The key to WanChain Interconnection: Full-chain interoperability protocol

Author: YBB Capital Researcher Zeke
Introduction
Since its inception, blockchain has been fraught with disputes, evolving from the original intention of an "electronic payment system" to a "world computer," "high-speed parallelism," and "application chains for games/finance." Different values and technical divergences have led to the emergence of hundreds of public chains. Due to its fundamental characteristic of decentralization, blockchain itself is a relatively closed and isolated system, unable to perceive or communicate with the outside world, and chains are like isolated islands that cannot achieve interconnection.
Today, the mainstream narrative of public chains is advancing towards a multi-layered modular process. In addition to Layer 2 as an execution layer, we also have DA layers, settlement layers, and even execution layers above the execution layer. Fragmented liquidity and a disjointed user experience will continue to intensify, while traditional cross-chain bridge solutions are fraught with risks.
From the perspective of an ordinary user, transferring assets across chains via cross-chain bridges is already cumbersome and lengthy. Additionally, users may face various issues such as incompatible assets, hacker attacks, surging gas fees, and liquidity shortages on target chains.
The lack of interoperability between chains not only hinders the large-scale adoption of blockchain but also makes various public chains resemble hostile tribes or nations over the years. The underlying public chains are still embroiled in disputes over the "trilemma," while different layers begin to endlessly debate the merits of various solutions. In the increasingly intense trend of multi-chain and multi-layer parallel development, traditional cross-chain bridges can no longer meet industry demands, and the need for full-chain interconnectivity in Web3 is urgent. So, how far have full-chain interoperability protocols developed today? How far are we from the next billion users?
What is Full-Chain Interoperability
In the traditional internet, we rarely feel a disjointed operational experience. For instance, in payment scenarios, using Alipay or WeChat can generally fulfill all web payment requests. However, in the world of Web3, there are inherent barriers between public chains, and full-chain interoperability protocols can be simply described as a hammer that breaks down these barriers, enabling seamless transmission of assets and information across multiple public chains through cross-chain communication solutions. The goal is to achieve a seamless experience close to the Web2 level mentioned above and ultimately realize a chain-less experience or even an Intent-Centric ultimate goal.
The realization of full-chain interoperability involves several key challenges, including communication issues between heterogeneous smart contract chains and the non-Wrap method of transferring cross-chain assets. To address these challenges, some projects and protocols have proposed innovative solutions, such as LayerZero and Wormhole, which we will analyze in the following sections. However, before that, we need to understand the specific differences between full-chain and cross-chain bridges, as well as the challenges of cross-chain and the current methods of cross-chain.
What Has Full-Chain Changed
Unlike the past where assets were transferred via third-party bridges, requiring users to lock assets on the source chain and pay gas fees, only to receive a wrapped asset on the target chain after a long wait, full-chain interoperability protocols represent a new paradigm that extends from cross-chain technology. It serves as a communication center that transmits everything, including assets, through information exchange.
This allows for interoperability between chains. For example, with Sushi integrated with Stargate for exchange routing, users can achieve seamless asset swaps between the source and target chains within Sushi, optimizing the cross-chain experience to the greatest extent. Future use cases could even involve seamless interoperability across different DApps on different chains.
Trilemma and Three Types of Validation
The world of blockchain is always full of choices. Just like the most famous public chain trilemma, cross-chain solutions also face an interoperability trilemma. Due to technical and security limitations, cross-chain protocols can only optimize two out of the following three key attributes:
Trustlessness: No reliance on any centralized trust entity, providing the same level of security as the underlying blockchain. Users and participants can ensure the security and correct execution of transactions without trusting any intermediaries or third parties;
Extensibility: The protocol can be easily applied to any blockchain platform or network, unrestricted by specific technical architectures or rules. This allows interoperability solutions to support a wide range of blockchain ecosystems, not just a few specific networks;
Generalizability: The protocol can handle any type of cross-domain data or asset transfer, not limited to specific transaction types or assets. This means that through this bridge, different blockchains can exchange various types of information and values, including but not limited to cryptocurrencies, smart contract calls, and other arbitrary data.
