Exploring Web3 Wallet Security Issues: What Kind of Recovery System Does the Ethereum Community Need?
Original Title: 《DAOrayaki |What Kind of Social Recovery System Does the Ethereum Community Need》
Author: Vitalik, isthisanart
Translator: Xinyang
One of the biggest challenges in making cryptocurrency and blockchain applications accessible to ordinary users is security: how do we prevent users from losing or having their funds stolen? Loss and theft of funds is a serious issue that often results in innocent blockchain users losing thousands of dollars, and in some cases, wasting most of their net worth.
Over the years, many solutions have been proposed: paper wallets, hardware wallets, and my once-favorite multi-signature wallets. In fact, they have led to significant improvements in security. However, these solutions all have various flaws—sometimes the additional protection against theft and loss provided is far below what is actually needed, sometimes they are cumbersome to use, leading to little adoption, and sometimes both. In early 2021, Vitalik proposed an alternative and reiterated it in his May article "Decentralized Society: Finding Web3's Soul": a new type of smart contract wallet known as a "social recovery wallet." Compared to previous options, these wallets have the potential to offer high levels of security and better usability, especially as the Ethereum ecosystem migrates en masse to rollup layer two solutions, which can effectively address the two major issues currently facing social recovery wallets: (1) reliance on centralized relayers, and (2) high transaction fees. The DAOrayaki community has organized and summarized a series of proposals for social recovery systems in this article. This article will discuss what a social recovery wallet is, alternative use cases for social recovery systems, and user feedback.
1. Social Recovery Wallet
The social recovery system works as follows:
- Only one "signature key" is used to approve transactions.
- There are at least 3 (or more) "guardians," with a majority needed to cooperate to change the account's signature key.
The signature key has the ability to add or remove guardians, but this can only be done after a certain period (usually 1-3 days).
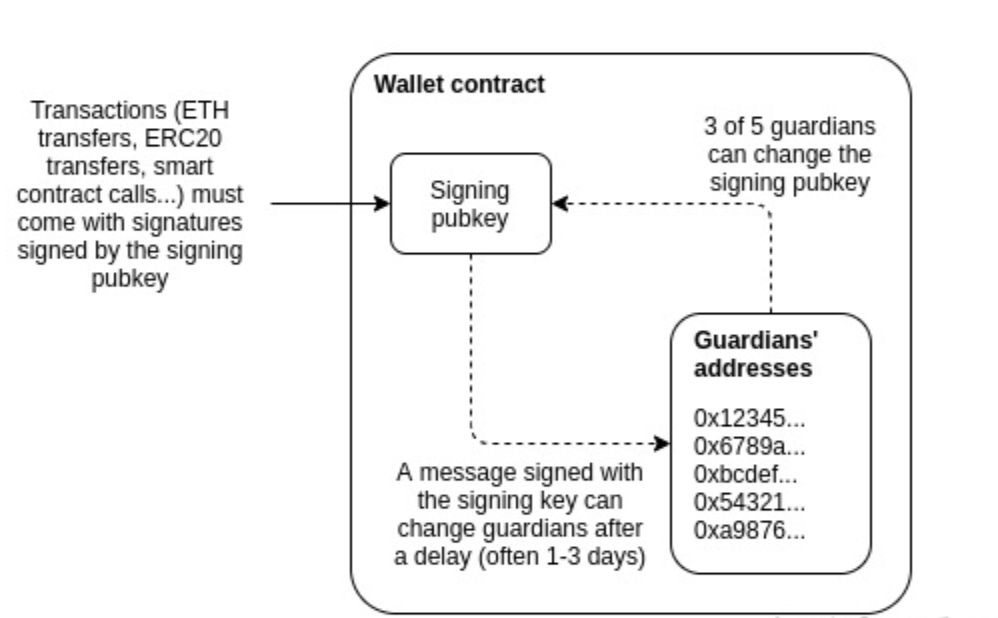
In all normal cases, users can use their social recovery wallet as simply as a regular wallet, signing messages with their signature key, allowing each signed transaction to be quickly completed with a single confirmation, just like in a "traditional" wallet (such as Metamask).
If a user loses their signature key, the social recovery function will be activated. The user just needs to contact their guardians and have them sign a special transaction to change the registered signature public key in the wallet contract to a new signature. This is simple: they can just visit a webpage, like security.loopring, to view and sign the recovery request. For each guardian, it is as easy as trading on Uniswap.
