The launch of the Blast mainnet is imminent, analyzing the security risks and potential opportunities from a technical perspective
Author: Beosin
Recently, Blast has once again become the "darling" of the market. With the conclusion of its "Big Bang" developer competition, its TVL has soared, surpassing $2 billion and securing a place in the Layer2 space.
At the same time, Blast announced that it will launch its mainnet on February 29, leading to continued public attention, especially since the "airdrop expectations" have successfully attracted a large number of participants to watch. However, as its ecosystem develops, various projects are emerging, which also leads to frequent security risks. Today, Beosin will analyze the strong start of Blast, the security risks and potential opportunities behind the soaring TVL.

Development History of Blast
Blast was launched by Pacman, the founder of Blur, on November 21, 2023, and quickly gained widespread attention in the crypto community. Within 48 hours of its launch, the network's total locked value (TVL) reached $570 million, attracting over 50,000 users.
Last year, Blast secured $20 million in funding from major supporters such as Paradigm and Standard Crypto. Following that, in November, Blast received a $5 million investment from the Japanese cryptocurrency investment firm CGV.
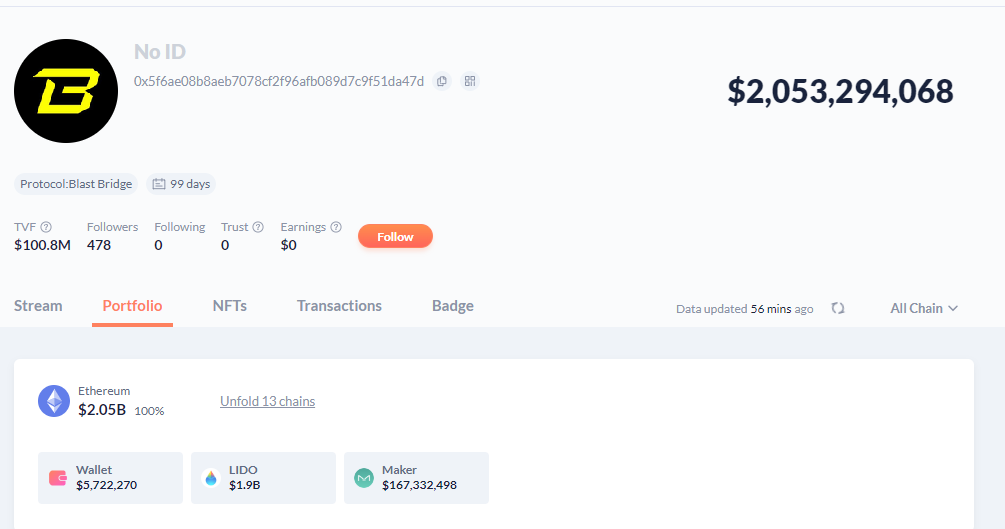
On February 25, news from DeBank indicated that the total asset value held by the Blast contract address currently exceeds $2 billion, with $1.8 billion in ETH deposited in the Lido protocol and over $160 million in DAI deposited in the MakerDAO protocol, demonstrating its popularity in the market.
DeBank data
Why is Blast so popular?
The uniqueness of Blast lies in its provision of native yields for ETH and stablecoins, a feature not found in other Layer2 solutions. When users transfer ETH to other Layer2s, these Layer2s only lock the ETH in smart contracts and map the corresponding Layer2 ETH; whereas Blast deposits users' ETH in Lido for yield and introduces a new yield-generating stablecoin USDB (which will generate returns by purchasing U.S. Treasury bonds through MakerDAO) into the Blast network.
Moreover, as a Layer2 launched by the Blur team, it inherently brings traffic. Previously, Blur distributed over $200 million in airdrops to users on its platform, establishing a broad community base. Currently, Blast is conducting airdrop incentives, attracting users to participate in Blast staking through a traffic-driven marketing approach.
