YBB ChainXplore: Sharing on Crypto Geeks Seminar and Web3 Winter Survival Guide
Author: YBB Capital Researcher Ac-Core
Introduction
On July 5th, amidst the drizzling weather that concealed a lukewarm cryptocurrency market, the YBB ChainXplore: Geek Symposium 01 event successfully concluded as the rain cleared. We were honored to invite many heavyweight guests—senior technical experts and founders dedicated to solving the industry's pressing needs—for a face-to-face exchange.
At the event, the guests shared insights on a series of issues, including how to ensure fund security and prevent hacker attacks; where developers can obtain cloud-based API services; how to find efficient and reliable RPC services that meet their needs; and what scalable cross-chain interoperability protocols based on MPC, ZKP, and TEE are. Now, let’s feel the sparks generated by geeks from different research directions.
Different Perspectives on the Crypto Winter
2022 was a long-awaited bear market, and with the end of the pandemic in 2023, we initially thought the market environment would improve. However, with continuous interest rate hikes by the dollar and the SEC's increasingly stringent regulatory stance on crypto trading, what was supposed to be a hopeful year has turned uncertain. As veterans in the industry, we have experienced several bull and bear cycles, so how do we view the future development of the industry? And how can each of us endure this "winter" in our respective fields? At the beginning of the event, YBB Capital co-founder John invited the guests to share how they are getting through the winter. Here are the core viewpoints from the guests.
YBB Capital Co-founder Hugh: From the end of 2020 to the end of 2022, we observed a positive correlation between market capital and technological development. The influx of capital drove the development of new narratives; for instance, the entry of large funds like Grayscale brought upward growth potential to the bull market. Later, as macro policies tightened, the market lost some liquidity. The changes in past bull and bear cycles have a certain periodicity, like gears. We need to focus more on technological development and breakthroughs in crypto to attract large capital.
From the recent Black Mountain EDCON conference, it was evident that there was more focus on breakthroughs in ZK technology and the intersection of AI and blockchain. Regarding AI, the general sentiment was pessimistic, with many believing AI will dominate the world. However, the discussions were still very interesting, with various thoughts colliding. Overall, we are also looking for a new narrative to drive the development of the next bull market.
Kernel Ventures Investment Manager Joshua: After Hong Kong released compliance policies in April this year, there is a need to align more with compliance due to liquidity considerations. Liquidity is also a highly regarded factor in the management of exchange categories. Overall, the liquidity and popularity of the project itself are still quite important. From the perspective of VC-level investments, although our frequency of investments is currently low, we are still looking for projects to collaborate with, including providing product suggestions, liquidity for assets at the product level, and connecting key resources to offer value support to projects. This is what we can currently do for the industry.
BlockPI Chief Scientist Albert He: For individuals, how can we endure this bear market? My advice is not to use leverage. When projects are raising funds, they should first think about how to navigate through bull and bear markets and prepare for the bear market. They need to enhance their operational capabilities in cost control and customer acquisition to ensure that the project can last long enough during the bear market. Looking back at previous bull and bear cycles, it is not difficult to see that they have been driven by mainstream coins. However, Bitcoin and Ethereum have already reached significant sizes, and the next bull market will certainly need to include several compliance factors. For example, BlackRock's ETH application and the clear expectations of dollar interest rate hikes indicate a turning point, after which funds will shift back to the crypto space.
Rooch Network Co-founder Haichao Zhu: The primary market is still in a cooling-off period. It can be felt that the current market is leaning towards restlessness, and a strange phenomenon has emerged. A project may not have outstanding innovations, but as long as it includes attributes like ZK, Layer2, EVM, GameFi, and has at least 100,000 users, it can easily attract VC interest. However, we will continue to focus on building infrastructure for the industry and contribute in ways we are good at.
YBB Capital Co-founder Hugh: We can also feel that the current market is polarized. Good projects are hard to invest in, while projects that are grounded but have weak technical barriers are still not attractive to VCs, even at low valuations. Most investments are driven by market sentiment, but looking at the investment results from major institutions like A16z, most projects have broken below their initial valuations. However, we still need to view the current market with optimism and maintain the passion to seek new technological breakthroughs.
Chainbase Developer Relations Director Zhengxue Dai: My perspective might differ from others. I believe the winter has not yet arrived. We are currently facing a global recession and a structural decline in the domestic population, leading many to reduce their investments in the primary market due to a lack of consumer momentum. Additionally, we can see that the number of developers is still increasing. Jokingly, I might say that the true winter of the industry will only come when I want to leave it myself. We will focus on the number of on-chain developers and the number of contract deployments. From the current numbers, there has been a significant decrease compared to last year, and most public chains are trying to hoard developers. Although Layer2 has a very high TVL, the vast majority are just users looking to exploit incentives and have not contributed to the ecosystem. So I would like to throw out a question: where do you think the current developers are?
BlockSec Co-founder YaJin Zhou: Where are the Web3 developers? We have been pondering this question because our service targets are mainly project parties. This is essentially a chicken-and-egg problem; the projects developed by developers are fundamentally for users. There are users only when there is demand, and there are projects only when there is demand, which in turn leads to developers. Before there are particularly good Web3 application scenarios, it is unrealistic for a large number of users to flood into Web3.
So the question returns to how to bring more users in. We need to consider what needs Web3 is addressing for users and what kind of applications can attract users in the context of the bear market. I am relatively optimistic about this issue. By leveraging the current market conditions, we can eliminate some poor projects. For example, with the continuous failures of centralized exchanges, more funds have flowed into decentralized exchanges. This process places us all in a stage of accumulation and development, and only after some sedimentation can better products emerge.

