A publicly announced hacker attack, the io.net vulnerability was reported by the community one month ago
Author: flowie, ChainCatcher
Editor: Marco, ChainCatcher
On the afternoon of April 25, io.net suffered a hacker attack, allowing unauthorized access to the io.net metadata API. Community users reported that the names and online statuses of multiple io.net machines were altered.
With the token issuance imminent, this attack on io.net has caused a certain level of panic within the community, leading to the emergence of some "io.net rights protection groups."
After the attack, Ahmad Shadid, co-founder and CEO of io.net, responded on the X platform, stating that the affected area was the user front-end metadata, and there was no leakage of GPU access rights or user/device data. All uptime records remained unaffected, and there would be no impact on the computing rewards for vendors.
Although community users are concerned that the calculation of reward points is unaffected, this attack may still lead to a certain degree of trust crisis for io.net.
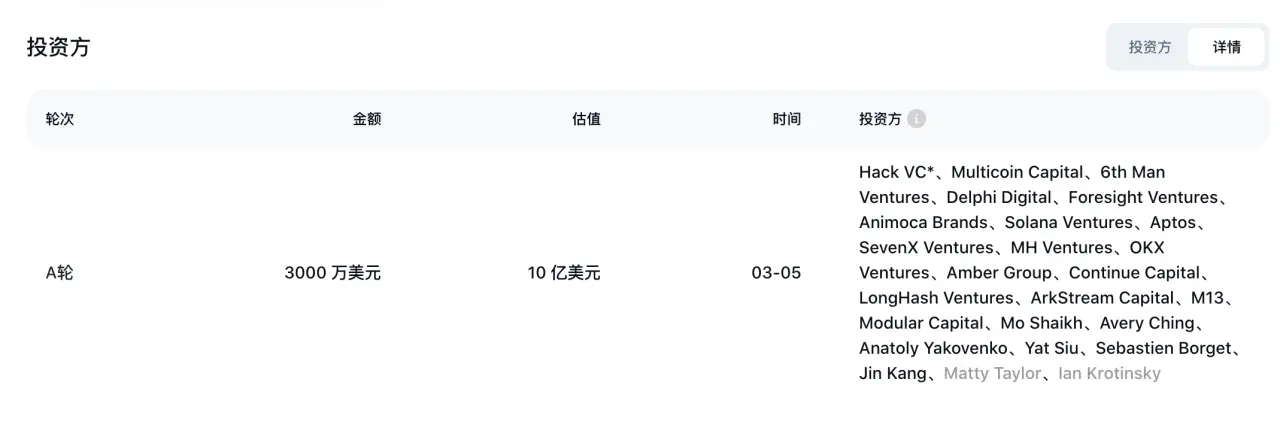
io.net is a star project in the Solana ecosystem focusing on AI + DEPIN, having secured $30 million in funding from a host of top-tier investors and well-known project parties and exchanges, including HackVC, Multicoin Capital, Animoca Brands, Solana Ventures, Aptos, and OKX in March this year.
Community Users: The Attack Vulnerability Was Reported a Month Ago
Community user COOK reported to ChainCatcher on the night of the attack that he had discovered the vulnerability that led to the attack while testing the official io.net mining script around mid-March, which allowed anyone to modify the user's mining machine. Additionally, he suspected that io.net had multiple security issues, including network system vulnerabilities.
COOK stated that he subsequently reported the vulnerability to the project team in the official Discord channel.
COOK mentioned that he was not the only one who discovered and discussed this vulnerability in the group, but ultimately they did not receive any feedback. Another community user, Box | 826.eth, also told ChainCatcher that he had discovered the issue a month ago.
Box | 826.eth stated, "Someone did what we wanted to do but didn't." COOK had similar thoughts about the attack but ultimately did not act on them, considering that the attack would not yield any benefits. Moreover, since this obvious vulnerability did not escalate, they speculated that some community users might want to exploit the vulnerability to modify their reward points.

From the information released by Box | 826.eth on the X platform, it appears that he publicly offered ultra-low-priced GPU services for running io.net, such as selling the use of a 4090 graphics card for 2 yuan a day. Given that this price is lower than the daily electricity cost of a 4090 graphics card, the authenticity of his graphics card is questionable. Whether COOK has ever sold similar computing power or running services has not yet been confirmed.
