Lost over 1800 ETH, liquidity went to zero, what happened to Velocore?
Author: BlockTempo
Yesterday, the decentralized trading platform Velocore was hacked, resulting in the theft of 1,807 ETH (approximately $6.88 million). In response, Velocore released a report detailing the affected liquidity pools, the method of attack, and subsequent compensation plans.
The decentralized trading platform Velocore, deployed on Layer 2 networks zkSync and Linea, was attacked by hackers yesterday (2nd), suffering a loss of 1,807 ETH (approximately $6.88 million).
On-chain analyst Yu Jin stated that all users' liquidity funds on the platform were stolen. The hackers then transferred the stolen funds to the Ethereum mainnet via a cross-chain bridge, moving all ETH to the address 0xe40 and using the mixer protocol Tornado to obscure and launder the funds.
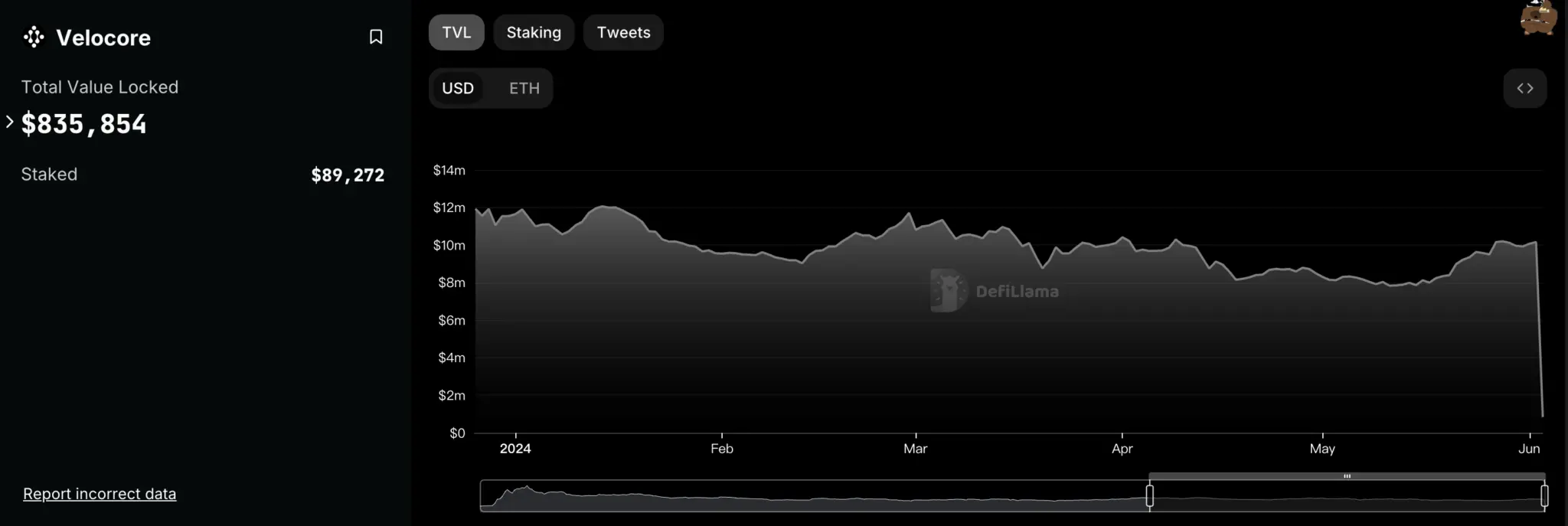
Additionally, according to data from the DeFi data platform DefiLlama, after the hack, Velocore's total locked value plummeted from $10.16 million the previous day to $835,000, a staggering decline of 92%.
Contract Vulnerability Causes
Yesterday, the Velocore team released a security review report regarding the hacking incident. The report indicated that the cause of the attack was a contract vulnerability in the Balancer-style CPMM pool. The report detailed the security status of each liquidity pool:
- All CPMM pools on Velocore in the Linea and zkSync Era chains were affected.
- Stable pools were not affected.
- Velocore on the Telos chain also faced the same issue, but the team addressed it before the problem was exploited.
- Although Bladeswap on the Blast chain uses Velocore's core contracts, it was not affected by this contract vulnerability because Bladeswap employs an XYK pool rather than a CPMM pool.
Constant product market makers (CPMM) are one of the early adopted functions in DeFi liquidity mining pools, with the function algorithm: x * y = k. Here, x and y are the reserves of assets in the pool, and k is a constant. This function determines the price range of the two tokens based on the available quantity (liquidity) of each token, meaning that if the supply of token X increases, the supply of token Y decreases to maintain the constant value k.
Another Flash Loan Attack?
According to the report, the attacker first obtained funds from the mixer protocol Tornado and then triggered the conditions for the contract vulnerability. Next, they used a flash loan to acquire liquidity provider (LP) tokens and withdrew most of the tokens, significantly shrinking the liquidity pool. Subsequently, the attacker exploited the token contract vulnerability to mint an abnormal amount of LP tokens, thereby repaying the flash loan.
Compensation for Users After Resuming Operations
In response to this hacking incident, the Velocore team stated that they are actively pursuing the hacker while also attempting to negotiate with them on-chain. Velocore communicated on-chain with the hacker, indicating:
If the hacker returns the remaining funds by 4 PM on June 3, the team is willing to offer a 10% white hat hacker bounty.
However, the hacker has yet to respond to Velocore.
On the other hand, the team also stated that they would provide compensation to those affected and took a snapshot of the block state before the attack occurred. However, the compensation plan will only be executed after Velocore resumes operations.










