White Hat Disclosure: In 2021, Huobi had a large-scale leak of OTC trading information, large customer information, client information, internal technical architecture, etc
Author: Aaron Phillips
Compiled by: Wu Says Blockchain (Huobi responds that no actual leak occurred, only white hat downloads)
Recently, some users received emails from white hats stating:
Hi, my name is Aaron. I am writing to inform you that some of your personal information has been exposed on the internet. I reported the issue and ensured it has been fixed. Your information is no longer online. (Editor’s note: It cannot be confirmed whether this information has been downloaded or even traded by others)
The cryptocurrency exchange Huobi accidentally leaked a "whale report" during a recent data breach. These reports contain the name, phone number, address, and email address you provided when registering with Huobi. They also include wallet balances and information about your assets.
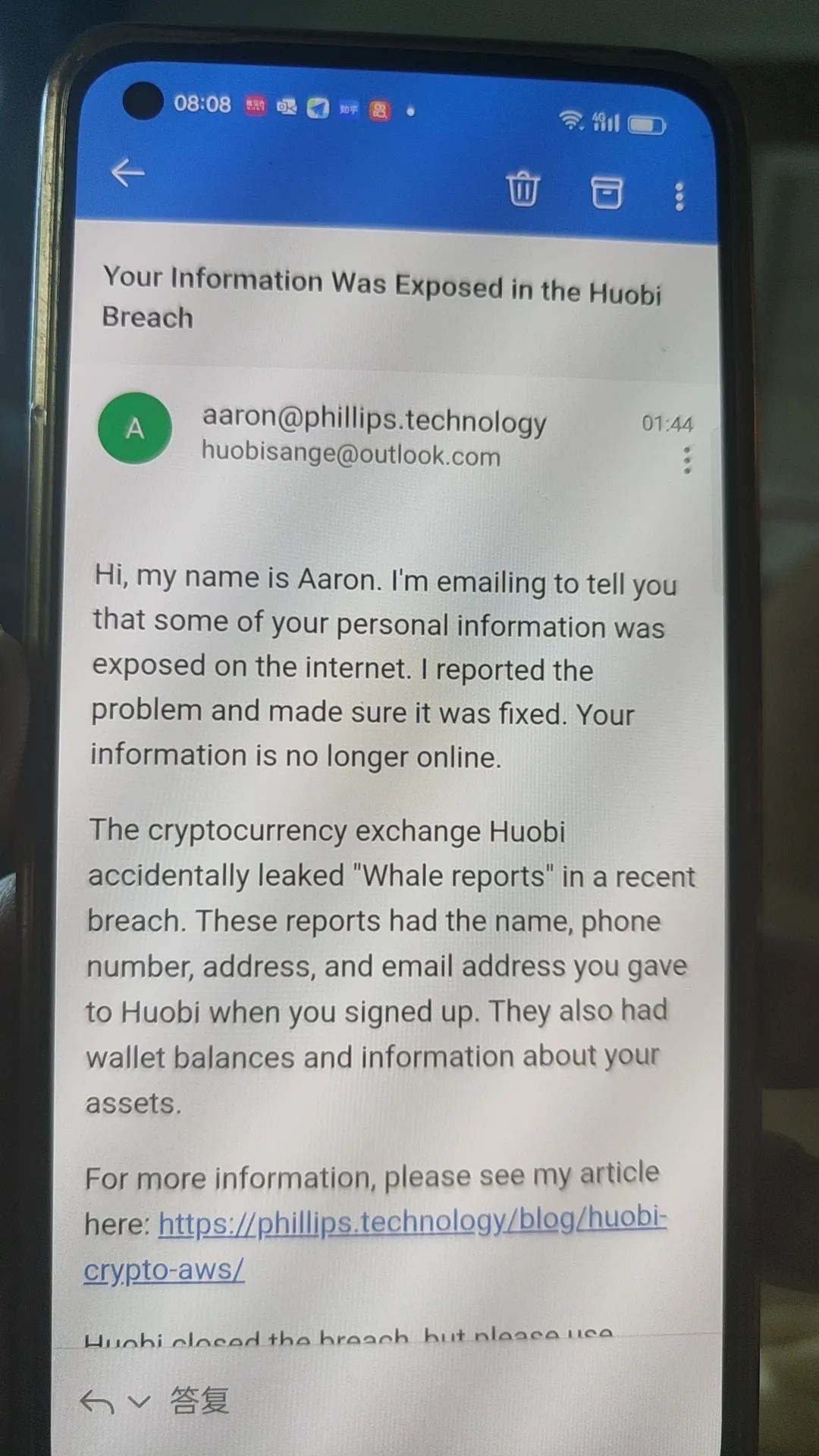
The original text is as follows, and the article has been confirmed by Slow Fog as "responsible disclosure by white hats":
https://phillips.technology/blog/huobi-crypto-aws/
phillips.technology is the personal website of white hat hacker, citizen journalist, and consumer advocate Aaron Phillips. Aaron Phillips is a U.S. professional with 4 years of experience in cybersecurity and 20 years in IT. His work primarily focuses on protecting consumers from data breaches and security vulnerabilities, and his contributions have been reported on some of the world's most popular tech news sites. His areas of focus include mobile and web application security, cloud security, and network penetration testing.
