By introducing Trusted Execution Environment (TEE) into Layer 2 network consensus, can the TEN Protocol create a new landscape for cryptographic security?
Author: Frank, PANews
In the rapidly evolving world of cryptocurrency trading, hackers and various trading vulnerabilities have become user risks that cannot be ignored. Data privacy and transaction security have emerged as core issues that the industry urgently needs to address. However, traditional blockchain architectures often fail to meet these demands, leading to exposure of transaction information, privacy breaches, and other security risks. These pain points have spurred the demand for higher-level security solutions, particularly the application of Trusted Execution Environment (TEE) technology, which can maintain efficient operation while ensuring privacy.
Against this backdrop, the Layer2 track has become a testing ground for various new technologies. Through different scaling solutions, Layer2 projects have not only enhanced network throughput but also explored new methods for privacy protection. However, most existing Layer2 solutions face trade-offs between privacy, security, and multifunctionality, making it difficult to fully meet market demands.
The Ethereum L2 network TEN Protocol provides a unique solution by integrating TEE technology. TEN Protocol has achieved breakthroughs in both security and privacy, and through its innovative Proof of Block Inclusion (POBI) mechanism, it ensures transaction finality and privacy protection. This architecture enables TEN Protocol to offer efficient transaction processing capabilities while safeguarding privacy, positioning it as an emerging force in the Layer2 track.

TEE - A Risk Mitigation Solution Combining Software and Hardware
In traditional computing environments, sensitive data is often processed at the operating system or application layer, making it vulnerable to various attacks, including operating system-level attacks, malware infections, and physical access attacks. Even the most stringent software security measures can hardly completely block these threats. The leakage of user data not only leads to privacy issues but can also result in more severe financial losses and reputational damage.
In 2014, Mt. Gox was the largest Bitcoin exchange in the world, but due to vulnerabilities in its security system, hackers successfully stole approximately 850,000 bitcoins (worth about $450 million at the time) in multiple attacks. Even a decade later, the repercussions of the Mt. Gox incident continue to affect the entire cryptocurrency industry.
Trusted Execution Environment (TEE) can create an isolated area within the main processing unit, ensuring that the code and data running in this protected environment are not interfered with or attacked by external systems. TEE is a hardware and software combined solution that creates an independent execution environment within the chip, protecting the code and data from external access. Specifically, TEE provides the following core functions:
Data Confidentiality: Data processed within the TEE is encrypted, and no external entity can access or read this data, not even the operating system itself.
Data Integrity: TEE ensures that the code and data running in the protected environment cannot be tampered with. This means that any operations executed within the TEE can be considered trustworthy, preventing interference from malware.
Authentication Functionality: TEE provides an authentication mechanism that allows external entities to verify the authenticity of the code and data running within the TEE. This authentication feature ensures that only verified code can run in the TEE, preventing unauthorized applications from executing.
Building a Trustworthy Consensus Mechanism with TEE
For a long time, the combination of blockchain and TEE has been a key technical focus in the industry. Currently, this integration has become a new security solution in areas such as wallets and smart contracts. However, the adoption of TEE in blockchain infrastructure, such as transaction data and verification nodes, remains limited. This has also led to the emergence of issues like MEV (Miner Extractable Value) caused by data exposure.
TEN Protocol regards TEE technology as a crucial component of its entire network. In its white paper, it describes the goal of its L2 design as creating a fair, permissionless, and decentralized network composed of nodes with effective TEE, which cannot see the transactions they are processing, while collaboratively managing a ledger stored in a rollup form on L1. Even in the face of catastrophic TEE hacking attacks, the integrity of the ledger should be maintained.
