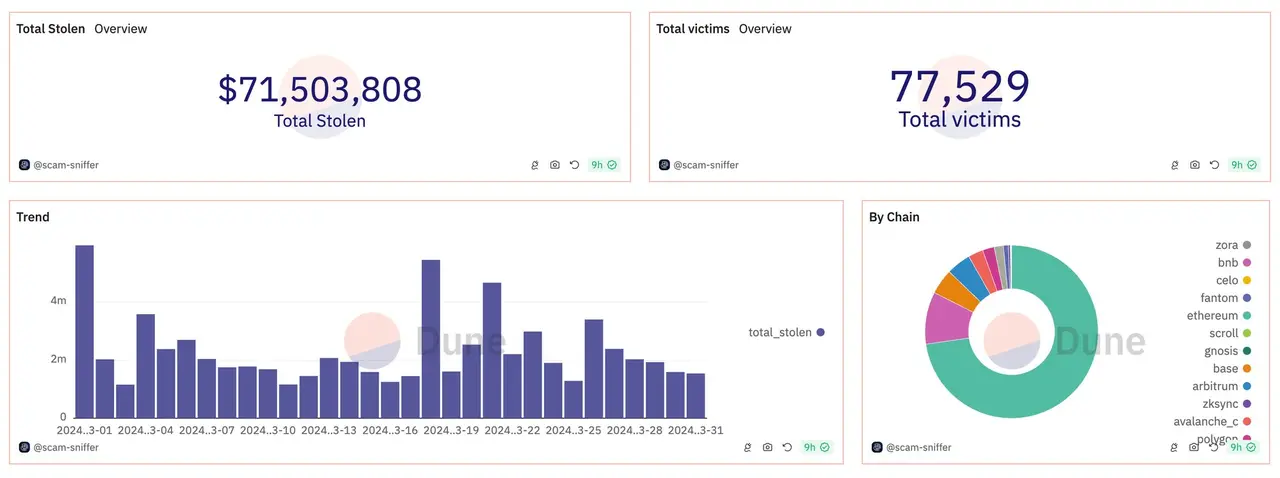
In the first quarter, phishing attacks caused a total loss of $173 million across the network, and new types of fraud leave people defenseless and helpless?
Recently, OKLink released the March 2024 Security Monthly Report, indicating that security incidents across the network in March resulted in losses of approximately $190 million. Among these, phishing incidents accounted for 16.72% of the losses, far exceeding the 9.64% loss from Rug Pull incidents, gradually becoming a new type of scam favored by hackers.
At the same time, Scam Sniffer released a phishing report for March, revealing that phishing scams in the cryptocurrency sector caused losses of $71 million, a 50% increase from February. In the first quarter of 2024, phishing scams resulted in a total loss of $173 million. Previously, Scam Sniffer reported that cryptocurrency phishing attacks in 2023 led to nearly $300 million in losses for 324,000 users.
So, what exactly are phishing attacks? Which projects have recently fallen victim to phishing attacks? How can ordinary users respond to these fraudulent tactics? The following text will address these questions.
What are the tactics of phishing attacks? Who are the unscrupulous attackers?
"Phishing" is a form of online deception targeting cryptocurrency users, which involves creating fake websites disguised as legitimate ones to steal users' authorizations, signatures, and crypto assets. The typical path of phishing attacks begins with the official Twitter account of a project being hacked, after which the hacker posts enticing phishing links on the official account, luring users to click the link and interact with their wallets, thereby directly stealing their assets.
In simple terms, hackers steal the Twitter accounts of project parties or KOLs, then post fake links accompanied by misleading text. Users, trusting the platform or KOL and tempted by potential benefits, naturally click on the links and urgently follow the hackers' prompts to complete a series of operations, such as entering their private keys, passwords, or other sensitive information on the fake website. Once this information is obtained by the attackers, the users' assets are quickly stolen. Behind this unscrupulous theft lies a massive profit chain—phishing attack software providers and their clients, who are the initiators of phishing attacks.
