Breaking the Islands Between Chains: A Detailed Explanation of How Cross-Chain Technology Shapes an Open and Interconnected Crypto World

So far, how many public chains (L1s & L2s) do we actually have?
Perhaps no one can immediately provide an accurate answer to this question. According to DefiLlama, there are currently as many as 225 public chains recorded, in addition to a large number of new chains that have not yet been recorded or launched. It can be said that the crypto world is a chaotic world composed of multiple chains.
In this multi-chain coexistence of the crypto world, each chain has its unique technical characteristics, community support, development tools, and ecosystems. For example, there are POW public chains led by Bitcoin, EVM-based public chains represented by Ethereum and a host of L2s, high-speed public chains like Solana, and Move-based public chains represented by Aptos and Sui. This diversity indeed provides more possibilities for decentralized applications (DApps) and financial innovation. However, at the same time, it also brings a series of challenges.
Interoperability, that is, the interaction of assets and information between different blockchains, has become an urgent problem to be solved. In the past, different blockchain systems were like islands to each other; they each had a large amount of assets and data but could not effectively interact with other chains. This is undoubtedly a huge obstacle for a crypto world that hopes to achieve true decentralization.
To solve this problem, cross-chain technology has emerged, attempting to break these islands and enable different blockchain systems to smoothly exchange assets and information. For developers and users, cross-chain not only means greater liquidity and choice but also signifies a more open and interconnected blockchain world.
In this article, we will explore why we need cross-chain, the core concepts, classifications, implementation methods, and challenges of cross-chain technology, as well as how it will shape our future crypto world.
Part 1 The Need for Cross-Chain
Is cross-chain technology really necessary for us to achieve a truly decentralized and interconnected blockchain future?
I believe many people will have different answers to this. Influenced by a series of security incidents that have occurred in the cross-chain field, some people have even become "Pavlov's dogs," automatically identifying cross-chain as a "pseudo proposition" or "trap" whenever it is mentioned. This is the tragedy of these individuals and the entire industry.
However, it must be acknowledged that multi-chain coexistence is the current market landscape, and with the increasing number of public chains and Layer 2s (Rollups) and the gradual improvement of their ecosystems, cross-chain will inevitably become a necessity in the current market landscape. From the following two aspects, you may find the answer:
First, the interoperability issue has become an increasingly obvious pain point. Among the more than 225 public chains, each may have its specific applications, assets, and users. However, if the value created on these chains cannot flow to other chains, its potential will be severely limited. This is not just an issue of asset trading; it also involves the interoperability of data, logic, and applications.
This is precisely the "island" problem that the current blockchain world faces. There are rich resources between these islands, but due to mutual isolation, they cannot be fully utilized. Imagine if major platforms on the internet could not communicate with each other; our online experience would be greatly diminished, and the situation on the blockchain is similar.
Second, asset liquidity is the core of the financial system. In the traditional financial world, assets can flow freely between major exchanges, banks, and financial institutions. However, in the current blockchain field, the liquidity of assets on different chains is restricted. This not only affects the trading experience of users but also limits the further development of decentralized finance (DeFi).
Therefore, whether from the perspective of interoperability issues or asset liquidity issues, we have a practical need for cross-chain, which includes both traditional asset cross-chain bridges and interoperability protocols. In the following chapters, we will attempt to classify all cross-chain solutions from a technical perspective and provide separate introductions for these two categories to help readers gain a better understanding.
Part 2 Classification of Cross-Chain Solutions
Cross-chain technology has rapidly developed in recent years, providing us with a range of methods to solve the interaction problems between chains. These cross-chain solutions can be classified in different ways based on various dimensions. Here, we introduce the cross-chain analysis framework proposed by Connext founder Arjun Bhuptani, which categorizes them into three main types based on the message verification methods of interoperability protocols (cross-chain bridges): native verification, external verification, and local verification.