Huobi's response:
The incident occurred on June 22, 2021, due to improper operations by personnel related to the testing environment S3 bucket on the Japanese site, and the relevant user information was completely isolated by October 8, 2022. After the white hat team discovered this incident, the Huobi security team took immediate action on June 21, 2023 (10 days ago), promptly closing access to the relevant files. The current vulnerability has been fixed, and all related user information has been deleted. Thanks to the white hat team for their contributions to Huobi's security.
The full text is as follows:
Huobi quietly fixed a data breach that could have allowed access to the company's cloud storage. Huobi inadvertently shared a set of credentials that granted write access to all of its Amazon Web Services S3 buckets.
The company uses S3 buckets to host its CDN and website. Anyone could use these credentials to modify content on domains such as huobi.com and hbfile.net. The leak of Huobi's credentials also exposed user data and internal files.
An attacker exploiting Huobi's mistake would have had the opportunity to carry out the largest cryptocurrency theft in history.
If Huobi had not taken action, this vulnerability could have been used to steal user accounts and assets. The company deleted the affected accounts, and its users are no longer at risk.
While checking open Amazon Web Services (AWS) S3 buckets, I discovered a sensitive file containing AWS credentials. After some investigation, I found that the credentials were legitimate and that the account belonged to Huobi.
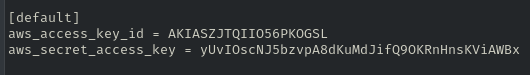
Although Huobi deleted the accounts exposed in the leak, the company has not removed the file. These credentials are still available online for anyone to download:
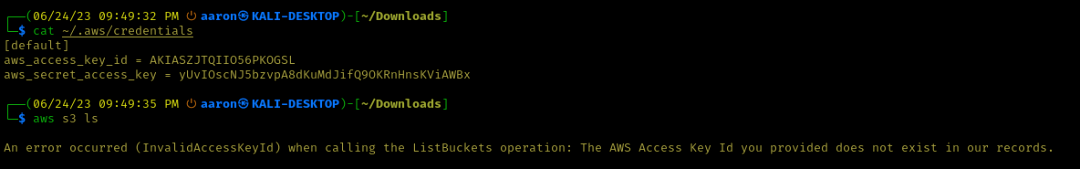
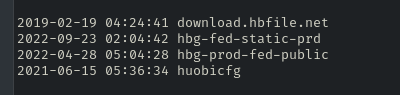
According to the metadata assigned by Amazon, Huobi accidentally released this file in June 2021.
This means the company had been sharing production AWS credentials for about two years.
Anyone who downloaded the credentials could have full access to Huobi's cloud storage. I was able to upload and delete files in all of Huobi's S3 buckets. This is particularly dangerous because Huobi makes extensive use of these buckets.
These credentials could be used to modify and control many of Huobi's domain names. An attacker could exploit Huobi's infrastructure to steal user accounts and assets, spread malware, and infect mobile devices.
There is no indication that anyone has exploited this vulnerability to attack Huobi.
Write access to critical S3 buckets
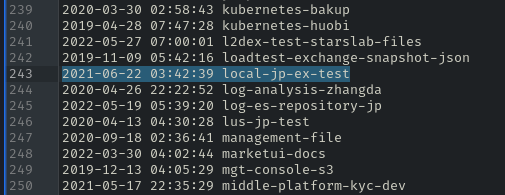
To assess the impact of this breach, I first listed everything that could be listed. I found a total of 315, many of which were private.
