In May, blockchain security incidents increased, with losses amounting to $154 million due to hacker attacks and other factors
Author: Zero Time Technology
The monthly security incident highlights from Zero Time Technology have begun! According to statistics from various blockchain security risk monitoring platforms, the total loss from various security incidents in May 2024 increased compared to April. In May, there were over 37 typical security incidents, with total losses due to hacker attacks, phishing scams, and Rug Pulls amounting to $154 million, an increase of approximately 52.5% compared to April. Among these, attack incidents accounted for about $54.51 million, an increase of approximately 3.7%; phishing scams accounted for about $97.4 million, an increase of approximately 754%; and Rug Pull incidents accounted for about $2.04 million, a decrease of approximately 94.5%.
In addition, there are some specific security incidents and new information, which will be detailed below.
Hacker Attacks
Typical Security Incidents 11 cases
(1) On May 5, GNUS on the Fantom chain was attacked, resulting in a loss of approximately $1.27 million.
(2) On May 9, the Blast ecosystem Bloom project was attacked, resulting in a loss of approximately $540,000. About 90% of the stolen funds have been recovered (after deducting a 10% bug bounty).
(3) On May 10, the Web3 game project Galaxy Fox was attacked, resulting in a loss of approximately $300,000.
(4) On May 10, the Base ecosystem Tsuru was attacked, resulting in a loss of approximately $410,000.
(5) On May 14, the DEX project Predy Finance on the Arbitrum chain was attacked, resulting in a loss of approximately $460,000.
(6) On May 15, the Bitcoin DeFi tool Alex Lab suffered a total loss of approximately $6.3 million on the Stacks and BSC chains due to stolen private keys.

(7) On May 15, Sonne Finance, a Compound fork project on the Optimism chain, was attacked due to a contract vulnerability, resulting in a loss of $20 million. After the incident, Seal contributors saved about $6.5 million by adding value of approximately $100 in VELO to the market. This attack exploited a vulnerability that was newly introduced to the market, and within two days of the market's creation, the attacker executed key transactions using a multi-signature wallet and time-lock features, successfully manipulating the market's collateral factors (c-factors).

(8) On May 16, the Solana ecosystem pump.fun project was attacked, resulting in a loss of approximately $1.9 million. The attacker then began airdropping funds to some random wallets. pump.fun stated on Twitter that the attack occurred because a former employee illegally obtained withdrawal permissions using their privileges at the company and executed a flash loan attack through a lending protocol.

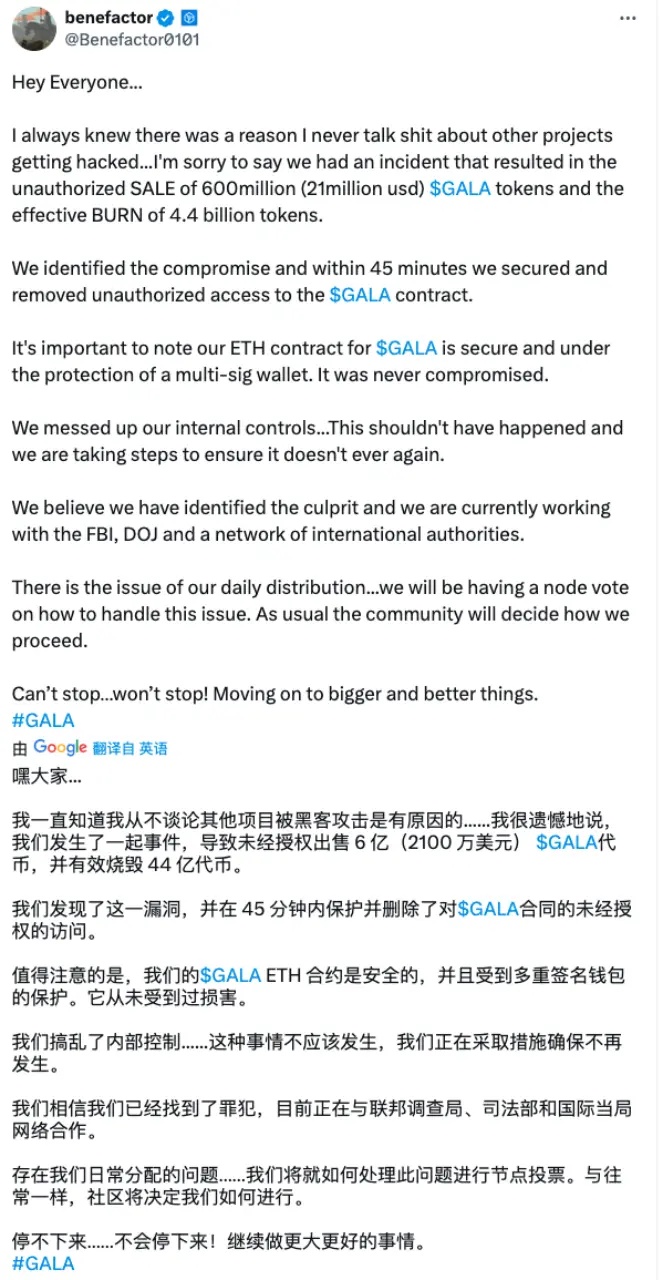
(9) On May 20, the Web3 gaming platform Gala Games was attacked, resulting in a loss of approximately $21.8 million. The attacker minted 5 billion GALA tokens, worth over $200 million, and then quickly sold 592 million GALA, obtaining 5,952 ETH. On May 22, according to on-chain records and Gala Games' statement on Discord, the hacker returned 5,913.2 ETH.
