Interpreting Vitalik's Latest Paper: Privacy Pools, Making Compliance No Longer at the Expense of Privacy and Centralization
Written by: Deep Tide TechFlow
Yesterday, Vitalik and several scholars from the University of Basel jointly published a paper titled "Blockchain Privacy and Regulatory Compliance: Towards a Practical Equilibrium," which has garnered widespread attention on Twitter.
Why should we pay attention to such papers during a market downturn?

Vitalik's thoughts and writings often influence the direction of new narratives and technological developments. Additionally, other well-known experts in the blockchain field have unique insights into blockchain technology and development trends.
Moreover, the paper discusses issues of blockchain privacy and compliance, which are crucial for the future development direction and compliance path choices of the crypto industry. Finding a balance between protecting user privacy and meeting regulatory requirements is a pressing challenge for the crypto industry.
After reading the paper, we found that the proposed Privacy Pools protocol provides a feasible technical solution for achieving compatibility between privacy and compliance. This seems to prevent the tragedy of Tornado Cash being condemned by regulation from happening again.
However, the paper is quite academic and technical, making it difficult for ordinary users to understand some of its details and implications.
Therefore, Deep Tide Research Institute has interpreted and refined the paper, attempting to explain its core points in plain language to help more people understand the important topic of privacy and compliance, as well as its technical pathways and possible solutions.
Who are the authors?
First of all, the paper is led by Vitalik, with contributions from professionals in academia and the industry.
Vitalik serves as the first author. Due to his significant influence and reputation in the cryptocurrency field, he can draw more attention to the proposed solutions.
Other co-authors include: Jacob Illum, a researcher at the crypto industry research firm Chainalysis;
mat nadler, a PhD student at the University of Basel, who is also involved in relevant DeFi and EVM development projects;
Fabian Schär, a professor at the University of Basel, whose research focuses on public chains and DeFi protocols;
Ameen Soleimani, founder of several well-known crypto projects with rich practical experience.
Background: The contradiction between privacy and regulation, the tragedy of Tornado Cash
The design of public blockchains is transparent for transactions, allowing anyone to verify transactions without relying on centralized third parties. However, this also brings privacy issues, as every transaction of each address is recorded on the blockchain, making addresses traceable and analyzable.
The Bitcoin white paper suggests that blockchain can ensure privacy through public key anonymity, but this protection has proven to be insufficient, as various blockchain analysis tools can link addresses and transactions. Therefore, more robust cryptographic techniques are needed to enhance privacy protection on public chains.
Systems using general zero-knowledge proofs, such as Zcash and Tornado Cash, can enlarge the anonymity set to include all transactions, thereby enhancing privacy protection. However, Tornado Cash has also been abused by some hackers, leading to its smart contract address being sanctioned by OFAC.
Regarding the issues with Tornado Cash, Deep Tide also provides some technical background for readers who may not be familiar with the previous regulatory sanctions:
Tornado Cash is a privacy-enhancing protocol based on zero-knowledge proofs that enables anonymous transactions. It allows users to deposit funds and then withdraw them at another address, where only deposits and withdrawals are visible on-chain, without revealing the correspondence between the two, thus ensuring anonymity.
However, this protocol has also been abused by some hacker organizations, which have used it for money laundering. For example, there is evidence that North Korean hacker groups have laundered money through Tornado Cash.
As a result, the U.S. Treasury's OFAC ultimately placed Tornado Cash's smart contract address on the sanctions list. Regulators believe that the protocol facilitates money laundering, hindering the fight against financial crime.
The key issue with Tornado Cash is that legitimate users find it difficult to dissociate themselves from the criminal activities attracted by the protocol.
However, creating this proof relies on Tornado Cash's centralized servers. Users need to provide specific information about the withdrawal to the server, which uses its database to verify that the withdrawal corresponds to a deposit, and then generates the proof.