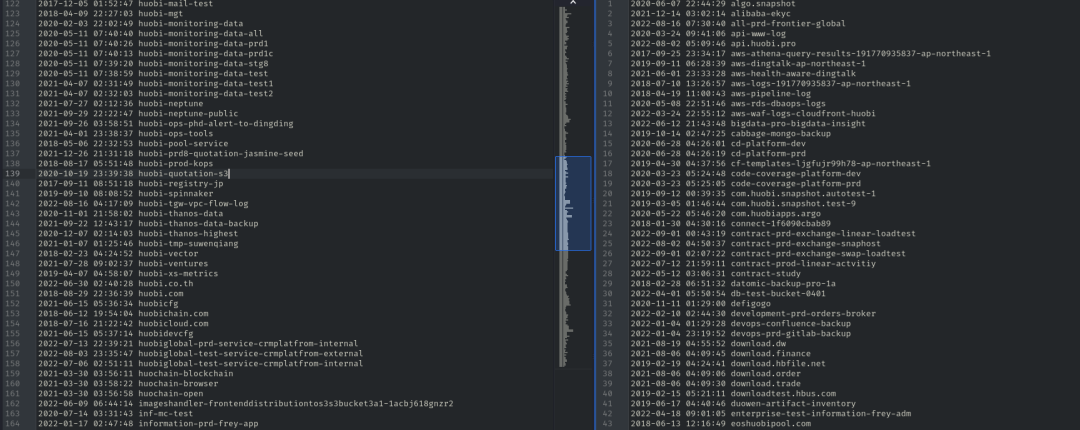
Some of these buckets share names with websites and CDNs operated by Huobi. For example, there is a CDN that hosts content used by many Huobi websites and applications.
Next, I attempted to write to the buckets. I was able to write and delete files in all 315 buckets. In the screenshot below, I uploaded a file to the CDN that Huobi uses to store and distribute its Android applications.
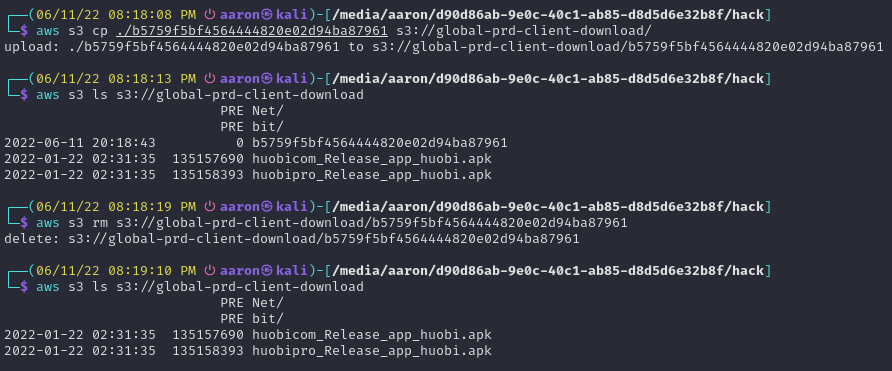
Malicious users could upload modified versions of Huobi's Android application.
Amazon uses IAM roles to control access to its cloud services. For a large company like Huobi, it is not uncommon to create a single role to manage its cloud storage. However, this approach is a poor one.
Sharing a single role among multiple teams can provide attackers with extensive access. In this case, I could read confidential reports, download database backups, and modify content on the CDN and website. I had complete control over nearly every aspect of Huobi's business data.
Arguably, the most dangerous aspect of this breach is that it granted write access to Huobi's CDN and website. The company spends significant resources testing to ensure that black hat hackers cannot gain write access to that infrastructure. It is frustrating that Huobi would leak the same access.
Once an attacker can write to the CDN, it becomes easy to find opportunities to inject malicious scripts. Once the CDN is compromised, all websites linked to it may also be at risk. Take Huobi's login portal as an example.
