Decoding L2 MEV: Sorter Workflow and MEV Data Analysis
Written by: Burce, Hildobby
Edited by: Lisa
* Thanks to Hildobby, the data analyst at Dragonfly, for supporting the L2 MEV data.
Core Role of L2 MEV: Sequencer
The L2 Sequencer, as a core component of Ethereum Layer 2 solutions, plays a critical role. Its main task is to process transactions, which involves packaging them and submitting them to the ETH main chain or off-chain networks to enhance the throughput and efficiency of the entire blockchain ecosystem. Specifically, the Sequencer acts similarly to the transaction pool on the Ethereum main chain but operates in a more specialized manner. Additionally, the L2 Sequencer provides more operational flexibility for applications and smart contracts, allowing for more complex logic and contracts to be implemented at the L2 level without worrying about high gas fees.
Process of Sequencer Handling Transactions
1. Collection
The Sequencer receives transaction requests from users, which are typically in the format of Ethereum transactions but are sent to the Layer 2 network instead of the main chain.
2. Validation
The Sequencer validates the transactions to ensure that the sender has sufficient funds to execute the transaction and that it complies with the rules of the Layer 2 network. It also ensures the validity of the transactions to prevent fraud and double spending.
3. Ordering
The Sequencer orders the transactions according to certain rules to ensure they are executed in the correct sequence, preventing potential transaction conflicts.
4. Submission
Once the transactions have been validated and ordered, the Sequencer submits them to the Layer 2 network for execution. This typically involves interacting with Layer 2 smart contracts, updating states, and ensuring that the ledger on Layer 2 remains in sync with the ledger on the ETH main chain.
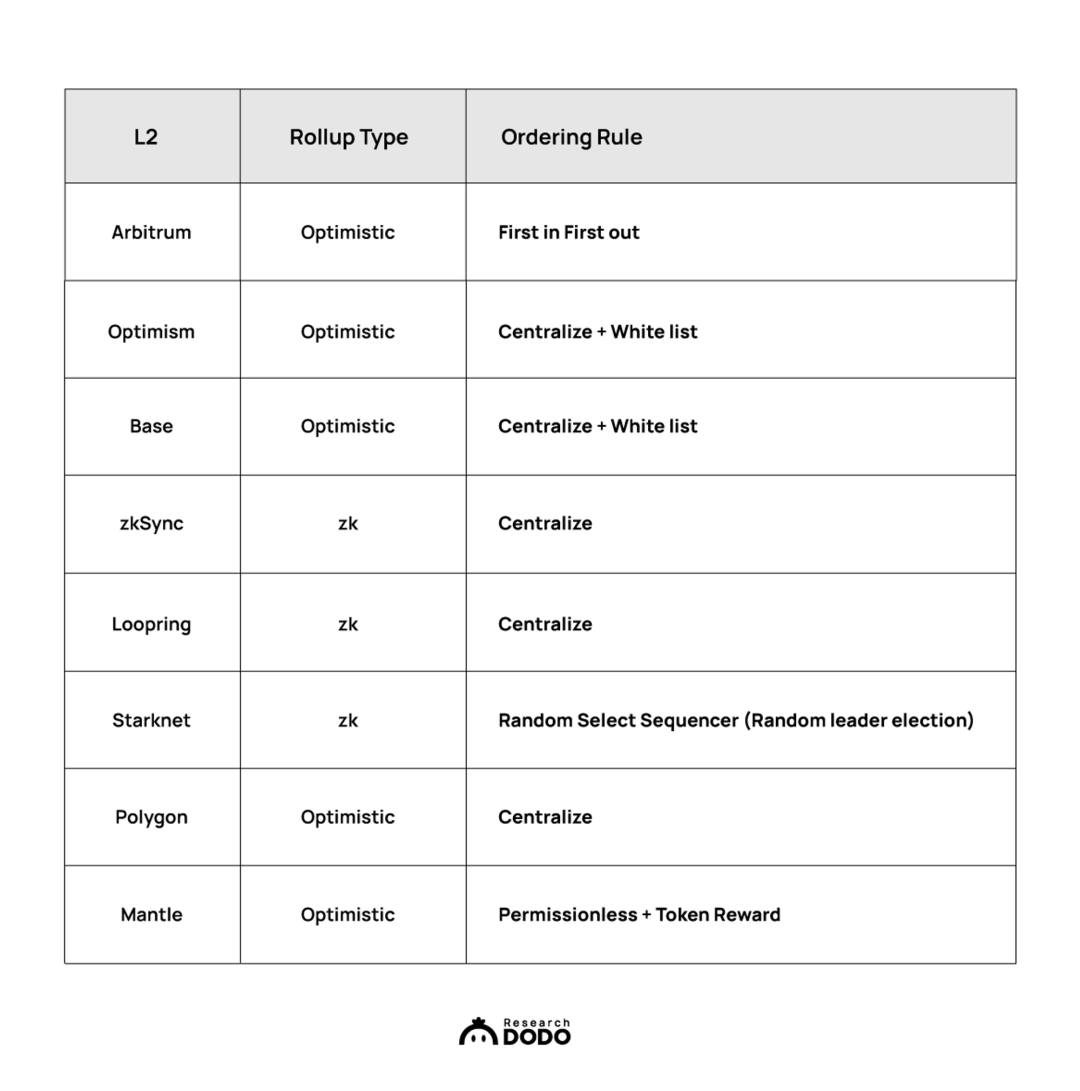
Different Ordering Rules of L2 Sequencers
Ordering Rules of Arbitrum
To minimize MEV issues, Arbitrum does not have a public mempool and adopts a first-come, first-served (FCFS) ordering model, allowing transactions that are submitted first to be processed earlier.
Ordering Mechanism of Optimism
Optimism introduces an auction-based ordering mechanism, known as MEV Auction (MEVA), to fairly distribute the advantages and disadvantages of transaction processing. Additionally, after the Bedrock upgrade, Optimism launched the Bedrock Sequencer, which, along with MEVA, is used for ordering. Similar to Arbitrum, the Bedrock sequencer has its own private mempool. MEVA has not been fully implemented yet, but according to current plans, the winners of MEVA will have the right to reorder submitted transactions and insert their own transactions, but cannot delay specific transactions beyond N blocks, which also means that the MEV profits for MEVA winners are limited.