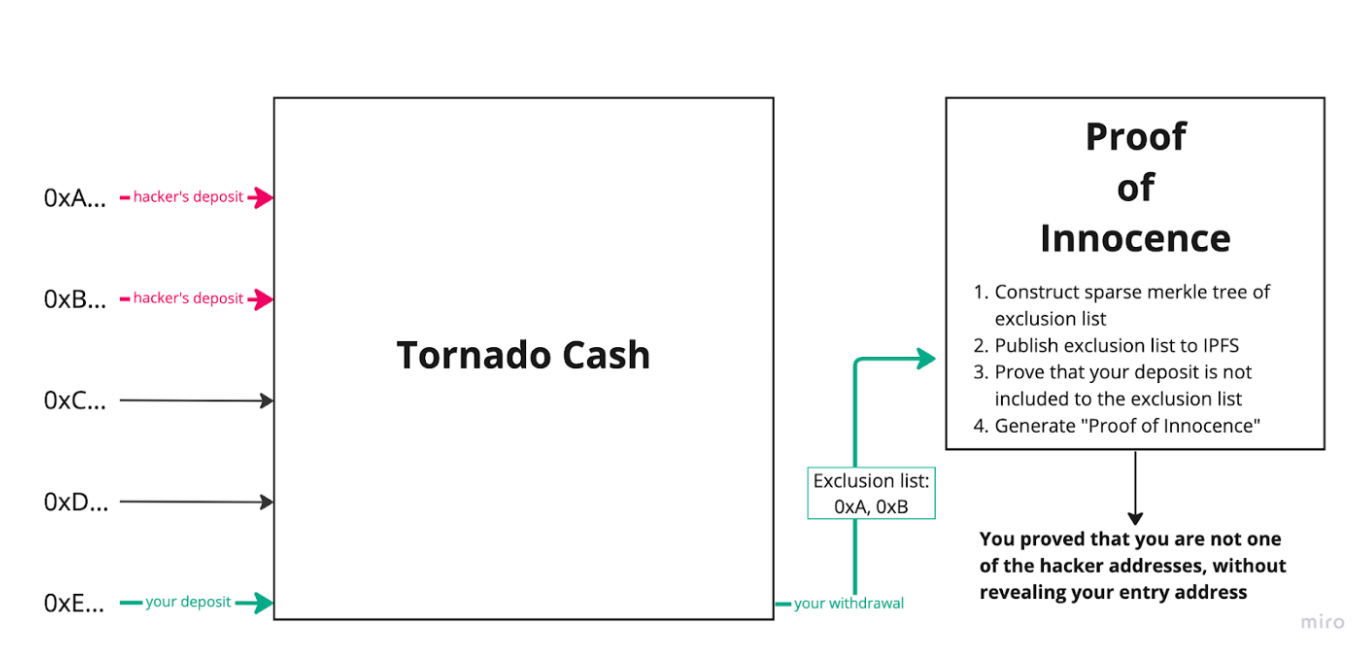
- This reliance on centralized intermediaries is necessary because only Tornado Cash holds the complete database capable of generating the correct proof. Ordinary users cannot verify the correctness of the proof, leaving users and regulators with no choice but to trust.
We urgently need a way to prove and convince regulators that my source of funds is clean and legal without exposing privacy and decentralization.
Therefore, this paper proposes a feasible technical solution called the Privacy Pools protocol: allowing users to prove that their funds come from a custom association set, protecting privacy while also proving whether they originate from certain illegal sources.
This could be the first step towards the coexistence of privacy and regulatory compliance.
zk + Association Set, the key to solving the problem
From the background described above, we understand the problem that needs to be solved: ensuring both privacy and decentralization to prove that one's funds are "innocent."
When we think of ensuring privacy, zk comes to mind. Indeed, Vitalik's latest paper affirms zk, especially the value of zk-SNARKs in addressing privacy issues:
Zero-knowledge: Does not disclose private data, only proves that the statement is correct.
Conciseness: The proof is short, verification is fast, and even if the computation is complex, it is highly efficient.
However, relying solely on zk-SNARKs can only solve part of the problem: proving that I have made this transaction while hiding the transaction details.
To thoroughly solve the problem, it is necessary to prove that the source of this transaction is legitimate while hiding the transaction details.
Thus, this paper connects zk with another method—Association Set.
An association set allows users to prove that their funds come from a custom set rather than being completely hidden or fully disclosed. For example, if I transferred 1 BTC, but this 1 BTC was accumulated from several other transactions, then these other transactions can form an association set.
The association set can be large or small, and users can freely determine its composition and scope; it can be a large anon set to enhance privacy or a small set to prove compliance.
Once we understand the concept of the association set, let's see how zk + association set can ensure both privacy and prove the source of funds:
When users deposit, a secret (key) is generated through zk, and then a public coin ID is calculated. (Marking the association between me and the money)
When users withdraw, they must submit a nullifier to prove that they have used this secret. (Proving that the money is mine)
Users only need to prove through zk technology: my coin ID exists in both the total set and the declared association set. (Proving that the money is clean)
The outside world can only see the number of transactions and the belonging set of this money, but cannot obtain specific information about the transfer parties.
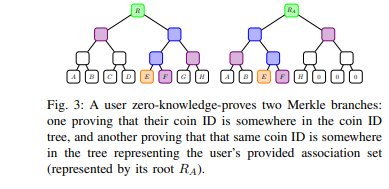
To be a bit more technical, we can look at this diagram of the Merkle tree from the original paper. The Merkle tree in the diagram is actually a combination of Coin IDs, meaning that the transaction itself is zk'd, and we cannot see the details; only the Coin IDs are stored in the tree structure.