(10) On May 21, the TON ecosystem Launchpad platform TonUP was attacked due to an engineer's misconfiguration of script parameters, resulting in a loss of approximately $107,000.
(11) On May 26, the Base ecosystem meme coin Normie was attacked, resulting in a loss of approximately $490,000.
Rug Pull / Phishing Scams
Typical Security Incidents 6 cases
(1) On May 3, a certain whale address fell victim to an address poisoning scam, resulting in a loss of $72 million.
(2) On May 14, a fake Pii Park project on the Polygon chain experienced a Rug Pull, with the deployer profiting approximately $490,000.
(3) On May 14, an address starting with 0xff49 was targeted by a Pink Drainer phishing scam, resulting in a loss of approximately $1.66 million.
(4) On May 16, an address starting with 0x719e suffered a phishing scam, resulting in a loss of approximately $1.25 million.
(5) On May 18, an address starting with 0xee6a suffered a phishing scam, resulting in a loss of Pendle yield tokens worth approximately $5.6 million.
(6) On May 26, an address starting with 0x2154 suffered a phishing scam, resulting in a loss of approximately $6.9 million.
Cryptocurrency Crimes
Typical Security Incidents 20 cases
(1) On May 19, the People's Court of Chongqing Liangjiang New Area (Free Trade Zone) recently concluded a highly publicized entrusted contract dispute case involving members of a pyramid scheme purchasing virtual currency. The court ruled that the entrusted contract violated mandatory provisions of national laws and administrative regulations and should be deemed invalid. After the first-instance verdict, Zhou appealed. The Chongqing First Intermediate People's Court upheld the original verdict. This ruling has now taken effect and has been automatically enforced.
(2) In May, the police in Tianshui Maiji District dismantled a virtual currency money laundering gang across 5 provinces and 9 cities, arresting 13 suspects and recovering over one million yuan. Currently, 13 suspects have been subjected to criminal coercive measures, and the case is under further investigation.
(3) On May 15, the Chengdu Public Security Bureau announced the investigation process of a major underground bank case involving virtual currency, with an amount involved of 13.8 billion yuan, and 193 suspects arrested, freezing 149 million yuan of involved funds. The case received relevant clues in November 2022, and on June 1, 2023, under the command of the Ministry of Public Security and the Public Security Bureau, 25 suspects including Lin, Weng, and Chen were arrested, and a large number of payment tools such as bank cards and U-shields used for committing crimes were seized.
(4) On May 13, it was reported that the Public Security Bureau of Panshi City, Jilin Province, successfully cracked a case of illegal operation of an underground bank using virtual currency, involving approximately 2.14 billion yuan. Six suspects who committed crimes in both China and South Korea were arrested. The police found that the criminal gang used domestic accounts to receive and transfer funds, OTC trading of virtual currency, and Korean currency settlement to illegally engage in foreign exchange business, helping groups such as Korean purchasing agents, cross-border e-commerce, and import-export trade companies to exchange RMB for Korean currency.
(5) On May 11, the police in Mingxi, Fujian, cracked a virtual currency fraud case. Li met a stranger through an overseas chat software and was lured by this stranger to make money by purchasing "USDT" virtual currency and reselling it for profit. Li transferred money multiple times to purchase "USDT" virtual currency, but after receiving the funds, the stranger fabricated various reasons to refuse to provide Li with "USDT" virtual currency, ultimately defrauding Li of 387,000 yuan. On May 11, the Mingxi police successfully arrested the fraud suspect Zhao in Sichuan.
(6) On May 16, the Anti-Fraud Center of the Public Security Bureau of Sunwu County, Heilongjiang Province, discovered a clue related to telecom network fraud during their work, and the police immediately organized forces to carry out operations. Upon investigation, the police found that a resident of a certain city in Jiangxi Province, Wu, was suspected of colluding with others to use virtual currency to help telecom fraudsters launder money, and quickly identified the suspects. That day, the police arrested four suspects including Wu, Chen, Liu, and Wang in a single operation in a certain city in Jiangxi Province.
(7) On May 16, it was reported that Hong Kong police recently arrested three local men in a suspected cryptocurrency fraud case. One man attempted to resell Tether (USDT) worth approximately 1 million HKD in a shop in Tsim Sha Tsui but was scammed with counterfeit money.
(8) On May 14, Hong Kong police arrested a cross-border money laundering gang. It is reported that the Commercial Crime Bureau of the Hong Kong police identified a cross-border money laundering group in November 2023, discovering that the group recruited mainland individuals to open puppet bank accounts in Hong Kong from September 2023 to March 2024, using various types of scams to defraud victims. Victims were instructed by the fraudsters to deposit the scammed funds into puppet accounts controlled by the criminal group, which would then withdraw the scammed funds in cash from the puppet accounts and purchase cryptocurrencies at over-the-counter (OTC) exchanges, while also opening accounts under false identities on overseas cryptocurrency platforms, depositing the cryptocurrencies purchased with the scammed funds, and transferring them to multiple cryptocurrency wallets to launder the criminal proceeds.