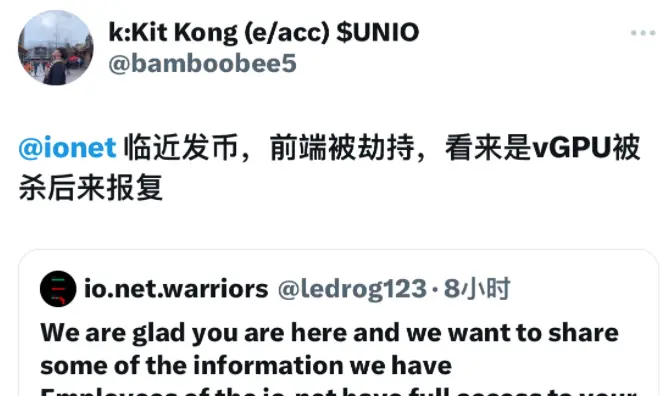
Since io.net has not yet issued tokens, such attacks generally do not yield bug bounties. What could be the motive behind the hacker attack? Crypto KOL @bamboobee5 speculated that it might be a retaliatory act following the recent crackdown on fake GPUs.
A relevant person from the io.net team revealed that the io.net security team had been marking fake GPUs but chose not to clean them up immediately, considering that these fake GPUs had developed new anti-detection measures. The team ultimately decided to concentrate on a crackdown before the token issuance.
This cleanup of fake GPUs may have left many fake GPU operators empty-handed.
Regarding the community users' reports of "officially unaddressed vulnerability feedback," ChainCatcher also sought verification from the io.net team.
The relevant person from the io.net team responded that after receiving community vulnerability feedback in March, their technical team began working on a system upgrade. However, for security reasons, they did not disclose the timeline and details of all security work to the community.
The person stated that the team began upgrading the system's API access with OKTA and Cloudflare in March, and partial upgrades were achieved last Tuesday. The plan for the latter part of the upgrade was to wait until the airdrop was completed. "The reason for this is that the latter part of the update requires users to restart their GPU Worker mining machines and execute new online and verification processes, which are no longer compatible with the old version, involving a complex learning and adjustment process for users. Therefore, the team originally planned to require users to execute this update when io.net released a major version update."
Following the sudden attack last night, the io.net team has now expedited the plan for the latter part of the API access upgrade. The io.net system is expected to return to normal within a day or two.
Token Issuance Delayed, How Will io.net Adjust Its Roadmap?
With the token issuance on the horizon, has io.net's roadmap been adjusted due to the attack?
According to previous official messages from io.net, the TGE for the IO token has been postponed to after April 28.
A relevant person from the io.net team further revealed that it is expected to occur around mid-May. The reason for the delay is not significantly related to the attack but is due to requests from trading platforms. The airdrop rewards will also be extended, and activities conducted during the extended period will also receive rewards.
In addition, the relevant person from the io.net team stated that most of the io.net roadmap should still proceed as planned, with increased investment in product security.
For some community users represented by @tonifungg, what worries them more than the attack is the subsequent security issues of the io.net team. With such a strong investment team and financial backing behind io.net, community users have high expectations for its security.
In response to community users' concerns, the relevant person from the io.net team stated that the AI + DEPIN development that io.net is engaged in is a relatively new field, and io.net is one of the faster-developing projects in this area. In exploring the framework of AI + DEPIN, it is difficult to avoid various bugs and even attacks.
On the other hand, the relevant person from the io.net team mentioned that the original expectation for the testnet capacity was in the tens of thousands, but it has now reached hundreds of thousands. The io.net team is conducting many urgent expansions, and they will actively address the issues and defects that may arise during rapid development.
This attack incident will also remind them to strengthen the development related to AI + DEPIN security. Currently, the entire io.net team consists of 70-80 people, with 50-60 technical personnel. The relevant person from the io.net team stated that they are in contact with some cybersecurity teams in the community to increase investment in security systems.



























