DeFi ecosystem security panorama
Author: BlockSec
Introduction
As DeFi continues to reshape the financial landscape, security remains a significant challenge faced by the DeFi ecosystem, with security issues causing billions of dollars in asset losses each year.
According to Chainalysis, DeFi hacks in 2023 resulted in over $1.1 billion in asset losses. Although this figure has decreased compared to 2022, new trends in DeFi attacks have emerged in 2023. For instance, well-known protocols that have operated securely for a long time, such as Curve and KyberSwap, have also been attacked. Additionally, complex attacks targeting infrastructure vulnerabilities (such as Flashbots Relay) have surfaced.
The Security Incident Dashboard data shows that over 50 hacking incidents causing losses of over $100,000 occurred in the first half of 2024.
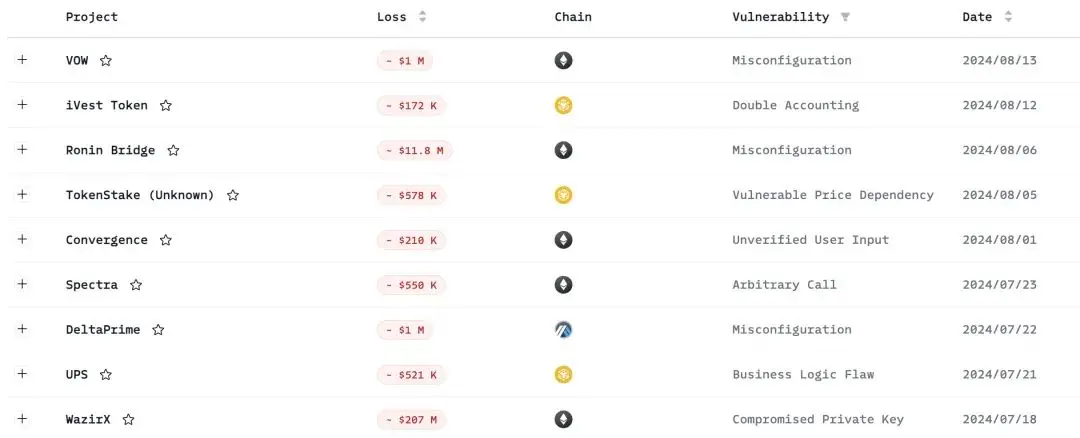
Recent Hacking Incidents
(Source: Security Incident Dashboard)
https://app.blocksec.com/explorer/security-incidents
Security is crucial for the development of DeFi protocols. Some protocols manage billions of dollars in user assets, and security incidents can lead to significant losses for users. While in some cases, stolen funds can be (partially) recovered (e.g., the Euler attack incident), we cannot rely solely on this hope. Each attack undermines user confidence in DeFi.
Despite the industry's many proposed measures to enhance security, there is still considerable room for improvement in DeFi security. On a positive note, code auditing has become a community consensus, with most protocols undergoing audits before launch, which helps reduce the risk of attacks caused by smart contract vulnerabilities. However, relying solely on code audits is far from sufficient to address all security issues. Code audits cannot prevent attacks caused by contract upgrades, configuration changes, and vulnerabilities introduced by external dependencies. Given these limitations, some protocols have begun to adopt more proactive solutions, such as operational monitoring and attack detection systems.
In this article, we will overview the security measures that protocols can take from the Pre-Launch, Post-Launch, to Attack Response stages to understand the DeFi security landscape. We will detail each type of security measure and its main vendors/products, along with their advantages and disadvantages. We hope this article can help the community better understand the current state of DeFi security and inspire innovative security solutions.
DeFi Security Landscape
Security measures for DeFi protocols should span the entire lifecycle from pre-launch to post-launch, ensuring the security of the protocol itself and during its operation. Additionally, it is crucial to deploy preventive measures and response plans in advance against potential attacks. To help readers clearly understand the current DeFi security solutions, we categorize the relevant vendors (products) into the following categories.
Pre-Launch Security
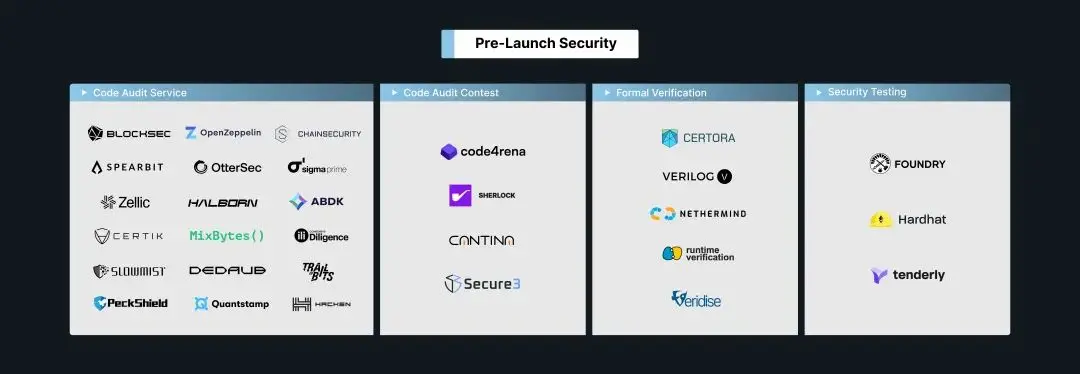
Security measures that can be taken before the protocol launch include code audits, formal verification, and security testing.
