OKX Web3 Latest Release: On-Chain Anti-Phishing Safe Trading Guide
Author: 0xming
As we enter a new cycle, the risks of on-chain interactions are increasingly exposed with the rise in user activity. Phishers often use methods such as fake wallet websites, stealing social media accounts, creating malicious browser extensions, sending phishing emails and messages, and publishing fake applications to lure users into disclosing sensitive information, leading to asset losses. The forms and scenarios of phishing exhibit characteristics of diversity, complexity, and concealment.
For example, phishers typically create counterfeit websites that resemble legitimate wallet sites, enticing users to input their private keys or seed phrases. These counterfeit sites are often promoted through social media, emails, or advertisements, misleading users into believing they are accessing legitimate wallet services, thereby stealing users' assets. Additionally, phishers may impersonate wallet customer service or community administrators on social media platforms, forums, or instant messaging applications, sending users false messages requesting wallet information or private keys. This method exploits users' trust in official sources, leading them to disclose private information, among other tactics.
In summary, these cases highlight the threat of phishing behavior to Web3 wallet users. To help users enhance their security awareness when using Web3 wallets and protect their assets from loss, OKX Web3 has conducted in-depth community research and collected numerous phishing incidents encountered by Web3 wallet users, thereby distilling the four most common phishing scenarios faced by users. Through segmented case studies in different scenarios, we have written the latest guide on how Web3 users can conduct secure transactions, for everyone’s learning and reference.
Sources of Malicious Information
1. Replies to Popular Project Tweets
Replies to popular project tweets are one of the main ways malicious information spreads. Phishing Twitter accounts can mimic the official account in terms of logo, name, and verification badge, and even have follower counts in the tens of thousands. The only way to distinguish between them is------the Twitter handle (be cautious of similar characters), so users must stay vigilant.
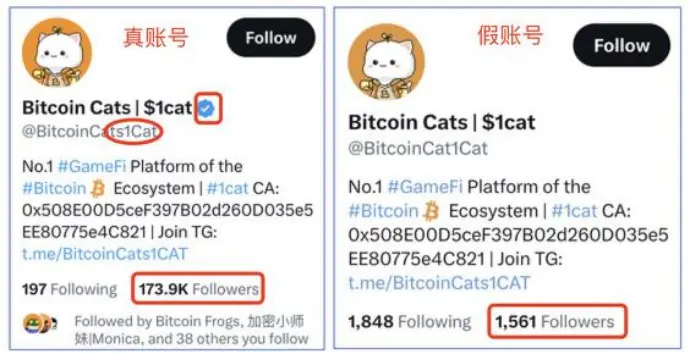
Moreover, often, fake accounts will deliberately reply under official tweets, but the reply content contains phishing links, easily misleading users into thinking they are official links, thus falling victim. Currently, some official accounts have started adding an "End of Tweet" note in their tweets to remind users to be cautious of potential phishing links in subsequent replies.
