Attack Vulnerabilities in DAO Governance: Technical, Economic, and Social Aspects
Author: Chandler
Compiled by: DAOctor@DAOrayaki.org
TLDR: Governance risks can arise from many areas, including social, economic, or technological risks—sometimes a combination of all three. Understanding how to mitigate these risks is crucial for building governance systems for the future. Most importantly, not everything requires a vote!
Decentralized contracts have permanence. Any changes to the contract are made through a managed governance process. The governance process is inherently human-involved, making it much more complex.
This article will explore some dangers in the governance process, providing a general framework for thinking about governance risks. Generally, any effective governance process aims to prevent decisions that push a project or protocol in a direction that diverges from its mission.
Here, we outline three main categories of risks: technical, social, and economic. In addition, there are some important lessons learned from effective governance processes.
Minimizing Governance Processes
Governance systems that minimize governance actions are more robust and maintainable. The fewer changes, the better. However, protocols need upgrades.
Broad governance systems also encompass many non-protocol-specific issues, such as how much to commit to funding, which can be considered a key decision but does not fundamentally affect the protocol. A system that distinguishes between specific protocol choices and societal-level choices will reduce the overall scope of governance actions.
Autonomous organizations are inherently autonomous, and reducing their governance footprint can decrease reliance on individuals.
As we mentioned, many tools are being developed to help protocols take different approaches to governance actions with social or human coordination characteristics versus actions that affect the protocol. For example, the emergence of the Zodiac Module allows users to submit transactions and perform optimistic verification. Instead of requiring a vote for every on-chain action, transactions can be submitted, and a vote is only necessary when there is a disagreement about the nature of the transaction.
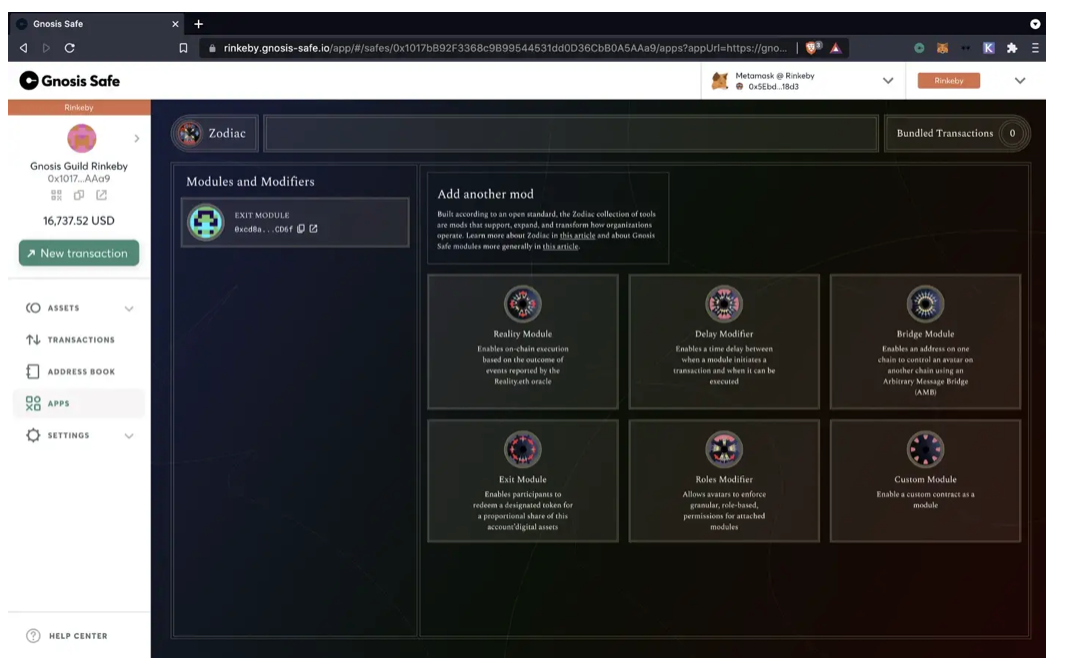
Secure multi-signature Zodiac Module
Technical Vulnerabilities
Vulnerabilities in smart contracts are a headache for many protocols, including governance protocols. Many governance contracts exist as an on-chain voting mechanism to execute a set of given instructions. As long as there is any code on-chain, technical vulnerabilities can arise.
A notable example of this risk is the $22 million Compound governance vulnerability. The Compound system had a flaw in the contract responsible for allocating liquidity mining rewards.
The only contract authorized to change the affected contract is the governor contract, meaning that only governance votes can influence changes to fix the erroneous contract.
A slow governance process hinders the ability to fix vulnerabilities and stop the flow of funds. Fortunately, for the Compound team, the response was as quick as possible, and the governance system reacted in the fastest way possible.
From another perspective, contracts execute according to the rules, including vulnerabilities. It is just that humans perceive the purpose of the contract as inconsistent with the actual coding of the contract.
Regardless of whether each of our thoughts is right or wrong, the fact remains that there is always a discrepancy between what humans think a piece of code can do and what it actually means to do. The shocking reality is that we often realize this only when it is too late.
Social Vulnerabilities
In addition to technical aspects, the social aspects of governance have their own challenges. Humans are inherently more complex than code.