Image source: live shooting
Dark Jungle and Bright Knights
According to the latest statistics from SlowMist Hacked.slowmist, from January 2012 to July 14, 2023, the total amount of losses in the blockchain field due to hacker attacks has exceeded $30 billion, with a total of 1,108 hacking incidents!
Regardless of our identity in Web3, we cannot escape the constraints of the dark jungle law. Compared to Web2, the decentralized Web3 network has, to some extent, lost some security. Similar to how Ethereum Layer2 provides scalability, Web3 also needs bright knights to enhance the network's security.
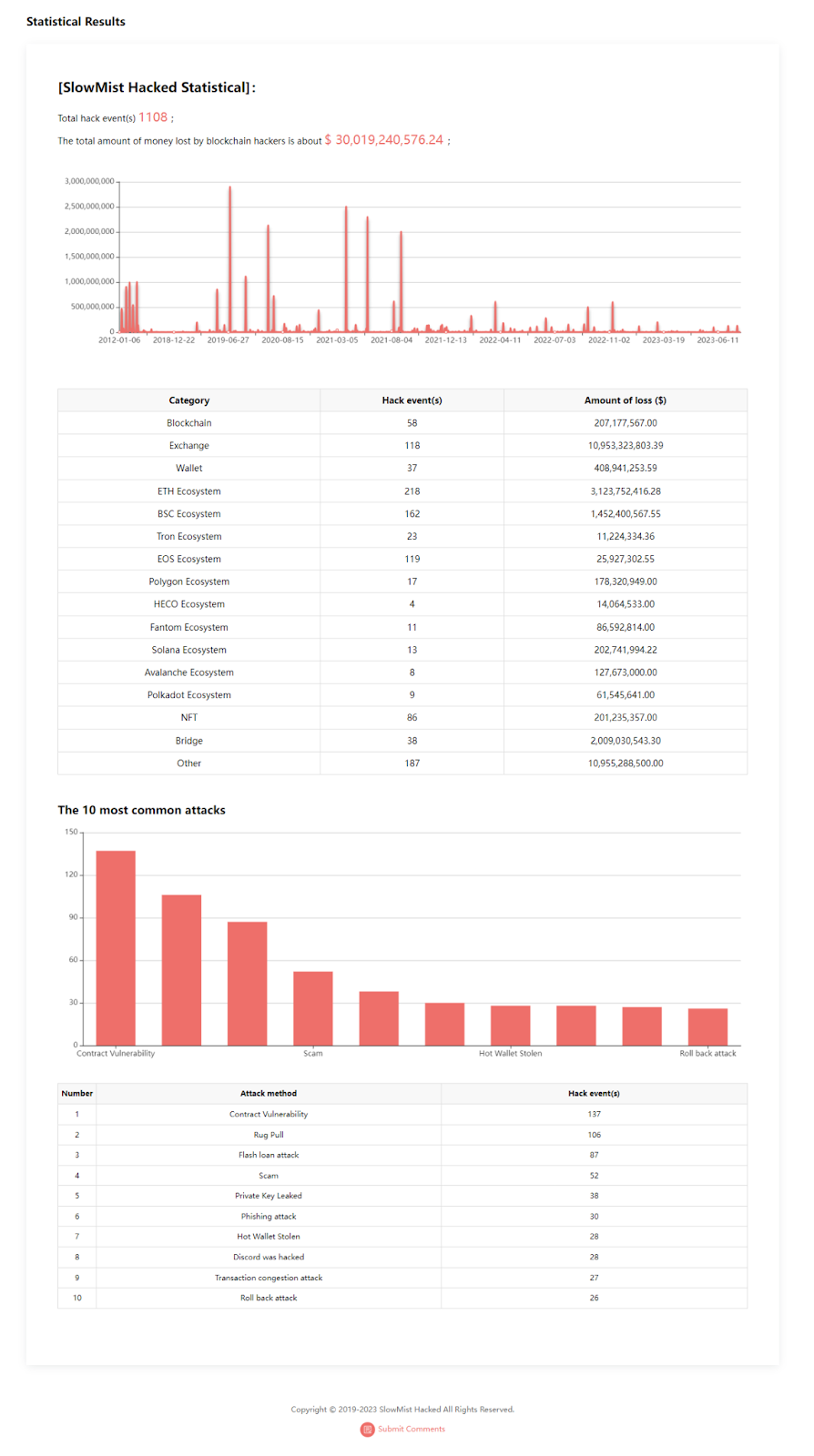
Data source: SlowMist official website
Guardians of User and Project Security
The biggest pain point in the current industry is security. Among the many types of asset theft, user wallets, project parties, and cross-chain bridges are the three types most susceptible to hacker attacks. To reduce the occurrence of such attacks, YBB Capital invited contract security audit project BlockSec and decentralized signature cross-chain bridge solution Bool Network to share their security solutions with the guests at the event.
Image source: BlockSec official
BlockSec is a blockchain security service team that provides security solutions for blockchain developers. BlockSec can offer full lifecycle security services for projects, from pre-deployment (e.g., code audits) to post-deployment (e.g., monitoring and blocking). BlockSec's security monitoring and attack blocking technologies have gained widespread recognition in the community and have collaborated with many mainstream project parties, including a recent partnership with Compound to develop an attack monitoring system for Compound V3 contracts. BlockSec is committed to providing security infrastructure for the community and has launched a series of security products and tools, including the blockchain development testing and monitoring blocking suite Phalcon, the security toolbox for Web3 users MetaDock, and the cross-chain fund flow tracking platform MetaSleuth.