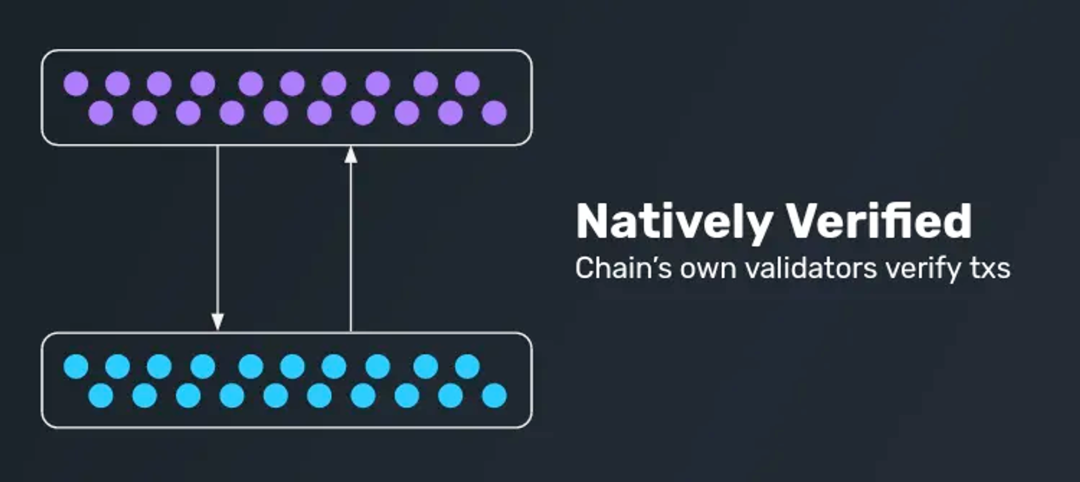
Native Verification
 (Chart source: Connext, Arjun Bhuptani)
(Chart source: Connext, Arjun Bhuptani)
In the native verification model, a light client or light node of the source chain runs on the target chain to verify messages from the source chain on the target chain. The main advantage of this method is its high trustworthiness and decentralization. Because the verification logic of the light client is identical to that of other types of nodes in verifying blocks, it provides a robust cross-chain verification mechanism.
The key role in this mechanism is the Head Relayer, which is responsible for transmitting the block header information of the source chain to the light client on the target chain for verification. The challenge of this method lies in its dependence on the underlying consensus mechanism and the potential complexity involved, especially as the number of chains that need to be handled increases.
Projects that adopt native verification include Cosmos IBC, Near Rainbow Bridge, Snowbridge, etc., where the entry/exit of Rollups is also a special form of native verification.
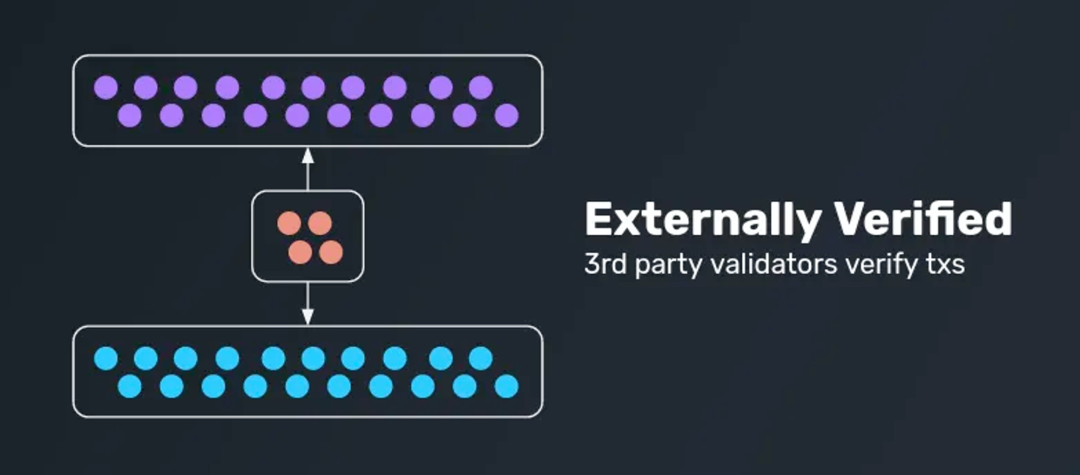
External Verification
 (Chart source: Connext, Arjun Bhuptani)
(Chart source: Connext, Arjun Bhuptani)
The external verification method involves introducing an external set of validators to verify cross-chain messages. This external validator set typically consists of multiple entities, and external validators can take various forms, including multi-party computation systems (MPC), oracles, multi-signature groups, etc. These validators/witnesses are essentially not very different. One obvious advantage of this method is its high scalability, as it can be easily extended to any blockchain (bridges using external verification currently account for the highest proportion in the cross-chain bridge track).
