July Security Monthly Report | Private key leakage losses account for approximately 88% of total losses, exceeding 260 million USD
In July, the total losses across the network amounted to approximately $290 million, with losses due to private key leaks accounting for 88.31% of the total losses. Among these, WazirX suffered a loss of approximately $235 million due to the leakage of multi-signature wallet private keys, marking the largest security incident in July.
 Largest Security Incident - Private Key Leak
On July 18, WazirX's multi-signature wallet private key was leaked, resulting in a loss of approximately $235 million.
Largest Security Incident - Phishing Scam
On July 24, the ETH on-chain address 0x07…fDC9 lost $4.69 million worth of Pendle re-staked tokens.
Largest Security Incident -REKT
On July 16, the LiFi Protocol cross-chain bridge aggregation protocol was attacked, leading to a loss of approximately $10 million. The attacker exploited a vulnerability that allowed them to steal assets authorized to this contract by users.
Largest Security Incident -RugPull
On July 21, the ETH TrustFund experienced a RugPull, stealing approximately $2 million worth of cryptocurrency on Base.
Largest Security Incident - Private Key Leak
On July 18, WazirX's multi-signature wallet private key was leaked, resulting in a loss of approximately $235 million.
Largest Security Incident - Phishing Scam
On July 24, the ETH on-chain address 0x07…fDC9 lost $4.69 million worth of Pendle re-staked tokens.
Largest Security Incident -REKT
On July 16, the LiFi Protocol cross-chain bridge aggregation protocol was attacked, leading to a loss of approximately $10 million. The attacker exploited a vulnerability that allowed them to steal assets authorized to this contract by users.
Largest Security Incident -RugPull
On July 21, the ETH TrustFund experienced a RugPull, stealing approximately $2 million worth of cryptocurrency on Base.
Case Analysis
On July 15, Minterest encountered a significant security incident on Mantle, resulting in a loss of approximately $1.4 million. Currently, its project team has suspended the protocol.
Process Analysis:
1) A flash loan of 4.265 million USDY was taken from the USDY/USDT liquidity pool on Mantle DEX;

In its callback function: a total of 25 FlashLoan & Redeem Underlying actions were looped;

2) A flash loan of 392,700 USDY was taken from the mUSDY market;

In its callback function: two methods, wrap & lendRUSDY, were called;

3) 4.265 million USDY was deposited, and 4.473 million mUSD was obtained based on the share price;
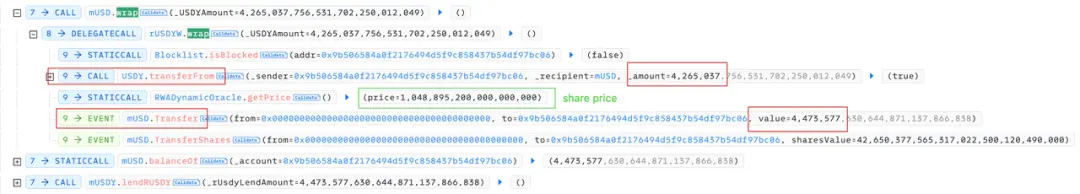
4) Using the 4.473 million mUSD share tokens obtained in the previous step, 2,747,677 million mUSDY was borrowed;

Step 1: Transfer 4.473 million mUSD share tokens;
Step 2: Unwrap 4.473 million mUSD back to 4.265 million USDY and place it in the mUSDY market contract;
Step 3: Transfer 2,747,677 million mUSDY to the user;

5) Retrieve the underlying USDY assets. The hacker calculated how many Redeem Tokens (mUSDY) were needed to retrieve 4.265 million USDY and found that when redeeming the underlying, the hacker only needed to return 2,566,963 million mUSDY, allowing the hacker to keep 180,714 million mUSDY;

6) After looping the above steps about 25 times, the hacker profited approximately $1.4 million.
OKLink Tips
In July, the total losses across the network amounted to approximately $290 million, an increase of 38.01% compared to the total losses in June, with losses due to private key leaks accounting for 88.31% of the total losses. OKLink reminds users not to disclose your private keys or mnemonic phrases to anyone, and do not save or memorize them through screenshots or similar methods. Do not click on unverified links; security awareness is an important line of defense in the Web3 world.
Web3 on-chain tools have become an important means of risk avoidance. OKLink provides tools for address querying and monitoring, on-chain data reporting, and private label establishment, ensuring the safety of each operation through multi-dimensional data comparison.

At the same time, OKLink has launched EaaS (Explorer-as-a-Service), a scalable solution designed to address challenges faced by projects, offering features such as zero-cost setup, rapid deployment, multi-chain support, advanced blockchain analysis, and open APIs.