Ordering Rules of Other L2 Solutions
In addition to Arbitrum and Optimism, there are many other L2 solutions such as zkSync, Loopring, Starknet, etc., each adopting different ordering rules to meet the needs of various users and applications.
MEV Extraction in L2
In the blockchain world, the generation of MEV (Miner Extractable Value) is the result of multiple factors working together. The root cause lies in the inevitable delay between the propagation of transaction information submitted by users in the network and the actual mining of blocks. This time lag provides nodes with operational space. Due to the nature of decentralized systems, different nodes may receive transactions in different orders and times, which means that the system cannot guarantee that all nodes are in a consistent state at the same moment. This inconsistency creates conditions for the generation of MEV.
On the Ethereum mainnet, MEV extraction has formed a scaled profit. MEV attackers typically monitor the transactions in the mempool and ensure their transactions are prioritized by participating in so-called Gas Auctions (bidding for transaction fees to prioritize transaction processing) or by bribing off-chain. This way, they can gain benefits through a predetermined transaction order.
The process of obtaining MEV profits can be divided into two key steps. First, attackers need to identify potentially profitable transactions and construct a transaction block specifically optimized for extracting MEV. Second, they must ensure that these specially constructed transactions can be accepted by the network and included in the blockchain.
However, with the rise of Layer 2 (L2) solutions, the methods and strategies for MEV extraction have changed significantly. Since the sequencers of L2 solutions are often centralized, the extraction of MEV faces new challenges and opportunities compared to traditional Layer 1 (L1).
For L2 solutions without a mempool, monitoring transactions becomes more difficult. In this case, the sequencer holds more power as it directly determines the order of transaction processing. The absence of a mempool means that attackers cannot adjust the transaction order by monitoring the transaction pool as they do in L1 solutions, significantly increasing the difficulty of conducting MEV attacks.
