Frequent hacker incidents, please accept this Crypto Theft Prevention Guide
Original Title: 《The State of Crypto Security》
Author: Kofi Kufuor
Compiled by: Katie Gu, Odaily Planet Daily
Hackers have stolen over $2 billion from crypto applications this year. During the National Day holiday, the industry experienced another crypto theft incident with the TokenPocket flash exchange service being hacked (loss exceeding $21 million) and the BNB Chain cross-chain bridge BSC Token Hub being attacked (loss of about $566 million).
As the crypto ecosystem evolves, the security arms race will only intensify. Therefore, this article will:
Propose a taxonomy of crypto security incidents;
List the most profitable attack methods for hackers to date;
Review the pros and cons of current tools used to prevent hacking;
Discuss the future of crypto security.
I. Types of Hackers
The crypto application ecosystem consists of interoperable protocols supported by smart contracts, relying on the underlying infrastructure of chains and the internet. Each layer of this stack has its unique vulnerabilities. We can classify crypto hackers based on the exploited stack layer and the methods used.
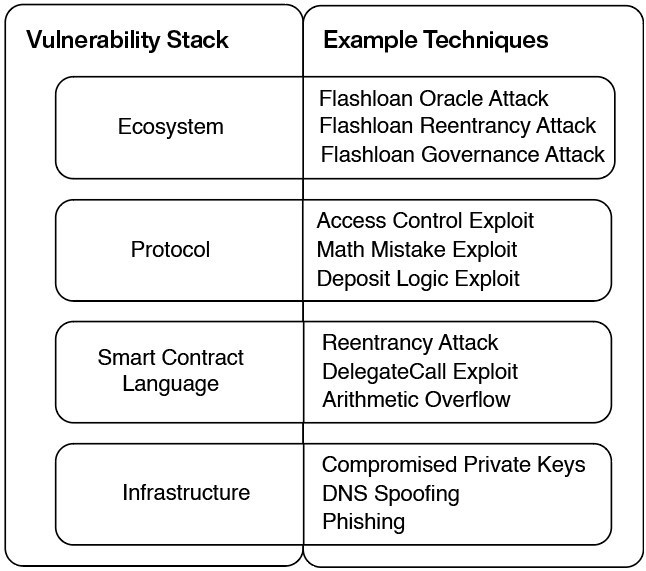
Attacking Infrastructure
Attacks on the infrastructure layer exploit weaknesses in the underlying systems of crypto applications: the blockchain used for consensus, internet services for the frontend, and tools for private key management.
Attacking Smart Contract Languages
Hackers at this layer exploit weaknesses and vulnerabilities in smart contract languages (such as Solidity), such as reentrancy and the dangers of implementing delegate calls, which can be avoided by following security best practices.
Attacking Protocol Logic
These attacks exploit errors in the business logic of individual applications. If a hacker discovers a flaw, they can exploit it to trigger behaviors that the application developers did not anticipate.
For example, if a new DEX has an error in the mathematical equation determining how much users earn from trades, this flaw can be exploited to allow users to earn more from trades than they should.
Protocol logic-level attacks can also exploit governance systems used to control application parameters.
Attacking Ecosystems
Many well-known crypto hackers exploit interactions between multiple applications. The most common scenario is when hackers exploit a logical error in one protocol to scale their attack using funds borrowed from another protocol.
Typically, the funds used for ecosystem attacks are borrowed through flash loans. When executing a flash loan, you can borrow the desired amount from liquidity pools of protocols like Aave and dYdX.
II. Data Analysis
I have collected a dataset of the 100 largest cryptocurrency hacking attacks since 2020, with a total stolen amount of $5 billion.
The ecosystem is the most frequently attacked. They account for 41%.