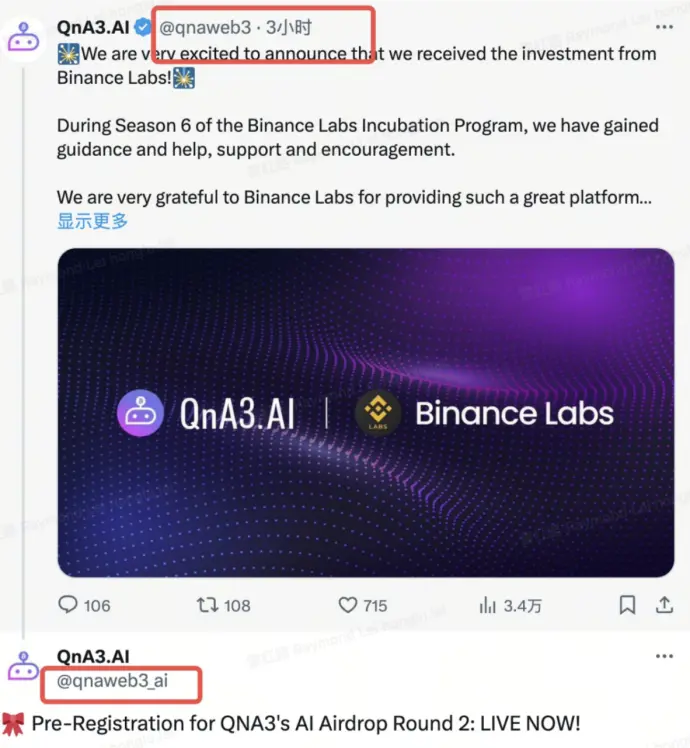
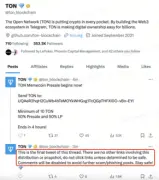
2. Compromised Official Twitter/Discord Accounts
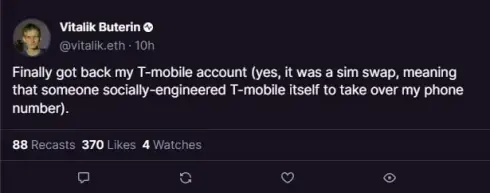
To increase credibility, phishers may also steal the official Twitter/Discord accounts of projects or KOLs, publishing phishing links in the name of the official account, making it easy for many users to fall for the scam. For instance, Vitalik's Twitter account and the official Twitter of the TON project have been compromised, with phishers taking the opportunity to publish false information or phishing links.
|-----------------------------------------------------------------------------------|-----------------------------------------------------------------------------------|
|  |
|  |
|
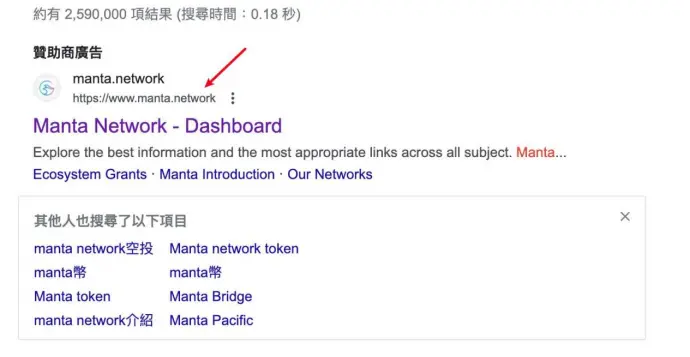
3. Google Search Ads
Phishers sometimes use Google search ads to publish malicious links, where users see the official domain name in the browser but are redirected to phishing links upon clicking.
4. Fake Applications
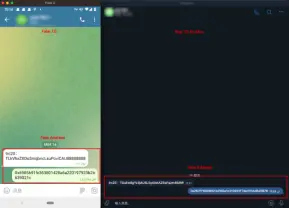
Phishers also lure users through fake applications. For example, when users download and install a fake wallet released by phishers, it can lead to the leakage of their private keys and asset loss. There have been instances where phishers modified Telegram installation packages, changing the on-chain addresses for receiving and sending tokens, resulting in users losing their assets.
|-----------------------------------------------------------------------------------|-----------------------------------------------------------------------------------|
|  |
|  |
|
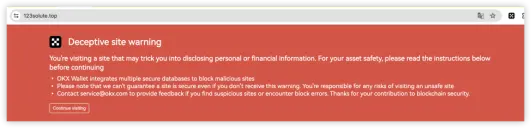
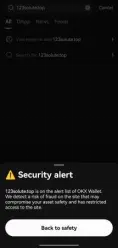
5. Countermeasures: OKX Web3 Wallet Supports Phishing Link Detection and Risk Alerts
Currently, OKX Web3 Wallet supports phishing link detection and risk alerts to help users better cope with the aforementioned issues. For instance, when users access websites through the OKX Web3 plugin wallet, if the domain is a known malicious domain, they will receive an immediate alert. Additionally, if users access third-party DApps on the Discover interface of the OKX Web3 APP, the OKX Web3 Wallet will automatically conduct risk detection on the domain. If it is a malicious domain, a warning will be issued to prevent users from accessing it.