(9) The U.S. Department of Justice has indicted and arrested Cartier, an heir to Cartier jewelry, on charges of money laundering using USDT, allegedly colluding with Colombian drug trafficking organizations. Cartier, along with five Colombian nationals, attempted to import 100 kilograms of cocaine and launder hundreds of millions of dollars, most of which was conducted through OTC USDT transactions. They had actually laundered $14.5 million before being arrested. Cartier is currently held at a detention center in Miami, while his accomplices are detained in Colombian prisons.
(10) The U.S. Department of Justice arrested the leader of a botnet responsible for orchestrating a $130 million online scam. According to the indictment dated May 29, the suspect is accused of "creating and distributing malware to infiltrate and aggregate a network of millions of home Windows computers worldwide." An independent analysis by blockchain analytics firm Chainalysis shows that wallet addresses associated with the suspect hold over $130 million in digital assets earned through illegal commissions.
(11) On May 17, it was reported that a lawsuit was unsealed in the Central District of California, accusing two Chinese nationals of playing key roles in a money laundering scheme involving cryptocurrency investment fraud. They are accused of leading a money laundering scheme related to an international cryptocurrency investment scam, involving at least $73 million.
(12) On May 1, it was reported that the FBI cracked a Ponzi scheme luring investors with cryptocurrency, Idin Dalpour, involving $43 million.
(13) On May 14, it was reported that Alexey Pertsev, one of the developers of the Tornado Cash mixing service, was convicted of money laundering and sentenced to 64 months in prison in the Netherlands.
(14) On May 15, it was reported that Canada's "King of Cryptocurrency" and his accomplices were arrested, accused of defrauding investors of $30 million through cryptocurrency and foreign exchange investment schemes.
(15) On May 21, it was reported that U.S. authorities arrested and charged a Taiwanese man operating a dark web drug trading market, suspected of using the site to sell illegal narcotics worth over $100 million in cryptocurrency, including fentanyl.
(16) Paraguayan authorities arrested nearly 400 Bitcoin miners in Sapukai City. This operation was conducted jointly by the police and the National Electricity Administration (ADE) as part of an investigation into suspected electricity theft.
(17) On May 31, it was reported that Turkish authorities conducted a cryptocurrency operation across 21 provinces in Ankara, detaining 127 suspects involved in "international fraud through Ponzi schemes" and "criminal activities and laundering criminal proceeds." During this operation, authorities seized over 177 pieces of real estate and 61 pieces of movable property, valued at 1 billion Turkish lira. Additionally, they confiscated an unlicensed firearm, a blank-firing gun, and some cryptocurrency assets.
(18) On May 26, it was reported that Malaysian law enforcement recently arrested a criminal gang suspected of laundering money using cryptocurrency, with a total of 10 people arrested. Law enforcement seized 129 vehicles worth approximately $3.8 million (18 million Malaysian ringgit), as well as luxury watches, 18 luxury cars, motorcycles, and handbags worth over $3.9 million, and froze bank accounts totaling approximately $10.8 million. This gang is suspected of illegally profiting through scams involving high-end license plates and luxury brand watches, transferring funds through unregistered exchangers and cryptocurrency transactions to Malaysia.
(19) The Texas State Securities Board has issued a cease-and-desist order to Arkbit Capital, accusing it of engaging in fraudulent cryptocurrency cloud mining activities. According to the order, the Texas Securities Board found that Arkbit Capital and its affiliates were engaged in fraudulent activities, including using deceptive images and video processing techniques to promote their investment plans. Arkbit falsely claimed to operate a data center in Arkansas for cloud mining various cryptocurrencies, promising daily investment returns of 1.6-2.8% for deposits ranging from $50 to $49,999.
(20) On May 26, it was reported that Indian citizen Chirag Tomar admitted to "stealing over $37 million from the Coinbase website through deception," pleading guilty to telecommunications fraud, which carries a maximum sentence of 20 years in prison and a $250,000 fine. Chirag Tomar and his accomplices designed a fake Coinbase Pro website to trick users into entering their login credentials and two-factor authentication codes, and were arrested at Atlanta Airport upon entering the U.S. on December 20 last year, and are currently still in federal custody.
Summary
From the analysis of the above incidents, it can be seen that the loss amount in May increased compared to April, with two hacker attack incidents resulting in losses exceeding $10 million: the gaming platform Gala Games lost $22.5 million due to private key leakage, and Sonne Finance lost $20 million due to a contract vulnerability.
The Zero Time Technology security team advises project parties to remain vigilant at all times, conduct internal security training, and manage permissions to enhance employees' security awareness and prevent internal malfeasance.
Note:
The content of this article is compiled from publicly available materials.
Important Reminder: This article only organizes industry information and does not constitute any investment advice or guarantees.