Code Audit Services & Competitions
Code auditing is a widely recognized practice for ensuring protocol security within the community. During this process, security companies conduct semi-automated reviews of the frozen code, scanning for common vulnerabilities automatically and then manually reviewing complex vulnerabilities. Representative auditing companies include OpenZeppelin, ChainSecurity, BlockSec, etc.
Additionally, there are auditing competition platforms. Unlike auditing companies that directly provide auditing services, these platforms publicly release auditing requirements, attracting security researchers from the community to participate in auditing competitions, with rewards distributed to participants who discover protocol vulnerabilities. Auditing competition platforms include Code4rena, SHERLOCK, Cantina, Secure3, etc., with differences in severity levels of vulnerabilities, reward distribution, and participation standards across platforms.
Code auditing is the first line of defense for protocol security. However, it also has some limitations, which is why many protocols audited by well-known companies still fail to avoid hacker attacks.
First, static code audits cannot address security issues arising from protocol dependencies, and the composability of DeFi protocols exacerbates this issue.
Second, during the code auditing process, some issues may not receive sufficient attention. For example, precision loss is a common issue that may be overlooked by auditors and protocol parties. It wasn't until the Hundred Finance and Channels Finance incidents occurred that the community fully recognized the security implications of precision loss.
Finally, high-quality code auditing remains a scarce resource, requiring interdisciplinary talent with knowledge in security, finance, and computer science, and currently, few universities can consistently and extensively provide such talent. Therefore, some protocols, despite being audited, have auditors who lack sufficient expertise.
Formal Verification
"Formal verification uses mathematical methods to prove the correctness or incorrectness of a system based on a certain formal specification or property." Formal verification can ensure that the behavior of DeFi protocols conforms to formal specifications. For example, Certora's Prover can perform formal verification on DeFi protocols. Developers provide rules (specifications), and Prover explores every possible program state, comparing the results with the rules to identify vulnerabilities. The greatest advantage of formal verification is its ability to mathematically prove the correctness of DeFi protocols managing billions in assets. However, some limitations in practical applications hinder its widespread adoption.
- First, specifications need to be provided by developers, which requires them to have detailed documentation of the expected behavior of the protocol, and most developers are not experts in this field.
- Second, frequent upgrades of protocols may require updating specifications and re-evaluating the protocol, which some protocols may not be able to afford in terms of time and effort. Despite these limitations, we still believe that protocols should undergo formal verification, especially new protocols that have not been time-tested and manage large amounts of user assets. However, enhancing the operability of formal verification and increasing its adoption rate remains a significant challenge.
Security Testing
Security testing identifies potential issues within the protocol through test cases. Compared to formal verification, which proves the correctness of the protocol using mathematical methods, security testing generally uses specific input data (rather than symbolic input in formal verification), making it more efficient but slightly less comprehensive.
Foundry is a popular smart contract development testing framework. Developers can execute tests in Foundry and perform differential testing, invariance testing, and regression testing on DeFi protocols. Other security testing tools include Tenderly and Hardhat.
Post-Launch Security

Security measures that can be taken after the protocol launch include Bug Bounty, attack detection, and operational monitoring.
Bug Bounty
Bug Bounty builds a bridge between protocols and security researchers. Protocols publish bounty programs on Bug Bounty platforms, detailing the scope of the bounty and reward amounts, while security researchers can earn rewards by reporting zero-day vulnerabilities in the protocol. Immunefi is a representative Web3 Bug Bounty platform.
Attack Detection
Attack detection platforms identify malicious transactions by scanning trades. Specifically, these platforms scan every transaction interacting with the protocol to look for malicious behavior, triggering alerts when malicious transactions are identified.
For example, BlockSec Phalcon scans every mempool and on-chain transaction, identifying malicious behavior (such as malicious contracts and proposals) by analyzing the behavioral characteristics of transactions. It acts like a security guard, tirelessly monitoring every detail of each transaction for unusual activity. It extracts behavioral patterns from these transactions and uses financial models (similar to those used by banks to detect fraud) to identify potential attacks. Similar systems include products offered by Hypernative and Hexagate. Additionally, Ironblocks' Venn Security Network provides a decentralized infrastructure capable of aggregating detection results from multiple sources.