|-----------------------------------------------------------------------------------|-----------------------------------------------------------------------------------|
|  |
|  |
|
Wallet Private Key Security
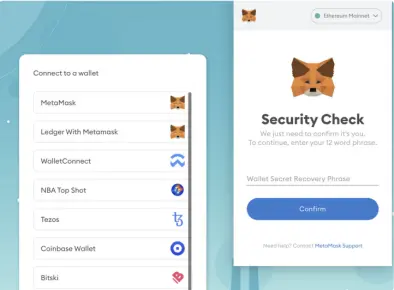
1. Project Interaction or Qualification Verification
Phishers often disguise themselves as plugin wallet pop-up pages or any other webpage during user project interactions or qualification verifications, requesting users to fill in their seed phrases/private keys. These are generally malicious websites, and users should remain vigilant.
|-----------------------------------------------------------------------------------|-----------------------------------------------------------------------------------|
|  |
|  |
|
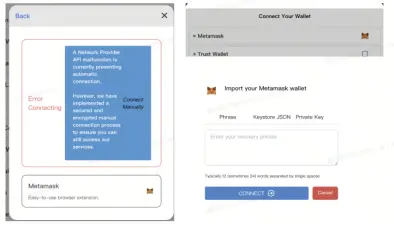
2. Impersonating Project Customer Service or Administrators
Phishers frequently impersonate project customer service or Discord administrators, providing URLs for users to input their seed phrases or private keys. This situation indicates that the other party is a phisher.
|-----------------------------------------------------------------------------------|----------------------------------------------------------------------------------|
|  |
|  |
|
3. Other Possible Paths for Seed Phrase/Private Key Leakage
Users' seed phrases and private keys can leak through many paths, commonly including computers being infected with trojan viruses, using fingerprint browsers for scraping, using remote control or proxy tools, screenshots of seed phrases/private keys saved in albums but uploaded by malicious apps, backups to the cloud where the cloud platform is hacked, monitoring during the input process of seed phrases/private keys, physical access to seed phrase/private key files/paper by nearby individuals, and developers pushing private key code to GitHub, etc.
In summary, users need to securely store and use their seed phrases/private keys to better ensure the security of their wallet assets. For instance, as a decentralized self-custody wallet, OKX Web3 Wallet has launched multiple backup methods for seed phrases/private keys, including iCloud/Google Drive cloud, manual, and hardware options, making it one of the most comprehensive wallets on the market for private key backup methods, providing users with a relatively secure way to store private keys. Regarding the issue of stolen private keys, OKX Web3 Wallet supports mainstream hardware wallet functions such as Ledger, Keystone, and Onekey, where private keys are stored in hardware wallet devices controlled by users, thus ensuring asset security. This means that OKX Web3 Wallet allows users to securely manage assets through hardware wallets while freely participating in on-chain token trading, NFT markets, and various DApp interactions. Additionally, OKX Web3 Wallet has now launched MPC non-custodial wallets and AA smart contract wallets to help users further simplify private key issues.
Four Classic Phishing Scenarios
Scenario 1: Stealing Main Chain Tokens
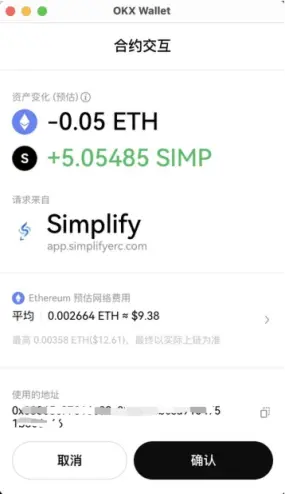
Phishers often name malicious contract functions with enticing names like Claim, SecurityUpdate, while the actual function logic is empty, thereby only transferring users' main chain tokens. Currently, OKX Web3 Wallet has launched a transaction pre-execution feature that displays asset and authorization changes after the transaction goes on-chain, further reminding users to pay attention to security. Moreover, if the interacting contract or authorization address is a known malicious address, a red security alert will be issued.