In L2 solutions with centralized sequencers and a mempool, the impact of Gas Auctions on ordering is also reduced. Some L2s even have no Gas Auctions at all, changing the game. Although attackers cannot determine the exact order of transactions, they can still attempt to influence the position of their transactions by adjusting Gas Fees. Compared to L1, the success rate and predictability of this strategy are much lower.
Additionally, some independent DAPPs on L2 may maintain their own local transaction mempool. These mempools become potential monitoring targets for attackers, who may exploit these DAPP-specific mempools to implement MEV extraction.
For L2 chains that run Gas Auctions, such as Polygon, the joining of their validator nodes is not completely open and permissionless. In this case, when attackers detect MEV opportunities, they may adopt a strategy of submitting a large number of transactions to increase the likelihood of their transactions being included on-chain. This strategy relies on luck and lower transaction costs, making it a less certain attack method.
Finally, attackers may also exploit interactions between L1 and L2 or between different L2 solutions to extract MEV. This requires attackers to have a deep understanding and analytical ability regarding cross-chain states and dynamics.
Differences in MEV Extraction Space Between Different L2s
There are significant differences in MEV extraction space among different L2 solutions. These differences are primarily determined by factors such as the centralization of L2's sequencer rules, mempool design, transaction volume, and transaction size. Generally, the higher the degree of centralization of a sequencer in an L2 solution, the more concentrated the MEV extraction space, resulting in relatively fewer extraction opportunities. Conversely, the more open the mempool design, the greater the space available for attackers, providing them with more opportunities for transaction monitoring and ordering manipulation.
At the same time, the transaction volume and size of L2 solutions also have a significant impact on the MEV extraction space. L2s with high transaction volume and large transaction sizes provide more opportunities for MEV extraction because, in high-traffic environments, there are more profitable transactions, giving attackers more chances to extract profits. Conversely, L2s with low transaction volume and small transaction sizes have relatively smaller MEV extraction spaces due to fewer opportunities.
Future Solutions for L2 MEV
One of the fundamental issues of blockchain technology is how to achieve true decentralization. In L2, the core of this issue is the realization of decentralized sequencers, which concerns how the authority to determine the order of transactions is distributed. This directly affects the fairness, security, and other key performance aspects of the blockchain system. The MEV problem in L2 is essentially a derivative issue of transaction ordering rights. Currently, most L2s use centralized sequencers, making MEV extraction opaque, and potential solutions can be categorized into two directions: one is to achieve decentralization of sequencers through specific mechanisms, and the other is to outsource ordering rights to third parties to construct ordering schemes.
Decentralized Sequencers
Blockspace Auctions allocate ordering rights through bidding. In this mechanism, participants publicly bid for block space during a specific time period and then enjoy the ordering rights for that block space. The advantage of this approach lies in its transparency and competitiveness, which can encourage participants to offer more reasonable prices. However, the downside is that it may lead to the "winner's curse," where the winner suffers losses due to overbidding.
Random leader election randomly selects a leader from a pool of participants who meet specific conditions for ordering. For example, selecting from users who have staked 32 ETH, like Starknet's random selection method. The advantage of this method is its randomness, which can reduce potential unfair competition, but the downside is that it may overlook the abilities and contributions of participants, and a lack of competition may lead to decreased efficiency.
Proof-of-Work allows many potential sequencers to compete for the construction of a block, with sequencers winning by being the most efficient or fastest competitors. The advantage of this method is that it encourages technological innovation and efficient operation, while the downside is that it may lead to significant resource waste.
Economic competition is a method where different participants compete to achieve the best economic outcomes. For example, determining the order of block inclusion based on block fees, this method is relatively flexible and has much design space, such as MEV redistribution, MEV auctions, etc., encouraging everyone to construct blocks through an open economic mechanism. This approach stimulates market vitality but may also allow a few entities to monopolize ordering rights through competitive advantages.
Fair Sequencing is a method of directly ordering transactions through specific algorithms, essentially forming a language and network. Chainlink has already implemented this solution, and the advantage of fair sequencing is that it limits the space for extracting MEV value by adjusting transaction order from the ground up. However, the downside is that the performance of DAPPs under fair sequencing may deteriorate, and the applicability of fair sequencing rules is not high.