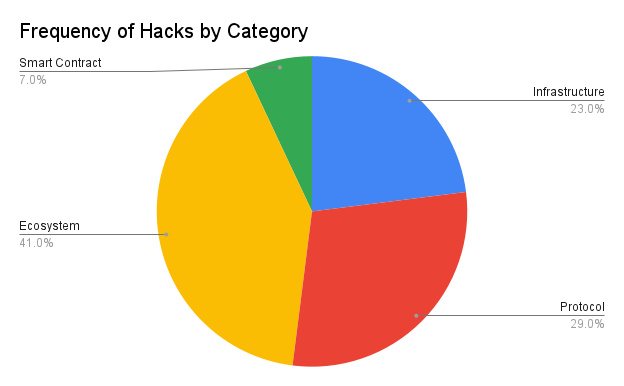
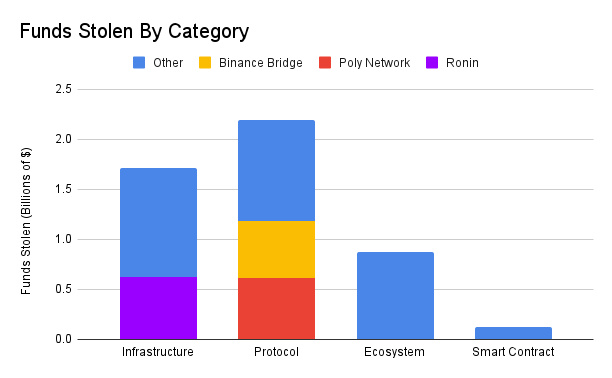
Protocol logic vulnerabilities have led to the most financial losses.
The three largest attacks: Ronin cross-chain bridge attack ($624 million), Poly Network attack ($611 million), and BSC cross-chain bridge attack ($570 million).
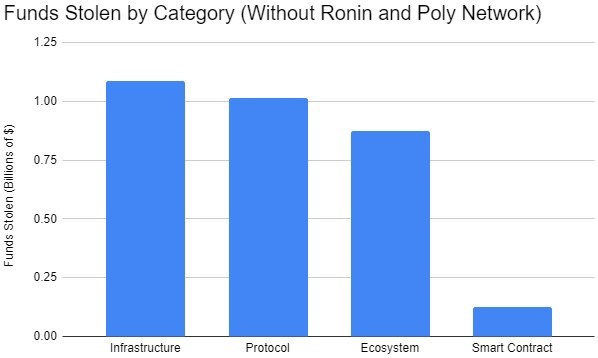
Excluding the top three attacks, cases of theft targeting infrastructure are the category with the highest financial losses.
III. How Do Hackers Operate?
Infrastructure
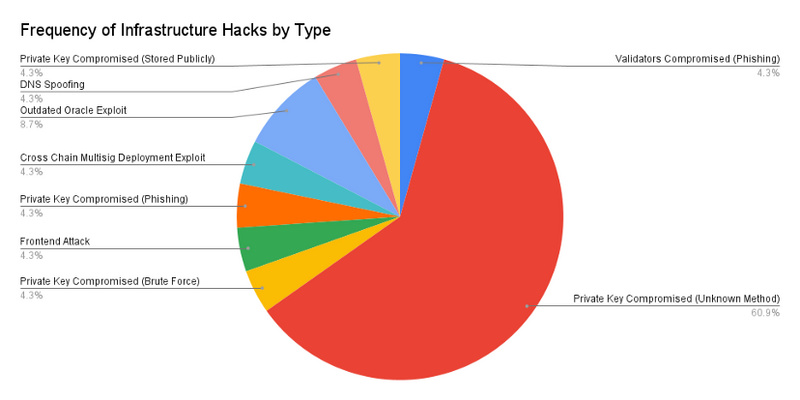
In 61% of infrastructure vulnerabilities, private keys were leaked in unknown ways. Hackers may obtain these private keys through social engineering attacks such as phishing emails and fake job postings.
