The Disappearing Mango: Understanding the Rise and Fall of the MangoFarmSOL Scam
Written by: CertiK
Event Overview
MangoFarmSOL positions itself as a staking protocol on the Solana network, encouraging users to deposit SOL in exchange for rewards. The project garnered attention from the Solana community by promising an airdrop on January 10.
However, the promise made on January 10 was never fulfilled. On January 6, 2024, MangoFarmSOL executed an exit scam, transferring 13,512 SOL (approximately $1.26 million at the time) from the project contract and deploying a malicious frontend that misled users into authorizing an "emergency migration," stealing approximately $60,000 in the process. This is the largest exit scam discovered so far in 2024.
Subsequently, MangoFarmSOL shut down its social accounts and website.
Similar to the previously reported xKingdom incident, this event once again highlights the inherent risks of exit scams in the DeFi space, emphasizing the importance of user vigilance and team KYC.
Scam Timeline
Step 1: Setting the Trap
① On January 3, the project used social media KOL promotions to enhance its credibility and attract more users.
② On January 5, the team published an article claiming that they would airdrop MANGO tokens on January 10, with more rewards for staking SOL and referring other users.

③ From January 3 to January 7, users began depositing SOL into the MangoFarmSOL contract. Tempted by the promise of the MANGO token airdrop and influenced by online marketing, the protocol's TVL exceeded $1.3 million.

Step 2: Executing the Scam
① Stealing Contract Funds: The MangoFarmSOL team initiated the scam, withdrawing 13,514 SOL (approximately $1.26 million) deposited by users into the Mango contract to wallet 8ggvi.

First transaction: 135 SOL transferred from the Mango contract (Bfg5SM) to wallet 8ggvi.

Second transaction: 13,379 SOL transferred from the Mango contract (Bfg5SM) to wallet 8ggvi.
② Deploying a Malicious Frontend to Scam Again: Subsequently, the team leveraged the previous theft incident, deploying a frontend containing malicious code under the guise of "emergency migration." The project's official social media accounts also promoted this malicious frontend, tricking users into making transactions, resulting in an additional $60,000 in assets being stolen.


③ Completely Disappearing: MangoFarmSOL subsequently disabled its social media accounts and shut down its official website, beginning to transfer funds.
Step 3: Fund Transfer
Flow of stolen funds from the Mango contract
① Initial Transfer: A total of 13.5K SOL, valued at approximately $1.26 million, was stolen from the Mango contract and sent to address 8ggvi…..ejND7.
② Mixing & Conversion: Next, 9,458 SOL were sent to 4nBETJ to obscure the fund trail; all SOL in 8ggvi and 4nBE were subsequently converted to USDC.

③ Cross-chain to Ethereum: These USDC were cross-chained from the Solana network to Ethereum via Wormhole and sent to four different ETH addresses through multiple transactions.
 380k USDC cross-chained to 0x09e3
380k USDC cross-chained to 0x09e3
 319k USDC cross-chained to 0xc504
319k USDC cross-chained to 0xc504
 351k USDC cross-chained to 0x6898
351k USDC cross-chained to 0x6898
 217k USDC cross-chained to 0x8816
217k USDC cross-chained to 0x8816
④ Final Laundering: After entering the Ethereum network, USDC was exchanged for ETH. The stolen funds were then laundered through Railgun (a privacy mixer) and exchanged via eXch (instant exchange) to further obscure the funds.
 Example of a transaction sent to Railgun
Example of a transaction sent to Railgun

Example of a transaction sent to eXch
Flow of funds stolen through the malicious frontend
① Integration and Conversion: User assets stolen through the malicious frontend were consolidated into SOL and then exchanged for approximately $58,600 in USDC.
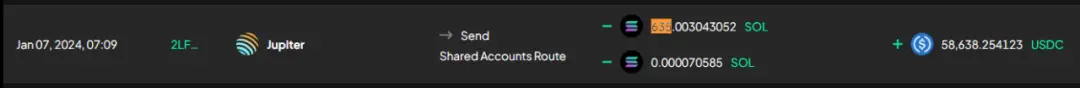
② Cross-chain to Ethereum via Allbridge: These USDC were cross-chained to the Ethereum network through two transactions on Allbridge, to address 0x7ca…..d8fec.

③ Final Laundering: The USDC bridged to Ethereum was exchanged for 26 ETH. Subsequently, these funds were deposited multiple times into FixedFloat.

Final Distribution of Stolen Funds
The stolen funds that were cross-chained to the Ethereum network are primarily concentrated in three places:
- eXch: approximately 292 ETH
- Railgun: approximately 263 ETH
- FixedFloat: approximately 26 ETH
Summary of Experience
The MangoFarmSOL scam is the largest exit scam so far in 2024. The tactics used in this scam are similar to those in the 2023 Harvest Keeper incident. Both projects deployed malicious frontends after the initial theft occurred, further stealing user funds.
The MangoFarmSOL exit scam is expected to have caused losses of $1.32 million, highlighting the urgent need for scrutiny of decentralized projects.










