In-depth interpretation of Privasea, how can facial data be used to mint NFTs in this way?
Author: Shijiu Jun
1. Introduction
Recently, a face NFT minting project initiated by Privasea has become exceptionally popular! At first glance, it seems simple: users can input their facial data on the IMHUMAN mobile application and mint their facial data as an NFT. It is precisely this combination of facial data on-chain + NFT that has led to over 200,000+ NFTs minted since the project's launch at the end of April, indicating its popularity. I am also puzzled: why is this happening? Can facial data really be put on-chain? Will my facial information be misused? What exactly does Privasea do? Let’s continue to investigate the project itself and the project team, Privasea, to find out. Keywords: NFT, AI, FHE (Fully Homomorphic Encryption), DePIN
2. From Web2 to Web3 - The Human-Machine Confrontation Never Stops
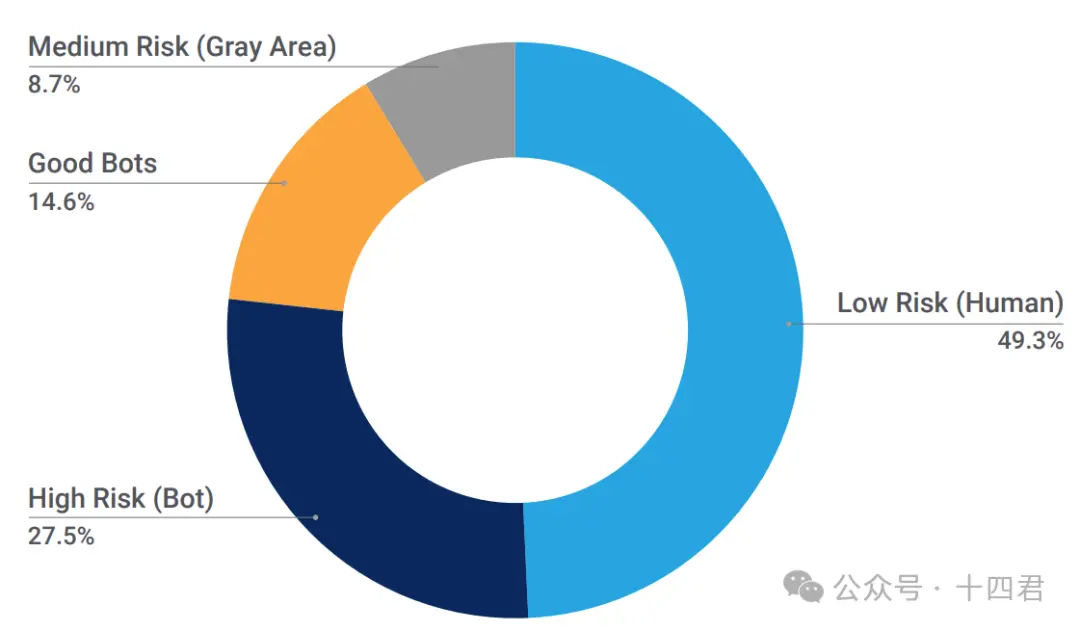
First, let’s interpret the purpose of the face NFT minting project itself. If you think this project is simply about minting facial data into NFTs, you are gravely mistaken. The name of the app we mentioned earlier, IMHUMAN, already illustrates this issue well: in fact, the project aims to determine whether you are a real person in front of the screen through facial recognition. So, why do we need human-machine recognition? According to the Q1 2024 report provided by Akamai (see appendix), bots (automated programs that can simulate human actions such as sending HTTP requests) astonishingly account for 42.1% of internet traffic, with malicious traffic making up 27.5% of total internet traffic. Malicious bots can lead to delayed responses or even catastrophic outages for centralized service providers, affecting the user experience of real users.
Taking the ticket grabbing scenario as an example, cheaters can create multiple virtual accounts to increase their chances of successfully grabbing tickets, and some even deploy automated programs next to the service provider's data center to achieve nearly zero latency in ticket purchasing.
Ordinary users have almost no chance against these high-tech users.
Service providers have also made some efforts. In the Web2 scenario, they distinguish between humans and machines through various methods such as real-name authentication and behavioral CAPTCHAs on the client side, while on the server side, they use WAF strategies and other means for feature filtering and interception.
So, can this problem be solved?
Clearly not, because the profits from cheating are substantial.
Moreover, the confrontation between humans and machines is ongoing, with both cheaters and verifiers constantly upgrading their arsenals.