The implementation of decentralized sequencers may not only promote fairness and transparency but also enhance the overall security of the system. However, it also brings a series of challenges, such as resource waste and market barriers. From a future perspective, all L2s will likely move toward decentralized sequencers, but currently, due to efficiency and cost considerations, most L2s are expected to maintain centralized sequencers.
Outsourcing Ordering Rights to Third Parties
Shared sequencers, such as Espresso and Astria, focus on providing ordering services, organizing ordering in specific ways, and the chains accessing their services do not need to consider the ordering issue themselves. The benefit of this approach is that it can standardize and professionalize the work of sequencers, but it may also introduce external dependencies, affecting the degree of decentralization.
From a personal perspective, the shared sequencer solution is essentially a modular idea, but we should also consider that for a public chain, establishing a feasible decentralized solution and mechanism for block construction and transaction ordering is part of building a public chain. With the rise of modularization, shared sequencers may be widely used.
By organizing cross-chain MEV auctions, indirectly providing ordering services, such as SUAVE. SUAVE is essentially a chain, and using SUAVE's solution effectively outsources block construction and mempool services to SUAVE.
The characteristics of SUAVE include: SUAVE itself does not capture MEV (except for gas fees); seekers (who express their preferences on SUAVE) extract MEV by requiring executors to accept their transaction bundles (including cross-chain MEV); executors can also capture a portion of the seekers' MEV (paying back as much as possible to the seekers). The advantage of this method is that it can optimize resource allocation through an open market, while the downside is that it may increase system complexity and potentially reduce the level of decentralization.
Outsourcing block construction to L1, i.e., Based Rollup (e.g., Taiko).
L1 has already built a sufficiently decentralized system capable of providing decentralized ordering services. The MEV extraction method of Based Rollup is as follows: MEV naturally flows to Ethereum, enhancing the economic security of L1; L2 seekers (creating L2 transaction bundles) and L2 builders (who can run mev-boost) can also share a portion of MEV; if L2 seekers monitor the Ethereum mempool, the mempool based on Rollup, and the states of both chains, they can capture cross-chain MEV value. This solution is quite feasible, but the downside is that the upper limit will not exceed the current solutions, as Ethereum currently has a large MEV extraction space under its current architecture. Outsourcing ordering rights to L1 does not improve the MEV ecosystem.
Outsourcing block proposal work to third parties can bring advantages in resource optimization and risk decentralization, but it also poses potential threats to decentralization.
L2 MEV Data
The dune dashboard created by Dragonfly's data analyst @hildobby showcases some L2 MEV data.
Polygon
Sandwich attacks on Polygon are relatively rare, mostly staying below 1%. In September of this year, it peaked at around 2.3%. Based on transaction volume, the volume of transactions affected by sandwich attacks is very low.

Sandwich Transaction Ratio

Sandwich Transaction Volume
Arbitrage transactions on the Polygon network account for a higher proportion, and the transaction volume is significantly greater than that of sandwich attacks.
