Beosin: Analysis of the Attack Incident on the Cross-Chain Protocol LI.FI
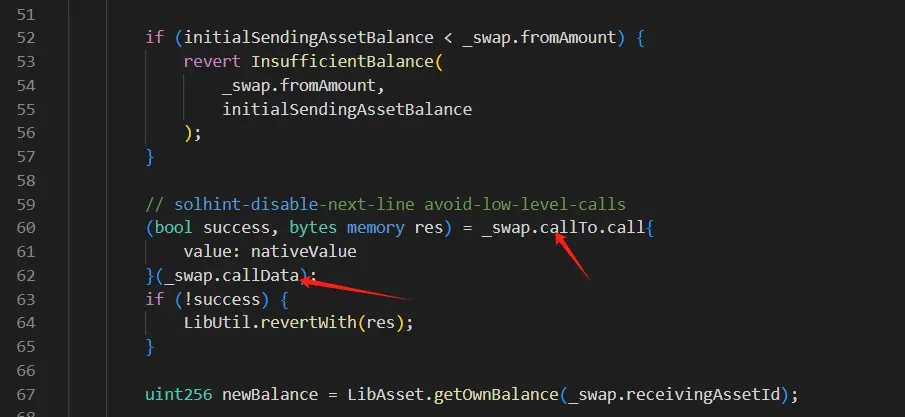
ChainCatcher message, according to Beosin Alert monitoring and early warning, the cross-chain protocol LI.FI has been attacked. The Beosin security team found that the vulnerability was caused by the attacker using a call injection in the project contract to transfer the assets of users authorized to the contract. The LI.FI project contract has a function called depositToGasZipERC20, which can exchange specified tokens for platform tokens and deposit them into the GasZip contract. However, the code in the exchange logic does not restrict the data of the call, allowing the attacker to exploit this function for a call injection attack, extracting the assets of users authorized to the contract.
Attacker address: 0x8B3Cb6Bf982798fba233Bca56749e22EEc42DcF3
Attacked contract: 0x1231DEB6f5749EF6cE6943a275A1D3E7486F4EaE
As of now, the total loss includes 6.3359 million USDT, 3.1919 million USDC, and 169,500 DAI, approximately 10 million USD.
Beosin Trace is currently tracking the stolen funds.