How AI is Revolutionizing Ethereum? A New Perspective on "AI + Blockchain"
Authors: Mirror Tang | Salus; Yixin Ren | Hongshan capital; Lingzhi Shi | Salus; Jiangyue Wang | Salus
Source: Salus
In the past year, as generative AI has repeatedly broken public expectations, the wave of AI productivity revolution has swept through the cryptocurrency space. We have seen many AI concept projects bringing a wave of wealth creation myths in the secondary market, while more and more developers are beginning to develop their own "AI + Crypto" projects.
However, upon closer observation, it can be found that there is a serious phenomenon of homogeneity among these projects, and most projects only stay at the level of improving "production relations," such as organizing computing power through decentralized networks or creating a "decentralized Hugging Face," etc. Very few projects attempt to achieve true integration and innovation from the underlying technology. We believe that the reason for this phenomenon lies in the existence of a "domain bias" between the fields of AI and blockchain. Although the intersection of the two is broad, few people can deeply understand both fields. For example, AI developers find it difficult to understand the technical implementation and historical infrastructure status of Ethereum, making it even harder to propose in-depth optimization solutions.
Taking machine learning (ML), the most basic branch of AI, as an example, it is a technology that allows machines to make decisions based on data without explicit programming instructions. Machine learning has shown great potential in data analysis and pattern recognition, and it has already become commonplace in web2. However, due to the limitations of the era at its inception, even in cutting-edge areas of blockchain technology innovation like Ethereum, its architecture, network, and governance mechanisms have not yet regarded machine learning as an effective tool for solving complex problems.
"Great innovations often arise from cross-disciplinary fields." The purpose of writing this article is to help AI developers better understand the blockchain world while providing new ideas for developers in the Ethereum community. In this article, we first introduce the technical implementation of Ethereum, and then propose a plan to apply machine learning, a foundational AI algorithm, to the Ethereum network to enhance its security, efficiency, and scalability. We hope to use this case as a starting point to present some different perspectives from those in the market, inspiring more "AI + Blockchain" innovative cross-combinations within the developer ecosystem.
Technical Implementation of Ethereum
Basic Data Structure
The essence of blockchain is a chain connecting blocks, and the key to distinguishing chains is the chain configuration, which is an essential part of a blockchain's genesis. For Ethereum, the chain configuration is used to distinguish different chains within Ethereum while identifying some important upgrade protocols and landmark events. For example, DAOForkBlock marks the block height of Ethereum's hard fork due to the DAO attack, and ConstantinopleBlock marks the block height of the Constantinople upgrade. For larger upgrades that include numerous improvement proposals, special fields are set to identify the corresponding block heights. Additionally, Ethereum includes various test networks and the main network, uniquely identified by ChainID to represent the corresponding network ecology.
The genesis block, as the zero-th block of the entire blockchain, is directly or indirectly referenced by other blocks. Therefore, when a node starts, it must load the correct genesis block information, which must not be arbitrarily modified. The configuration information of the genesis block includes the aforementioned chain configuration, along with additional fields such as relevant mining rewards, timestamps, difficulty, and gas limits. It is important to note that Ethereum's consensus mechanism has shifted from a proof-of-work mining mechanism to a proof-of-stake.
Ethereum accounts are divided into external accounts and contract accounts, where external accounts are uniquely controlled by private keys, while contract accounts have no private key control and can only be operated by calling contract execution code through external accounts. They both contain a unique address. The Ethereum world state is a tree of Ethereum accounts, where each account corresponds to a leaf node that stores the state of that account (various account information and code information).
Transactions: As a decentralized platform, Ethereum's essence is for transactions and contracts. Ethereum blocks are packed transactions along with some other related information. Specifically, blocks are divided into two parts: the block header and the block body. The block header data contains evidence that connects all blocks into a chain, which we can understand as the previous block hash, as well as the state root, transaction root, receipt root, and several other additional data such as difficulty indicators and nonce counts. The block body stores the list of transactions and the list of uncle block headers (since Ethereum has transitioned to proof-of-stake, uncle block references no longer exist).
Transaction receipts provide the results and additional information after transaction execution, which cannot be directly obtained by merely viewing the transaction itself. Specifically, the information contained can be divided into: consensus content, transaction information, and block information, including whether the transaction processing was successful, transaction logs, and gas consumption information. Analyzing the information in the receipt can help debug smart contract code and optimize gas consumption. It also provides a confirmation indicating that the transaction has been processed by the network, and the results and impacts of the transaction can be viewed.