For example, taking advantage of the rapid development of AI in recent years, behavioral CAPTCHAs on the client side have been significantly undermined by various visual models, and AI can even recognize faster and more accurately than humans. This forces verifiers to passively upgrade from early user behavior feature detection (image-based CAPTCHAs) to biomimetic feature detection (perceptual verification: such as client environment monitoring, device fingerprinting, etc.), and for some high-risk operations, it may need to escalate to biological feature detection (fingerprints, facial recognition).
For Web3, human-machine detection is also a strong demand.
For some project airdrops, cheaters can create multiple fake accounts to launch witch attacks, and at this point, we need to identify real people.
Due to the financial attributes of Web3, for some high-risk operations such as account login, withdrawal, trading, and transferring, it is necessary to verify that the user is not only a real person but also the account owner, making facial recognition the best choice. The demand is clear, but how to achieve it? As we all know, decentralization is the original intention of Web3. When we discuss how to implement facial recognition in Web3, the deeper issue is how should Web3 adapt to AI scenarios:
- How should we build a decentralized machine learning computing network?
- How to ensure user data privacy is not leaked?
- How to maintain the operation of the network, etc.?
3. Privasea AI Network - Exploring Privacy Computing + AI
Regarding the questions mentioned at the end of the previous chapter, Privasea has provided a groundbreaking solution: Privasea has built the Privasea AI Network based on FHE (Fully Homomorphic Encryption) to solve the privacy computing problem in AI scenarios on Web3. FHE, in simple terms, is an encryption technology that ensures the results of operations performed on plaintext and ciphertext are consistent. Privasea has optimized and encapsulated traditional FHE, dividing it into application layer, optimization layer, arithmetic layer, and raw layer, forming the HESea library, making it suitable for machine learning scenarios. Below are the specific functions of each layer:
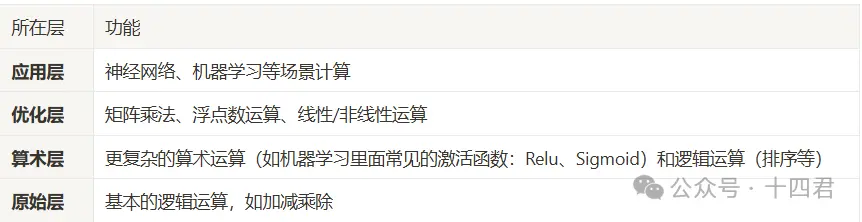
Through a layered structure, Privasea provides more specific and tailored solutions to meet each user's unique needs. Privasea's optimization encapsulation mainly focuses on the application layer and optimization layer, and compared to the basic solutions in other homomorphic libraries, these customized computations can provide over a thousand times acceleration.
3.1 Network Architecture of Privasea AI Network
From the architecture of the Privasea AI Network:
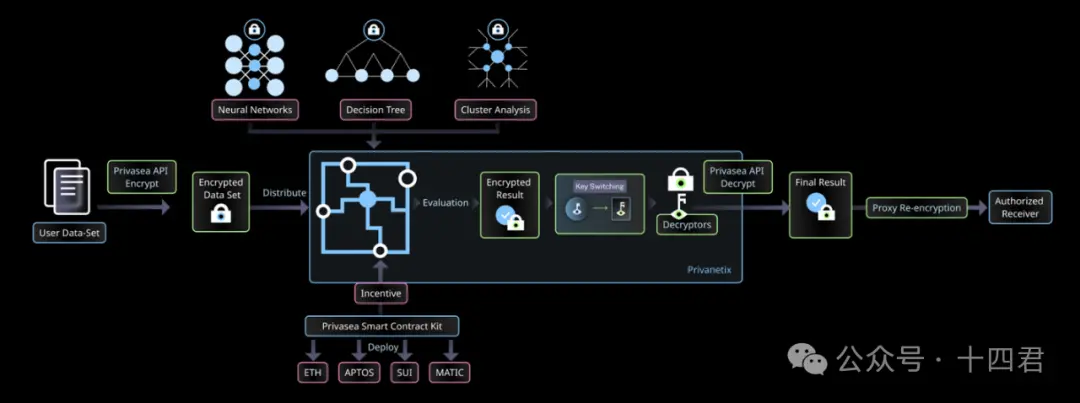
There are a total of four roles in its network: data owner, Privanetix node, decryptor, result recipient.
Data Owner: Submits tasks and data securely through the Privasea API.
Privanetix Node: The core of the entire network, equipped with the advanced HESea library and integrated with a blockchain-based incentive mechanism, can perform secure and efficient computations while protecting the privacy of underlying data and ensuring the integrity and confidentiality of computations.