Supplementing Security Beyond Code Audits
Development Testing and Monitoring Blocking Suite for Project Parties: Phalcon (Phalcon.xyz)
Phalcon is a security development, testing, and monitoring blocking suite developed by BlockSec for crypto project parties. BlockSec believes that relying solely on code audits cannot solve Web3 security issues. On one hand, high-quality audit services are scarce and cannot meet the needs of so many project parties. On the other hand, as attack methods continue to evolve, projects may face new risks after going live. After a series of practical exercises and product explorations, Phalcon was born, aiming to bring a new security paradigm to Web3.
Phalcon includes three core modules:
1) Phalcon Explorer: A powerful blockchain transaction explorer that provides transaction analysis, simulation execution, debugging, and other functions;
2) Phalcon Fork: A secure testing platform that can be deployed in a private environment, consistent with the mainnet state, embedded with a security tool suite to help project parties conduct initial security screenings, while supporting team collaboration and project public testing;
3) Phalcon Block: A proactive threat defense system that offers monitoring, alerts, and the exclusive ability to block (pause or front-run) hacker attacks. It is reported that BlockSec has successfully intercepted attacks and recovered over $14 million, making it the only security company in the industry with successful practical cases in proactive defense.
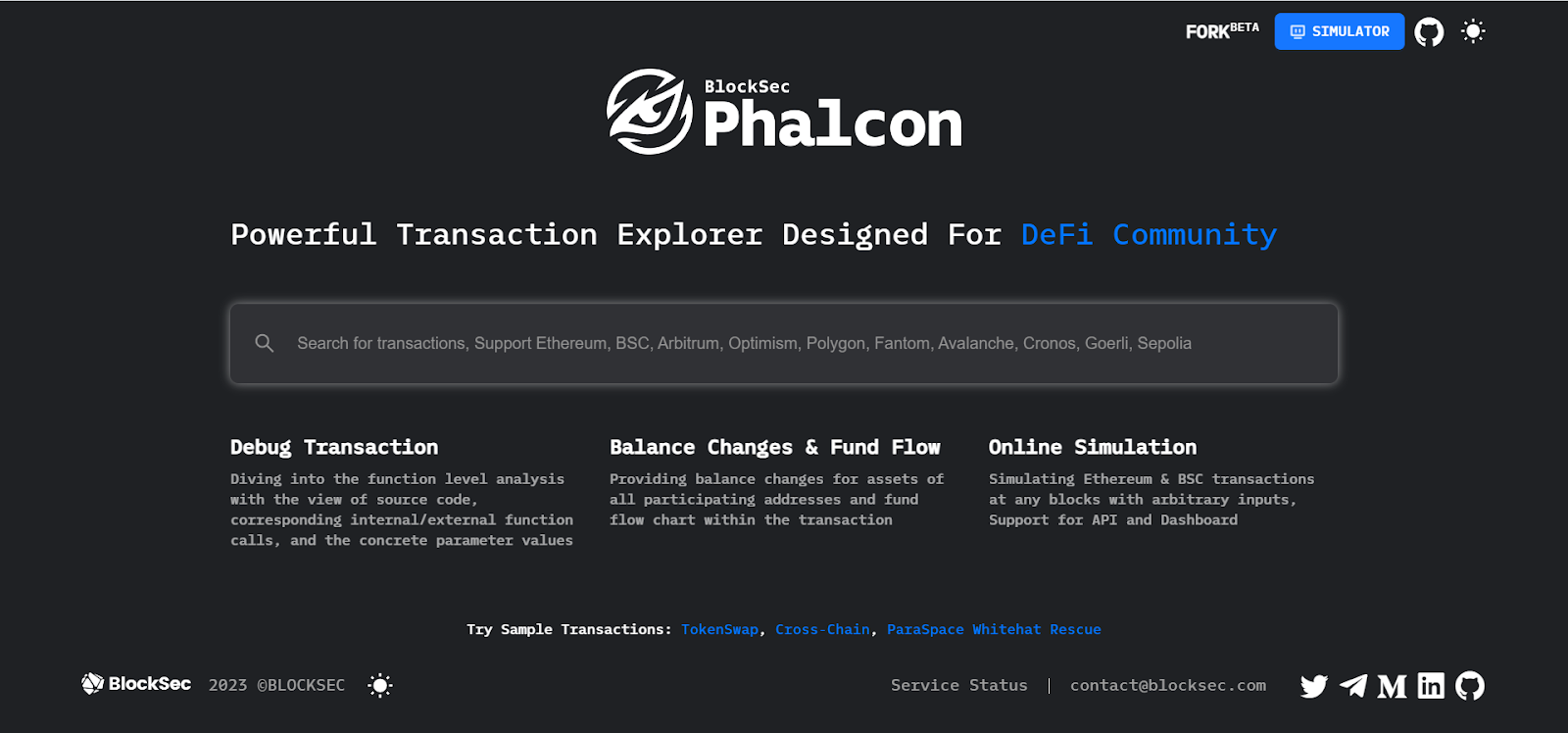
Image source: Phalcon official website
Security Toolbox for Web3 Users: MetaDock (blocksec.com/metadock)
MetaDock is a completely free, open-source, ad-free browser extension that provides extended functionality for blockchain explorers like Etherscan. Through innovative product design, it seamlessly integrates shortcuts for over ten practical product functions, making it a highly efficient tool for every security researcher, data analyst, and crypto user. This product helps users quickly understand transaction implications through its embedded GPT functionality, view fund flows for addresses with one click, assess the risks of NFT collections, and provide clearer labels and ratings for contract addresses. It has received five-star reviews and featured recommendations from both Google Chrome and Firefox.