In Ethereum, gas fees can be simply understood as transaction fees. When you send tokens, execute contracts, transfer Ether, or perform various operations on this block, these operations require gas fees. The Ethereum computer consumes network resources to process this transaction, so you must pay gas fees to have the computer work for you. Ultimately, the fuel fees are paid to miners as transaction fees, and the specific fee calculation formula can be understood as Fee = Gas Used * Gas Price, which is the actual consumption multiplied by the unit price of consumption, where the unit price is set by the transaction initiator. The amount often determines the speed at which the transaction is confirmed on-chain. If set too low, the transaction may not be executed, and there is also a need to set a gas limit to avoid unexpected gas consumption due to errors in the contract.
Transaction Pool
In Ethereum, there are a large number of transactions. Compared to centralized systems, the number of transactions processed per second in decentralized systems is evidently disappointing. Due to the influx of numerous transactions into nodes, nodes need to maintain a transaction pool to manage these transactions correctly. Transaction broadcasting is done through P2P; specifically, a node will broadcast executable transactions to its neighboring nodes, which will then broadcast the transaction to their neighboring nodes. Through this method, a transaction can spread throughout the entire Ethereum network within 6 seconds.
Transactions in the transaction pool are divided into executable transactions and non-executable transactions. Executable transactions have higher priority and will be executed and packed into blocks, while all newly entered transactions in the transaction pool are non-executable transactions, which will later become executable. Executable transactions and non-executable transactions are recorded in the pending container and the queue container, respectively.
Additionally, the transaction pool maintains a local transaction list. Local transactions have multiple advantages: they have higher priority, are not affected by transaction volume limits, and can be immediately reloaded into the transaction pool when the node is restarted. The local persistent storage of local transactions is achieved through journals (reloading upon node restart), aimed at not losing incomplete local transactions and will be updated regularly.
Before entering the queue, transactions are verified for legality, including various types of checks, such as preventing DOS attacks, preventing negative transactions, and checking transaction gas limits, etc. The simple composition of the transaction pool can be divided into: queue + pending (two components make up all transactions). After completing the legality checks, further checks are performed, including checking whether the transaction queue has reached its limit, and then determining whether remote transactions (non-local transactions) are the lowest in the transaction pool, replacing the lowest-priced transaction in the pool. For executable transaction replacements, by default, only transactions that increase the fee by 10% are allowed to replace already pending transactions, and the replaced transaction is stored as a non-executable transaction. Additionally, during the maintenance of the transaction pool, invalid and over-limit transactions will be deleted, and transactions that meet the conditions will be replaced.
Consensus Mechanism
The early consensus theory of Ethereum was still based on the difficulty value hash calculation method, meaning that the hash value of the block must be calculated to meet the target difficulty value condition for the block to be valid. Since Ethereum's consensus algorithm has now shifted from POW to POS, we will not elaborate on mining-related theories here. Briefly, the POS algorithm was completed with the merge of the beacon chain in September 2022, specifically, in POS-based Ethereum, the block production time is stabilized at 12 seconds, and users stake their Ether to gain the right to become validators. A batch of validators is randomly selected from users who participate in staking, and in each round cycle, which contains 32 slots, a validator is selected as the proposer, who produces the block, while the remaining validators for that slot form a committee to verify the legality of the proposer’s block and make judgments on the legality of the blocks from the previous round. The POS algorithm significantly stabilizes and increases the block production speed while greatly avoiding the waste of computational resources.
Signature Algorithm
Ethereum follows Bitcoin's signature algorithm standard, also using the secp256k1 curve, with the specific signature algorithm employing ECDSA. This means that the calculated signature is derived from the hash of the original message, and the entire signature consists simply of R + S + V. Each calculation introduces a random number, where R + S is the original output of ECDSA. The last field, V, is called the recovery field, indicating the number of times to look up when successfully recovering the public key from the content and signature, as there may be multiple coordinate points that meet the requirements based on the R value in the elliptic curve.
The entire process can be simply summarized as follows: transaction data and signer-related information are RLP encoded and hashed, and then signed with the private key through ECDSA to obtain the final signature, where the curve used in ECDSA is the secp256k1 elliptic curve. Finally, combining the signature data with the transaction data yields a signed transaction data that can be broadcasted.