Early cross-chain bridges were generally categorized by figures like Vitalik, who divided cross-chain technology into three types: hash time locks, witness validation, and relay validation (light client validation). However, later classifications by Connext founder Arjun Bhuptani divided cross-chain solutions into native validation (trustlessness + extensibility), external validation (extensibility + generalizability), and native validation (trustlessness + generalizability). These validation methods are based on different trust models and technical implementations to meet varying security and interoperability needs.
Natively Verified:
- Natively verified bridges rely on the consensus mechanisms of the source and target chains themselves to directly validate the validity of transactions. This approach does not require additional verification layers or intermediaries. For example, some bridges may utilize smart contracts to create validation logic directly between two blockchains, allowing these two chains to confirm transactions through their own consensus mechanisms. The advantage of this method is that it increases security, as it directly relies on the inherent security mechanisms of the participating chains. However, this method may be technically more complex, and not all blockchains support direct native verification.
Externally Verified:
- Externally verified bridges use third-party validators or validator clusters to confirm the validity of transactions. These validators may be independent nodes, consortium members, or other forms of participants that operate outside the source and target chains. This approach typically involves cross-chain messaging and validation logic executed by external entities rather than directly handled by the participating blockchains. External validation allows for broader interoperability and flexibility, as it is not restricted by specific chains, but it also introduces an additional layer of trust and potential security risks. (Although there are significant centralization risks, external validation is the most mainstream cross-chain method, combining flexibility and efficiency with low costs.)
Locally Verified:
Locally verified refers to the target chain validating the state of the source chain during cross-chain interactions to confirm transactions and execute subsequent transactions locally. The usual practice is to run a light client on the source chain within the target chain's virtual machine, or both in parallel. Local verification requires an honest minority or synchronization assumptions, where at least one honest relayer exists in the committee (i.e., an honest minority), or if the committee cannot operate normally, users must transmit transactions themselves (i.e., synchronization assumptions).
Local verification is the most trust-minimized form of cross-chain communication, but it also has high costs, lower development flexibility, and is more suitable for blockchains with high state machine similarity, such as between Ethereum and L2 networks or between blockchains developed based on the Cosmos SDK.
Different Types of Solutions
As one of the most important infrastructures in the Web3 world, the design of cross-chain solutions has always been a tricky issue, leading to a plethora of different types of solutions. Currently, these solutions can be categorized into five types, each adopting unique methods to achieve asset exchange, transfer, and contract calls.
Token Swap: Allows users to trade a certain asset on one blockchain and receive an equivalent asset on another chain. By utilizing technologies such as atomic swaps and cross-chain automated market makers (AMMs), liquidity pools can be created across different chains to facilitate exchanges between different assets;
Asset Bridge: This method involves locking or destroying assets on the source chain through smart contracts and unlocking or creating new assets on the target chain through corresponding smart contracts. This technology can be further divided into three types based on how assets are handled:
Lock/ Mint Mode: In this mode, assets on the source chain are locked, while an equivalent "bridged asset" is minted on the target chain. The reverse operation involves destroying the bridged asset on the target chain to unlock the original asset on the source chain;
Burn/ Mint Mode: In this mode, assets on the source chain are burned, and an equivalent amount of the same asset is minted on the target chain;
Lock/ Unlock Mode: This method involves locking assets on the source chain and then unlocking equivalent assets in a liquidity pool on the target chain. Such asset bridges often attract liquidity by providing incentives such as revenue sharing;
Native Payment: Allows applications on the source chain to trigger payment operations using native assets on the target chain, or to trigger cross-chain payments based on data from one chain on another chain. This method is mainly used for settlement and can be based on blockchain data or external events;
Smart Contract Interoperability: Allows smart contracts on the source chain to call functions of smart contracts on the target chain based on local data, enabling complex cross-chain applications, including asset exchanges and bridging operations;
Programmable Bridge: This is an advanced interoperability solution that combines asset bridging and messaging capabilities. When assets are transferred from the source chain to the target chain, it can immediately trigger contract calls on the target chain, realizing various cross-chain functionalities such as staking, asset exchange, or storing assets in smart contracts on the target chain.
