True or false, a blockchain perspective on the "ransom" addresses of the Northern Myanmar Alliance
^Written by: Slow Fog, Bitrace Team^
Background
On January 16, 2024, a blogger revealed on a Chinese social media platform that the Myanmar Allied Army allegedly forced practitioners of the telecom fraud industry stranded in Myanmar to pay high amounts in cryptocurrency, showcasing a cryptocurrency address claimed to be used for payments. This revelation has since spread widely online.
This article, co-authored by Bitrace & MistTrack, conducts an analysis of the disclosed addresses regarding cryptocurrency funds, including: the patterns of fund inflow and outflow, risks associated with the source of funds, and activities of related addresses, aiming to disclose relevant analytical content.
Address Behavior Analysis

(https://mp.weixin.qq.com/s/WDWM22vw68-NsVr0_1jHfA)
The above image contains information from the revelation article. Based on this, researchers conducted a USDT exchange rate analysis on the disclosed receiving address TKFsCN, attempting to deduce the underlying settlement unit through specific amounts of USDT received.
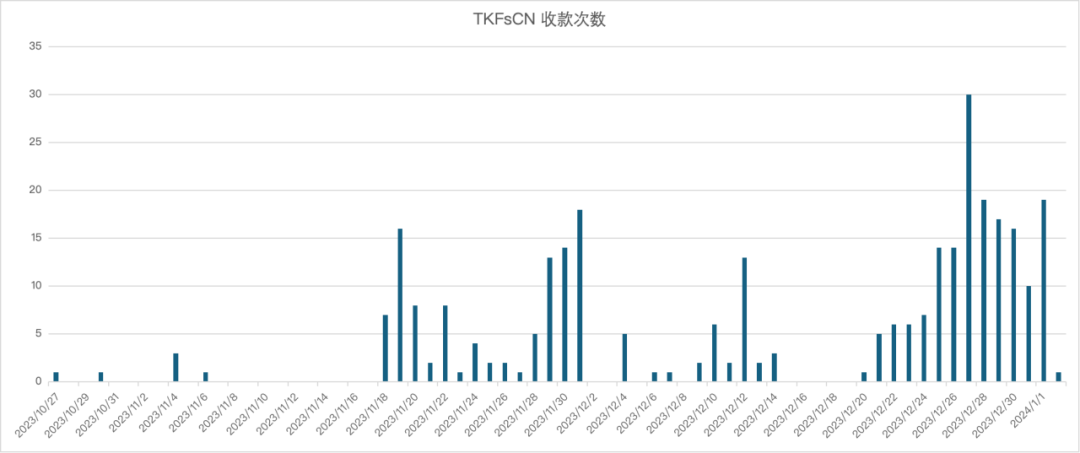
The historical transaction records of the receiving address show that the USDT transactions received by this address contain a large number of non-round figures, such as 71417, 42857, etc. This is common in transactions settled in non-USD currencies. After attempting to calculate using various mainstream fiat currency to USDT exchange rates, researchers found that these transactions were likely settled at an exchange rate of 1 USD : 7-7.2 RMB, with single fund inflows clustering around amounts of 500,000-600,000 RMB, 1 million, and 1.5 million.

After filtering out transactions of 100 USDT and below, statistics show that out of a total of 307 USDT inflows to TKFsCN, 193 transactions were amounts converted from RMB to USD, accounting for 62.86% of the transaction count and 45.29% of the transaction amount.
This indicates that over half of the transactions received by this address were settled in RMB, with inflows converted to amounts of 500,000 being predominant. The party paying in USDT is likely Chinese.
Source of Funds Analysis
The original text mentions, "After occupying the old street, they also captured (the author’s note: telecom fraud practitioners) Chinese people everywhere, asking whether they are willing to pay for self-protection; those who pay can leave, while those who do not pay will be sent back to China." If true, there should be a large number of new counterparties in the transactions of TKFsCN, with part of the funds sourced from gray and black industries, money laundering, fraud, and related addresses.

Data shows that between October 22, 2023, and January 2, 2024, TKFsCN received USDT transfers from 182 direct counterparties, among which 117 addresses exhibited the characteristic of small amount + large amount consecutive transfers. This is a typical transfer testing behavior, where the payer confirms the address is correct by not choosing to transfer the entire amount at once, indicating that at least 62.29% of the counterparties may be making their first transfer and are not fixed trading partners of TKFsCN.