However, it is worth noting that introducing an external validator set also means introducing new security assumptions. The security of this model is determined by the lowest security among Chain A, Chain B, and the external validator set. For this reason, this approach may increase the system's vulnerabilities.
Examples of external verification protocols include Wormhole (Portal Bridge), Axelar, Chainlink CCIP, Multichain, etc. Essentially, the solution adopted by LayerZero also falls under external verification.
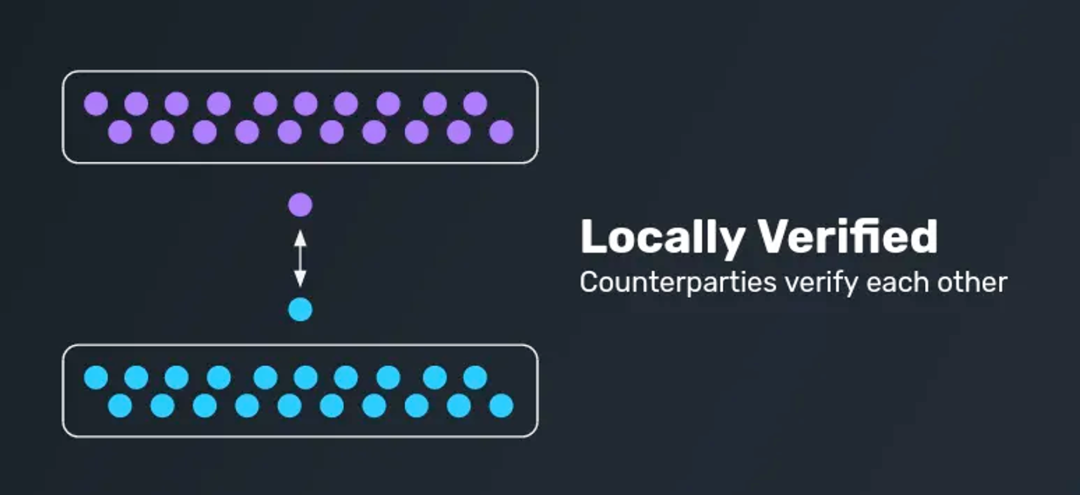
Local Verification
 (Chart source: Connext, Arjun Bhuptani)
(Chart source: Connext, Arjun Bhuptani)
Unlike the above two methods, local verification, also known as peer-to-peer verification, focuses on the direct verification between the two parties involved in the transaction. This method typically involves a hash time-locked contract (HTLC), where both parties can verify each other's transactions. Since the parties involved in this model usually have adversarial economic interests, the possibility of collusion is greatly reduced.
One significant advantage of this method is its decentralization and high trustworthiness for both parties involved in the transaction. However, it also faces some challenges, such as the potential need for both parties to be online simultaneously and the inability to support general data transmission between chains (meaning that local verification is only suitable for swap bridges, primarily for Ethereum cross-layer asset bridges).
Typical cases that adopt local verification include Connext, cBridge, Hop, etc.
In summary, the above three cross-chain technology methods each have their advantages and limitations, and they are only classified based on one dimension. In practice, the specific choice of which method to use depends on the specific application requirements, security considerations, and the nature of the chains involved. As the crypto field continues to evolve, we look forward to more innovative methods to address the challenges of cross-chain interaction.
Part 3 Asset Cross-Chain and Cross-Chain Messaging
Having introduced the basic concepts of cross-chain and the classification of cross-chain solutions, I believe everyone now has a preliminary understanding of cross-chain technology. To provide a clearer understanding of asset cross-chain and cross-chain messaging, this chapter will mainly introduce the differences between the two.
