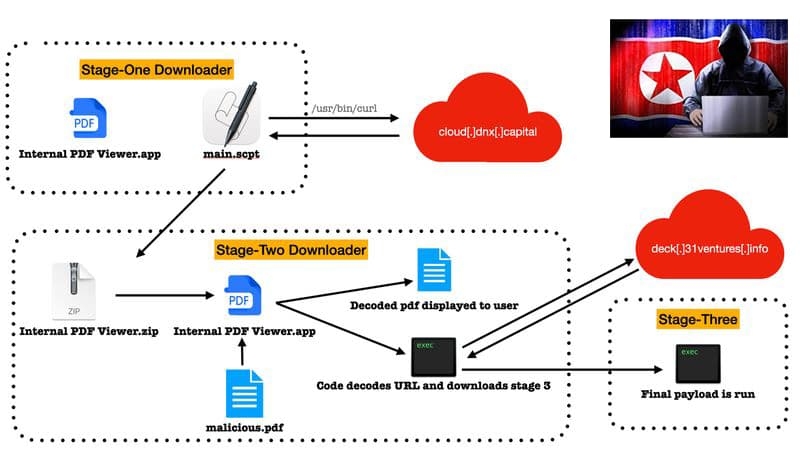
Slow Fog: Domains and Trojan samples used by North Korea's Lazarus group have been discovered
ChainCatcher news, recently, Slow Mist and its partners discovered a large-scale APT attack activity directed at the cryptocurrency industry by the North Korean Lazarus group.
It is reported that their attack methods are as follows: first, they impersonate identities, tricking reviewers through real-person authentication to become legitimate customers, and then making real deposits. Under the cover of this customer identity, they then specifically deploy customized Trojans for Mac or Windows targeting official personnel during multiple communication points with officials and customers (attackers). After gaining access, they conduct lateral movement within the internal network, remaining dormant for a long time to achieve the goal of stealing funds.