Smart Contract Languages
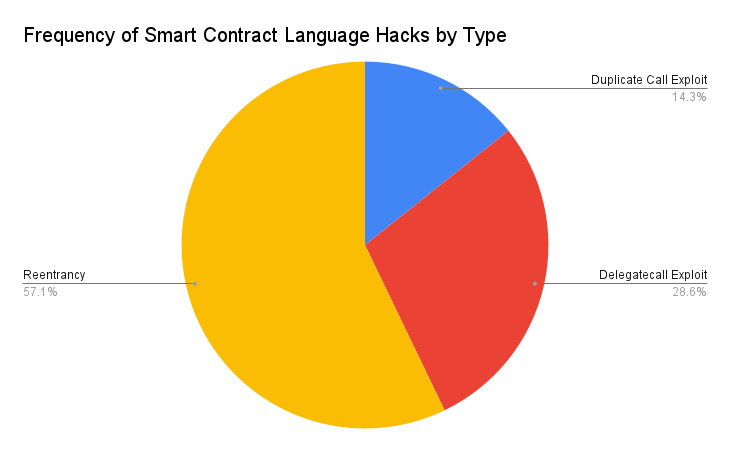
Reentrancy attacks are the most popular type of attack at the smart contract language level.
In a reentrancy attack, a function call in a vulnerable smart contract calls a function on a malicious contract. Alternatively, when the vulnerable contract sends tokens to the malicious contract, it can trigger a function in the malicious contract. Then, before the contract updates its balance, the malicious function recursively calls the vulnerable function.
For example, in the Siren Protocol hack, the function for withdrawing collateral tokens was easily reentrant and was called repeatedly (each time the malicious contract received tokens) until all collateral was exhausted.
Protocol Logic
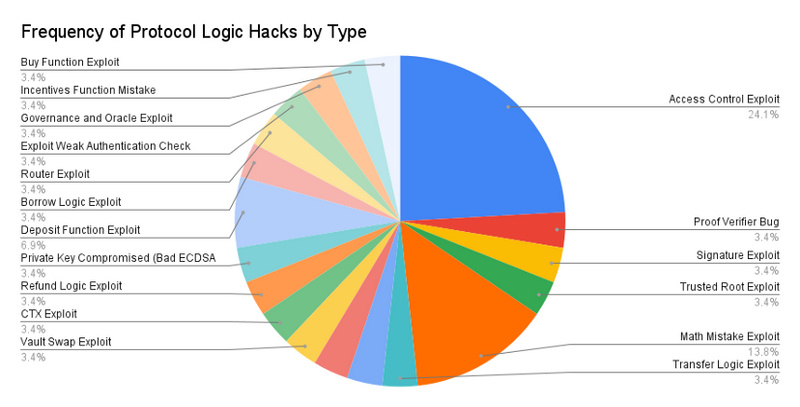
Most vulnerabilities at the protocol layer are unique to specific applications because each application has unique logic (unless it is a pure fork).
Access control errors are the most common recurring issue in the sample set. For example, in the Poly Network hack, the "EthCrossChainManager" contract had a function that anyone could call to execute cross-chain transactions.
Note: There are many cases where multiple protocols using the same technology are hacked because teams forked a vulnerable codebase.
For instance, many Compound forks, such as CREAM, Hundred Finance, and Voltage Finance, became victims of reentrancy attacks because Compound's code did not check the effects of interactions before allowing them. This worked effectively for Compound because they reviewed vulnerabilities for each new token they supported, but the teams making forks did not do the same.
Ecosystem
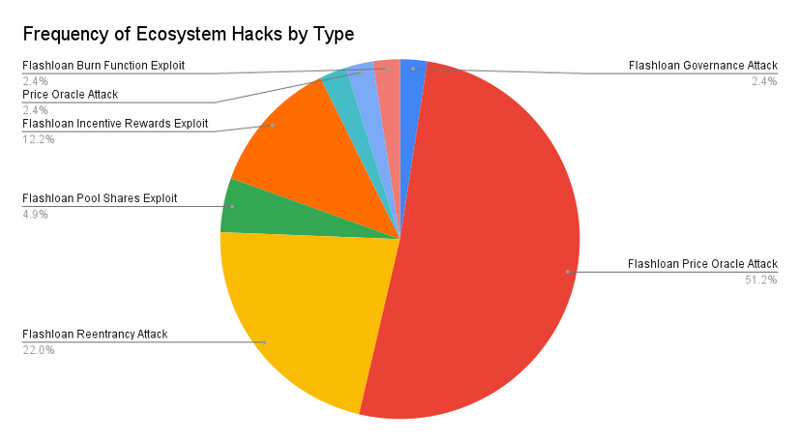
98% of ecosystem attacks utilized flash loans.