A deeper audit of the risk funds associated with TKFsCN shows that the counterparties transferring to this address are closely linked to activities such as black and gray industries, online gambling, fraud, money laundering, and risk payments. Among the 182 direct inflow parties, as much as 42% are addresses associated with risk activities, transferring a total of USDT valued at $33,523,148 to TKFsCN.

(Image from MistTrack and BitracePro)
Notably, among this batch of risk activity-associated addresses, investigators also found 7 addresses clearly linked to known criminal cases, including two money laundering cases, one fraud case, one online gambling case, and one telecom fraud case, with the suspects' geographical locations all in northern Myanmar or Cambodia.
This indicates that the counterpart addresses initiating payments to TKFsCN are not only involved in a large number of risky cryptocurrency activities but are also closely related to criminals in Southeast Asia.
Another strange point is that investigators also found a laundering address linked to a telecom fraud case among the outgoing addresses, indicating that there are also certain doubts in the upstream analysis of the fund flows of some outgoing addresses. This doubt will be elaborated on in the "Related Address Analysis" section below.
Related Address Analysis
Based on the clustering analysis of the TKFsCN address, it was found that this address appears to have a clustering relationship with nearly a hundred addresses, some of which not only exhibit similar fund inflow and outflow activities as TKFsCN but also reveal more information about the payees. Taking the payee TKKj8G as an example:
- TKKj8G directly received 6 transfers from TKFsCN totaling over 4.6 million USDT, serving as one of the aggregation addresses in the payee's subsequent fund chain;
- TKKj8G is one of the core receiving addresses, with 50 out of 60 payments over 100 USDT exhibiting similar small amount testing behavior as TKFsCN;
- TKKj8G became active on August 18, 2023, well before other addresses, and during this period, there were transactions with Huawang Guarantee, receiving 160,000 USDT from the Huawang Guarantee address, which is analyzed as the merchant of Huawang Guarantee retrieving a deposit.

This suggests that the "Finance Department address" mentioned in the original text may not exist, and the address cluster including TKFsCN and TKKj8G should belong to a cryptocurrency exchange located in northern Myanmar or Cambodia, which collects these payments on behalf of some party for some reason.

Abnormal Transactions
In summary, investigators can easily sketch a typical profile of the payers—engaged in illegal work in Southeast Asia, compelled for some reason to pay a receiving address with USDT valued at 500,000 RMB. Since it is the first transaction, they conducted a small amount test to prevent address errors before making large transfers. The cryptocurrency used for payment may come from their original illegal earnings or purchased from other illegal entities.
However, not all payers fit this profile. Investigators also found some addresses that do not fully conform to these characteristics. For example, TYU5acSGRwsYJfBhdpQc3broSpfsjs8QFF is one of the 7 directly involved addresses mentioned earlier. The other 6 addresses transferred cryptocurrencies valued at 500,000, 500,000, 1 million, 1 million, 2.7 million (1.5 million + 1.2 million), and 550,000 RMB to TKFsCN, but the transfer amount of TYU5ac, when converted at the same exchange rate, equals 1.36 million RMB. Although it is a round number, this particular amount still differs from the other addresses.
Investigators could not ascertain the reason behind this. Considering that this address exhibited small amount testing behavior, a reasonable speculation is that the transactions behind this address represent a merged transfer of three amounts of 500,000 RMB, obtaining a 10% discount.

Conclusion
This article provides an in-depth analysis of the disclosed addresses regarding the patterns of fund inflow and outflow, risks associated with the source of funds, and activities of related addresses, and discloses relevant analytical content. The main conclusions are as follows:
- Over half of the transactions received by the target address in this analysis were settled in RMB, with inflows converted to amounts of 500,000, 1 million, and 1.5 million being predominant;
- The counterpart addresses transferring to the target address are closely linked to activities such as black and gray industries, online gambling, fraud, money laundering, and risk payments;
- The target address and its related addresses exhibited traces of risky business activities even before intensively receiving such funds. Clustering analysis of the target address suggests that this cluster may belong to a merchant of Huawang Guarantee;
- The counterpart addresses initiating payments to the target address are closely related to criminals in northern Myanmar or Cambodia.