Asset Cross-Chain
Asset cross-chain is the technology that enables digital assets to seamlessly migrate from one blockchain to another. It is also the most common and popular cross-chain application today, as it addresses a core issue: how to represent and use the same asset across different chains. The common working principle of asset cross-chain is as follows:
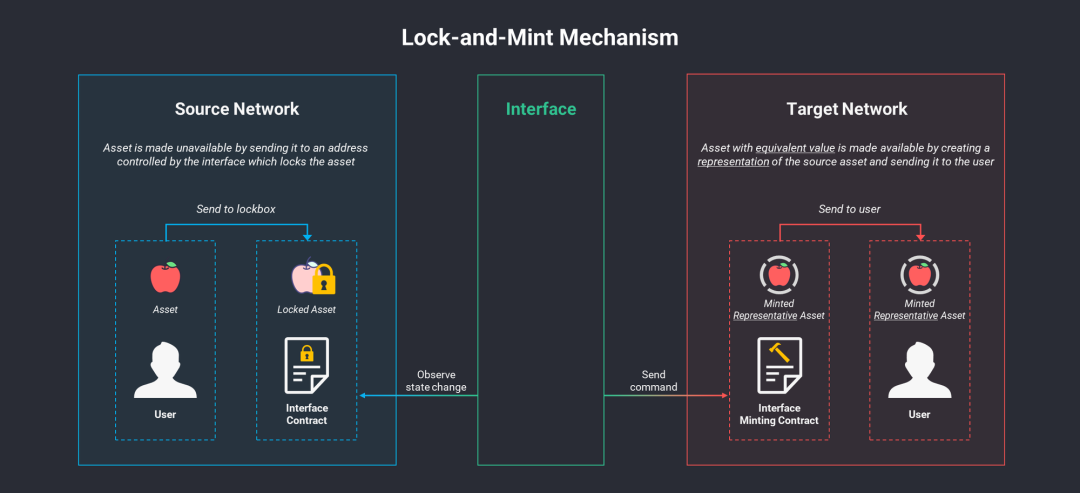
Lock-and-Mint
In the asset cross-chain process, the most common method is lock-and-mint. Simply put, when an asset moves from the source chain to the target chain, it is locked on the source chain and "minted" on the target chain. (A similar mechanism is burn-and-redeem; due to space constraints, this article will not elaborate on it. A typical case is the cross-chain method adopted by USDC issuer Circle.)
 (Chart source: web3edge, @0xPhillan)
(Chart source: web3edge, @0xPhillan)
For example, when BTC is used as a token on Ethereum, the original BTC is locked, and an equivalent Wrapped Bitcoin (WBTC) token is generated on Ethereum. This ensures that the total supply of BTC does not change, thus maintaining the asset's scarcity. In addition to WBTC, some official bridges of Ethereum's Layer 2, such as Polygon Bridge, Arbitrum Bridge, and the Rainbow Bridge connecting Ethereum and the Near ecosystem, also adopt the lock-and-mint/burn mechanism.
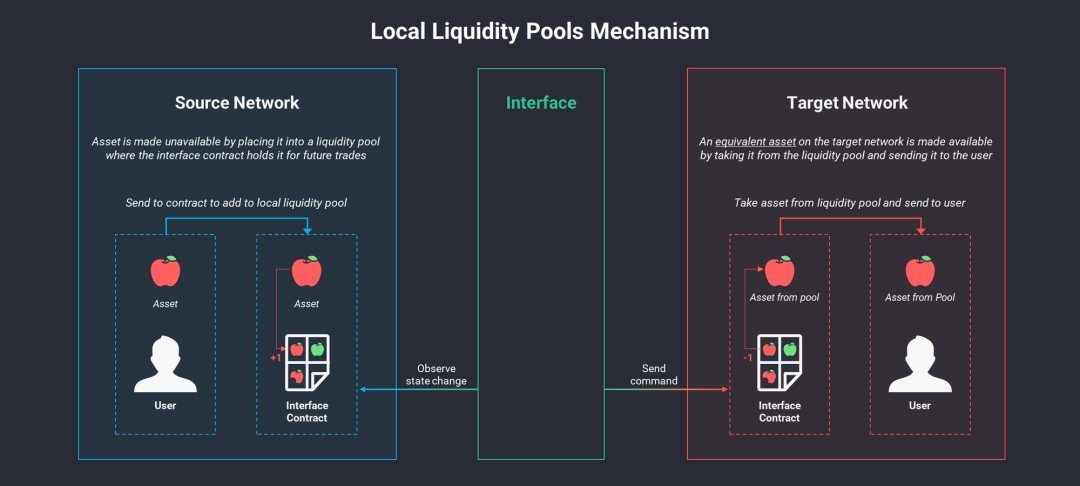
Liquidity Pool
Liquidity swapping involves using a special liquidity pool to facilitate cross-chain transactions. When users perform cross-chain transactions, they can deposit their assets on one chain into the liquidity pool and withdraw equivalent assets from the liquidity pool on another chain. The benefit of this method is that it can provide fast transactions and exchanges, but it may involve certain fees, as liquidity providers (LPs) typically expect to be compensated for the liquidity they provide.
