The World Cup is coming, and while enjoying the "Last Battle of the Gods," one must also be wary of risk scams
Author: GoPlus Security
1. The Emerging Crypto Risks Related to the World Cup
The 2022 Qatar World Cup is approaching, and it is highly likely to be the last World Cup for stars like Messi, Ronaldo, Benzema, Modric, and Lewandowski. As the "final battle of the gods" draws near, various scams related to the World Cup on blockchain are emerging.
According to data from the GoPlus Token detection engine, over 1,000 risky tokens with "FIFA" or "World Cup" in their names have appeared in just the past week, involving more than 160,000 addresses and accumulating liquidity exceeding 5 million USD.
The list below includes some major types of risks:
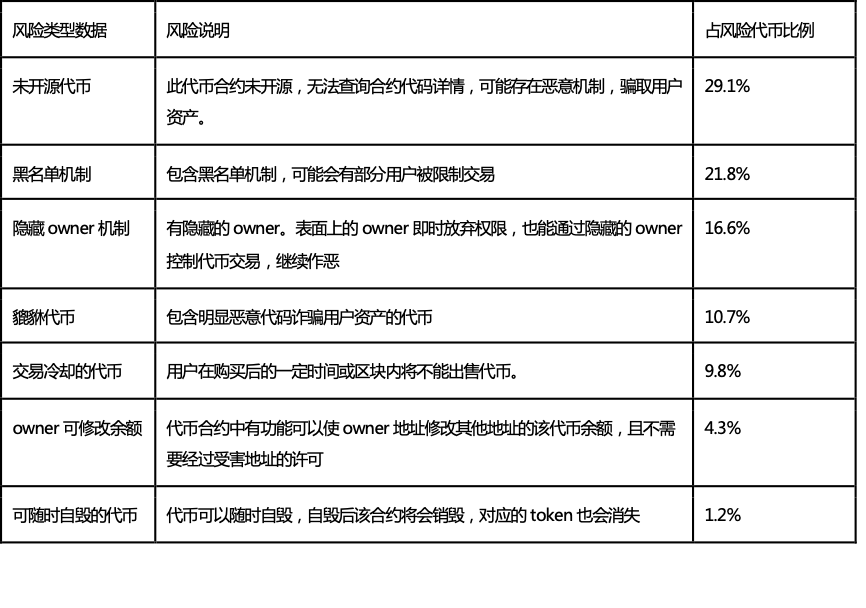
At the same time, various World Cup-related NFTs are also emerging, many of which carry serious risks. Therefore, amidst the World Cup festivities, we must not let our guard down regarding various opportunistic token/NFT projects. It is essential to use convenient security detection tools to protect our crypto assets.
2. Introduction to Token Risks Users May Encounter
Token risks are diverse and may concentrate during the World Cup. Here are a few major and very serious risks.
1. Malicious Tokens
These are tokens that contain explicit malicious code in the contract, preventing users from trading or resulting in asset loss.
For example, the following token (BSC chain, 0xaf25a7336f4984976febc5c0bca62caeb57b4a97) contains malicious code.
As shown in the image above, all related functions in the contract code are implemented through external contracts, meaning that the balances of all holders are stored in an external contract. This means that as long as this external contract is replaced with a new one, all holders' balances will be directly cleared. This is a serious risk due to malicious code.
2. Self-Destructible Tokens
A self-destructible contract can be destroyed, and once destroyed, the contract no longer exists, along with the corresponding assets. In simple terms, if the contract is gone, the corresponding token is also gone, and the user's assets will directly disappear. Moreover, monitoring shows that tokens containing self-destruct functions generally end up activating this function.
For example, the following token (Ethereum, 0xc1f5ba8bab3ca299f9817876a6715627f9e2b11a) has a self-destruct function.
As shown in the image above, once the "kill" function in its code is activated, the contract will self-destruct, and its token will disappear.
3. Owner Can Modify Balances
This means that the token contract has a function that allows the owner address to modify the token balance of other addresses without the permission of the affected address.
For example, the following token (BSC chain, 0xf3f064ed4848345dd7505915c3d43c238831f1a2) has this issue, where its owner address can modify the balances of other addresses.
The problematic code is shown in the image above, where the owner address can directly allocate tokens from "address from" to the addresses in "address[]", without needing the user's permission.
3. Introduction to NFT Risks
In addition to tokens, NFTs also carry various security risks. According to data from relevant security agencies, many NFTs have certain security vulnerabilities at the contract level (the list includes several common and serious NFT risks):
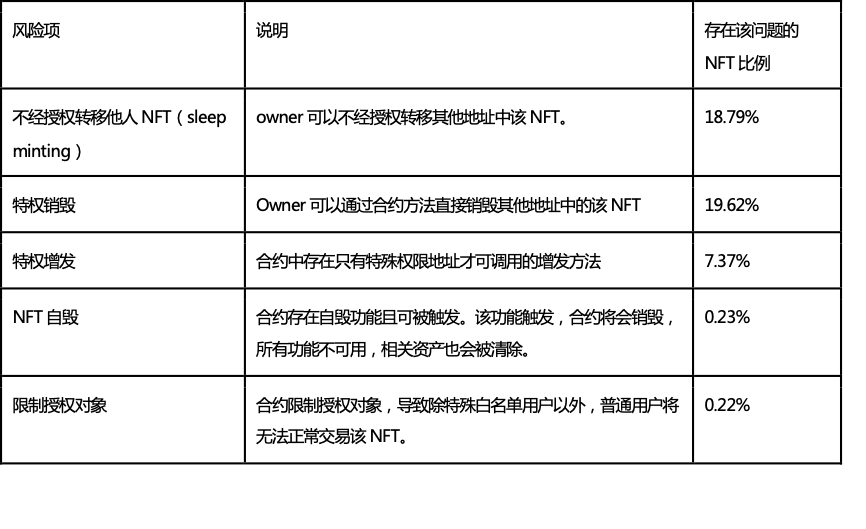
Moreover, NFTs are easy to forge, which may lead to a rapid increase in World Cup NFT scams.
