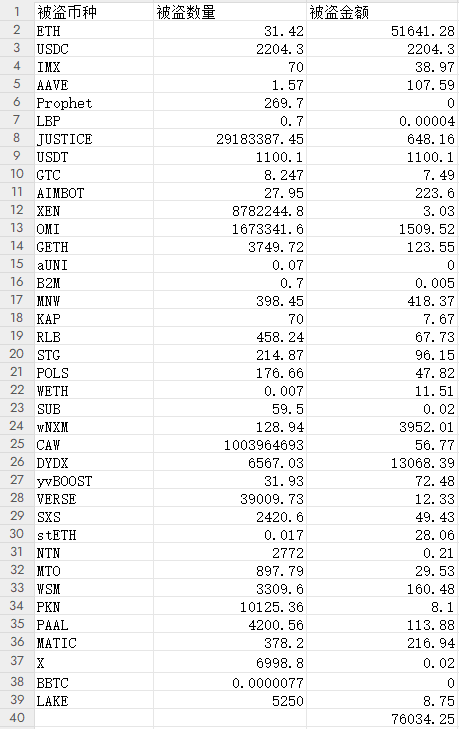
Beosin: After Galxe encountered DNS hijacking, most user funds were transferred to the hacker address 0x4103
According to ChainCatcher news, monitoring by Beosin's Beosin EagleEye security risk monitoring, early warning, and blocking platform shows that Galxe is suspected to have suffered a DNS hijacking attack, resulting in a large amount of user funds being stolen. The currently reported stolen funds involve multiple cryptocurrencies, primarily sent to the address 0x4103baBcFA68E97b4a29fa0b3C94D66afCF6163d, which has collected over $70,000 in virtual currency. Almost all of the funds were eventually converted to ETH and sent to the address 0x1c0e96Ef2A82b573B826B4138DF9c126AA4d1825, while some funds were sent to the address 0x412f10AAd96fD78da6736387e2C84931Ac20313f, and part of the funds entered FixedFloat. The image shows the fund statistics for the address 0x4103baBcFA68E97b4a29fa0b3C94D66afCF6163d.