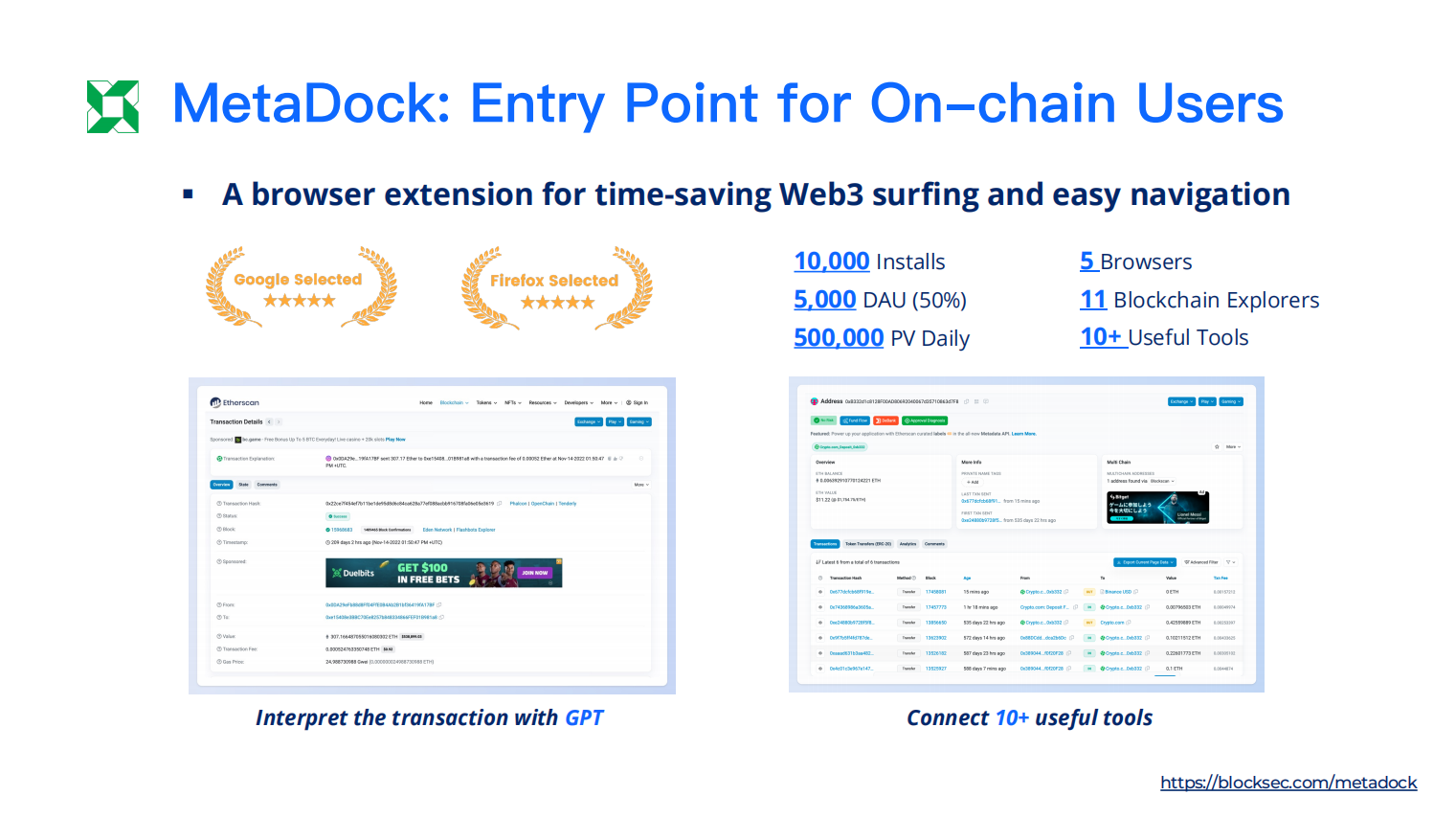
Image source: MetaDock official website
Cross-Chain Fund Flow Tracking Platform: MetaSleuth (metasleuth.io)
MetaSleuth is a visual analysis platform for cross-chain crypto assets. By inputting the wallet address to be queried, users can visualize the on-chain asset transfer dynamics related to that address. It is currently a frequently used tool among "on-chain detectives" and can comprehensively monitor the flow of funds on-chain, having integrated ten chains.