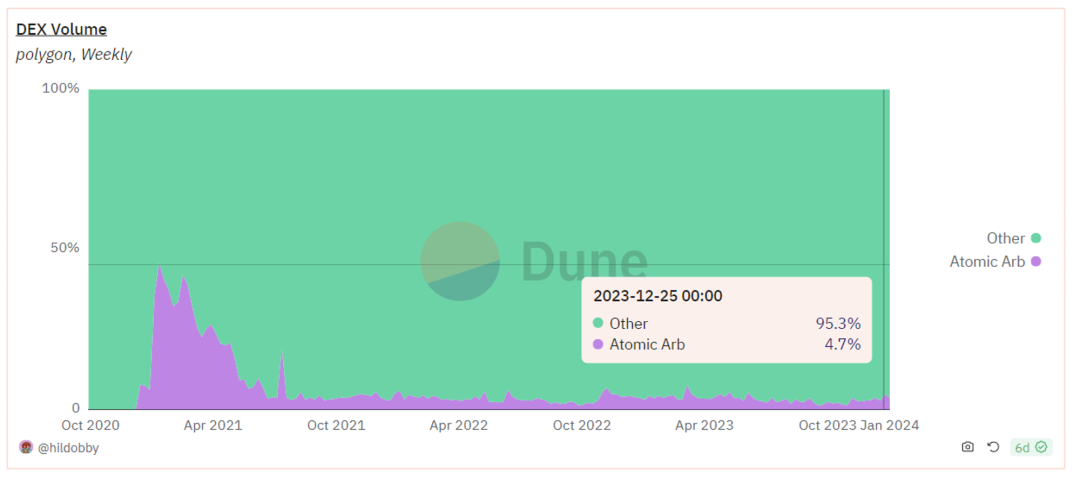
Arbitrage Transaction Ratio
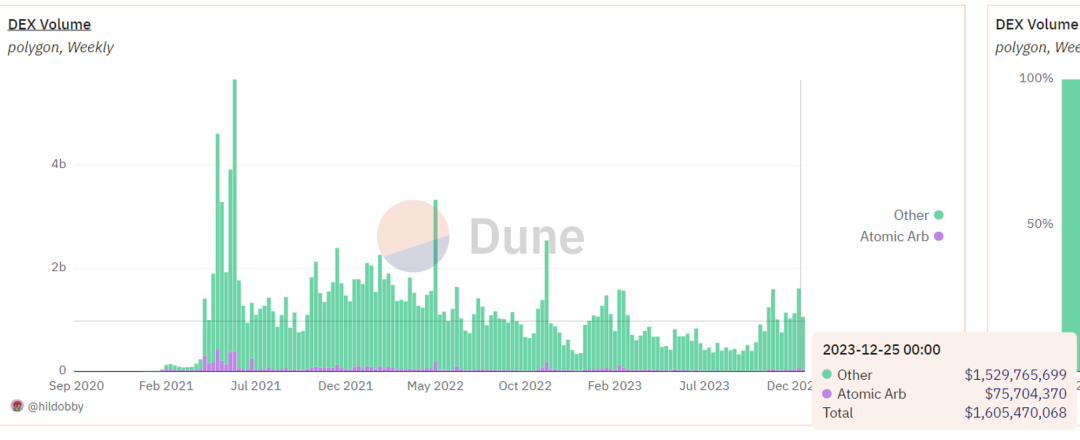
Arbitrage Transaction Volume
Arbitrum
Since 2023, the proportion of sandwich attacks in Arbitrum block transactions has dropped to a sufficiently low level. In terms of transaction volume, the total transaction volume is in the billions, while the volume of transactions involving sandwich attacks is only in the hundreds of thousands, which is also very small. This may be related to Arbitrum's FIFO transaction ordering rules.
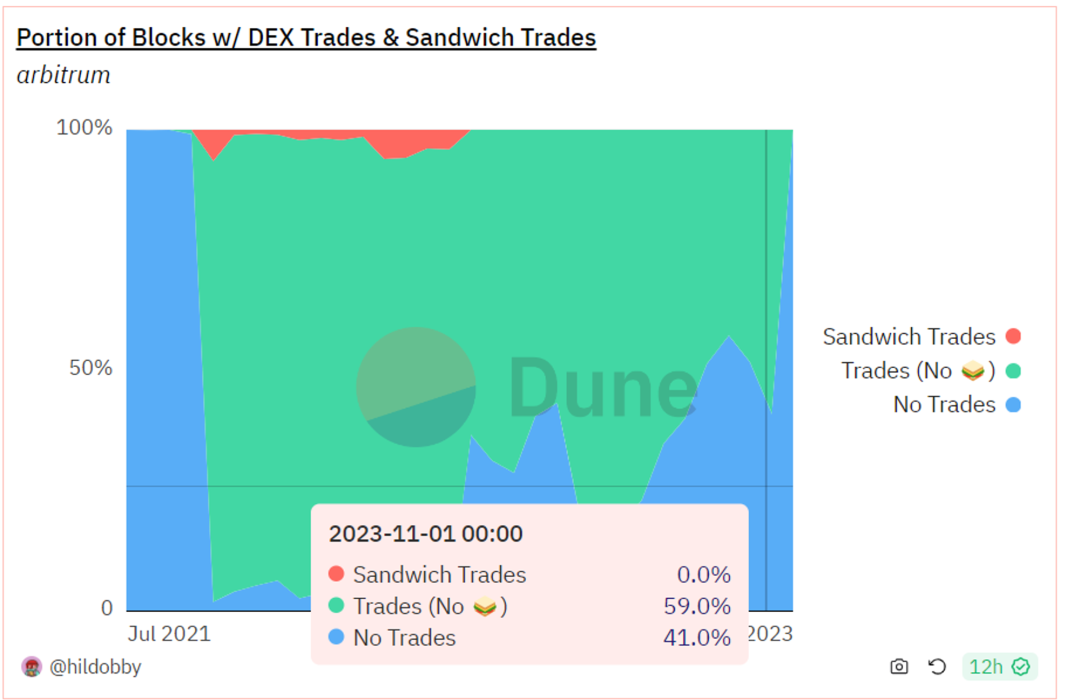
Sandwich Transaction Ratio

Sandwich Transaction Ratio