There are many possible options for choosing who acts as guardians. The three most common choices are:
- Other devices owned by the wallet holder (or paper mnemonic phrases)
- Friends and family
- Institutions that will sign recovery information upon receiving confirmation of your phone number or email, or verify your identity in person via video call in important cases.
Guardians can be easily added: you can simply enter their ENS name or ETH address to add a guardian, although most social recovery wallets will require guardians to sign a transaction on the recovery webpage to agree to be added. In any reasonably designed social recovery wallet, there is no need to download and use the same wallet; they can simply use their existing Ethereum wallet, regardless of the type of wallet. Given the high convenience of adding guardians, if you are fortunate enough to have a social circle composed of Ethereum users, I personally lean towards a higher number of guardians (ideally more than 7) to increase security.
If you already have a wallet, there is no need for guardians to constantly put in effort: any recovery actions you take will be completed through your existing wallet. If you do not know many other active Ethereum users, then trusting a small number of technically capable guardians is the best option.
To reduce the risk of guardians being attacked or colluding, your guardians do not have to be public: in fact, they do not need to know each other's identities. This can be achieved in two ways. First, instead of directly storing the guardians' addresses on-chain, it is better to store the hash of the list of addresses on-chain, with the wallet owner simply posting the complete list during recovery.
Second, each guardian can be required to deterministically generate a new single-use address that they will only use for a specific recovery; they do not need to send any transactions using that address unless recovery is actually needed. To supplement these technical protections, it is advisable to choose a diverse set of guardians from different social circles (ideally including an institutional guardian); these suggestions combined will make it difficult for guardians to be attacked or collude simultaneously.
If you die or become permanently incapacitated, guardians can publicly announce their identities so that they can find each other and recover your funds.
A social recovery wallet is not a betrayal, but rather an expression of "cryptographic value."
For any form of multi-signature, social recovery, or other suggested solutions, a common response is that such solutions trace back to the idea of "trusted persons," which is seen as a betrayal of the values of the blockchain and cryptocurrency industry. While I understand why people might think this at first glance, I want to say that this criticism stems from a fundamental misunderstanding of cryptographic technology.
To me, the goal of cryptocurrency has never been to eliminate the need for all trust. Rather, the purpose of cryptography is to give people access to the foundations of cryptography and economics, to provide people with more choices about whom to trust, and to allow people to establish more constrained forms of trust: empowering someone to do something on your behalf without giving them the power to do whatever they want. From this perspective, multi-signature and social recovery are perfect expressions of this principle: each participant has some influence over the ability to accept or reject transactions, but no one can unilaterally move funds. This more complex logic allows for the establishment of a mechanism that is far more secure than one controlled unilaterally by a single person or key.
Human input should be used cautiously, not completely discarded; this fundamental idea is very powerful because it aligns well with the strengths and weaknesses of the human brain. The human brain is not well-suited for remembering passwords and tracking paper wallets, but it is a specialized chip for tracking relationships with others. This effect is even stronger among non-technical users: they may struggle more with wallets and passwords, but they are equally adept at social tasks like "choosing 7 people who won't collude against me."
If we can extract some information from human input to make it a mechanism without turning these inputs into mediums for attack and exploitation, then we should figure out how to do that. Social recovery is very robust: to compromise a wallet with 7 guardians, 4 of those guardians would need to somehow discover each other and agree to steal the funds, and any one of them would not tip off the owner. Of course, this is a daunting challenge compared to attacking a wallet protected solely by one person.
2. Alternative Use Cases for Social Recovery Wallets
In his January 2021 article, Vitalik briefly introduced the principles and characteristics of social recovery wallets (i.e., smart contract wallets) through the examples of Argent and Loopring. In July 2021, he proposed "Alternative Mechanisms for Social Recovery Use Cases" on ethresear.ch[1]. This article focuses on that alternative mechanism.
The term Dark Crystal Web3 originates from a proposal made by Vitalik Buterin after his initial post in 2021[2], suggesting a system that allows recovery partners to operate without installing software or holding any other data, provided they have a personal Ethereum wallet.
The Magma Collective is currently working to develop it into an MVP (Minimum Viable Product). This is a social recovery protocol for which we have identified three main important features.
- The application does not require recoverers to remember anything other than the access password to their Ethereum main wallet.
