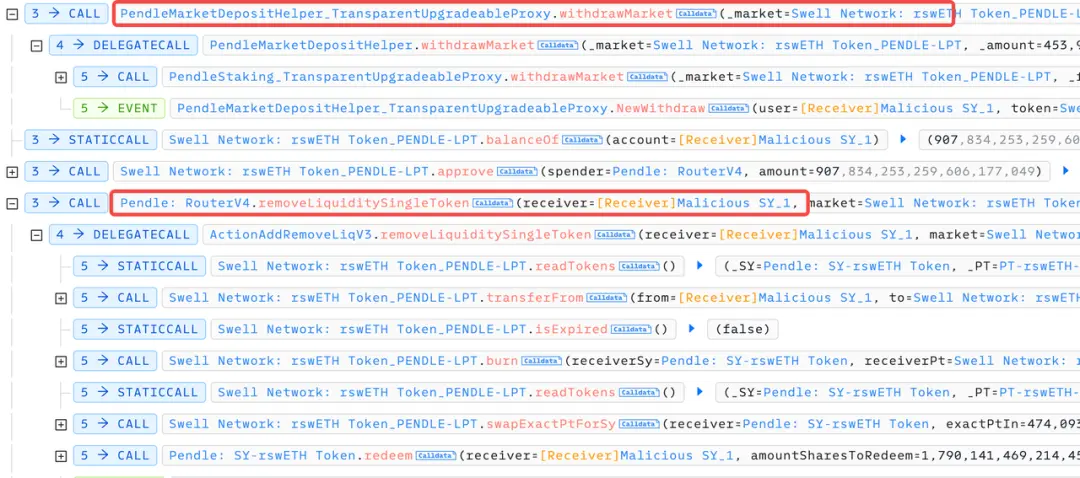
On September 3, the Penpie contract suffered a reentrancy attack, where the attacker added liquidity to the contract during the reentrancy phase to impersonate the reward amount, thereby obtaining the existing reward tokens within the contract. The asset loss reached $27.34 million.
- The attacker created a malicious SY1PENDLE-LPT market on the Pendle protocol using a malicious SY1 token contract. Subsequently, the attacker used this malicious SY1PENDLE-LPT market to create a new collateral pool on Penpie and deposited a large amount of SY1_PENDLE-LPT tokens into that pool;

- The attacker obtained a large amount of wstETH, sUSDe, egETH, and rswETH tokens through a flash loan and deposited them into the SY1 token contract as rewards generated by the SY1 token contract. Then, they called the Penpie.batchHarvestMarketRewards function, which would trigger the claimRewards function of the SY1 token contract, expecting to obtain reward tokens from the SY1 token contract;

- However, in the claimRewards function of the SY_1 token, the attacker exploited the reentrancy vulnerability of the Penpie protocol to deposit the wstETH, sUSDe, egETH, and rswETH tokens obtained from the flash loan into the corresponding Pendle market, and deposited the LP tokens obtained into the Penpie protocol.
Since this operation occurred during the call to the Penpie.batchHarvestMarketRewards function, Penpie mistakenly treated these newly deposited tokens as reward tokens and sent these incorrectly calculated reward tokens to the RewardDistributor contract. Because the attacker was the only depositor in this malicious Pendle market, they could obtain all the rewards;

- Finally, the attacker redeemed all Pendle-LP tokens from Penpie, then redeemed wstETH, sUSDe, egETH, and rswETH tokens from Pendle and repaid the flash loan.
OKLink Tips
OKLink reminds users to carefully verify on-chain addresses when performing on-chain operations to avoid losses due to address tampering. It is recommended to regularly check and revoke contract authorizations that are no longer in use to prevent malicious contract abuse. Utilize on-chain tools to ensure operational security; OKLink provides features such as token authorization queries, address monitoring, and contract comparisons to easily manage token authorizations and keep contract risks under control.
Maintain rationality when facing high-yield projects, especially those lacking transparency or audit reports, to avoid falling into RugPull and REKT traps.