Layer Zero

As the most well-known project in the full-chain interoperability protocol space, LayerZero has attracted many prominent crypto capitals, including a16z, Sequoia Capital, Coinbase Ventures, Binance Labs, and Multicoin Capital, completing three rounds of funding totaling $315 million. Beyond the project's inherent appeal, it is clear that the full-chain track holds significant importance in the eyes of top capital. However, setting aside these accolades, LayerZero has been a controversial project, often criticized for issues related to centralization and ecological flaws. But today, let’s put aside these biases and analyze whether LayerZero's architecture has the potential to enable full-chain connectivity.
Trustless Cross-Chain: As mentioned above, the most mainstream cross-chain bridge solutions in the past have relied solely on external validation. However, as trust shifts to off-chain verification, security is significantly compromised (most of the failed multi-signature bridges are due to this reason, as hackers only need to target the location where assets are held). In contrast, LayerZero transforms the verification architecture into two independent entities—an oracle and a relayer—compensating for the flaws of external validation in the simplest way.
The independence between the two should theoretically provide a completely trustless and secure cross-chain communication environment. However, the problem is that hackers can also target the oracle and relayer for malicious purposes, and there is also the potential for collusion between the oracle and relayer, so LayerZero's so-called trustless cross-chain in version V1 seems to have many logical flaws. In version V2, a decentralized validation network (DVNs) will be introduced to improve the verification method, which we will mention later.
LayerZero Endpoint: The LayerZero endpoint is a key element of the entire protocol's functionality. While the oracle and relayer in V1 and the DVNs in V2 are primarily responsible for message validation and fraud prevention, the endpoint is a smart contract that enables actual message exchange between the local environments of the two blockchains. Each endpoint on the participating blockchains consists of four modules: communicator, validator, network, and libraries. The first three modules enable the core functionalities of the protocol, while the libraries module allows protocol developers to extend its core functionalities and add blockchain-specific custom functions. These custom libraries enable LayerZero to adapt to diverse blockchains with different architectures and virtual machine environments. For example, LayerZero can support both EVM-compatible networks and non-EVM chains.
How It Works: The core of LayerZero's communication system relies on endpoints, which, through the aforementioned three modules, form the infrastructure for cross-chain messaging. The process begins when an application on one blockchain (Chain A) sends a message, involving the transmission of transaction details, target chain identifiers, payload, and payment information to the communicator. The communicator then compiles this information into a data packet and forwards it along with other data to the validator.
At this point, the validator collaborates with the network to initiate the transfer of the block header from Chain A to the target chain (Chain B), while instructing the relayer to pre-fetch transaction proofs to ensure the authenticity of the transaction. The oracle and relayer are responsible for retrieving the block header and transaction proofs, respectively, and then transmitting this information to the Network contract on Chain B, which then passes the block hash to the validator. Once the validator verifies that the data packet and transaction proofs provided by the relayer are correct, it forwards the message to the communicator on Chain B. Finally, the smart contract delivers the message to the target application on Chain B, completing the entire cross-chain communication process.
In LayerZero V2, the oracle will be replaced by a decentralized validation network (DVNs), addressing the criticized issues of centralization and insecurity of off-chain entities. Meanwhile, the relayer is replaced by executors, whose role is limited to executing transactions without being responsible for validation.
Modular and Scalable: Developers can use the libraries module to extend LayerZero's core functionalities on the blockchain. These modules are part of a set of protocol smart contracts. Libraries allow for the implementation of new features in a blockchain-specific manner without modifying LayerZero's core code. The protocol is also highly scalable, as it uses lightweight messaging setups for cross-chain communication. A simple user experience is a key feature of LayerZero.