Security Risks of Blast
Since its launch, Blast has faced criticism and skepticism. On November 23, 2023, Jarrod Watts, a developer relations engineer at Polygon Labs, tweeted that Blast's centralization could pose serious security risks to users. He also questioned Blast's classification as a Layer 2 (L2) network, as Blast does not meet L2 standards and lacks features such as transactions, bridging, Rollup, or sending transaction data to Ethereum.
What is the security of Blast like? What security risks exist? This time, we will use the Beosin VaaS tool to scan the Blast Deposit contract and analyze the contract code with insights from Beosin security experts.
Beosin VaaS
The Blast Deposit contract is an upgradeable contract, with its proxy contract address being 0x5F6AE08B8AeB7078cf2F96AFb089D7c9f51DA47d. Currently, its logic contract address is 0x0bD88b59D580549285f0A207Db5F06bf24a8e561, with the main risk points as follows:
1. Centralization Risk
The most important function of the Blast Deposit contract, enableTransition, can only be called by the contract's admin address. Additionally, this function takes the mainnetBridge contract address as a parameter, and the mainnetBridge contract can access all staked ETH and DAI.
function enableTransition(address mainnetBridge) external onlyOwner {
if (isTransitionEnabled) {
revert TransitionIsEnabled();
}
_pause();
_setMainnetBridge(mainnetBridge);
isTransitionEnabled = true;
LIDO.approve(mainnetBridge, type(uint256).max);
DAI.approve(mainnetBridge, type(uint256).max);
}
code: https://etherscan.io/address/0x0bd88b59d580549285f0a207db5f06bf24a8e561#code#F1#L230
Moreover, the Blast Deposit contract can be upgraded at any time through the upgradeTo function. This is primarily used to fix contract vulnerabilities, but it also poses a risk of malicious actions. Currently, Polygon zkEVM has implemented a relatively robust upgrade process, requiring a 10-day delay for contract modifications under non-emergency situations, and changes must be decided by a protocol council of 13 members.
function upgradeTo(address newImplementation) public virtual onlyProxy {
_authorizeUpgrade(newImplementation);
_upgradeToAndCallUUPS(newImplementation, new bytes(0), false);
}
code: https://etherscan.io/address/0x0bd88b59d580549285f0a207db5f06bf24a8e561#code#F2#L78
2. Multi-signature Disputes
Looking at the Blast Deposit contract, its contract permissions are controlled by a Gnosis Safe 3/5 multi-signature wallet 0x67CA7Ca75b69711cfd48B44eC3F64E469BaF608C. The five signing addresses are:
0x49d495DE356259458120bfd7bCB463CFb6D6c6BA
0xb7c719eB2649c1F03bFab68b0AAa35AD538a7cC8
0x1f97306039530ADB4173C3786e86fab5e6b90F41
0x6a356C0EAA560f00127Adf5108FfAf503b9f1e11
0x46e31F27Df5047D7Fad9b1E8DFFec635cF6efAcF
These five addresses were all created three months ago, and their identities are unknown. Since the entire contract is actually a custodial contract protected by a multi-signature wallet, rather than a Rollup bridge, Blast has faced many questions from the community and developers.
Blast has acknowledged this series of security risks and stated that while immutable smart contracts are considered secure, they may hide undetected vulnerabilities. Upgradeable smart contracts also bring their own risks, such as contract upgrades and easily exploitable time locks. To mitigate these risks, Blast will use multiple hardware wallets for management to avoid centralization risks.
However, whether wallet management can avoid centralization and phishing attacks, and whether there is a complete management process, has not been disclosed by Blast. In previous security incidents involving Ronin Bridge and Multichain, although the project parties used multi-signature wallets or MPC wallets, the centralization of private key management led to user asset losses.
On February 19, the Blast team conducted an update on the Deposit contract. This update mainly added Predeploys contracts and introduced the IERC20Permit interface to prepare for the mainnet launch.