Ethereum's data structure not only relies on traditional blockchain technology but also introduces the Merkle Patricia Tree, also known as the Merkle compressed prefix tree, to efficiently store and verify large amounts of data. MPT combines the cryptographic hash function of Merkle trees with the key path compression feature of Patricia trees, providing a solution that ensures data integrity while supporting fast lookups.
Merkle Compressed Prefix Tree
In Ethereum, MPT is used to store all state and transaction data, ensuring that any changes to the data will be reflected in the root hash of the tree. This means that by verifying the root hash, the integrity and accuracy of the data can be proven without checking the entire database. MPT consists of four types of nodes: leaf nodes, extension nodes, branch nodes, and empty nodes, which together form a tree that can adapt to dynamic data changes. Each time data is updated, MPT reflects these changes through the addition, deletion, or modification of nodes while updating the root hash of the tree. Since each node is encrypted through a hash function, any slight change to the data will result in a significant change to the root hash, thereby ensuring the security and consistency of the data. Additionally, the design of MPT supports "light client" verification, allowing nodes to verify the existence or state of specific information by only storing the root hash of the tree and necessary path nodes, greatly reducing the demand for data storage and processing.
Through MPT, Ethereum not only achieves efficient data management and rapid access but also ensures the security and decentralization of the network, supporting the operation and development of the entire Ethereum network.
State Machine
The core architecture of Ethereum integrates the concept of a state machine, where the Ethereum Virtual Machine (EVM) is the runtime environment for executing all smart contract code, and Ethereum itself can be viewed as a globally shared state transition system. The execution of each block can be seen as a state transition process, moving from one globally shared state to another. This design not only ensures the consistency and decentralization of the Ethereum network but also makes the execution results of smart contracts predictable and immutable.
In Ethereum, the state refers to the current information of all accounts, including the balance of each account, stored data, and the code of smart contracts. Whenever a transaction occurs, the EVM calculates and transitions the state based on the transaction content, and this process is efficiently and securely recorded through MPT. Each state transition not only changes the account data but also leads to updates in the MPT, reflected in the changes to the root hash of the tree.
The relationship between EVM and MPT is crucial because MPT provides a guarantee of data integrity for Ethereum's state transitions. When the EVM executes a transaction and changes the account state, the relevant MPT nodes are updated to reflect these changes. Since each node of MPT is linked through hashes, any modification to the state will cause a change in the root hash, which is then included in the new block, ensuring the consistency and security of the entire Ethereum state. Below, we introduce the EVM virtual machine.
EVM
The EVM virtual machine is fundamental to the entire Ethereum's construction of smart contract execution state transitions. Thanks to the EVM, Ethereum can be truly envisioned as a world computer. The EVM is Turing complete, meaning that smart contracts on Ethereum can execute any complex logical computation, and the introduction of the gas mechanism successfully prevents infinite loops in contracts, ensuring the stability and security of the network. From a more in-depth technical perspective, the EVM is a stack-based virtual machine that uses Ethereum-specific bytecode to execute smart contracts. Developers typically use high-level languages, such as Solidity, to write smart contracts, which are then compiled into bytecode that the EVM can understand for execution. The EVM is key to Ethereum's blockchain innovation capabilities; it not only supports the operation of smart contracts but also provides a solid foundation for the development of decentralized applications. Through the EVM, Ethereum is shaping a decentralized, secure, and open digital future.