Operational Monitoring
As the name suggests, operational monitoring frameworks oversee the operational security of protocols after launch. For example, they can monitor real-time changes to administrator keys, the deployment and updates of smart contracts, and automatically detect security vulnerabilities in pull requests. The OpenZeppelin Defender platform helps developers securely write, deploy, and operate smart contracts. BlockSec Phalcon can monitor contract upgrades, Safe wallet transactions (such as initiation, new signatures, execution), access control, and governance-related risks. Furthermore, through the real-time monitoring system Forta Network, users can create bots to monitor protocols or subscribe to existing bots to receive alerts about security threats like phishing.
Attack Response
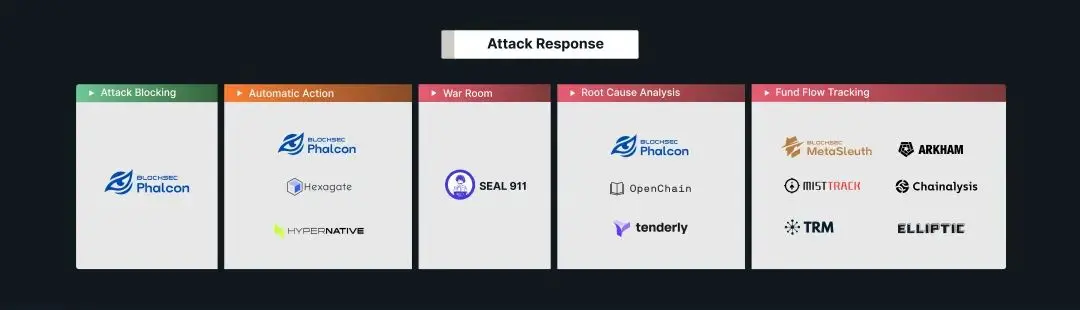
Security measures that are automatically triggered or urgently taken after an attack occurs include attack blocking, automatic response, War Room, cause analysis of the attack, and tracking the flow of funds of the attacker.
Among these five response measures, attack blocking is particularly noteworthy because project teams can deploy it in advance to block attacks before they occur, reducing losses to zero. Automatic response platforms also help minimize losses caused by attacks.
Establishing a War Room, conducting cause analysis of the attack, and tracking the flow of funds are response measures taken after an attack occurs. While these measures help reduce losses and prevent similar attacks in the future, they may have already caused significant losses that are difficult to recover. Additionally, damage to the project's reputation and loss of user trust can have far-reaching negative impacts. Risks seem omnipresent and difficult to guard against, but project teams do not have to respond passively; they can deploy preventive measures in advance, which is a more recommended approach.
Attack Blocking
Attack detection is an important channel for knowing about hacker attacks, but to combat hacker attacks, detection alone is not enough. Without automated attack blocking capabilities, manual response measures often come too late. For example, in the cases of KyberSwap, Gamma Strategies, and Telcoin, these protocols took response measures only minutes or even hours after the attacks began, during which hackers initiated multiple attack transactions, stealing substantial assets. The Velocore and Rho attacks in July caused the Linea and Scroll chains to halt operations, raising user concerns about the centralization issues of L2 chains.
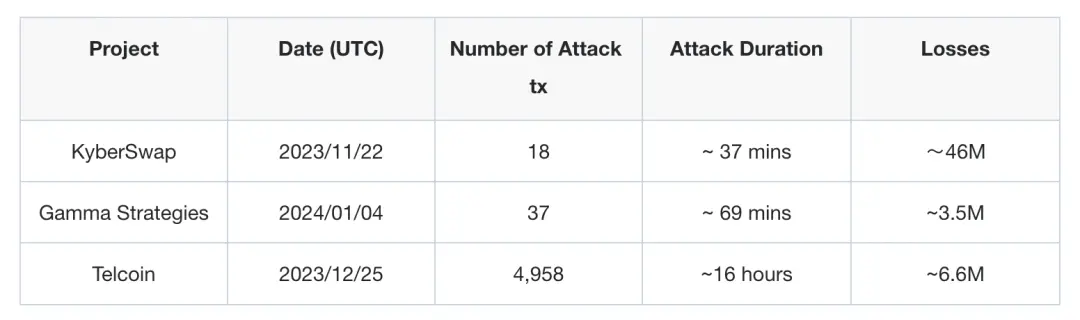
Attack blocking can automatically prevent hacker attacks, relying on two core technologies: early detection and automatic front-running. Early detection refers to identifying which transactions are attack transactions while they are still in the mempool stage, before they are recorded on-chain. Automatic front-running involves submitting a front-running transaction to pause the protocol before the attack transaction is recorded on-chain, thereby preventing the execution of the attack transaction. This method blocks the attack before it actually occurs, thus avoiding losses.