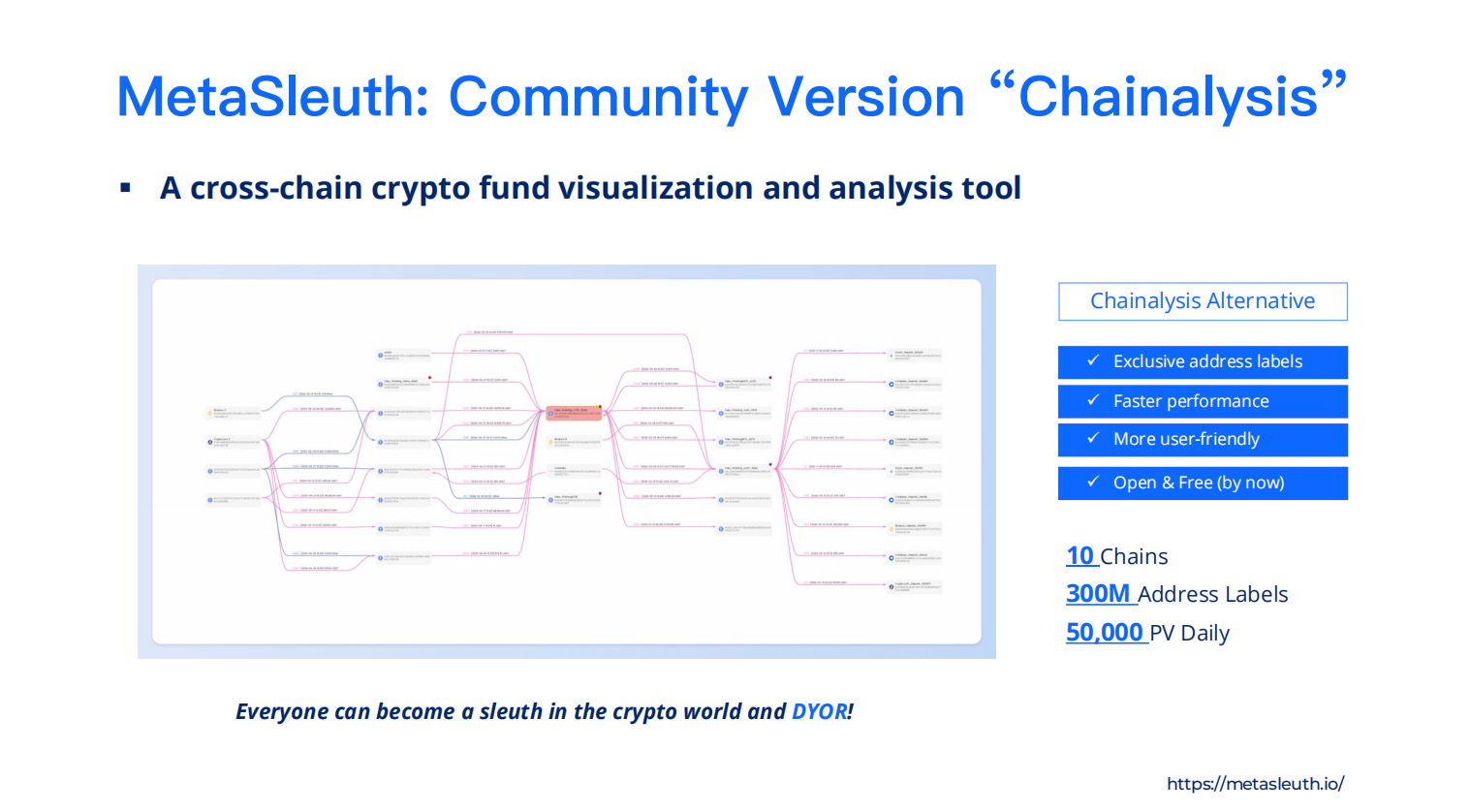
Image source: MetaSleuth official website
A New Solution to Address Another Disaster Area of Hacker Attacks—Cross-Chain
Bool Network is a decentralized signature network based on Multi-Party Computation (MPC), Zero-Knowledge Proof (ZKP), and Trusted Execution Environment (TEE) that is permissionless, completely trustless, and highly scalable. This network can serve all-chain interoperability protocols. It proposes a decentralized signature scheme to facilitate arbitrary message transmission and digital asset transfer across heterogeneous networks.
Technical Architecture
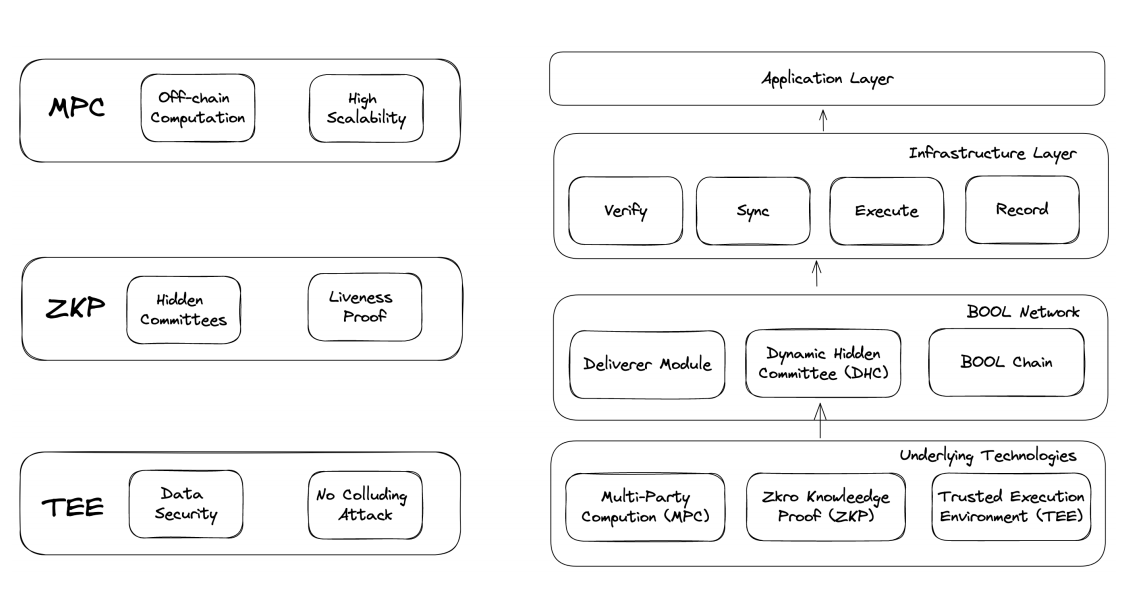
Image source: Bool Network official
The core part of cross-chain is the relayer. However, currently, secure and decentralized relayers have not been realized, so most hacker attacks in the current network are primarily cross-chain bridge attacks. This is because most cross-chain relayers are controlled in a centralized manner, fundamentally stemming from improper management and leakage of private keys. For example, traditional solutions like multi-signature or MPC are still controlled by some centralized entities and cannot fundamentally solve security issues. Bool Network adopts a solution that maintains a decentralized signature network, ensuring that private key management is not controlled by any third party, thus addressing such problems.