- The application should be confidential, meaning it can back up any type of secret, including but not limited to Ethereum private keys.
- Ideally, the application should allow for the anonymity of both the secret owner and the recovery partners.
Since the application deals with secrets, possibly high-value secrets, it is crucial to validate the security assumptions and trust requirements in our project.
The system consists of two parts:
- A web-based dAPP for recovery partners that calls Web3 APIs to generate cryptographic key pairs for derived signatures and retrieves and decrypts shared data from the contract during recovery.
- An offline-first software component for backup personnel. Given a list of keys and public keys, it generates a set of encrypted shares and then publishes them to the blockchain. As an offline fist, the program does not perform actual publication but generates a dapp link containing the encrypted payload. This can then be transferred to any browser with a Web3 extension (e.g., via QR code).
The basic process of its operation can be referenced here.
3. What Kind of Social Recovery System Does the Ethereum Society Need?
The social recovery system built on the Ethereum foundation focuses on usability.
As part of the initial phase of MVP development, Dark Crystal Web3 conducted user research on the core tools and protocols of the Web3 and Ethereum communities, interviewing representatives from WalletConnect, 3Box, Metamask, Gnosis Safe, Rainbow, and Tally, and distributing an anonymous questionnaire on Twitter and Discord. The goal was not only to assess the usability of the Dark Crystal Web3 project but also to evaluate the importance of the current concept of social recovery and the potential demand for tooling.
The Role of Cold Storage
- What is the technical level of users?
- What kinds of "identities" are already being used on-chain, and what are the preferences for anonymity?
- The roles of on-chain storage versus centralized storage.
- Most importantly, considerations for the roadmap.
The Role of Cold Storage
Usability is prioritized, and this is an important consensus; beyond that, our most significant finding is that cold storage user scenarios are quite rare. Cold storage refers to saving keys in a way that is never connected to the internet—this could be a paper wallet or a hard drive that is only connected to an offline computer. It is widely regarded as the safest way to store keys. However, transacting with cold storage keys presents significant usability barriers: typically, a wallet program must be downloaded and set up on an offline computer to package and sign transactions, which are then transferred to another device for broadcasting. Given that our application deals with privacy, we wanted to know how likely users are to accept this process.
Perhaps somewhat surprisingly, we found that this security practice is not common. Or more accurately, the overlapping subset between cold storage keys and the keys users would back up with our application is very small. In all our synchronous conversations, we learned that while supporting cold storage pathways is important, users do not use it. From those respondents who do have cold storage keys, we learned that they would only use a system like ours for keys from less valuable hot wallets.
The respondents to the questionnaire were somewhat more inclined towards cold storage—33% said they would keep their keys in cold storage all the time. As the research period extended, we also received feedback that the most security-conscious users tend to have their own backup systems rather than trust ours. Considering that those who most need social recovery often lack technical skills: "Anyone who can use the command line does not need social recovery."
What is the Technical Level of Users?
In fact, what level of technical literacy we can expect from users is another area of discussion—what tools, wallets, etc., are our potential users familiar with or need?
Architecturally, Dark Crystal Web3 involves a browser-based hosted application and a Rust command-line component that can provide services locally. Our questionnaire respondents and interviewees are tech-savvy, with 80% saying they would be willing to use a command-line application if necessary. The current architectural plan is based on the desire to support cold storage, but based on feedback, we suspect that if our application had a fully hosted version, only a small portion of users with clear motivation would use it in other ways. The feedback was so strong that despite our work spanning from cold storage to hosted solutions, the possibility of going in the opposite direction is not negligible.
Although we discuss the browser-based dapp as the main entry point, we received strong feedback from 2 out of 6 respondents that a downloadable application is a more trustworthy and preferable design pattern due to the frequency of phishing attacks. In the vast majority of cases, tools like Metamask, Walletconnect, mobile wallets, and blockchain explorers posed no issues for respondents or questionnaire participants.
While we try to make the protocol independent of whether secrets are backed up, we believe that all potential secret owners have already joined Ethereum. We repeatedly heard that non-Ethereum users are unlikely to choose our social recovery protocol. That is to say, they hope recovery partners can cover those who are technically inexperienced and do not even have a wallet. We need to consider this unique demand.
What Kind of "Identities" Are Already Being Used On-Chain, and What Are the Preferences for Anonymity?