Compared to other chains, the proportion of arbitrage transactions on Arbitrum is relatively small. However, compared to sandwich transactions on Arbitrum, the volume of arbitrage transactions is still much larger.
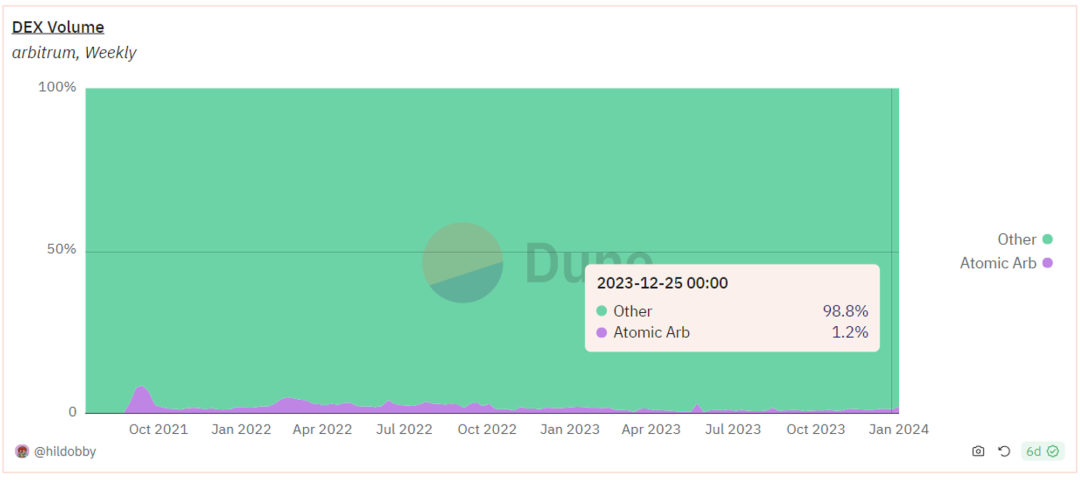
Arbitrage Transaction Ratio
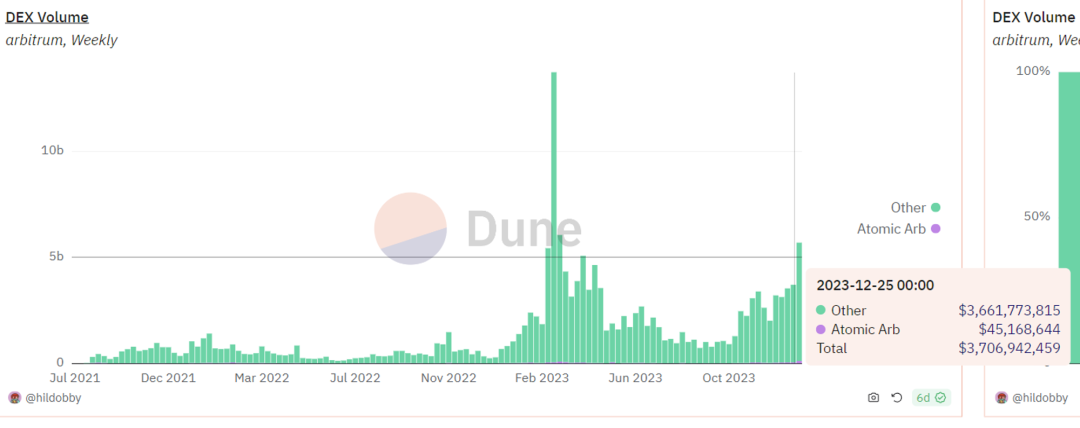
Arbitrage Transaction Volume
Optimism
On Optimism, the situation is different. The proportion of sandwich attacks in block transactions once reached as high as 62.7%, but over time it has gradually decreased due to the Bedrock upgrade introducing a gas mechanism similar to EIP-1559. Recently, the proportion of sandwich attacks has dropped to a sufficiently low level. In terms of transaction volume, the scale of sandwich attacks has decreased to a few thousand dollars.