To this end, Bool Network introduces the important concept of a "dynamically hidden committee," where each committee manages private keys on specific blockchains to complete any form of cross-chain transactions and information transmission. It also proposes its unique Ring Verifiable Random Function (Ring VRF) election algorithm to ensure the privacy of committee member identities. Notably, all committee programs run in TEE to ensure the confidentiality and integrity of related components.
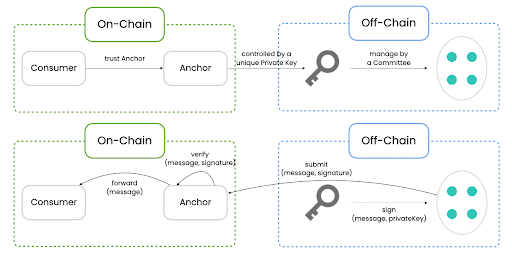
Image source: Bool Network official
MPC: Allows data holders to achieve collaborative computation and result output without mutual trust. Unlike multi-signatures, MPC (Multi-Party Computation) offers higher privacy, stronger security, better flexibility, and broader applicability.
ZKP: It provides a uniquely secure verification method, based on the Ring VRF that hides the real public key of the VRF within a ring structure, allowing its prover to demonstrate ownership of a corresponding private key to the verifier without revealing confidential information through non-interactive ZKP technology.
TEE: It is a region within the mobile device CPU that ensures the privacy and security of computations. In the Bool Network, it exists as an isolated environment, capable of storing sensitive data and providing verifiability. Verifiers can confirm that the core code and business logic running in TEE have not been modified to ensure security.
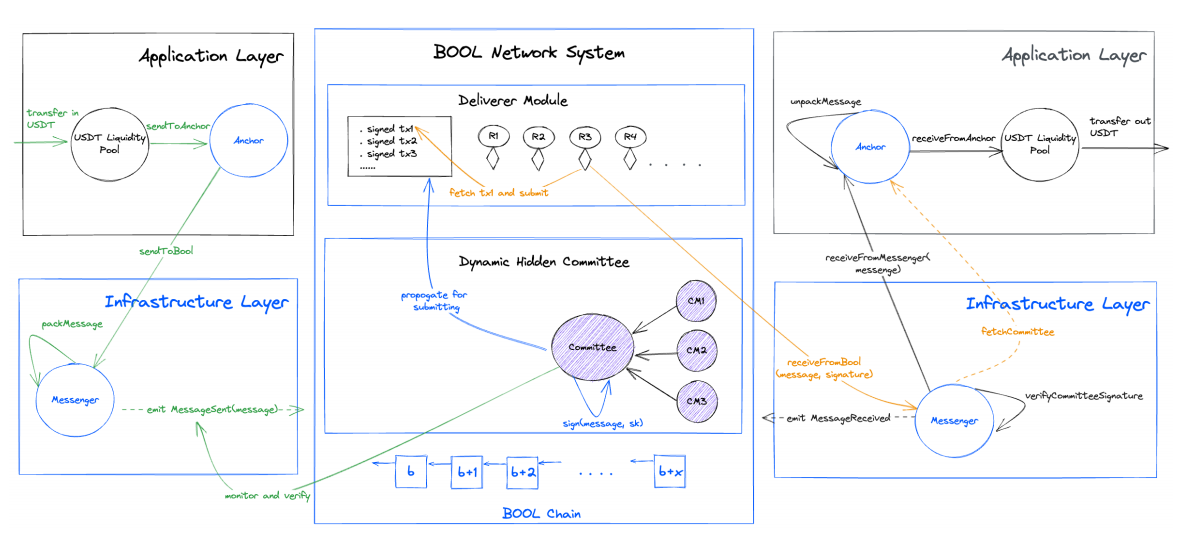
Image source: Bool Network official
In the "committee" initialization phase, we assume that 21 nodes are randomly selected from 10,000 TEE nodes. First, the private key controlled by the "committee" is divided into 21 shares through the DKG algorithm, and then the private key fragments are encrypted and stored using trusted hardware. This way, even malicious nodes cannot access the real private key fragments, fundamentally eliminating the intent to commit wrongdoing. During this process, the Ring VRF protocol is used to hide the true identities of these committee members, preventing internal collusion while also increasing the cost of external attacks. This is because external hackers need to identify the 21 hidden committee members from a total of 10,000 nodes.