Flash loan attacks typically follow this formula: use the loan for large-scale trades, pushing up the token price on the AMM used as a price feed for the loan protocol. Then, in the same transaction, use the inflated tokens as collateral to obtain a loan far exceeding their actual value.
IV. Where Do Hackers Strike?
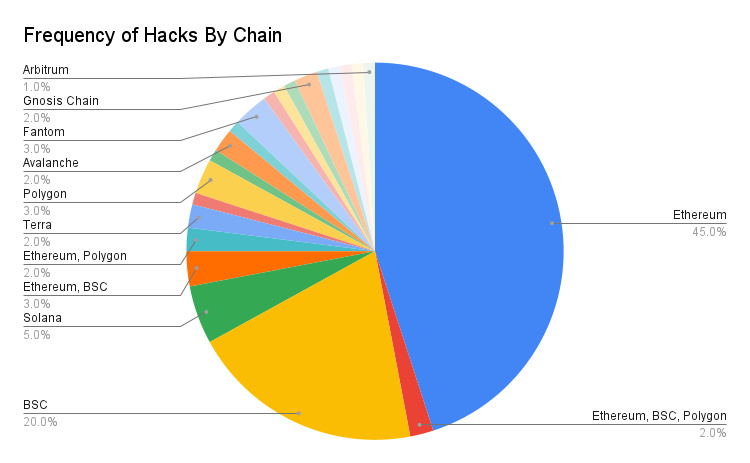
Analyzing the dataset based on the chain where the stolen contract or wallet resides, Ethereum has the highest number of hacks, accounting for 45% of the sample set. Binance Smart Chain (BSC) ranks second with a 20% share.
Several factors contribute to this:
Ethereum and BSC have the highest TVL (total value locked in applications), so the scale of rewards for hackers on these chains is larger.
Most cryptocurrency developers are familiar with Solidity, the smart contract language on Ethereum and BSC, and there are more complex tools supporting this language.
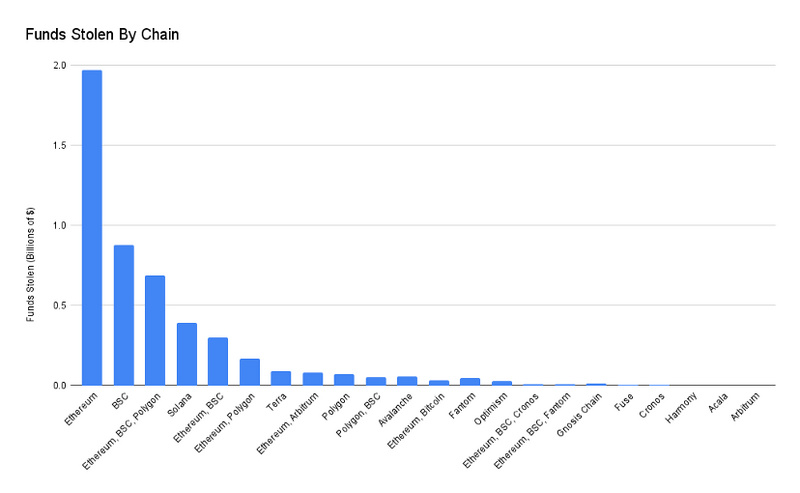
Ethereum has the highest amount of stolen funds ($2 billion). BSC ranks second ($878 million).
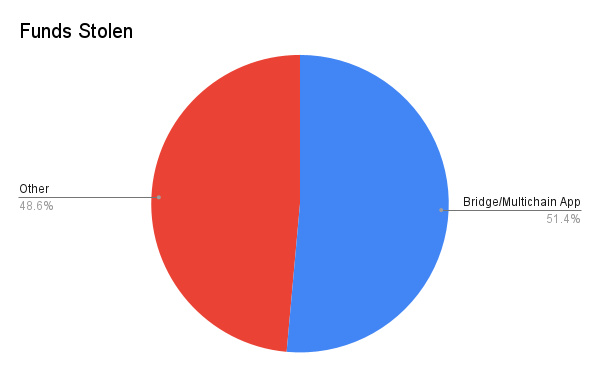
Involvement in cross-chain bridges or multi-chain applications (such as multi-chain trading or multi-chain lending) has had a significant impact on the dataset. Although these hacking incidents account for only 10% of the total, they have stolen $2.52 billion in funds.