|-----------------------------------------------------------------------------------|-----------------------------------------------------------------------------------|
|  |
|  |
|
Scenario 2: Similar Address Transfers
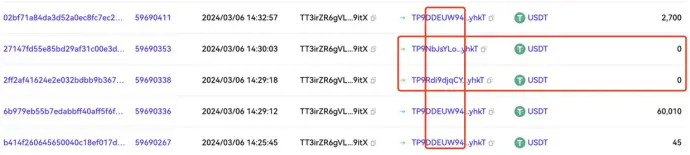
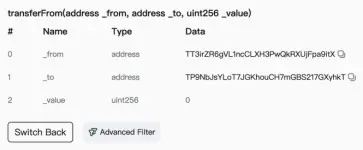
When a large transfer is detected, phishers will generate addresses that have several leading characters in common with the receiving address through address collision, using transferFrom for zero-amount transfers or using fake USDT for transfers of a certain amount, polluting the user's transaction history, hoping that users will later copy the wrong address from their transaction history for subsequent transfers, completing the scam.
https://www.oklink.com/cn/trx/address/TT3irZR6gVL1ncCLXH3PwQkRXUjFpa9itX/token-transfer

https://tronscan.org/#/transaction/27147fd55e85bd29af31c00e3d878bc727194a377bec98313a79c8ef42462e5f
|----------------------------------------------------------------------------------|-----------------------------------------------------------------------------------|
|  |
|  |
|
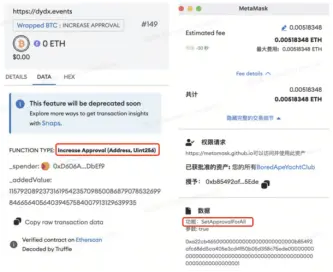
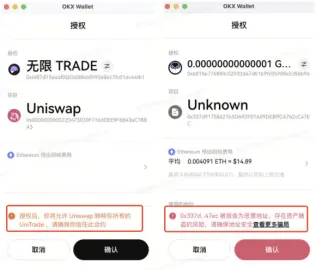
Scenario 3: On-Chain Authorization
Phishers typically induce users to sign approve/increaseAllowance/decreaseAllowance/setApprovalForAll transactions, as well as upgrade using Create2 to generate pre-calculated new addresses, bypassing security checks to deceive users into granting authorization. OKX Web3 Wallet will issue security alerts for authorization transactions, reminding users that this transaction is related to authorization and to be cautious of risks. Additionally, if the transaction authorization address is a known malicious address, a red information alert will be issued to prevent users from falling victim.
|-----------------------------------------------------------------------------------|----------------------------------------------------------------------------------|
|  |
|  |
|
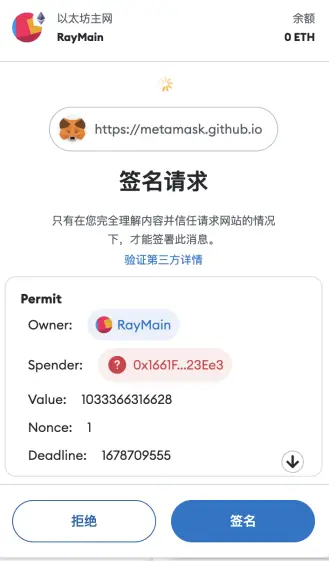
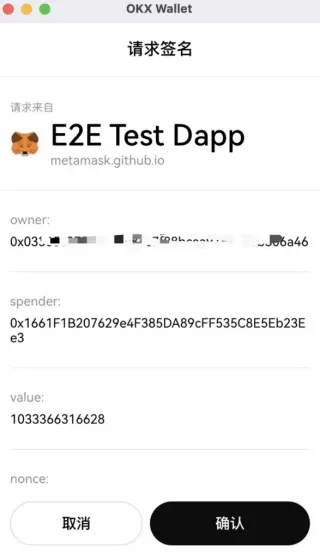
Scenario 4: Off-Chain Signatures
In addition to on-chain authorization, phishers also use off-chain signatures to conduct phishing. For example, ERC20 token authorization allows users to authorize another address or contract a certain amount, and the authorized address can transfer user assets through transferFrom. Phishers exploit this feature to commit fraud. Currently, OKX Web3 Wallet is developing risk alert features for such scenarios. When users sign offline signatures, the wallet will parse the signature authorization address, and if it matches a known malicious address, a risk alert will be issued to the user.