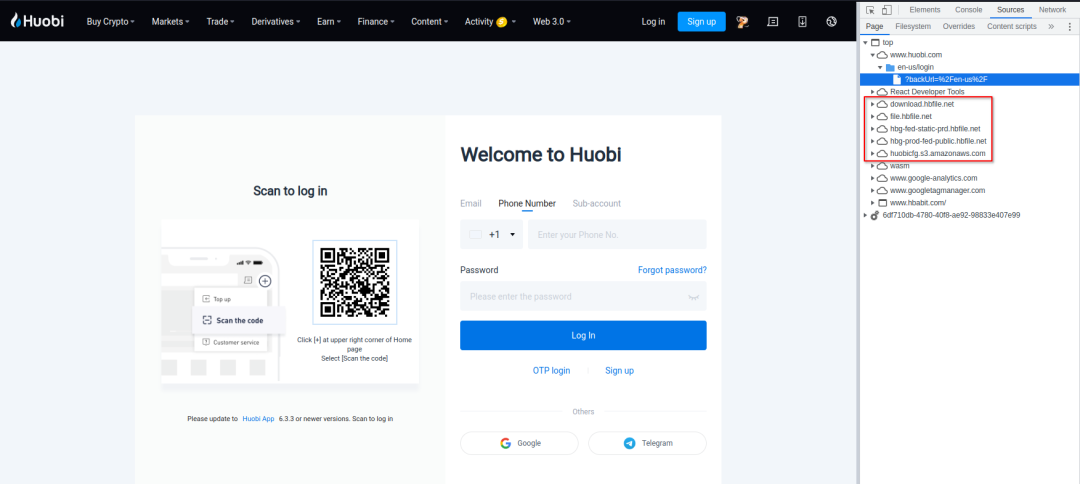
Huobi's U.S. login page loads resources from at least five different CDNs. Let's focus on the part highlighted in red above. One of these five is clearly a bucket, huobicfg.s3.amazonaws.com, as the URL contains the string "s3.amazonaws.com".
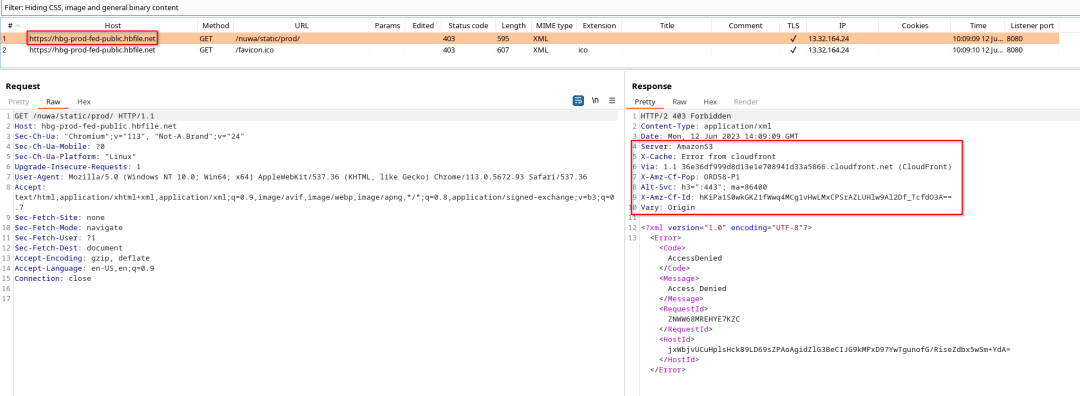
But the other four also correspond to compromised buckets. I was able to get Cloudfront to generate detailed response headers for invalid requests. The headers showed that some content from the hbfile.net domain was served by Cloudfront via AmazonS3.
In this case, Cloudfront acts as a middleman, redirecting hbfile.com requests to the S3 bucket. I found four of the five CDNs in the list of compromised buckets.
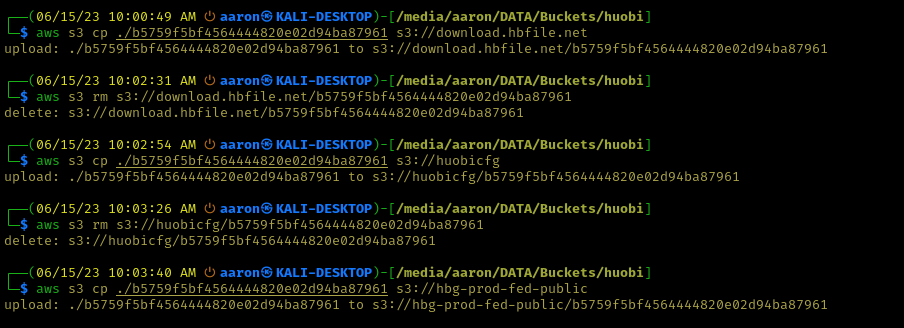
I could write and delete files on all CDNs.
In general, it is difficult for consumers to detect compromised CDNs and websites. From the user's perspective, they are accessing a trusted site. Users cannot determine whether the files stored on the CDN have been altered.