When performing cross-chain operations using this protocol, it can be treated as a single transaction, eliminating the usual token wrapping and unwrapping procedures associated with traditional crypto bridge asset transfers. Therefore, the user experience is similar to performing token swaps or transfers on the same chain.
LayerZero Scan: Given that LayerZero supports nearly 50 public chains and Layer 2s, tracking message activity on LayerZero is no small feat. This is where LayerZero Scan comes into play. This cross-chain browser application allows you to see all protocol message exchanges on participating chains. The browser lets you view message activity by source chain and target chain separately. You can also explore transaction activities by each DApp using LayerZero.
OFT (Omnichain Fungible Token): The OFT (Omnichain Fungible Token) standard allows developers to create tokens with native-level functionalities across multiple chains. The OFT standard involves burning tokens on one chain while minting a copy of the token on the target chain. Meanwhile, the original OFT token standard can only be used with EVM-compatible chains. LayerZero has expanded this standard in the latest version OFT V2 to support non-EVM platforms.
ONFT (Omnichain Non-Fungible Token): ONFT is the non-fungible version of the OFT standard. NFTs created based on the ONFT standard can be transferred and stored at the native level across chains that support this standard.
Wormhole
Wormhole, like LayerZero, is also a participant in the full-chain protocol space and has recently begun to show its potential through airdrop activities. The protocol was first launched in October 2020 and has since transitioned from a bi-directional token bridge in V1 to now being able to build native cross-chain applications covering multiple chains. One of the most notable events for the protocol was the hacker attack on February 3, 2022, which resulted in the theft of $360 million worth of ETH. However, Wormhole managed to fill this funding gap in less than 24 hours (source unknown), and recently announced a funding round of up to $225 million. So, what magic does Wormhole possess that makes it so favored by capital?
Precise Targeting: Wormhole's goal is not primarily focused on EVM chains but rather on non-EVM chains. Wormhole is the only mainstream full-chain protocol that supports heterogeneous public chains such as Solana and Move-based chains (APT, SUI). As the ecosystems of both continue to recover and flourish, Wormhole's emergence becomes inevitable.