Here are a few very serious NFT contract risks.
1. Restricted Authorization Leading to Inability to Trade
This generally refers to addresses outside the whitelist being unable to authorize the contract. Since decentralized NFT trading platforms require contract authorization, this means users will be unable to trade the NFT on decentralized exchanges.
This scam typically involves the project team first allowing whitelisted addresses to inflate data, leading users to see normal trading data for the NFT on trading platforms, mistakenly believing it can be traded. However, when users buy and then try to sell, they find they cannot trade.
In the above case, the NFT contract code contains a requirement that the authorized object cannot be a contract, and since listing on OpenSea requires authorization to OpenSea's contract, this NFT cannot be listed.
The code is shown in the image below.
In the image above, only addresses in the _addressTransferToContract list can successfully authorize (i.e., only addresses in the whitelist can authorize), and addresses not in this list will fail to authorize the contract.
2. Unauthorized Transfers
This means that the owner of the NFT can directly transfer the NFT from other addresses to a designated address without authorization.
This malicious tactic generally has two forms of use:
(1) Direct Transfer After Selling the NFT
As shown in the image below, after selling this NFT (Ethereum, 0xa9bcd4bd5b851479307fe71398ce2352c281e0c1), it is directly transferred away.
The reason this scam can occur is that the contract code sets an address that has authorization for all NFTs. Therefore, this address can directly transfer the NFT from other addresses at any time. As shown in the image below:
(2) Forging Celebrity Ownership and Transfer of the NFT, Giving It So-Called Celebrity Endorsement
Recently, many users have reported that some NFT projects claim that a certain influencer has endorsed them and that the influencer has traded the NFT, leading users to inquire about the project's security. In fact, this is another specific mode of "unauthorized transfer."
The main process is as follows:
First, mint the NFT to a publicly known influencer's address, with the NFT contract code containing logic for unauthorized transfers.
Then, find an appropriate opportunity to transfer the NFT from the influencer's address. This will appear on-chain as if the influencer not only holds but has also transferred the NFT (especially the transfer step is very misleading, as ordinary users may mistakenly believe the influencer has genuinely traded the NFT).
The project team can then use this to promote the so-called "influencer endorsement," thereby scamming users.
4. How Users Should Defend Against Related Risks
First, establish a preventive awareness and implement basic preventive measures based on personal circumstances.
(1) It is essential to recognize that scams related to the World Cup will only increase, and one must remain vigilant. As the World Cup progresses and related hype increases, more scams will emerge. In addition to scams related to the World Cup or FIFA, there may also be scams related to well-known players (e.g., "Messi Coin," "Ronaldo Coin") or popular events. Everyone must stay alert.
(2) Be cautious about tokens/NFTs of interest, and first understand their basic situation through official websites/community/Twitter, etc.
(3) Be careful with tokens or links recommended by others to avoid being scammed.
The above points are not complicated, but why do attackers still succeed repeatedly?
Firstly, the attack range is vast, covering a large number of users, and there will always be some who fall through the cracks; secondly, they exploit users' impatience, causing panic and not allowing users time to think; thirdly, users often lack tools for quickly detecting token/NFT scams.
Secondly, learn to use security detection tools.
For various scams in tokens/NFTs, it is necessary to use relevant detection tools to check before purchasing, to avoid risks as much as possible.
1. For Token Detection, you can use GoPlus Token Security Detection Service.
GoPlus Token Security Detection Service is one of the token detection services with the most extensive coverage, the most comprehensive detection items, and the most accurate results. Its detection service has been integrated into many well-known blockchain products such as TokenPocket, AveDex, Mask, and Bitkeep.
GoPluseco Token Security Detection Introduction Page (https://gopluseco.io/detail/49)
After opening, directly select the public chain corresponding to the token on the page and enter the address to view the detection results.
After clicking the detection button, a comprehensive security detection result will appear, including contract security, malicious token risks, holding amounts, and lock-up conditions, among dozens of security detection items.
2. For NFT Detection, you can use GoPlus NFT Security Detection Service.
GoPlus NFT Security Detection Service currently supports various major NFT security detections. Its security service has also been used by major platforms like X2Y2.
GoPluseco GoPlus NFT Introduction Page (https://gopluseco.io/detail/75)
After opening, directly select the public chain corresponding to the NFT on the page and enter the address to view the detection results.
After clicking the detection button, a comprehensive security detection result will appear, including contract security, NFT authenticity, transaction information, and dozens of other security detection items.
3. Directly search by entering the address in GoPluseco.
You can directly enter the address in GoPluseco to search, which integrates relevant detection for tokens and NFTs.
After entering the address, it will check for any malicious behavior associated with that address and provide the corresponding token/NFT detection entry.
All the above content comes from GoPluseco (https://gopluseco.io/). GoPluseco matches users with optimal security solutions by aggregating high-quality security applications or services in the industry. When encountering security-related issues, feel free to ask GoPluseco, where all questions will be answered.
Additionally, during the World Cup, GoPluseco (https://gopluseco.io/) will provide a World Cup security theme page, offering security services that can detect World Cup-related tokens, NFTs, and phishing websites to protect everyone's asset security.