Historical Review of Ethereum
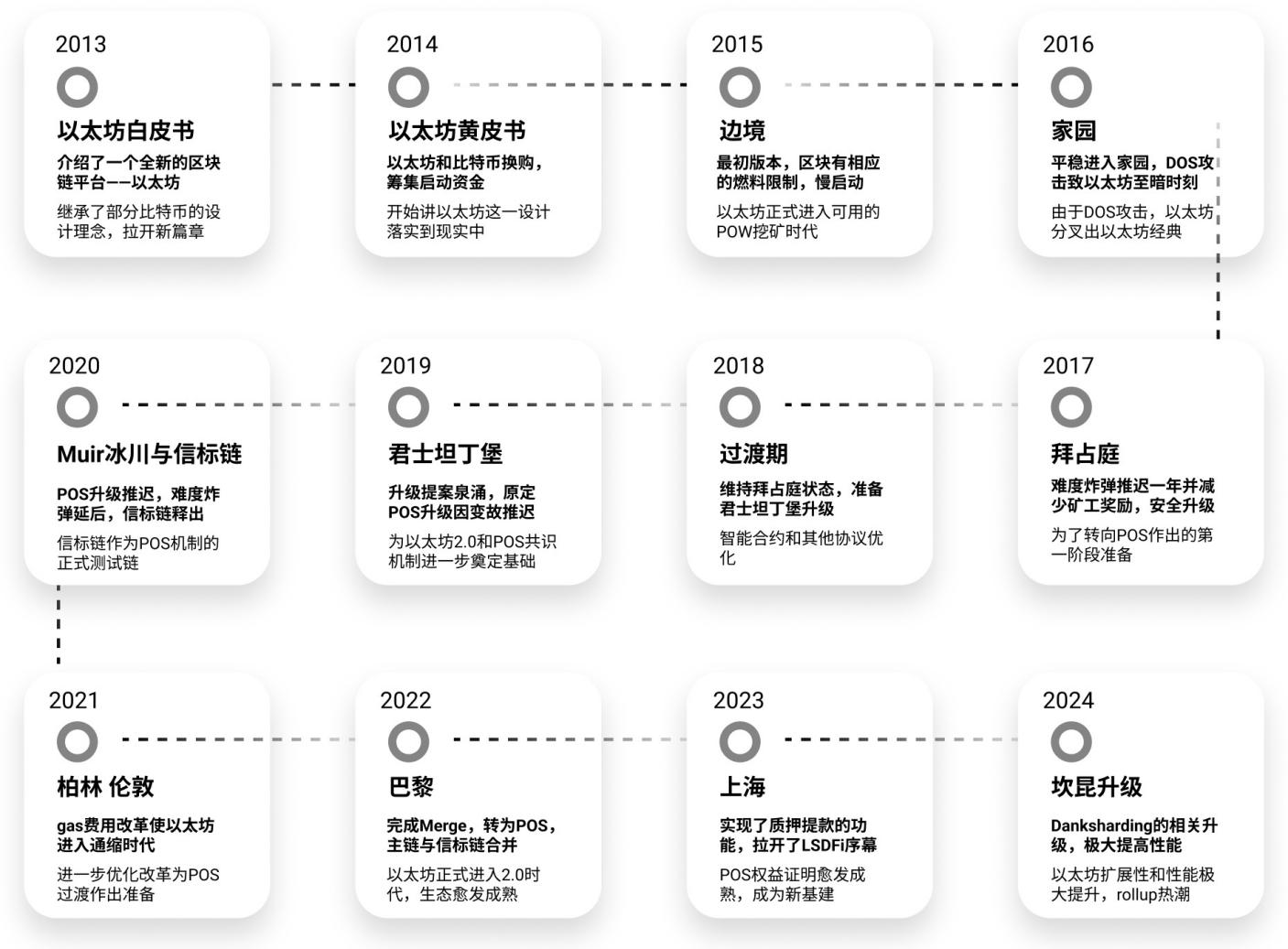
Figure 1 Historical Review of Ethereum
Challenges Facing Ethereum: Security
Smart contracts are computer programs that run on the Ethereum blockchain. They allow developers to create and publish various applications, including but not limited to lending applications, decentralized exchanges, insurance, secondary financing, social networks, and NFTs. The security of smart contracts is crucial for these applications. These applications are directly responsible for handling and controlling cryptocurrencies, and any vulnerabilities in smart contracts or malicious attacks on them pose a direct threat to the safety of funds, potentially leading to significant economic losses. For example, on February 26, 2024, the DeFi lending protocol Blueberry Protocol suffered an attack due to a logical flaw in its smart contract, resulting in a loss of approximately $1,400,000.
The vulnerabilities of smart contracts are multifaceted, covering unreasonable business logic, improper access control, insufficient data validation, reentrancy attacks, and DOS (Denial of Service) attacks, among others. These vulnerabilities can lead to execution issues in contracts, affecting the effective operation of smart contracts. Taking DOS attacks as an example, this type of attack consumes network resources by sending a large number of transactions from the attacker, making it difficult for transactions initiated by normal users to be processed in a timely manner, which can degrade user experience. Moreover, this can also lead to an increase in transaction gas fees. Because in situations where network resources are tight, users may need to pay higher fees to have their transactions prioritized.