Decryptor: Obtains the decrypted results through the Privasea API and verifies the results.
Result Recipient: The task results will be returned to the data owner and the designated person specified by the task issuer.
3.2 Core Workflow of Privasea AI Network
Below is a general workflow diagram of the Privasea AI Network:
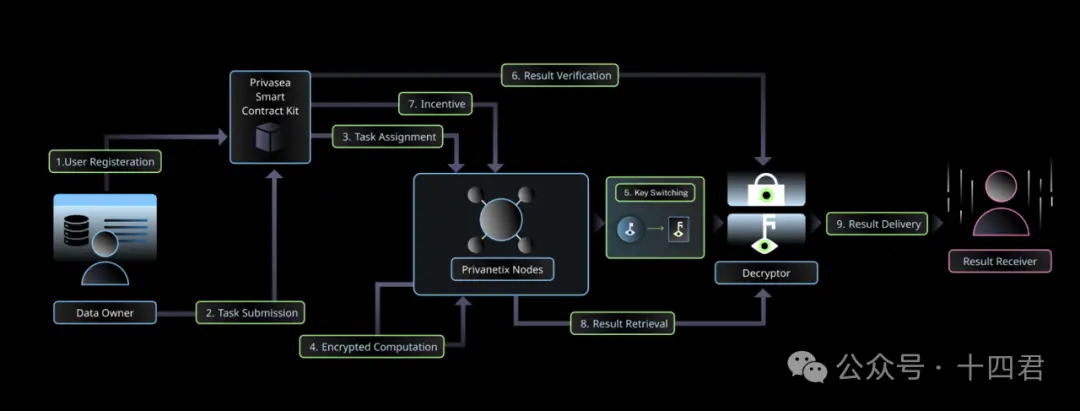
STEP 1: User Registration: The data owner initiates the registration process on the privacy AI network by providing necessary authentication and authorization credentials. This step ensures that only authorized users can access the system and participate in network activities.
STEP 2: Task Submission: Submit computational tasks and input data, which are encrypted data from the HESea library. The data owner also specifies authorized decryptors and result recipients who can access the final results.
STEP 3: Task Assignment: Blockchain-based smart contracts deployed on the network assign computational tasks to suitable Privanetix nodes based on availability and capability. This dynamic allocation process ensures efficient resource allocation and distribution of computational tasks.
STEP 4: Encrypted Computation: The designated Privanetix node receives the encrypted data and performs computations using the HESea library. These computations can be executed without decrypting sensitive data, thus maintaining its confidentiality. To further verify the integrity of the computations, the Privanetix node generates zero-knowledge proofs for these steps.
STEP 5: Key Switching: After completing the computations, the designated Privanetix node uses key switching technology to ensure that the final results are authorized and can only be accessed by the specified decryptor.
STEP 6: Result Verification: After the computations are completed, the Privanetix node sends the encrypted results and corresponding zero-knowledge proofs back to the blockchain-based smart contract for future verification.
STEP 7: Incentive Mechanism: Tracks the contributions of Privanetix nodes and allocates rewards.
STEP 8: Result Retrieval: The decryptor accesses the encrypted results using the Privasea API. Their primary task is to verify the integrity of the computations, ensuring that the Privanetix nodes executed the computations according to the data owner's intentions.
STEP 9: Result Delivery: Shares the decrypted results with the designated result recipients predetermined by the data owner.
In the core workflow of the Privasea AI Network, users are exposed to an open API, allowing them to focus only on input parameters and corresponding results without needing to understand the complex internal computations of the network, thus reducing cognitive burden. Meanwhile, end-to-end encryption ensures that data itself is not leaked without affecting data processing.
PoW && PoS Dual Mechanism Overlay: Privasea recently launched WorkHeart NFT and StarFuel NFT, which manage network nodes and reward distribution through a dual mechanism of PoW and PoS. Purchasing WorkHeart NFT grants eligibility to become a Privanetix node and participate in network computations, earning token rewards based on the PoW mechanism. StarFuel NFT is a node booster (limited to 5000), which can be combined with WorkHeart; similar to PoS, the more tokens staked, the greater the yield multiplier for WorkHeart nodes. So, why PoW and PoS? This question is relatively easy to answer. The essence of PoW is to reduce the rate of node misconduct through the time cost of computation, maintaining network stability. Unlike the massive invalid computations of BTC's random number verification, the actual work output (computation) of these privacy computing network nodes can be directly linked to the workload mechanism, making it naturally suitable for PoW. PoS, on the other hand, balances economic resources more easily. Thus, WorkHeart NFT earns rewards through the PoW mechanism, while StarFuel NFT increases yield multipliers through the PoS mechanism, forming a multi-layered and diversified incentive mechanism that allows users to choose suitable participation methods based on their resources and strategies. The combination of the two mechanisms optimizes the reward distribution structure and balances the importance of computational resources and economic resources in the network.