The left tree represents all transactions that have occurred, which may include one of my own funds. Now, to prove that the source of this money is legitimate, I need the right tree—this represents a custom association set that includes my money and the associations of other transactions. As long as I correctly state the past transactions on the right, I can tell you the source of my current money.
In a broader concept, this is like a privacy pool. The association set on the right contains the origins of my money, but because it has passed through zero-knowledge proof, I can prove to you that the origins of the money are real without disclosing transaction details.
Practical Use Cases of Privacy Pools
The paper provides a very vivid example to illustrate the application of Privacy Pools.
- Background Setting:
There are five users: Alice, Bob, Carl, David, and Eve.
The first four are honest, but Eve is a known thief.
Although Eve's true identity may be unknown, the public knows that the address marked as "Eve" has received stolen funds.
User's Choices and Game When Withdrawing:
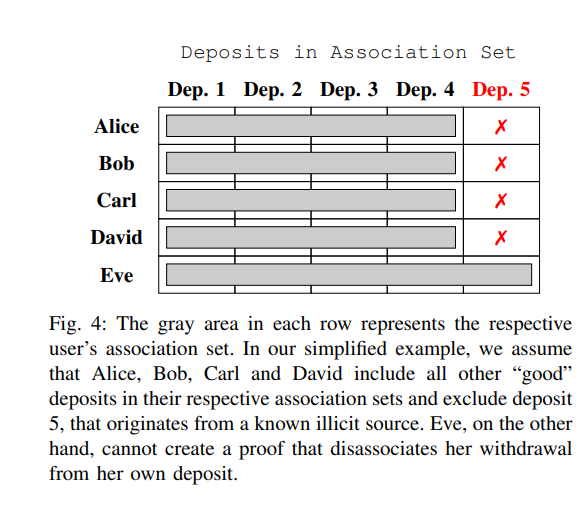
When each user withdraws, according to the method in the paper, they can choose an association set.
This association set must include their own deposits. This means that each user cannot exclude their own deposits when choosing the association set.
For Alice, Bob, Carl, and David, to avoid being associated with the known bad actor Eve, they can choose an association set that does not include Eve. This way, they can prove that they are not associated with Eve.
However, Eve faces a problem: she cannot choose an association set that only includes herself, as this would immediately reveal her as a bad actor.
To try to hide her wrongdoing, Eve might choose an association set that includes all five users, hoping to confuse observers;
However, since the other four users have chosen association sets that do not include Eve, this makes Eve's attempt futile, as people can determine through elimination that Eve is the bad actor.
- Results:
Through the choice of association sets, Alice, Bob, Carl, and David can prove that they are not associated with the known bad actor Eve.
Eve cannot hide her wrongdoing because her association set includes everyone.
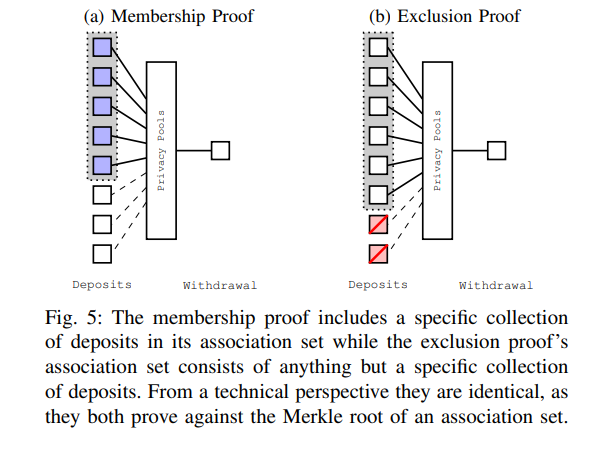
Figure 5 in the paper further illustrates the differences between these two proofs. Membership proof includes a specific deposit set, while exclusion proof's association set includes all deposits except for a specific deposit set.
Future Prospects
Although the above privacy-enhancing protocol based on zkSNARK and association sets achieves a balance between compliance and privacy for blockchain technology, there are still some technical and governance challenges. The authors propose some future development directions:
Further research on privacy attributes: The privacy provided by these protocols depends on many different factors. The size of the association set, the appropriateness of root selection, and user errors may allow specialized attackers to link users' transactions.
Research on separating balance attributes: Further study of how good and bad actors behave under certain assumptions, and how the public proofs of the former affect the privacy of the latter.
Legal research: Legal scholars can further investigate specific disclosure requirements. The recommendations proposed in this paper are highly adaptable, and insights from legal experts can help adjust the protocols and the ecosystem surrounding them to ensure compliance with various legal jurisdictions.
Finally, we believe that at this point, privacy and compliance are often seen as irreconcilable opposites.
The technology described in the paper finds a balance between the two, bringing positive significance to the entire industry. We hope that more researchers and developers can be inspired by this technology to contribute to the healthy and sustainable development of the industry.