For anti-malware, certain malicious scripts may be allowed to run because they are served from the correct source. For black hat hackers, compromising a CDN is one of the most effective ways to inject code or malware into a website.
Huobi makes it easy for malicious users to take over their CDN and website. To my knowledge, every login page operated by the company is affected by this vulnerability.
For two years, every user logging into Huobi's website or application may have faced the risk of losing their account.
This breach also raises privacy concerns. Using the leaked credentials from Huobi, I was able to access customer relationship management (CRM) reports containing user information.
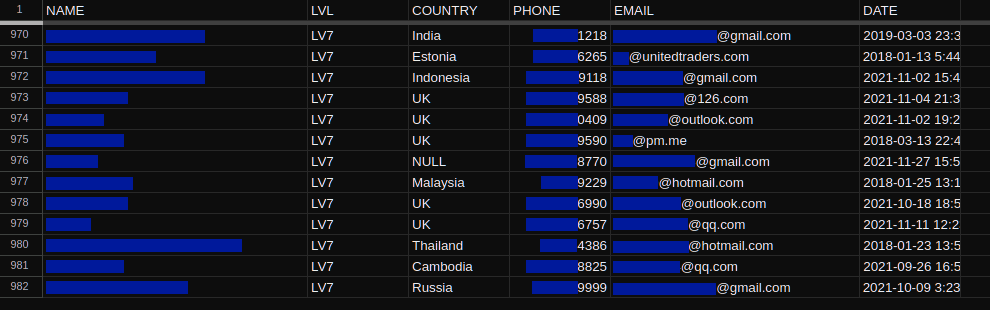
The reports I found included contact information and account balances for "crypto whales." Whales are wealthy users with large amounts of cryptocurrency, and Huobi is clearly interested in building relationships with them.
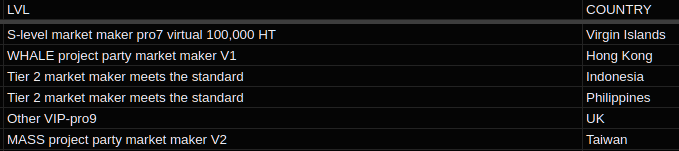
The company seems to rank these users based on their ability levels. Users with greater market influence are ranked higher.
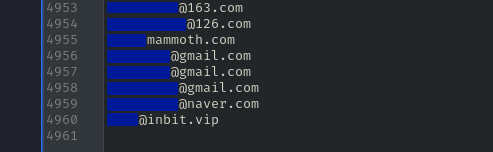
Huobi leaked contact information and account details for a total of 4,960 users.
Another set of data exposed in the Huobi leak is a database of over-the-counter (OTC) trades.
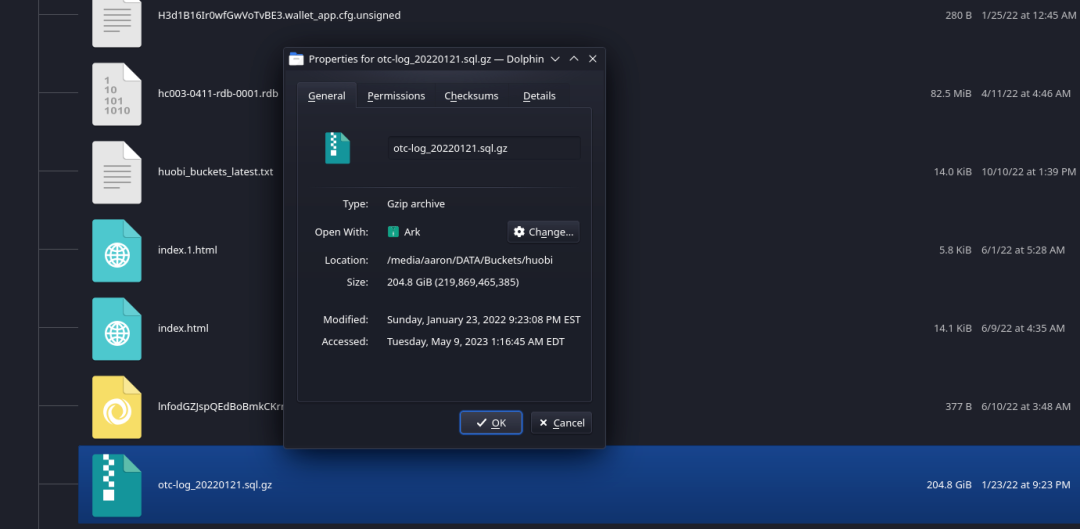
After extraction, the database backup exceeds 2TB and appears to contain every OTC transaction processed by Huobi since 2017. This may be a concern for many traders, as one of the benefits of OTC trading is increased privacy.