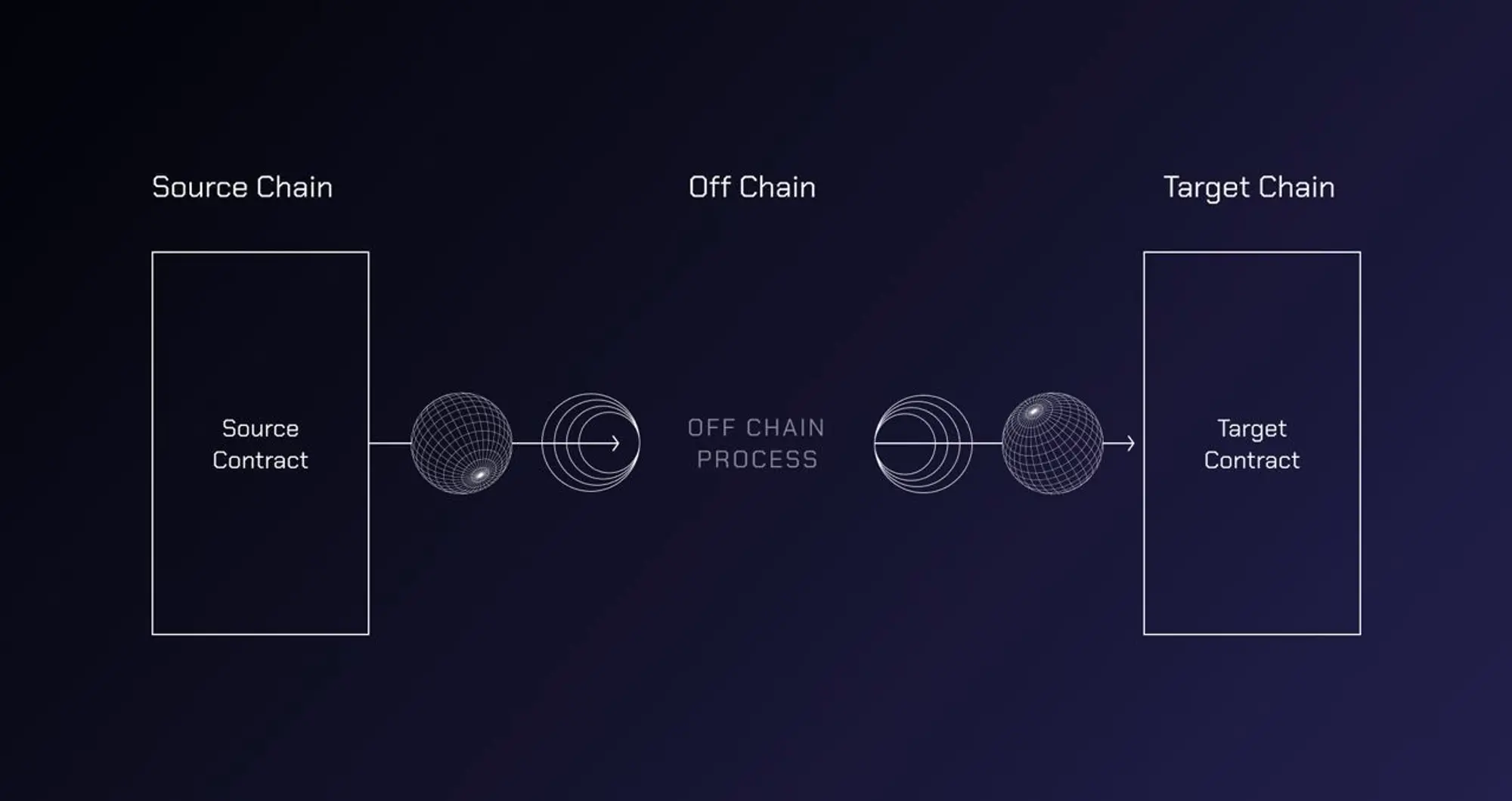
How It Works: The core of Wormhole is the Verifiable Action Approval (VAA) cross-chain protocol and 19 Guardian nodes (Wormhole has chosen well-known institutions in the industry as guardian nodes, but this has also led to criticism). It converts requests into VAA through Wormhole Core Contracts on each chain to complete cross-chain operations. The specific process is as follows:
Event Occurrence and Message Creation: A specific event (such as an asset transfer request) occurring on the source chain is captured and encapsulated into a message. This message details the event that occurred and the operations that need to be executed;
Guardian Node Listening and Signing: The 19 Guardian nodes in the Wormhole network are responsible for monitoring cross-chain events. When these nodes detect an event on the source chain, they validate the event information. Once validated, each Guardian node uses its private key to sign the message, indicating validation and approval of the event (requiring two-thirds of the nodes' agreement);
Generating Verifiable Action Approval (VAA): Once a sufficient number of Guardian nodes sign the message, these signatures are collected and packaged into a VAA. The VAA is a verifiable approval of the occurred event and its cross-chain request, containing detailed information about the original event and signatures from the Guardian nodes;
Cross-Chain Transmission of VAA: The VAA is then sent to the target chain. On the target chain, the Wormhole Core Contract is responsible for verifying the authenticity of the VAA. This includes checking the signatures of the Guardian nodes included in the VAA to ensure they are generated by trusted nodes and that the message has not been tampered with;
Executing Cross-Chain Operations: Once the Wormhole contract on the target chain verifies the validity of the VAA, it executes the corresponding operations based on the instructions in the VAA. This may include creating new tokens, transferring assets, executing smart contract calls, or other custom operations. In this way, events on the source chain can trigger corresponding reactions on the target chain.
Security Module: Wormhole is developing three main internal security features: oversight, accounting, and emergency shutdown, all developed in a public environment to gain insights into their final implementation. These features are awaiting completion and adoption by the guardians.