Ecological Risks of Blast
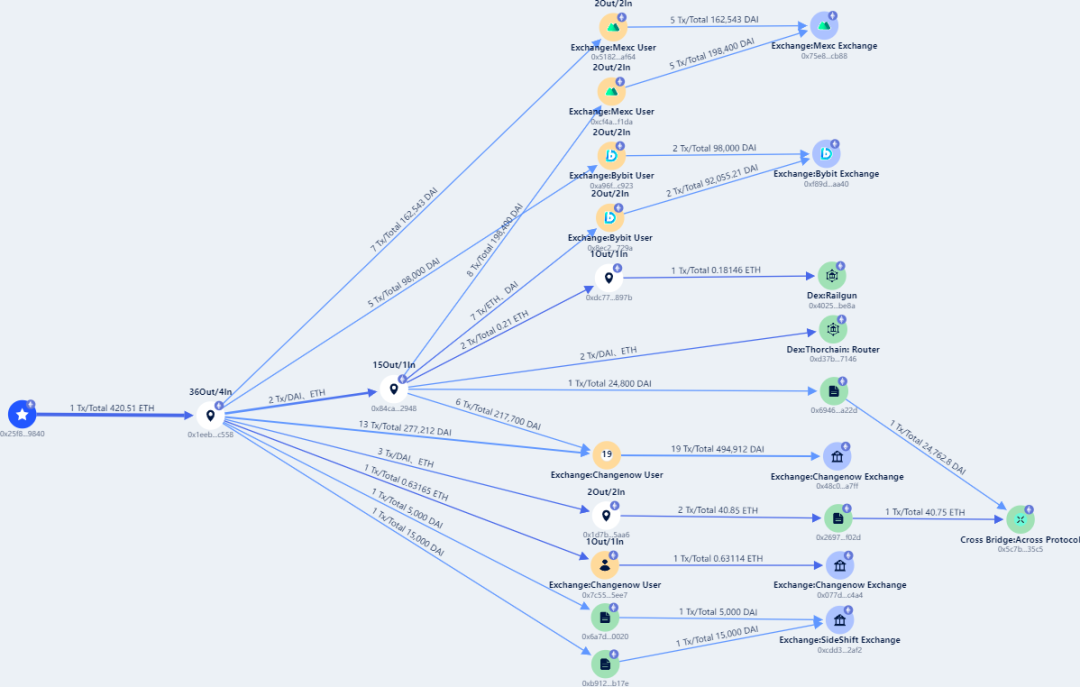
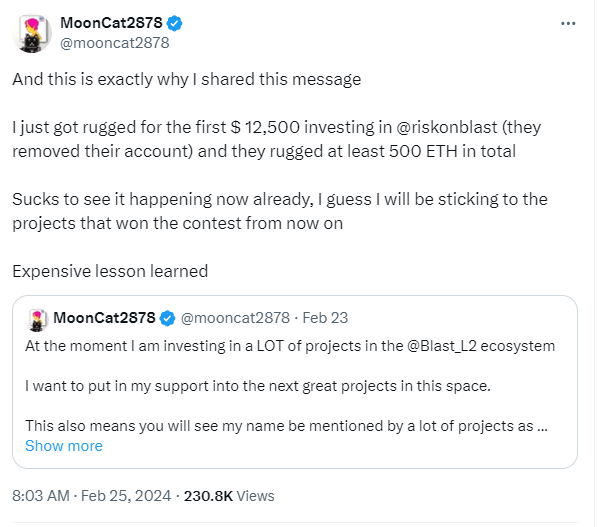
On February 25, Beosin's KYT anti-money laundering analysis platform detected that the Blast ecosystem GambleFi project Risk (@riskonblast) is suspected of having a Rug Pull, with losses amounting to approximately 500 ETH. Currently, its official X account shows that it no longer exists.

Investors like MoonCat2878 also shared their personal losses. MoonCat2878 recounted that after seeing reputable projects and partners within the Blast ecosystem, they initially viewed RiskOnBlast as a promising investment opportunity. However, the subsequent public sale turned into an unlimited fundraising round, raising their suspicions about this GameFi project.
Beosin Trace monitoring shows that most of the stolen funds from the Blast ecosystem game Risk project have been transferred to different exchanges, and a small portion of the stolen funds has been cross-chained to Arbitrum and Cosmos.