When phishing attacks are mentioned, many industry professionals immediately think of the scam group Pink Drainer. The Pink Drainer team is notorious for its high-profile attacks on platforms like Twitter and Discord, involving incidents such as Evomos, Pika Protocol, and Orbiter Finance.
Pink Drainer can provide malicious software as a service (Malware-as-a-Service, MaaS) to ill-intentioned attackers, allowing them to quickly establish malicious phishing websites and use this malware to obtain illegal assets.
Blockchain security company Beosin pointed out that these phishing websites use a crypto wallet stealing tool to lure users into signing requests. Once the request is signed, attackers can transfer NFTs and ERC-20 tokens from the victim's wallet. After a successful theft, Pink Drainer charges the attacker 30% of the stolen assets as a fee.
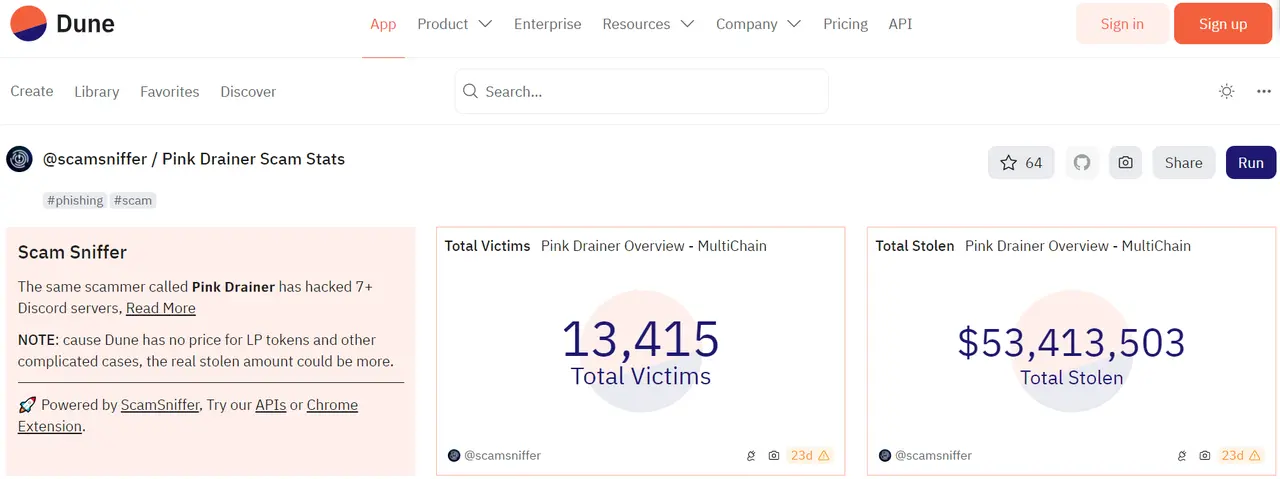
According to Dune data, as of April 4, phishing attacks initiated by Pink Drainer have victimized 13,415 individuals, with a total theft amount reaching $53.41 million across the industry.
The rampant phishing attacks put projects and investors in a potentially irreversible predicament
The claws of phishing attackers are reaching more and more project parties.
According to the March 2024 Security Monthly Report released by OKLink, there were a total of 50 incidents of scams and phishing attacks on official social media in March, primarily concentrated on X, Discord, and various phishing websites. This article summarizes some of the major projects or institutions that have encountered phishing attacks since the beginning of the year:
On January 5, the CertiK Twitter account was briefly hacked; on January 10, the SEC Twitter account was hacked due to the illegal occupation of the associated phone number; on January 26, the AltLayer Twitter account was attacked; on January 29, the Masa Twitter account was suspected to be hacked and posted a fake airdrop link; on February 3, the Twitter account of the founder of Blockworks was suspected to be hacked; on February 20, the official ARPA Twitter account was hacked and posted a fake token claiming link; on March 6, a phishing link was posted by a fake Aevo Twitter account; on March 12, the official beoble Twitter account was suspected to be hacked and posted a fake airdrop link; on March 15, the official Twitter account of Activision Blizzard was hacked; on March 20, the Twitter account of hardware wallet Trezor was hacked; on March 23, the Cointelegraph Twitter account was suspected to be hacked.