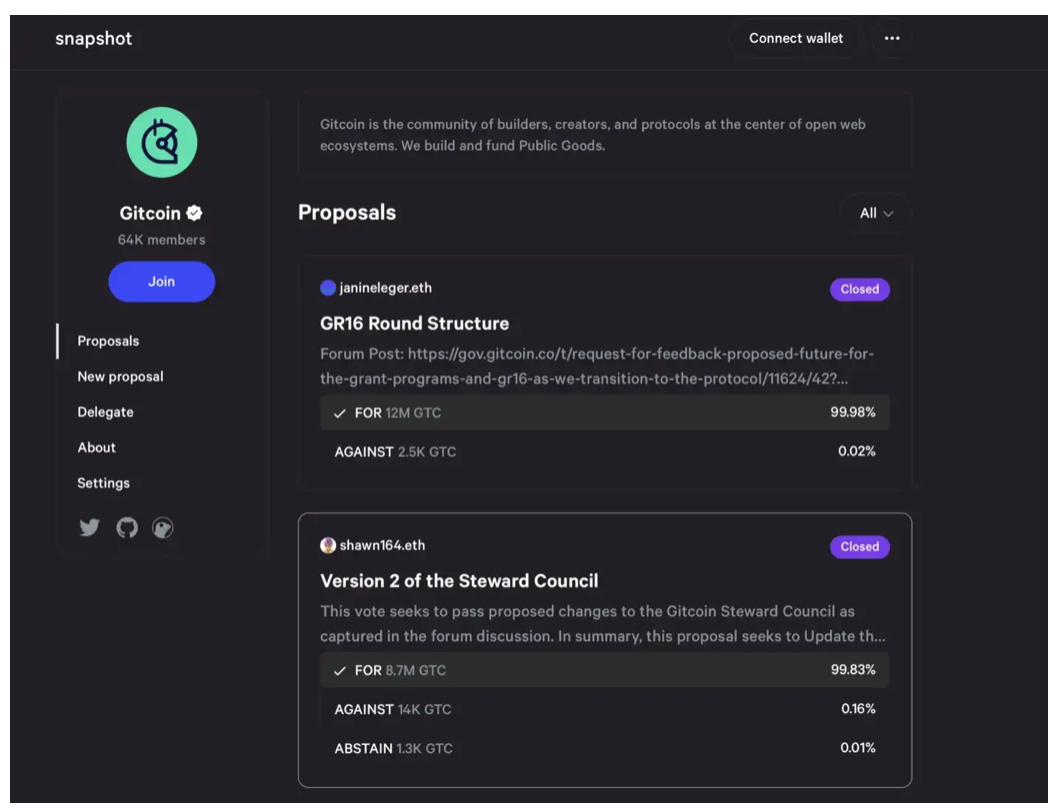
Snapshot: Off-chain voting tool
On-chain vs Off-chain Voting: As mentioned, governance actions of protocols should be minimized to the absolute basics. On-chain voting should affect on-chain contracts, while off-chain voting is designated for projects where people can reach consensus socially. I often see hundreds of on-chain votes easily reaching soft consensus. This naturally diminishes the significance of important votes compared to standard operational projects.
Mechanisms and processes of voting. While not all voting processes follow this trend, there are enough methods to be wary of. In some cases, off-chain "temperature" checks lead to on-chain votes executed by multi-signature individuals.
As a step from on-chain voting, this makes no sense. Either abandon the on-chain part and let trusted multi-signatures manage soft consensus, or let on-chain voting trigger necessary actions.
The most valuable aspect of the governance process is the attention of qualified voters: more votes lead to voter apathy and lower long-term voting rates. Ensuring that voices are meaningful, to the point, and reach a level of comprehensive voting is essential to ensure your voting results.
Quorum and how many participants are needed: As we wrote in the previous article, there is a trade-off between voter participation and the size of the organization. However, there is also a trade-off between decentralization of power and the ability of a small group of founding team members to simply overturn votes. If tokens are not sufficiently decentralized, a team can meet the quorum requirements for voting.
Expertise of voters: One of the highest governance risks is the level of expertise that voters must possess to make informed choices. In many cases, users can cheaply acquire governance tokens (e.g., airdrops, liquidation mining programs) and become eligible to vote. Voters may be uncertain about what they are voting on, leading them to either abstain or make the most popular decision based on others' inclinations. This does not lead to sufficiently decentralized and representative voting.
Economic Vulnerabilities
Economic exploitation refers to attackers deploying funds to take over the voting process. In most cases, governance is conducted through tokens that can be purchased. This means the cost of acquiring voting shares (e.g., 51%).
If we look at some theoretical numbers, a treasury would need to own at least 50% of the voting supply value of any other protocol to complete such an exploitation. Given that some treasuries are several orders of magnitude larger than others, this type of risk is not far-fetched.
Fortunately, many protocols have enough tokens locked up, while the circulating supply is insufficient, making such attacks unrealistic. However, with this token, economic attacks can unlock timelines and cycle supplies over time.
Over time, such attacks may not be economic. They could involve undermining competitors, gaining control to influence contentious votes, or even creating deadlocks.
Examples of exploiting protocols through economic attacks can be found in lesser-known protocols: True Seignorage.
The TLDR version is that an attacker bought 51% of their voting tokens due to their small market cap. After acquiring the tokens, the attacker initiated a vote to mint 11.5 quintillion tokens to their address. The vote naturally passed, and users could sell as many tokens as possible on Pancake Swap.
The profits the attacker made from the token sales exceeded the cost of acquiring the tokens through voting, while the Dev wallet did not have enough funds to stop them.
Conclusion
Governance will continue to exist, and we have a responsibility to establish a governance process that leads us into a future we all wish to enter. Understanding the risks of governance systems and how we can address these risks is an evolving process. An obvious trend is that governance systems have flaws that require thoughtful work to fulfill their promises.
Decentralized governance is still in its infancy, as is the technology behind it. As the industry matures, governance attack vectors will naturally diminish.