In addition, users on Ethereum also face investment risks, with the safety of funds being threatened. For instance, "junk coins" are used to describe cryptocurrencies that are considered to have little value or no long-term growth potential. Junk coins are often used as tools for scams or for price manipulation strategies involving pump and dump. The investment risk of junk coins is high and can lead to significant financial losses. Due to their low price and low market capitalization, they are easily manipulated and volatile. Such coins are often used in pump and dump schemes and honeypot scams, where fake projects lure investors and steal their funds. Another common risk associated with junk coins is the "Rug Pull," where creators suddenly remove all liquidity from the project, causing the token's value to plummet. These scams are typically marketed through false partnerships and endorsements, and once the token price rises, the scammers sell their tokens, profiting and disappearing, leaving investors with worthless tokens. Additionally, investing in junk coins diverts attention and resources away from legitimate cryptocurrencies that have real applications and growth potential. Besides junk coins, air coins and Ponzi coins are also quick profit schemes. For users lacking expertise and experience, distinguishing them from legitimate cryptocurrencies is particularly challenging.
Efficiency
Two very direct indicators for assessing Ethereum's efficiency are transaction speed and gas fees. Transaction speed refers to the number of transactions the Ethereum network can process in a unit of time. This metric directly reflects the processing capacity of the Ethereum network; the faster the speed, the higher the efficiency. Each transaction in Ethereum requires a certain gas fee to compensate miners for validating the transaction. The lower the gas fee, the higher the efficiency of Ethereum.
A decrease in transaction speed will lead to an increase in gas fees. Generally, when transaction processing speed decreases, due to limited block space, the competition for transactions entering the next block may increase. To stand out in this competition, traders often raise gas fees, as miners tend to prioritize transactions with higher gas fees when validating transactions. Thus, higher gas fees can degrade user experience.
Transactions are merely the basic activities within Ethereum. In this ecosystem, users can also engage in various activities such as lending, staking, investing, and insurance. All of these can be accomplished through specific DApps. However, given the wide variety of DApps and the lack of personalized recommendation services similar to traditional industries, users may feel confused when choosing applications and products that suit them. This situation can lead to decreased user satisfaction, thereby affecting the overall efficiency of the Ethereum ecosystem.
Taking lending as an example, some DeFi lending platforms use over-collateralization mechanisms to maintain the security and stability of their platforms. This means that borrowers need to put up more assets as collateral, which cannot be used for other activities during the borrowing period. This can lead to a decrease in the capital utilization rate for borrowers, thereby reducing market liquidity.
Applications of Machine Learning in Ethereum
Machine learning models, such as RMF models, Generative Adversarial Networks (GAN), decision tree models, K-Nearest Neighbors (KNN), and DBSCAN clustering algorithms, are playing important roles in Ethereum. The application of these machine learning models in Ethereum can help optimize transaction processing efficiency, enhance the security of smart contracts, achieve user segmentation for more personalized services, and contribute to maintaining the stable operation of the network.
Algorithm Introduction
Machine learning algorithms are a set of instructions or rules used to analyze data, learn patterns within the data, and make predictions or decisions based on these learnings. They learn and improve automatically from the provided data without the need for explicit programming instructions from humans. Machine learning models, such as RMF models, Generative Adversarial Networks (GAN), decision tree models, K-Nearest Neighbors (KNN), and DBSCAN clustering algorithms, are playing important roles in Ethereum. The application of these machine learning models in Ethereum can help optimize transaction processing efficiency, enhance the security of smart contracts, achieve user segmentation for more personalized services, and contribute to maintaining the stable operation of the network.
- Bayesian Classifier
The Bayesian classifier is an efficient classifier among various statistical classification methods, aimed at minimizing the probability of classification errors or minimizing average risk within a specific cost framework. Its design philosophy is deeply rooted in Bayes' theorem, allowing it to calculate the probability of an object belonging to a certain class given known features, making decisions based on the posterior probability of the object. Specifically, the Bayesian classifier first considers the prior probability of the object, then applies Bayes' formula to integrate observational data, thereby updating the belief about the classification of the object. Among all possible classifications, the Bayesian classifier selects the class with the highest posterior probability, assigning the object to that class. The core advantage of this method lies in its ability to naturally handle uncertainty and incomplete information, making it a powerful and flexible tool suitable for a wide range of applications.