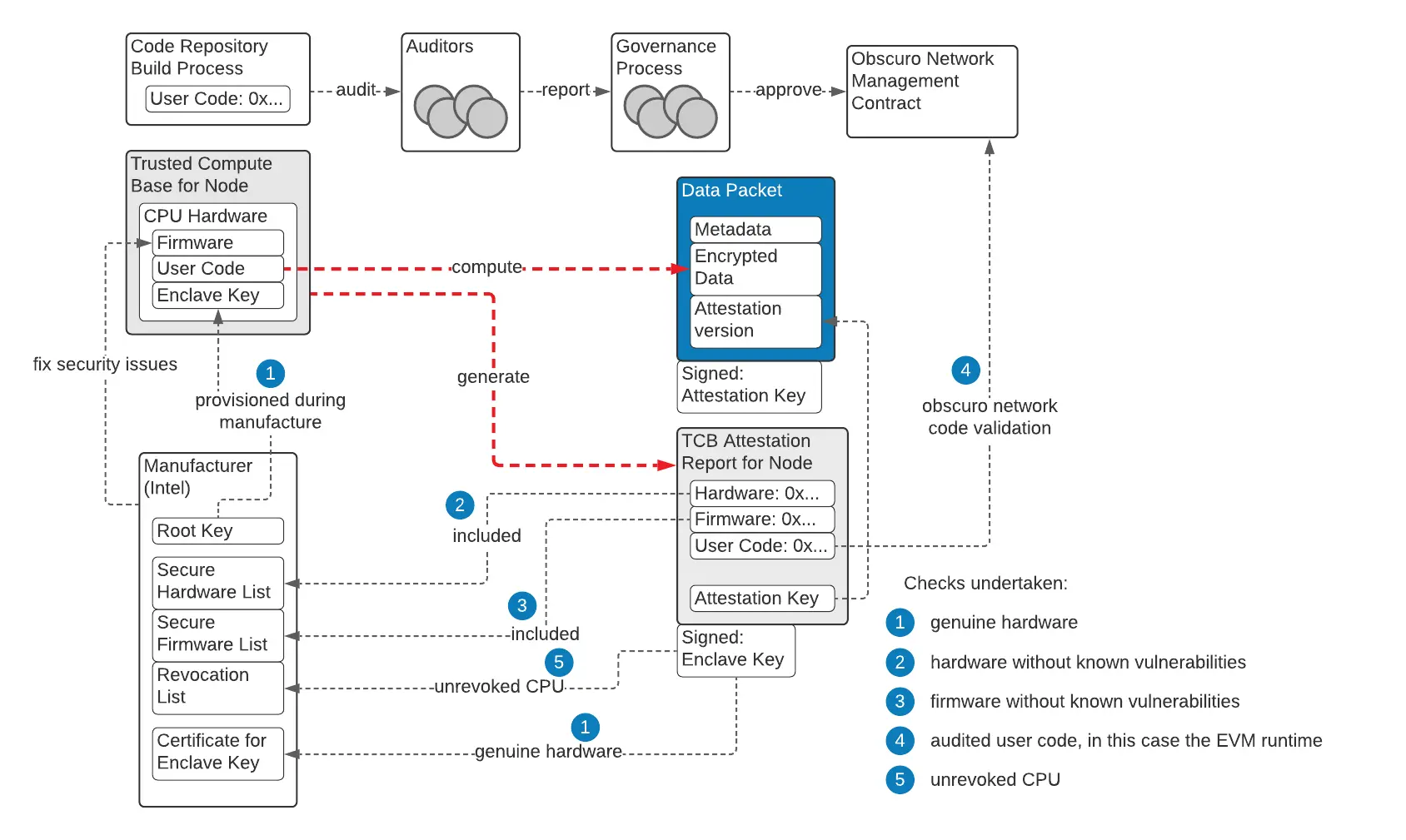
By leveraging hardware-based Trusted Execution Environment (TEE), TEN Protocol can achieve data confidentiality, computational privacy, and prevent maximum extractable value (MEV). Additionally, TEE is employed in various top-level designs to address privacy and security issues. For instance, all nodes wishing to join the network must undergo a security contract review, along with TEE certification requirements, and provide certification reports.
It is worth mentioning that TEN Protocol employs a Proof Of Block Inclusion (POBI) mechanism, which uses TEE to verify the legitimacy of transactions, ensuring that only certified transactions are written to the blockchain, further enhancing the network's security and privacy protection.
This design scheme maximizes the security of nodes while allowing trusted nodes with access restrictions to help improve the efficiency of the blockchain.
Breaking the MEV Dilemma through the Combination of Blockchain and TEE
MEV is a serious issue in blockchain networks, where miners or validators gain extra profits by manipulating the order of transactions. TEN Protocol addresses this problem through TEE technology. Before transactions are packaged into blocks, TEE encrypts the order and content of the transactions, preventing miners from accessing sensitive information before transaction execution.

In addition, the encryption and protection of transaction data also involve TEE. In TEN Protocol, all user transaction data is encrypted using TEE. This process ensures that transaction data is protected before entering the blockchain network, making it impossible to decrypt sensitive information even when transaction records are publicly available on the blockchain. In this way, TEN Protocol eliminates the privacy risks associated with transaction data exposure, providing users with enhanced security guarantees.
TEN Protocol utilizes TEE to protect the execution process of smart contracts. Smart contracts typically handle highly sensitive data, such as user assets and identity information. By executing smart contracts within TEE, TEN ensures that this data cannot be accessed or tampered with by unauthorized third parties during processing.
Currently, TEN Protocol has sparked discussions among many users with security performance requirements due to its extensive use of TEE technology.
A user named Anthony Nixon stated on Twitter: "Combating misinformation is crucial, especially considering the 2024 U.S. election campaign and the recent incident at Manchester Airport. TEN Protocol utilizes Trusted Execution Environment (TEE) to ensure data security for on-chain solutions combating misinformation."
Moreover, artificial intelligence may, to some extent, become one of the execution tools for TEE in the future. TEN has stated that it is building infrastructure for private AI agents. Ultimately, TEN Protocol's goal remains focused on MEV, enhancing the overall privacy and security of the network, with TEE being an important technical solution.
In terms of collaboration progress, TEN Protocol has accumulated numerous cases in areas such as RWA, AI, Gaming, and DeFi. Currently, TEN Protocol has attracted over 120 partners, and the number of interactions on its test network has exceeded 3.4 million, demonstrating its strong stability and scalability.
With the upcoming launch of its mainnet and token TGE, the combination of TEE is likely to attract attention within the industry.



