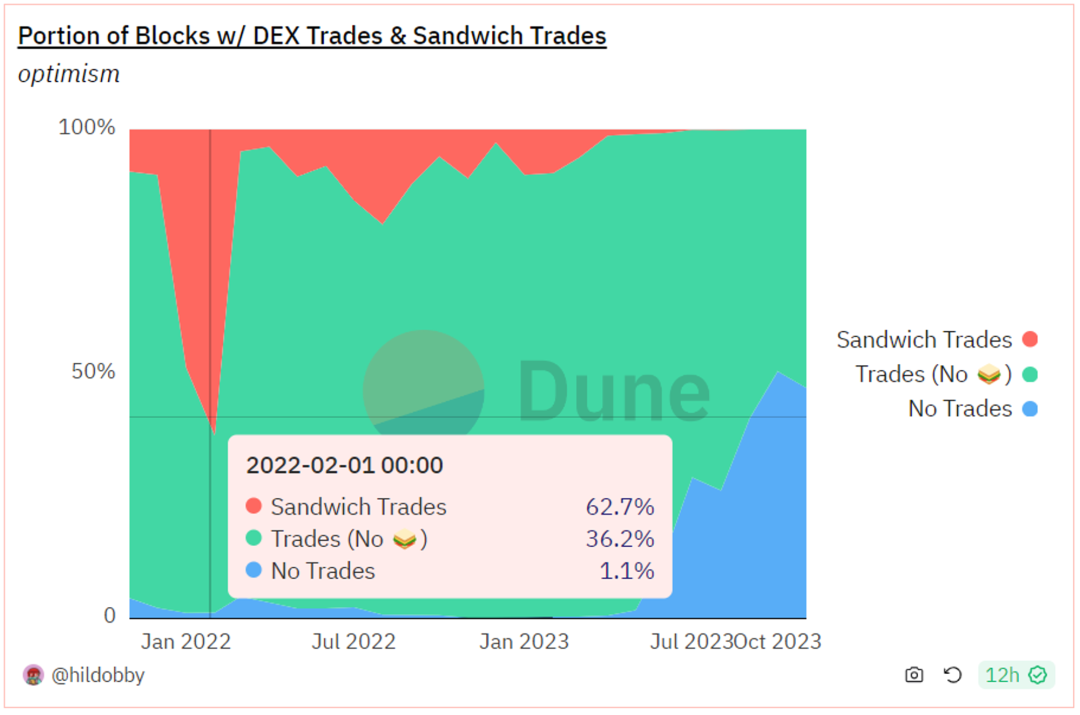
Sandwich Transaction Ratio

Sandwich Transaction Volume
On Optimism, the proportion of arbitrage transactions is between 2% and 4%, showing a downward trend compared to last year. The transaction volume of arbitrage transactions is relatively low.