3.3 Summary
It can be seen that Privasea AI Network has built a encrypted version of the machine learning system based on FHE. Thanks to the characteristics of FHE privacy computing, it packages computational tasks to various computing nodes (Privanetix) in a distributed environment, effectively verifying the validity of results through ZKP, and rewarding or punishing nodes that provide computational results using the dual mechanism of PoW and PoS, thus maintaining the operation of the network. It can be said that the design of Privasea AI Network paves the way for privacy-protecting AI applications in various fields.
4. FHE Homomorphic Encryption - The New Holy Grail of Cryptography?
In the previous chapter, we saw that the security of Privasea AI Network relies on its underlying FHE. With the continuous breakthroughs in technology by FHE leader ZAMA, FHE has even been dubbed the new holy grail of cryptography by investors. Let’s compare it with ZKP and related solutions.
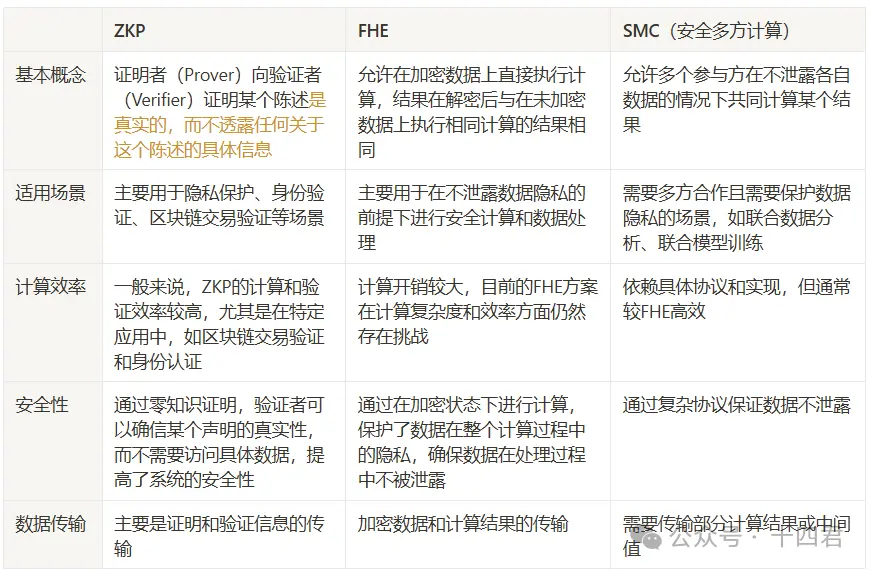
In comparison, it can be seen that ZKP and FHE have significantly different applicable scenarios; FHE focuses on privacy computing, while ZKP focuses on privacy verification. SMC seems to have a greater overlap with FHE, as the concept of SMC is secure multi-party computation, which addresses the data privacy issues of individual computing entities in joint computations.
5. Limitations of FHE
FHE achieves the separation of data processing rights and data ownership, thus preventing data leakage without affecting computation. However, the trade-off is computational speed. Encryption is like a double-edged sword; while it enhances security, it significantly reduces computational speed. In recent years, various performance enhancement solutions for FHE have been proposed, some based on algorithm optimization and others relying on hardware acceleration.
- In terms of algorithm optimization, new FHE schemes like CKKS and optimized bootstrap methods significantly reduce noise growth and computational overhead;
- In terms of hardware acceleration, custom GPUs, FPGAs, and other hardware significantly improve the performance of polynomial computations.
Additionally, the application of hybrid encryption schemes is also being explored, which combines partially homomorphic encryption (PHE) and searchable encryption (SE) to improve efficiency in specific scenarios. Nevertheless, FHE still has a significant performance gap compared to plaintext computation.
6. Conclusion
Privasea, through its unique architecture and relatively efficient privacy computing technology, not only provides users with a highly secure data processing environment but also opens a new chapter in the deep integration of Web3 and AI. Although the underlying FHE has a natural disadvantage in computational speed, Privasea has recently partnered with ZAMA to tackle the challenges of privacy computing. In the future, with continuous technological breakthroughs, Privasea is expected to unleash its potential in more fields, becoming an explorer in privacy computing and AI applications.