Below are highlights of some OTC trades. Anyone who has conducted OTC trades on Huobi since 2017 may have been affected by this data leak.
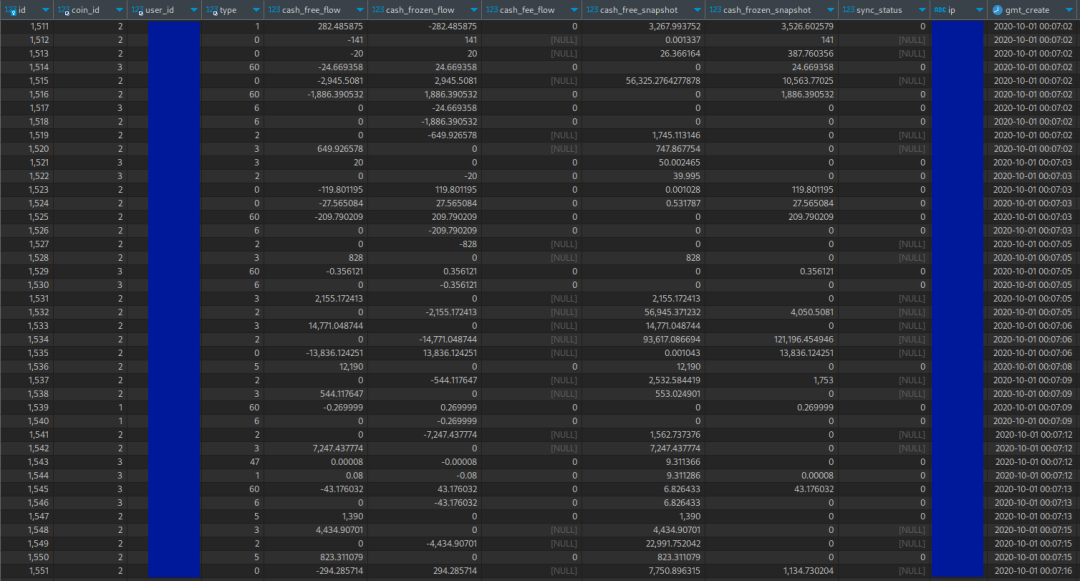
In the screenshot above, user accounts, transaction details, and traders' IP addresses can be seen. The complete database contains tens of millions of such transactions.
The database also contains some notes that give us insight into how Huobi manages its OTC trading platform behind the scenes.
The documents detail Huobi's infrastructure.
Huobi leaked information about itself. Attachments show the internal workings of its production infrastructure. Software stacks, cloud services, internal servers, and other sensitive details are listed.
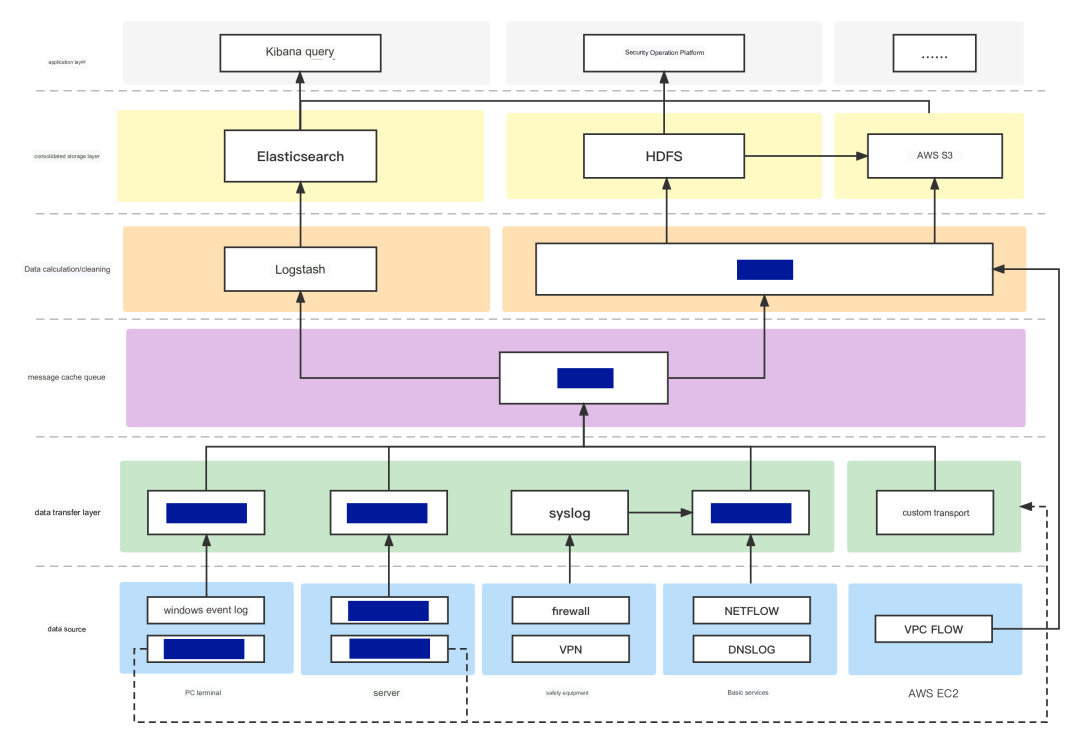
These files, like the other data leaked by Huobi, are now secure.
One of the most unique CDNs affected by Huobi's breach is the Utopo blockchain NFT. Malicious users could change JSON files on the CDN to edit NFTs.