 (Chart source: web3edge, @0xPhillan)
(Chart source: web3edge, @0xPhillan)
Mechanically, the security risks of this type of cross-chain bridge are primarily borne by the LPs. If the pool is hacked, the liquidity provided by the LPs is likely to be stolen by the hacker. An imbalance in the liquidity pool can also lead to the value of cross-chain assets evaporating, thus transmitting the crisis to cross-chain users. Cross-chain bridges that adopt liquidity pools include ThorSwap, Hop Exchange, Synapse Bridge, etc.
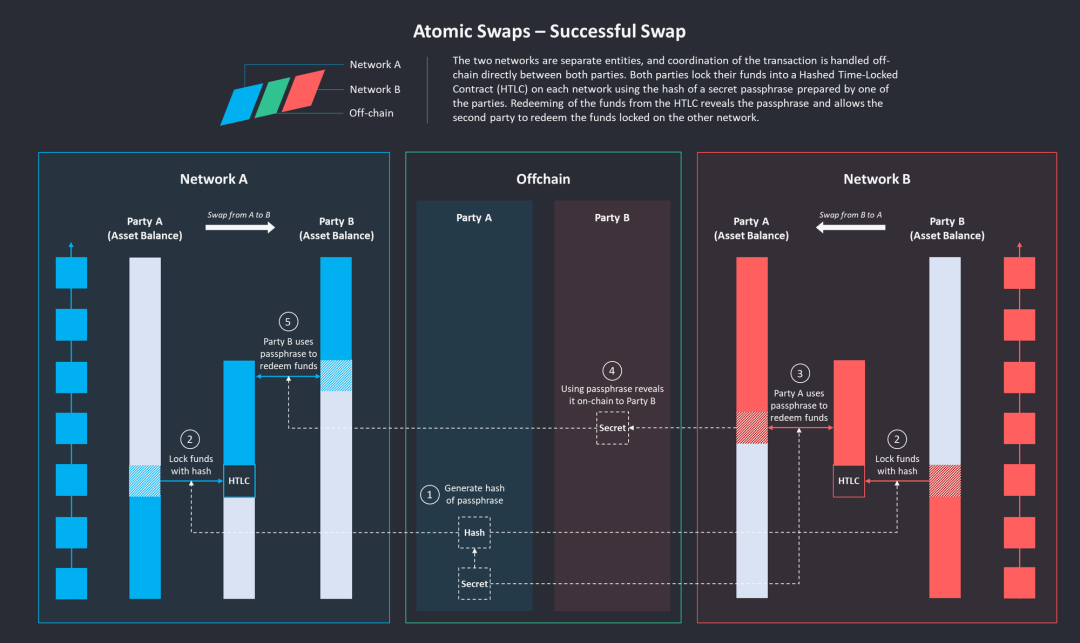
Atomic Swaps
Atomic swaps allow two parties to exchange assets directly without the need for intermediaries. It achieves this by utilizing hash time-locked contracts (HTLC), ensuring that the exchange is "atomic," meaning the transaction is either fully completed or not executed at all. In atomic swap cross-chain bridges, assets are accessed through private keys, and if one party acts maliciously, the other party can retrieve the assets through a time lock (which can only be opened after a specified time), without needing a centralized third party to provide trust assurance. Typical projects that adopt atomic swap cross-chain methods include Connext, cBridge, etc.
 (Chart source: web3edge, @0xPhillan)
(Chart source: web3edge, @0xPhillan)
Cross-Chain Messaging
Unlike asset cross-chain, cross-chain messaging involves not only assets but also all types of information transmitted from one chain to another, such as contract calls, state updates, etc.
State Synchronization
A common method of cross-chain messaging is through state synchronization. This means that the state or part of the state of one chain is synchronized to another chain. For example, the relay chain of Polkadot is responsible for handling the synchronization of the states of its various parachains.
Event Listening and Response
When an event occurs on one chain (such as a transaction being confirmed or a smart contract being called), another chain can be configured to listen for these events and respond as needed. For example, ChainSafe's ChainBridge adopts this method to handle cross-chain messaging.