V. How to Prevent Hacking Attacks?
For each layer of the threat stack, we can use some tools to identify potential attack vectors early and prevent attacks from occurring.
Infrastructure
Most large infrastructure hacking attacks involve hackers obtaining sensitive information such as private keys. Following good operational security (OPSEC) practices and conducting regular threat modeling can reduce the likelihood of this happening. Development teams with good OPSEC processes can:
Identify sensitive data (private keys, employee information, API keys, etc.);
Identify potential threats (social engineering, technical exploits, internal threats, etc.);
Find vulnerabilities and weaknesses in existing security defenses;
Determine the threat level of each vulnerability;
Develop and implement plans to mitigate threats.
Smart Contract Languages and Protocol Logic
- Fuzz Testing Tools
Fuzz testing tools, such as Echidna, test how smart contracts respond to a large number of randomly generated transactions. This is a good way to detect edge cases that produce unexpected results for specific inputs.
- Static Analysis
Static analysis tools, such as Slither and Mythril, automatically detect vulnerabilities in smart contracts. These tools are excellent for quickly identifying common vulnerabilities, but they can only capture a predefined set of issues. If a smart contract has issues not covered by the tool specifications, they will not be discovered.
- Formal Verification
Formal verification tools, such as Certora, compare smart contracts against specifications written by developers. These specifications detail what the code should do and the required properties. For example, when building a lending application, developers specify that each loan must have sufficient collateral backing it. If any possible behavior of the smart contract does not conform to the specifications, the formal verifier will identify the violation.
The downside of formal verification is that testing only maintains the same standards as the specifications. If the provided specifications do not cover certain behaviors or are too lenient, the verification process will not capture all errors.
- Audits and Peer Reviews
During audits or peer reviews, a trusted group of developers will test and review the project code. Auditors will write a report detailing the vulnerabilities they find and recommendations for fixing these issues.
Having a professional third party review contracts is a good way to discover vulnerabilities that the original team may have overlooked. However, auditors are human and will never catch all vulnerabilities. Additionally, trust in auditors is essential; if they find issues, they will inform you rather than exploit them themselves.
- Ecosystem Attacks
Although ecosystem attacks are the most common and destructive type, there are not many existing tools suitable for preventing such attacks. Automated security tools focus on finding errors within a single contract each time. Audits often fail to address how interactions between multiple protocols in the ecosystem can be exploited.
Monitoring tools like Forta and tenerly Alerts can provide early warnings when combinatorial attacks occur, allowing teams to take action. However, in flash loan attacks, funds are often stolen in a single transaction, so any early warning comes too late to prevent significant losses.
Threat detection models can be used to identify malicious transactions in the memory pool; transactions exist in the memory pool before nodes process them, but hackers can bypass these checks by using services like flashbot to send transactions directly to miners.
VI. The Future of Crypto Security
I have two predictions for the future of crypto security:
- I believe the best teams will shift from viewing security as an event-based practice (testing -> peer review -> audit) to seeing it as a continuous process. They will:
Perform static analysis and fuzz testing on every new code added to the main codebase;
Conduct formal verification for every major upgrade;
Establish monitoring and alert systems with responsive actions (pausing the entire application or specific affected modules);
Have some team members develop and maintain security automation and attack response plans.
Security work should not end after an audit. In many cases, such as the Nomad cross-chain bridge hack, the vulnerabilities were based on errors introduced in upgrades after the audit.
- The process of the crypto security community responding to hacking incidents will become more organized and streamlined. Whenever a hacking incident occurs, contributors flood into crypto security group chats eager to help, but the lack of organization means important details may be lost in the chaos. I believe that in the future, these group chats will evolve into more structured forms:
Using on-chain monitoring and social media monitoring tools to quickly detect active attacks;
Coordinating work using security information and event management tools;
Adopting independent workflows to communicate the work of white-hat and black-hat hackers, data analysis, root causes, and other tasks.


