Among these, the most shocking was the hacking of the CertiK account, a leading security institution in the industry, highlighting the rapid technological updates of fraudsters. On the same day that the CertiK account was hacked on January 5, the attacker posted a phishing link using its account, but fortunately, CertiK quickly discovered the vulnerability and deleted the related tweets within minutes. Afterwards, CertiK stated on social media that this was a sustained attack.
Not everyone is as fortunate as CertiK when encountering phishing attacks. First, the users whose assets were stolen bear huge financial losses without any recourse, often venting their anger on the project parties; the project parties, also victims, often find themselves in a dilemma, needing to simultaneously initiate compensation procedures, crisis management, and technical maintenance, which brings significant losses to project operations. Some project parties have seen their asset prices plummet shortly after suffering phishing attacks, for example:
On March 6, according to Scam Sniffer monitoring, a user lost $736,000 worth of PAAL assets due to a phishing scam, and the price of PAAL dropped by 7.96% within one hour.
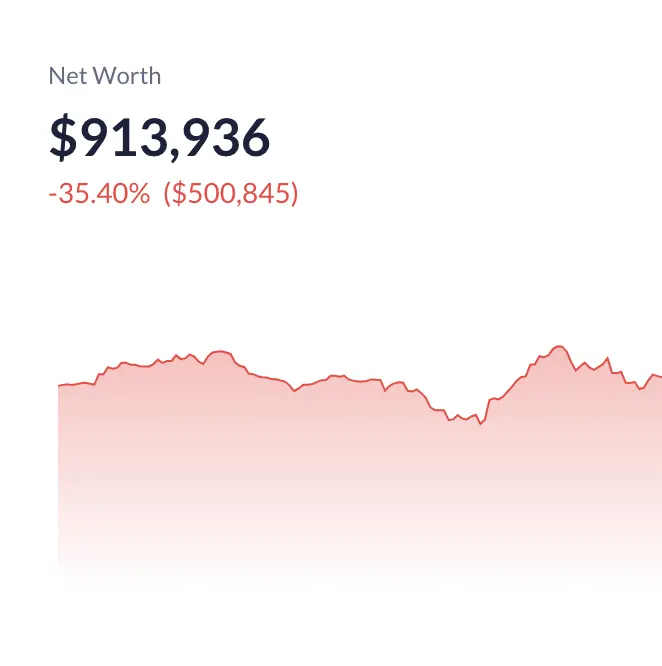
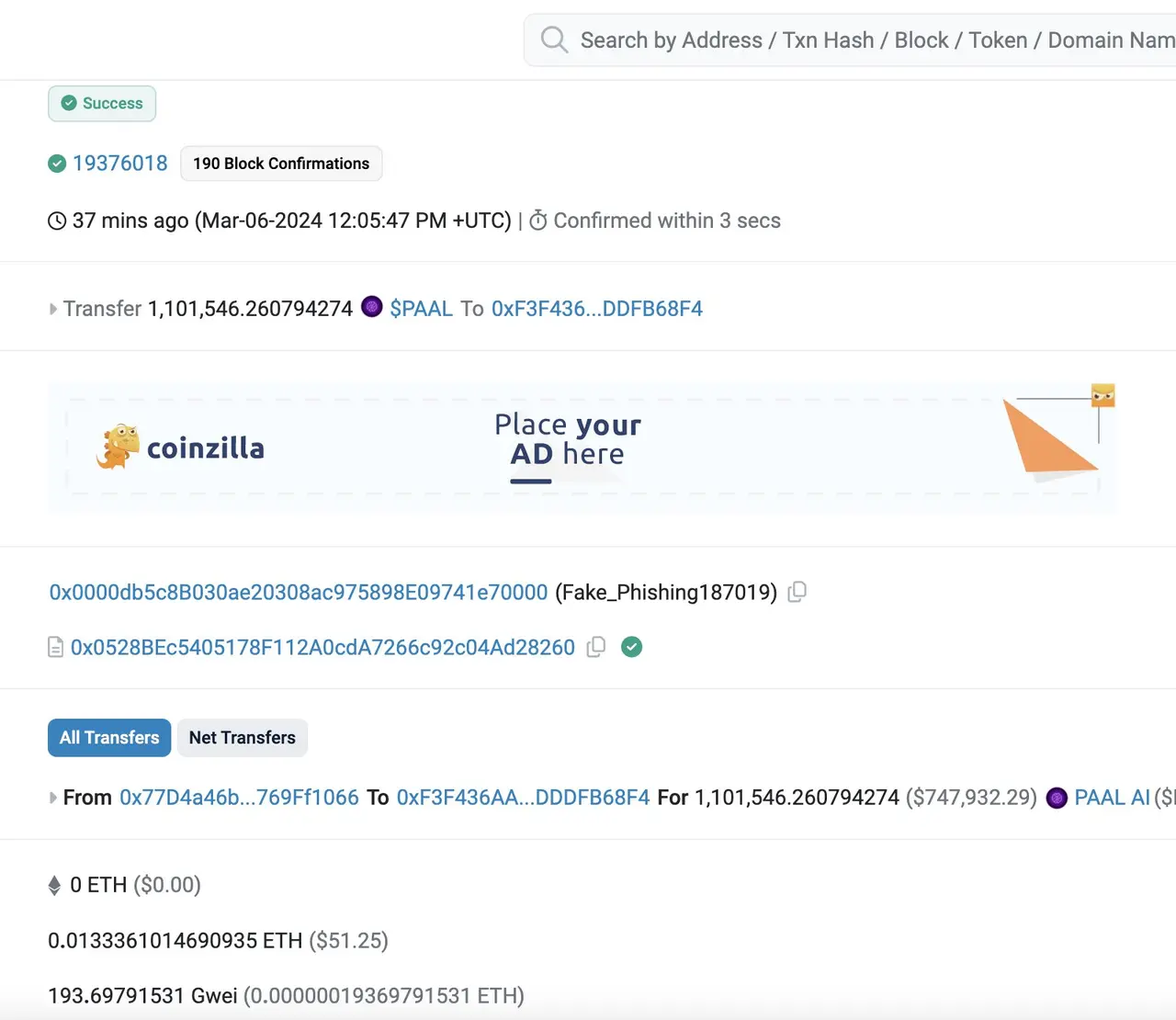
From this bloody lesson, it is clear that if phishing attacks continue to proliferate, the world of crypto assets will fall into an increasingly severe trust crisis.
How to identify phishing links: these simple and practical methods can help you avoid risks at critical moments
Analysis shows that phishing attacks are highly deceptive and covert, making it difficult for victims to trace the attackers hiding in the shadows afterward.
For users, it is essential to remain vigilant about all links at all times; otherwise, clicking on phishing links and following the attackers' instructions can lead to irreversible disasters. When uncertain whether a link is a phishing attack link, the following measures can be taken for identification and prevention:
- Check the link address: Phishing links often mimic the URLs of legitimate websites, but careful inspection can reveal subtle differences. For example, the URL of a counterfeit website may differ in spelling from the authentic site or use a similar domain name;
- Verify the security certificate: Check whether the website has a valid SSL certificate. Legitimate websites will have secure SSL encryption, and the browser's address bar will display a "lock" icon. Phishing sites often lack this security certificate;
- Domain resolution check: Use DNS query tools to check domain resolution and see if the domain registration information matches the claimed organization;
- Search engine query: Use search engines to find the website or organization claimed by the link and compare it with official information;
- Directly visit the official website: If you suspect a link is phishing, directly enter the official website address instead of clicking through the link;
- Contact official confirmation: For suspicious links, it is best to directly contact the official customer service for confirmation;
- Cultivate security awareness: Users should maintain a high level of security awareness at all times, avoiding clicking on unknown links and not casually providing personal private keys, passwords, or other sensitive information;
- Use security software: Install and use professional cybersecurity software that can detect and block phishing websites.
By employing the above methods, users in the crypto asset space can significantly reduce the risk of encountering phishing attacks and protect their asset security. At the same time, project developers should actively focus on cybersecurity education to enhance their own cybersecurity literacy.