In fact, whether it is asset cross-chain or cross-chain messaging, the core challenge is to ensure the integrity, security, and timeliness of the information. With the development of technology, new cross-chain solutions will continue to emerge, providing stronger and more flexible support for interoperability in multi-chain environments.
Part 4 Challenges of Cross-Chain
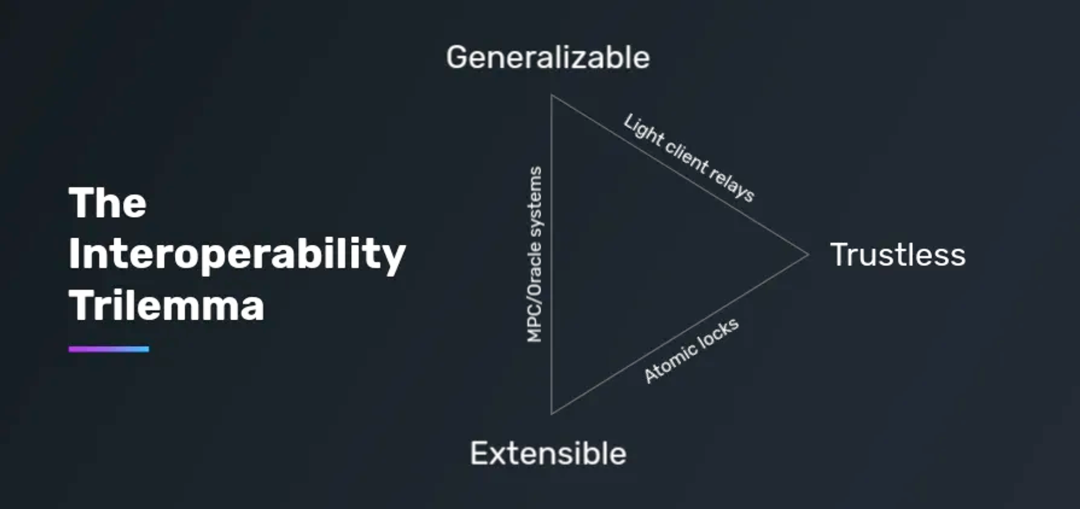
In the development and increasing maturity of blockchain, cross-chain technology has become an important research direction aimed at achieving seamless communication of assets and data between different blockchains. However, achieving this goal is not easy. Analogous to the "impossible triangle" in monolithic blockchains, there is also a "trilemma" in the field of cross-chain interoperability.
According to the framework proposed by Arjun Bhuptani, any cross-chain solution design can satisfy at most two of the following three:
- Scalability (Extensible): Supports arbitrary message transmission
- Trustlessness (Trustless): Does not introduce new trust assumptions
- Generalizability (Generalizable): Can easily adapt to more blockchains
 (Chart source: Connext, Arjun Bhuptani)
(Chart source: Connext, Arjun Bhuptani)
When we cannot satisfy all three at the same time, we need to make trade-offs and balances among them, and this trade-off may have higher complexity compared to monolithic blockchains. It includes security and trust trade-offs, unification and diversification trade-offs, wrapped assets and native assets trade-offs, etc. These are all challenges that cross-chain technology will face in its continued development and evolution. It can be said that various cross-chain bridge projects are attempting to optimize or even break the trilemma from different angles, aiming to achieve the highest overall performance.
Part 5 Conclusion and Outlook
Cross-chain technology is a key area of blockchain development and is even considered the holy grail of the blockchain field, as it is the key technology to break the blockchain "islands" and achieve interconnectivity among thousands of chains. From asset cross-chain to messaging cross-chain, all Web3 builders are striving to create a unified and collaborative blockchain ecosystem.
However, as we have discussed, cross-chain technology still faces many challenges. But with the deepening of research and technological advancements, we look forward to overcoming these challenges in the future, achieving a more secure, efficient, and seamless cross-chain ecosystem.
References:
[1] The Interoperability Trilemma (https://medium.com/connext/the-interoperability-trilemma-657c2cf69f17)
[2] Master Web3 Fundamentals: Interoperability & Bridges (https://web3edge.io/fundamentals/master-web3-interoperability-bridges#)
[4] Not in the Profound Cross-Chain Bridge: A Comprehensive Explanation
Follow us:
Chinese Official Twitter/X: https://twitter.com/wormholeCHN
Chinese Telegram: https://t.me/wormholechina
Scan the WeChat QR code
Follow this public account