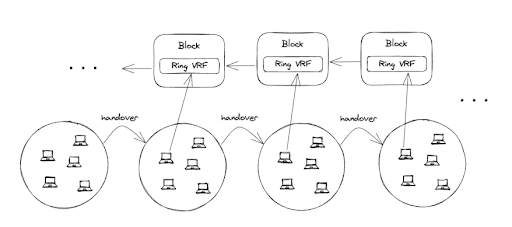
Image source: Bool Network official
Finally, through secure multi-party computation technology, data signing needs are realized based on private key fragments. Secure multi-party computation has a significant characteristic: even if some nodes go offline abnormally, signing can still be completed. Additionally, Bool defines a fixed time period known as an "epoch." For a selected group of nodes, they can only mutually control a committee within one epoch. After one epoch, their management of a committee will be handed over to a new group of nodes. This process is still facilitated by the Ring VRF algorithm to enhance the security of private key management within the committee.
Bool Network is the secure underlying infrastructure for private key management
Bool Network is the industry's infrastructure, proposed as a service to maintain the security of cross-chain communication, such as managing the private keys of terminals in DeFi bridging applications built on Bool Network. Furthermore, Bool Network is scalable to provide consensus for off-chain committees, such as oracle services operating in a more decentralized manner.
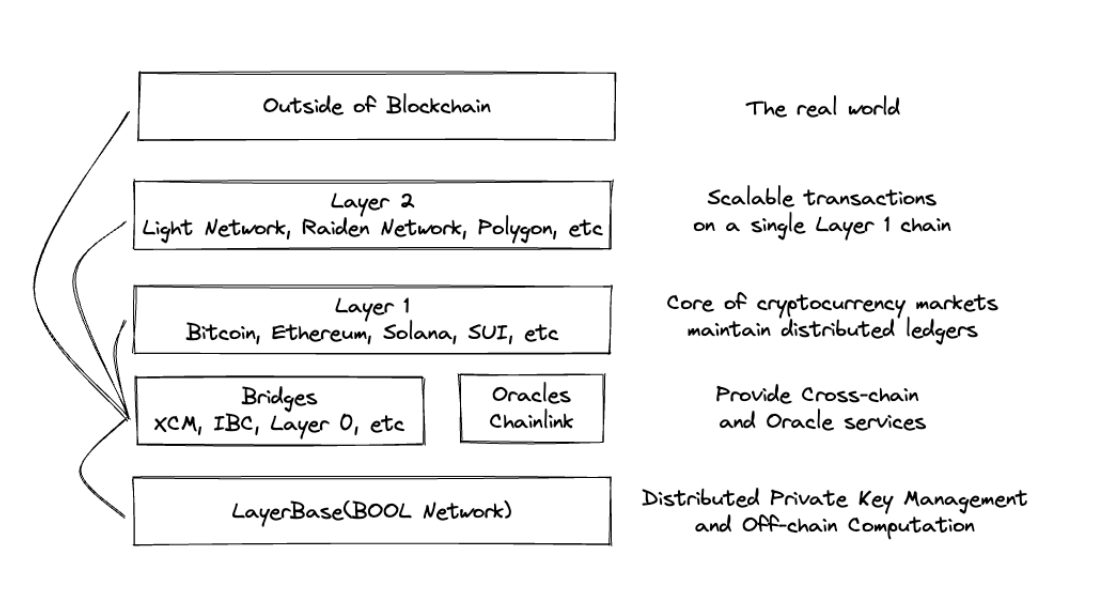
Image source: Bool Network official
In summary, what distinguishes Bool Network from other cross-chain protocols is its use of Ring VRF to achieve dynamic privacy committee management of private keys, offering complete composability for arbitrary information transmission between heterogeneous blockchains. Notably, Bool Network's academic research has been accepted by the IEEE Transactions on Information Forensics and Security (TIFS) journal. The team plans to support more blockchain networks in the future.
The product is now applicable to networks such as Bitcoin, EVM, Solana, Sui, and Filecoin. The team also plans to provide security solutions for wallet and asset management platforms. By the fourth quarter of 2023, it is expected that over 1,000 nodes will be running in Bool Network; the more nodes supported, the stronger the network's security and decentralization.
Accelerating Developer Efficiency with RPC Services
Technically, blockchain nodes are high-performance computers or servers connected to each other in a decentralized network, responsible for storing and updating blockchain data. In simpler terms, blockchain protocols like Ethereum's EVM and Bitcoin's protocol mean that when you run EVM on your computer, you are a node, but there are various types of nodes.
RPC (Remote Procedure Calls) refers to a protocol for remote procedure calls. RPC services run blockchain node clients on servers and provide HTTP or WebSocket interfaces through DNS domain name resolution.
Image source: BlockPI official website
Technical Architecture:
BlockPI Network is a blockchain infrastructure project, and its technical architecture consists of five parts: BlockPI Hub, HyperNode, Gateway, FisherMan, and Validator. These five components complement each other to form a complete network for BlockPI Network.
1) BlockPI Hub
BlockPI Hub is a collection that integrates multiple functions, including user management systems, node ratings, validator systems, and account systems. Additionally, user registration information, account information, and KYC information are stored here. It also continuously tests nodes in the network, which serves as a reference data source for BlockPI's load balancer. The income and expenditure of the entire network, as well as the distribution of rewards to roles within the system, are all completed in the Hub, which plays a significant role in the entire system.
2) Gateway
The Gateway is responsible for collecting and classifying user requests, which are routed to the appropriate HyperNode by the BlockPI load balancer. The load balancer in the Gateway evaluates the health status of backend HyperNode nodes in real-time and allocates workloads to keep the entire network in an optimal service state.
3) HyperNode
HyperNode is the terminal node that processes RPC requests and sends responses to users via the Gateway. HyperNode typically runs alongside the full node of the target blockchain (the target of RPC requests). During the testing phase, the official opened HyperNode to third-party operators to run nodes, validating the decentralized architecture. It currently supports twenty-four blockchain networks.