In this category, BlockSec Phalcon is the only product that possesses these core technologies. After a hacker initiates an attack transaction, Phalcon's attack monitoring engine can detect this transaction in advance, pushing attack alerts to users while automatically front-running to pause the protocol, reducing losses to zero. The attack blocking capability of this product has been validated in over twenty past white-hat rescues, saving over $20 million in assets.
Automatic Response
In addition to attack blocking platforms, platforms like Phalcon, Hexagate, and Hypernative can also automatically respond when an attack occurs.
By subscribing to such platforms, users can set up monitoring and response measures for various protocol risks. If a transaction hits the monitoring rules, the system will automatically initiate the response measures that the user has previously set (such as pausing the protocol), thereby reducing losses. However, some platforms lack attack detection engines, meaning the system cannot directly identify attack transactions and inform users; instead, users need to define the conditions under which a transaction can be deemed an attack. Given the complex characteristics of attack transactions and the fact that users (often contract developers) may not possess sufficient security knowledge, this poses a significant challenge for users.
War Room
Establishing a War Room is particularly crucial when a protocol is under attack. This helps the protocol grasp the situation, synchronize information with the community in a timely manner, and effectively integrate resources to take response measures, requiring close collaboration among experts from multiple fields.
SEAL 911 aims to "help users, developers, and security researchers directly contact trusted security experts in emergencies." Users can access this service through the SEAL 911 Telegram Bot (https://t.me/seal911bot) to quickly assemble a War Room to address security challenges when a project is attacked.
Cause Analysis of the Attack
When a protocol is attacked, it is crucial to identify the root cause of the problem, such as vulnerabilities within the smart contract and how those vulnerabilities were exploited. Analyzing attack transactions requires the use of certain tools, with Phalcon Explorer, OpenChain, and Tenderly being good choices.
Tracking the Flow of Funds
Tracking the flow of funds refers to on-chain tracking of the attacker's initial funds and profits from the attack to locate relevant addresses and entities. If these assets flow to centralized entities (such as centralized exchanges and other institutional entities), law enforcement can be contacted to help freeze the funds.
Chainalysis, TRM Labs, ARKHAM, ELLIPTIC, and MetaSleuth are representative companies/products in this field. For example, MetaSleuth can automatically track cross-chain fund flows and provide rich address tagging. ARKHAM has established a community where protocol parties can publish investigation bounties to incentivize community members to assist in tracking the flow of the attacker's funds.
Security Education Resources

Knowledge is the best defense. In addition to the security vendors and products mentioned earlier, there is another category of roles that are crucial for DeFi security: educational platforms. The resources or information provided by these platforms can help DeFi practitioners and users deepen their understanding of security knowledge, enhance security awareness, and develop security skills, playing an important role in promoting the development of DeFi security. We pay tribute to these platforms and share the following noteworthy ones.
- SΞCURΞUM: A Discord community focused on Ethereum security, regularly hosting smart contract security competitions called "Secureum RACE." https://x.com/TheSecureum
- Security Incidents Dashboard: This platform aggregates and updates in real-time attack incidents with losses exceeding $100,000, providing detailed information such as loss amounts, affected chains, types of vulnerabilities, cause analysis of attacks, and PoC. https://app.blocksec.com/explorer/security-incidents
- Rekt: Known as the dark web of DeFi news, it provides in-depth analysis of DeFi vulnerabilities, hacks, and scams. https://rekt.news/
- RugDoc: A DeFi security and education community. This platform provides project risk assessment information and features a platform called RugDocWiKi that introduces the DeFi ecosystem and technology. https://rugdoc.io/
- DeFiHackLabs: A Web3 security community dedicated to helping Web2 security talent transition into the Web3 space, with over two thousand members and nearly two hundred white-hat hackers globally. DeFiHackLabs' repository offers a wealth of learning resources. https://x.com/DeFiHackLabs
- Solodit: This platform collects past audit reports from Web3 auditing companies. https://solodit.xyz/
- Ethernaut: A Web3/Solidity-based game where players need to identify vulnerabilities in Ethereum contracts, resembling a CTF format. https://ethernaut.openzeppelin.com/
Conclusion
Security issues cause billions of dollars in losses each year and pose a serious threat that the DeFi ecosystem has long faced. Currently, most security measures focus on pre-launch security issues. However, there is no "silver bullet" in the security field. Appropriate measures should be in place at different stages of protocol development to ensure its security, spanning the entire lifecycle of the protocol.
We hope the industry recognizes the importance of post-launch security and takes measures to monitor protocol risks and automatically block attacks.
We also hope that the DeFi ecosystem can form a consensus on prioritizing security to better protect users' asset safety.