Wolf in Sheep's Clothing: Analysis of Fake Chrome Extensions Theft
Author: Slow Mist Security Team
Background
On March 1, 2024, Twitter user @doomxbt reported abnormal activity on their Binance account, with funds suspected to be stolen:

(https://x.com/doomxbt/status/1763237654965920175)
Initially, this incident did not attract much attention, but on May 28, 2024, Twitter user @TreeofAlpha analyzed and discovered that the victim @doomxbt had seemingly installed a malicious Aggr extension from the Chrome store that had many positive reviews! It could steal all cookies from the websites users visited, and two months prior, someone had paid some influencers to promote it.

(https://x.com/TreeofAlpha/status/1795403185349099740)
In the past few days, the attention on this incident has increased, with victims reporting that their login credentials were stolen, and subsequently, hackers used these credentials to steal the victims' cryptocurrency assets. Many users have consulted the Slow Mist Security Team about this issue. Next, we will analyze this attack incident in detail to sound the alarm for the crypto community.
Analysis
First, we need to find this malicious extension. Although Google has already removed the malicious extension, we can see some historical data through snapshot information.

After downloading and analyzing, we found that the JS files in the directory are background.js, content.js, jquery-3.6.0.min.js, and jquery-3.5.1.min.js.
During static analysis, we found that background.js and content.js did not contain much complex code or any obvious suspicious code logic, but we discovered a link to a site in background.js, which sends the data collected by the extension to https[:]//aggrtrade-extension[.]com/statistics_collection/index[.]php.

By analyzing the manifest.json file, we can see that background uses /jquery/jquery-3.6.0.min.js, and content uses /jquery/jquery-3.5.1.min.js, so we focused on analyzing these two jQuery files:

We found suspicious malicious code in jquery/jquery-3.6.0.min.js, which sends cookies from the browser to the site: https[:]//aggrtrade-extension[.]com/statistics_collection/index[.]php after processing them with JSON.

After static analysis, to more accurately analyze the behavior of the malicious extension in sending data, we began to install and debug the extension. (Note: Analysis should be conducted in a brand new testing environment, where no accounts are logged in, and the malicious site should be changed to one that is controllable to avoid sending sensitive data to the attacker's server during testing.)
After installing the malicious extension in the testing environment, we opened any website, such as google.com, and then observed the network requests in the background of the malicious extension, finding that Google’s cookie data was sent to an external server:

We also saw the cookie data sent by the malicious extension on the Weblog service:

At this point, if the attacker obtains user authentication, credentials, and other information, they can hijack cookies using the browser extension to conduct counter-trading attacks on some trading sites, stealing users' crypto assets.
Next, we analyze the malicious link that sends data back: https[:]//aggrtrade-extension[.]com/statistics_collection/index[.]php.
Involved domain: aggrtrade-extension[.]com

Analyzing the domain information in the image above:

The .ru domain appears to be typical of Russian-speaking users, so it is highly likely that it is a Russian or Eastern European hacker group.
Attack Timeline:
Analyzing the counterfeit AGGR (aggr.trade) malicious website aggrtrade-extension[.]com, we found that the hackers began planning the attack three years ago:


Four months ago, the hackers deployed the attack:

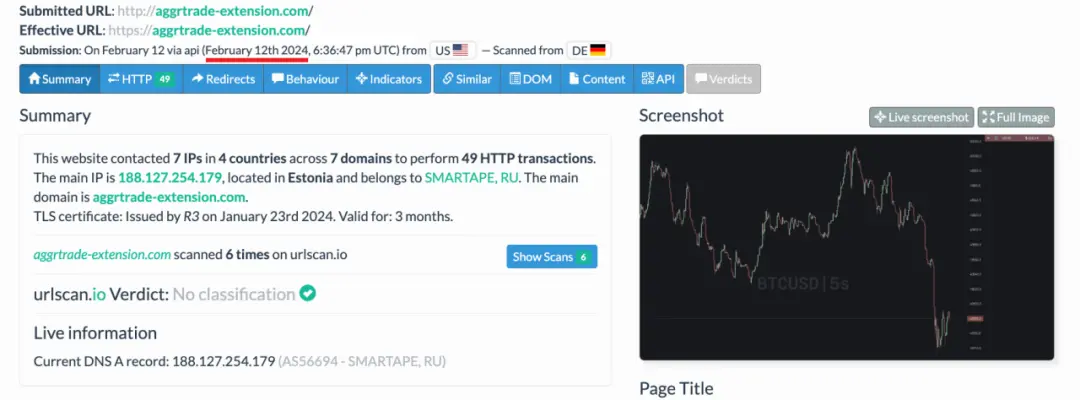

According to the InMist threat intelligence collaboration network, we found that the hacker's IP is located in Moscow, using a VPS provided by srvape.com, and the email is aggrdev@gmail.com.

After successful deployment, the hackers began promoting on Twitter, waiting for victims to bite. The rest of the story is well known; some users installed the malicious extension and were subsequently stolen from.
The following image is the official reminder from AggrTrade:

Conclusion
The Slow Mist Security Team reminds users that the risks of browser extensions are almost as significant as directly running executable files, so it is essential to review them carefully before installation. Additionally, be cautious of those who send you private messages; hackers and scammers often impersonate legitimate, well-known projects under the guise of funding or promotion, targeting content creators for fraud. Finally, when navigating the dark forest of blockchain, always maintain a skeptical attitude, ensuring that what you install is safe and preventing hackers from exploiting vulnerabilities.