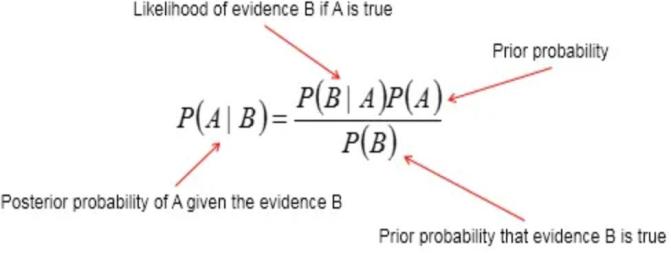
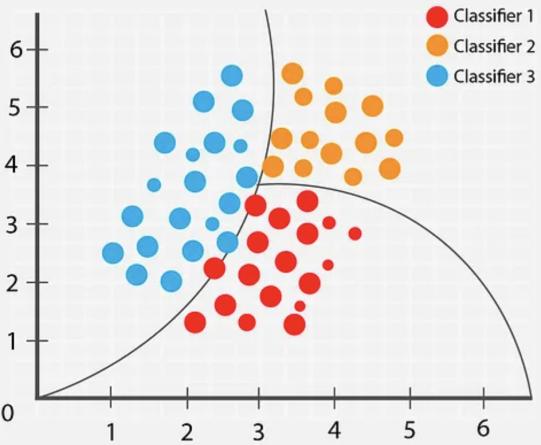
Figure 2 Bayesian Classifier
As shown in Figure 2, in supervised machine learning, data and probability models based on Bayes' theorem are used for classification decisions. By utilizing likelihood and prior probabilities of categories and features, the Bayesian classifier calculates the posterior probabilities of data points belonging to each category and assigns the data points to the category with the highest posterior probability. In the scatter plot on the right, the classifier attempts to find a curve that best separates the differently colored points, thereby minimizing classification errors.
- Decision Tree
The decision tree algorithm is commonly used in classification and regression tasks, employing a hierarchical judgment approach to split based on features with high information gain rates, thus training a decision tree. In simple terms, the entire algorithm can learn a decision rule from the data to judge the value of variables, specifically in implementation, it can decompose complex decision processes into several simpler sub-decision processes. Through this derivation method, each simpler decision judgment is derived from a parent decision criterion, forming a tree structure.
As seen in Figure 3, each node represents a decision, establishing a judgment criterion for a certain attribute, while branches represent the outcomes of decisions. Each leaf node represents the final predicted result and category. From the algorithm's composition perspective, the decision tree model is relatively intuitive and easy to understand, possessing strong interpretability.
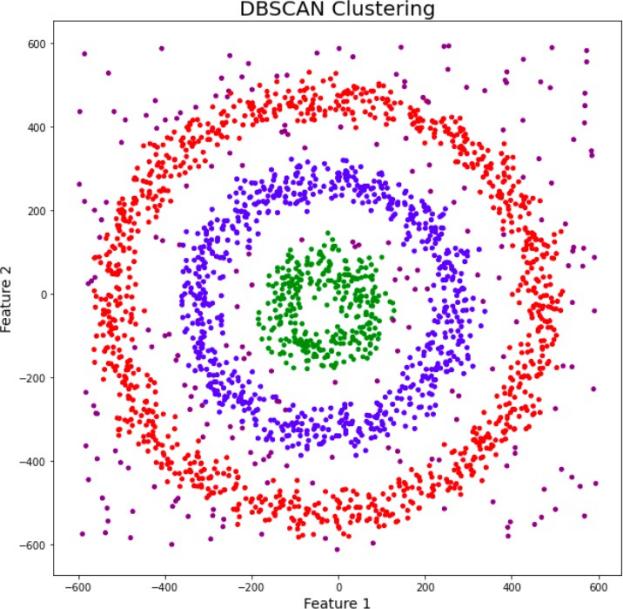
- DBSCAN Algorithm
DBSCAN (Density-Based Spatial Clustering of Applications with Noise) is a density-based spatial clustering algorithm that works particularly well for non-connected datasets. This algorithm can discover clusters of arbitrary shapes without needing to specify the number of clusters in advance and is robust against outliers in the dataset. The algorithm can effectively identify outliers in noisy datasets, where noise or outliers are defined as points in low-density regions, as shown in Figure 4.
- KNN Algorithm
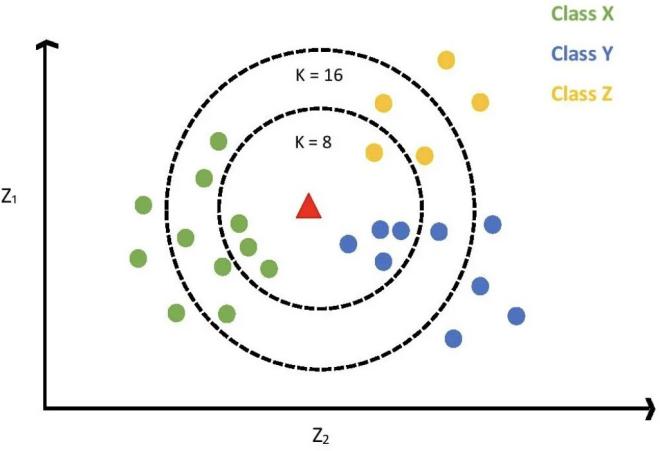
The K-Nearest Neighbors (KNN) algorithm can be used for both classification and regression. In classification problems, it determines the category of the item to be classified based on a voting mechanism; in regression problems, it calculates the average or weighted average of the K nearest samples to make predictions.