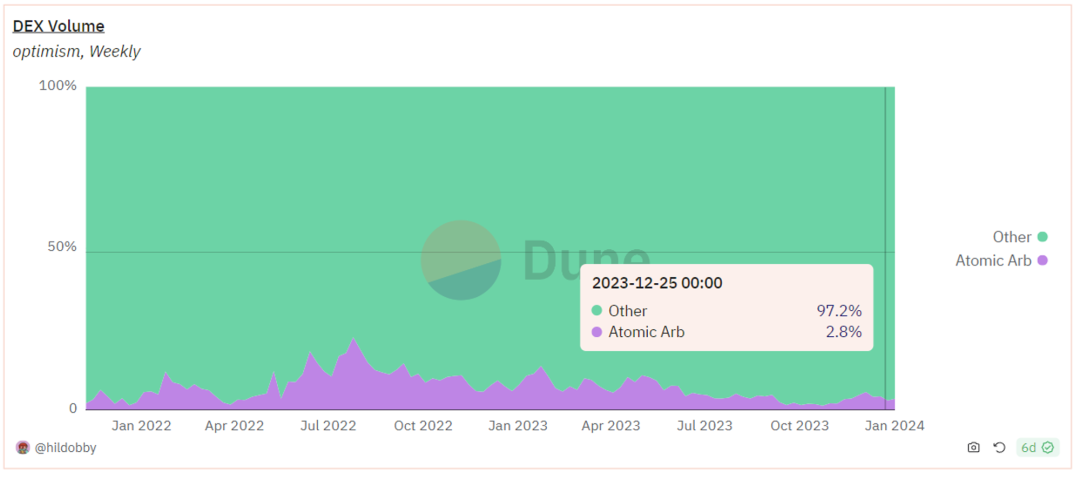
Arbitrage Transaction Ratio
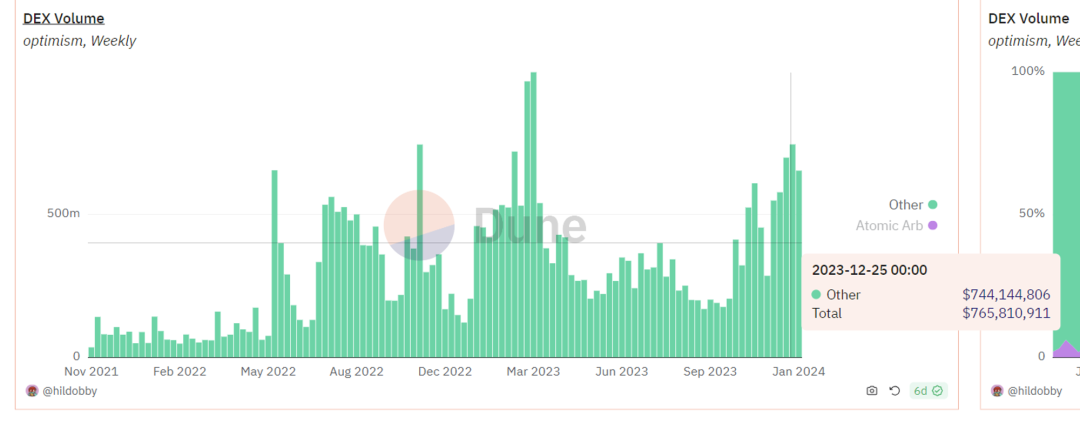
Arbitrage Transaction Ratio
Conclusion
In summary, the relationship between L2 Sequencer and MEV is of significant importance to the development of the ETH ecosystem. Currently, L2 faces the challenge of ensuring a fair and transparent ordering mechanism to prevent MEV extraction. However, the complexity and diversity of L2 solutions bring many challenges, including how to resist MEV and ensure fair and transparent ordering mechanisms. At this stage, there are already some feasible solutions, such as Shared Sequencer and cryptographic methods to protect the privacy of transaction ordering.
In the future, practical solutions may focus more on the decentralization of Sequencers to reduce potential MEV extraction space. At the same time, outsourcing block generation to third parties can improve the fairness and efficiency of the entire network system. On the other hand, the emergence of cross-chain MEV requires us to re-examine the definition and importance of MEV and explore new solutions such as Slot Auctions and Interchain Scheduler. Additionally, future research questions include how to quantify MEV on L2 chains and the impact of PGA on L2, and addressing these issues will help further refine MEV resistance strategies in the L2 space.


