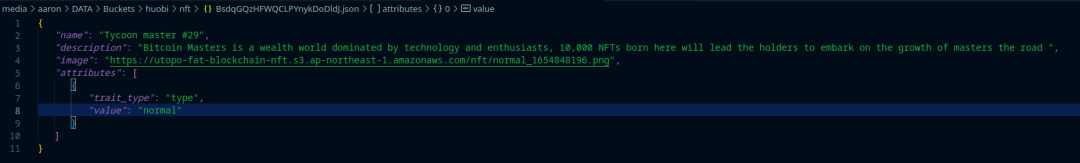
NFTs are links to JSON files on the blockchain. When JSON files are modified, they change the characteristics of the NFTs. In this case, all NFTs could be edited, although I did not make any changes.
The security risks surrounding NFTs are still being explored. In some cases, modified NFTs could be used to inject malicious code into browsers, applications, or games. There is no indication that this has occurred here.
Timeline
Here is the complete timeline of events:
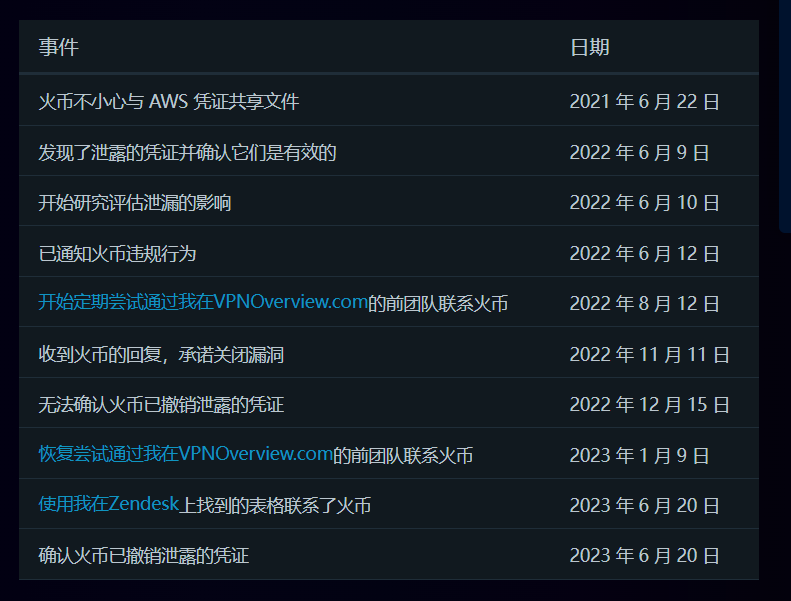
Ultimately, Huobi revoked these credentials and secured their cloud storage.
Huobi users narrowly escaped disaster.
Unfortunately, in this case, I cannot conclude that Huobi has done a good job. Leaking their Amazon credentials is bad enough, but it took months to respond, and even then, Huobi chose to leave the credentials online.