As shown in Figure 5, the KNN algorithm works in classification by finding the K nearest neighbors of a new data point and predicting the category of the new data point based on these neighbors' categories. If K=1, the new data point is simply assigned to the category of its nearest neighbor. If K > 1, a voting method is typically used to determine the category of the new data point, meaning that the new data point will be assigned to the category that has the most neighbors. When the KNN algorithm is used for regression problems, the basic idea is the same, with the result being the average of the output values of the K nearest samples.
- Generative AI
Generative AI is a type of AI technology that can generate new content (such as text, images, music, etc.) based on input requirements. Its background is based on advancements in machine learning and deep learning, particularly in applications such as natural language processing and image recognition. Generative AI learns patterns and associations from large amounts of data and then generates entirely new output content based on this learned information. The key to generative AI lies in model training, which requires excellent data for learning and training. During this process, the model improves its ability to generate new content by analyzing and understanding the structure, patterns, and relationships within the dataset.
Transformer
The Transformer, as the cornerstone of generative AI, innovatively introduces the attention mechanism, allowing for processing information that can focus on key aspects while also taking a global view. This unique capability has made the Transformer shine in the field of text generation. Utilizing the latest natural language processing models, such as GPT (Generative Pre-trained Transformer), to understand user application requirements expressed in natural language and automatically convert them into executable code can reduce development difficulty and significantly improve efficiency.
As shown in Figure 6, the introduction of multi-head attention mechanisms and self-attention mechanisms, combined with residual connections and fully connected neural networks, along with previous word embedding technologies, has greatly enhanced the performance of generative models related to natural language processing.
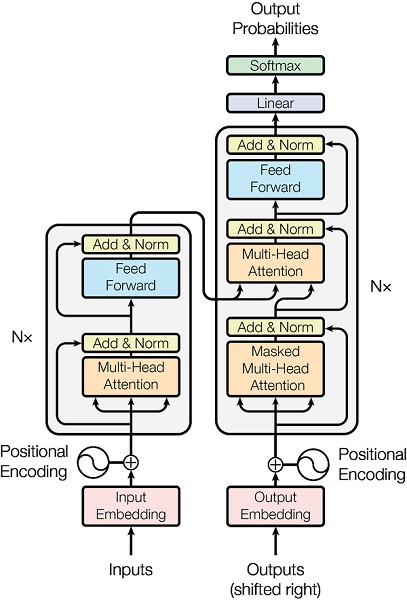
Figure 6 Transformer Model
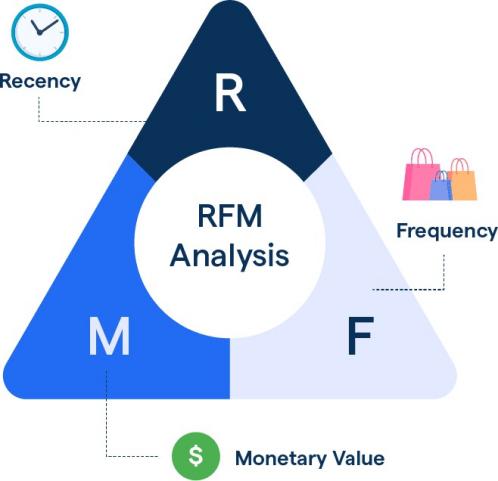
- RFM Model Introduction:
The RFM model is an analysis model based on user purchasing behavior. By analyzing user transaction behavior, it can identify user groups of different values. This model scores users based on their recent purchase time (R), purchase frequency (F), and purchase amount (M).
As shown in Figure 7, these three indicators together form the core of the RFM model. The model scores users based on these three dimensions and ranks them according to their scores to identify the most valuable user groups. Moreover, this model can effectively segment customers into different groups to achieve user segmentation functionality.