4) Validator
Validators are independently existing blockchain nodes that act as "police" to monitor the entire network. Using verifiable random algorithms, Validators verify workload data from HyperNode and Gateway and write the results to the blockchain. Through consensus protocols, this data is also verified and recorded by other Validators, serving the purpose of mutual recording and verification.
5) FisherMan
FisherMan is another role responsible for network security, similar to Validator, serving as a special role. It disguises itself as Gateway and User to send RPC requests to HyperNodes and Gateways and compares the results, reporting any discrepancies.
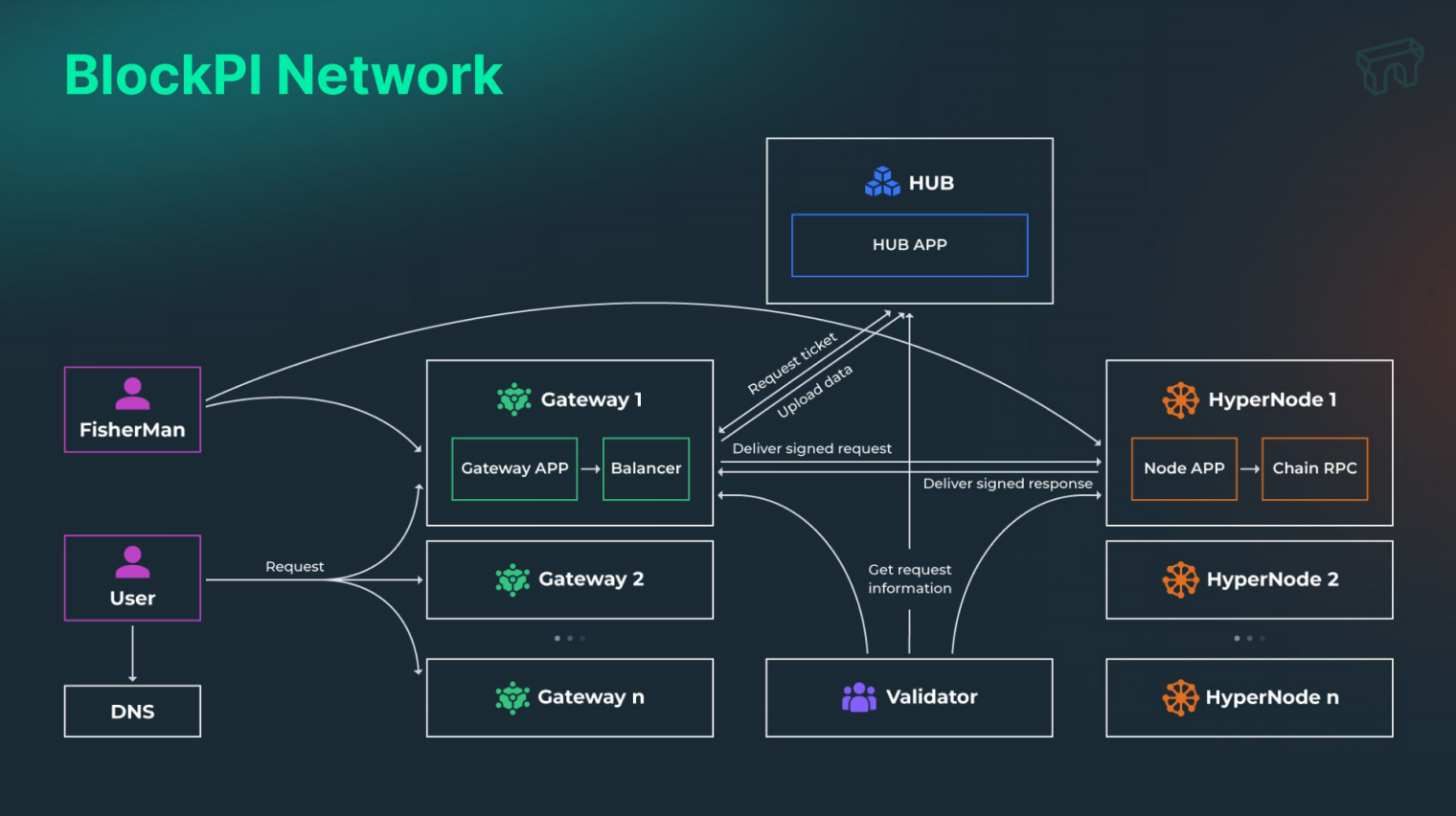
Image source: BlockPI official website
Winter and Outlook
Since its inception, the blockchain industry has continuously attracted new members with its unique charm. Regardless of how we participate, we ultimately move forward with a belief-driven mindset. Although the industry is still in its early development stage, with many technical gaps, we firmly believe that if the internet is to change the world again in the future, blockchain technology will undoubtedly take the lead.
Whether we are currently in a winter or a summer, the development of the industry relies on the construction and innovation of every developer. YBB Capital always adheres to a value investment logic centered on technological development, continuously providing financing assistance to outstanding projects. We believe that the development of blockchain needs to rely on continuous breakthroughs in its own technology to create a larger and more complete market environment. Finally, we are very honored to work with all the excellent developers and builders to "add bricks and tiles" to the blockchain cause, relying on technological innovation to solve market demand challenges. Whether we are developers or investors, we are all pioneers at the forefront of the times. Finally, we sincerely thank all the guests present.



