Oversight: This feature is implemented at the guardian/oracle level, allowing guardians to monitor the flow of value on any regulated chain within a certain time window. Guardians set acceptable liquidity limits for each chain, and once exceeded, they block excess asset flows;
Accounting: This feature is implemented by guardians or oracles, maintaining their own blockchain (also known as wormchain) as a cross-chain ledger between different chains. This ledger not only makes guardians on-chain validators but also serves as an accounting plugin. Guardians can reject cross-chain transactions that originate from chains with insufficient funds (this validation is independent of smart contract logic);
Shutdown: This feature is implemented on-chain, allowing guardians to pause asset flows on the bridge through consensus when they detect potential threats to the cross-chain bridge. The current implementation is achieved through on-chain function calls.
Rapid Integration: Wormhole's Connect product provides applications with a simple bridging tool that can be integrated with just a few lines of code to realize cross-chain functionality. Connect's main feature is to provide developers with a set of simplified integration tools, allowing them to integrate Wormhole's wrapping and native asset bridging functionalities into their own applications with just a few lines of code. For example, an NFT marketplace wishing to bridge its NFTs from Ethereum to Solana can use Connect to provide its users with a simple, fast bridging tool within its application, enabling them to freely move their NFTs between the two chains.
Messaging: In a diverse blockchain ecosystem, messaging has become a core need. Wormhole's Messaging product provides a decentralized solution that allows different blockchain networks to securely and easily exchange information and value.
The core functionality of Messaging is cross-chain information transmission, equipped with simplified integration methods to accelerate user and liquidity growth while maintaining high security and decentralization. For instance, suppose a DeFi project operates on Ethereum but wishes to interact with another project on Solana. Through Wormhole's Messaging, these two projects can easily exchange information and value without complex intermediary steps or third-party intervention.
NTT Framework: The NTT framework (Native Token Transfers) provides an innovative and comprehensive solution for transferring native tokens and NFTs across blockchains through Wormhole. NTT allows tokens to retain their inherent properties during cross-chain transfers and supports direct cross-chain transfers of tokens without going through liquidity pools, thus avoiding LP fees, slippage, or MEV risks. Additionally, it can integrate with any token contract or standard as well as protocol governance processes, allowing project teams to maintain ownership, upgrade rights, and customizability of their tokens.
Conclusion
Although full-chain interoperability protocols are still in their early stages, the overall implementation process faces risks of security and centralization, and the user experience cannot yet compare to the Web2 internet ecosystem. However, compared to early cross-chain bridge technologies, current solutions have made significant progress. In the long run, full-chain interoperability protocols represent a grand narrative that integrates thousands of isolated chains, especially in an era that pursues extreme speed and cost-effectiveness. Full-chain protocols are undoubtedly a key link in bridging the past and the future, and they are a track we must pay close attention to.
References
Understanding Blockchain Interoperability: https://blog.chain.link/blockchain-interoperability-zh/
New Forces in Cross-Chain: Analyzing the Potential of Wormhole: https://www.binance.com/zh-TC/feed/post/4142724308034
Understanding the General Cross-Chain Information Transmission Protocol Wormhole: https://wormholechina.medium.com/一文了解通用跨链信息传送协议-wormhole-c88ffd14540c
Wormhole Introduces Native Token Transfers (NTT): https://wormholechina.medium.com/wormhole-引入原生代币转移-ntt-一个新的开放框架-用于使任何代币成为原生多链-7a2cbb20bee6
Sushi's Cross-Chain Swap: https://www.sushi.com/blog/sushi-xswap-a-crosschain-dex
What Is LayerZero: Revolutionizing Omnichain Interoperability: https://learn.bybit.com/blockchain/what-is-layerzero/
The Future of Cross-Chain Bridges: Full-Chain Interoperability is Inevitable, Liquidity Bridges Will Decline: https://medium.com/@eternal1997L/跨链桥的未来-全链互操作成必然-流动性桥将没落-abf6b9b55fbc
The Controversies Behind the LayerZero Airdrop Craze: https://www.chaincatcher.com/article/2091995