Possible Applications
In applying machine learning technologies to address the security challenges of Ethereum, we have researched four main aspects:
Identifying and filtering malicious transactions based on Bayesian classifiers. By constructing a Bayesian classifier, it can identify and filter potential junk transactions, including but not limited to large, frequent, small transactions that lead to DOS attacks. This method effectively maintains the network's health status and ensures the stable operation of the Ethereum network by analyzing transaction features such as gas prices and transaction frequency.
Generating secure smart contract code that meets specific requirements. Generative Adversarial Networks (GAN) and Transformer-based generative networks can be used to generate smart contract code that meets specific requirements while ensuring the security of the code as much as possible. However, there are differences in the types of data relied upon for training the models; the former mainly relies on insecure code samples, while the latter does the opposite.
By training GANs to learn existing secure contract patterns and constructing self-adversarial models to generate potentially insecure code, the model can learn to identify these insecurities, ultimately achieving the automatic generation of high-quality, more secure smart contract code. Utilizing Transformer-based generative network models, by learning from a large number of secure contract examples, can generate contract code that meets specific needs and optimizes gas consumption, which will undoubtedly further enhance the efficiency and security of smart contract development.
Conducting smart contract risk analysis based on decision trees. By analyzing features of smart contracts such as function call frequency, transaction values, and source code complexity using decision trees, potential risk levels of contracts can be effectively identified. By analyzing the operational patterns and code structures of contracts, potential vulnerabilities and risk points can be predicted, providing developers and users with assessments of safety. This method is expected to significantly improve the security of smart contracts within the Ethereum ecosystem, thereby reducing losses caused by vulnerabilities or malicious code.
Constructing an evaluation model for cryptocurrencies to reduce investment risks.
By analyzing multidimensional information such as transaction data, social media activity, and market performance of cryptocurrencies using machine learning algorithms, a model can be constructed to predict the likelihood of junk coins. This model can provide valuable references for investors, helping them avoid investment risks and promoting the healthy development of the cryptocurrency market.
In addition, the application of machine learning also has the potential to further enhance the efficiency of Ethereum. We can explore the following three key dimensions in depth:
Optimizing the decision tree application for the transaction pool queuing model. The decision tree can effectively optimize the queuing mechanism of the Ethereum transaction pool. By analyzing transaction characteristics such as gas prices and transaction sizes, the decision tree can optimize the selection and queuing order of transactions. This method can significantly improve transaction processing efficiency, effectively reduce network congestion, and lower users' transaction waiting times.
Segmenting users and providing personalized services. The RFM model (Recency, Monetary value, Frequency), as an analysis tool widely used in customer relationship management, can effectively segment users by evaluating their recent transaction time (Recency), transaction frequency (Frequency), and transaction amount (Monetary value). Applying the RFM model on the Ethereum platform can help identify high-value user groups, optimize resource allocation, and provide more personalized services, thereby improving user satisfaction and the overall efficiency of the platform.
The DBSCAN algorithm can also analyze user transaction behaviors, helping to identify different user groups on Ethereum, further providing more customized financial services for different users. This user segmentation strategy can optimize marketing strategies and enhance customer satisfaction and service efficiency.
Credit scoring based on KNN.
The K-Nearest Neighbors (KNN) algorithm can analyze the transaction history and behavior patterns of Ethereum users to perform credit scoring, which is extremely important in financial activities such as lending. Credit scoring can help financial institutions and lending platforms assess borrowers' repayment capabilities and credit risks, leading to more accurate lending decisions. This can prevent over-lending and improve market liquidity.
Future Directions
From the perspective of macro capital allocation, as the largest global distributed computer, Ethereum requires significant investment at the infrastructure level to attract more developers from diverse backgrounds to participate in co-construction. In this article, we have outlined the technical implementation of Ethereum and the challenges it faces, envisioning a series of intuitive possible applications of machine learning, and we look forward to AI developers in the community delivering real value from these visions.
As on-chain computing power gradually increases, we can foresee the development of more complex models for network management, transaction monitoring, security auditing, and various other aspects, improving the efficiency and security of the Ethereum network.
Furthermore, AI/agent-driven governance mechanisms may also become a significant innovation point in the Ethereum ecosystem. This mechanism brings a more efficient, transparent, and automated decision-making process, providing Ethereum with a more flexible and reliable governance structure. These future development directions will not only drive technological innovation in Ethereum but also provide users with a higher quality on-chain experience.






