|-----------------------------------------------------------------------------------|-----------------------------------------------------------------------------------|
|  |
|  |
|
Other Phishing Scenarios
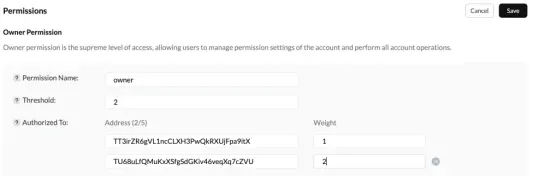
Scenario 5: TRON Account Permissions
This scenario is relatively abstract, where phishers gain TRON account permissions to control users' assets. TRON account permissions are similar to EOS, divided into Owner and Active permissions, and can be set up in a multi-signature format for permission control. For example, if the Owner threshold is set to 2, with two addresses having weights of 1 and 2 respectively, the first address being the user address with a weight of 1 cannot operate the account independently.
https://tronscan.org/#/wallet/permissions
https://www.oklink.com/trx/tx/1fe56345873425cf93e6d9a1f0bf2b91846d30ca7a93080a2ad69de77de5e45f
|----------------------------------------------------------------------------------|-----------------------------------------------------------------------------------|
|  |
|  |
|
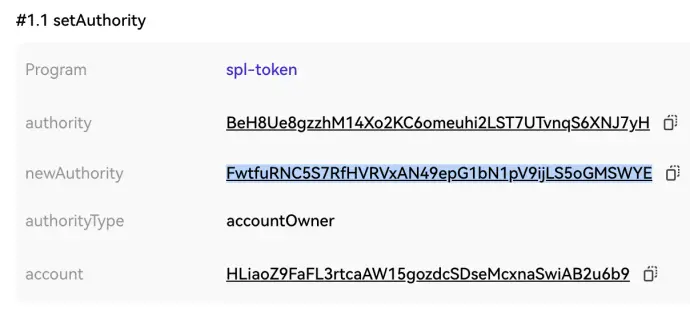
Scenario 6: Solana Token and Account Permissions
Phishers modify token ATA account ownership through SetAuthority, effectively transferring the token to a new Owner address. If users fall for this method, their assets are transferred to the phisher, etc. Additionally, if users sign an Assign transaction, the Owner of their normal account will be changed from the System Program to a malicious contract.
|-----------------------------------------------------------------------------------|-----------------------------------------------------------------------------------|
|  |
|  |
|
Scenario 7: EigenLayer Calling queueWithdrawal
Due to issues with the protocol's design mechanism, it can also be easily exploited by phishers. The queueWithdrawal call of the Ethereum-based middleware protocol EigenLayer allows specifying other addresses as withdrawers, and users may be phished into signing this transaction. Seven days later, the specified address can obtain the user's staked assets through completeQueuedWithdrawal.
Exploring the On-Chain World, Safety First
Using Web3 wallets securely is a key measure to protect assets, and users should take concrete precautions to guard against potential risks and threats. They can choose the industry-renowned, security-audited OKX Web3 Wallet to explore the on-chain world more safely and conveniently.
As the most advanced and feature-rich wallet in the industry, OKX Web3 Wallet is fully decentralized and self-custodied, supporting users to seamlessly engage with on-chain applications. It now supports over 85 public chains, with a unified app, plugin, and web interface covering five major areas: wallets, DEX, DeFi, NFT markets, and DApp exploration, and supports Ordinals markets, MPC, AA smart contract wallets, gas exchanges, and hardware wallet connections. Additionally, users can enhance wallet security by securely protecting their private keys and seed phrases, regularly updating wallet applications and operating systems, carefully handling links and information, and enabling multi-factor authentication.
In summary, in the on-chain world, asset security is paramount.
Users should remember these three Web3 security rules: do not fill in seed phrases/private keys on any webpage, be cautious when clicking the confirm button on wallet transaction interfaces, and links obtained from Twitter/Discord/search engines may be phishing links.