One of our core questions is how to support the anonymity of participants: how much anonymity is needed, and how can recovery data be reliably found later while maintaining anonymity? There are several potential solutions, all involving storing recovery data with some query key that can be hashed or derived from the user's main wallet.
However, we wanted to know if users' usage patterns would support this approach. Do people maintain a persistent wallet, or do they frequently switch between different wallets derived from the same seed? Do they generate new seeds? All the in-person interviews confirmed that our typical users would have a "main Ethereum address" that they could never forget. However, interestingly, half of the questionnaire respondents said it is possible or indeed the case that users have forgotten this or never had it. The frequency of "main Ethereum address" as an identity concept is a potential area for future research.
Overall, feedback strongly supports anonymity, but we repeatedly heard that once a significant number of users become part of the application, a "needle in a haystack" level of anonymity is sufficient in many cases. However, it is unclear how to initiate this or what specific threshold can achieve this. We discussed with several respondents whether there is a public protocol that could be used to map Ethereum addresses to public cryptographic keys, thus providing a bootstrap for this anonymity, but we found no existing project to fill this role. We also found that the anonymity of recovery partners received more recognition than that of secret owners, as shown in the figure below.
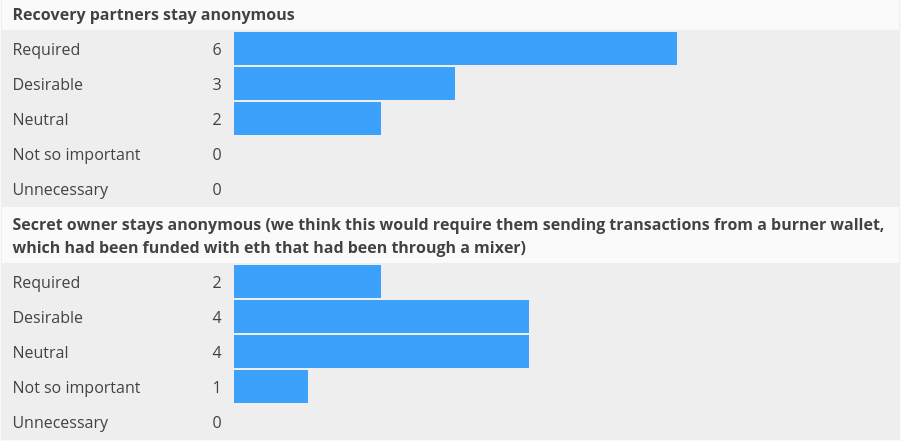
Three questionnaire respondents expressed concerns that they might forget who their recovery partners are, and we also received requests for the ability to change recovery partners multiple times.
On-Chain Storage vs. Centralized Storage
We received criticism regarding on-chain storage of encrypted secrets in two scenarios: one from a cost perspective and one from concerns about quantum threats to cryptography. Indeed, if any cryptography we use is ever broken, all secrets stored by our protocol would be affected. In terms of cost, both questionnaire respondents and interviewees considered around $200 to be the upper limit for the application's transaction costs, with lower costs being more favorable.
We heard that for our use case, there is no advantage to being on the mainnet compared to another Ethereum-like network, such as Polygon or Gnosis Chain.
Finally, some suggested considering a centralized approach for the application, allowing users to choose not to store on-chain, which would certainly bring other potential issues (ongoing maintenance, potential leaks) but could still meaningfully increase accessibility. 37% of questionnaire respondents indicated they would feel more comfortable with off-chain storage. Moreover, the long-term maintenance of the protocol was repeatedly cited as a concern: how can potential users trust that the recovery process will still work after our team potentially disbands or undergoes significant changes? And is there any way for secret owners to verify that their secrets are recoverable without going through the entire process?
Most Important Considerations for the Roadmap
So far, through thinking about the minimum viable product, we have identified an important aspect of secret recovery: the need for communication between secret owners and recovery partners. Initial setup information and recovery data need to be exchanged between both parties. This is likely the biggest security weakness of the system. 100% of questionnaire respondents believe it is possible to leak some fragments of secrets through insecure out-of-band transmission, and our in-person interviews strongly echoed this view.
Since many of our respondents are protocol developers, we asked them about the transmission of information from wallet to wallet in encrypted wallets and existing roadmap features that could assist communication. A closely related set of features pertains to notifications for secret owners and recovery partners at various stages of the recovery process. Many wallet developers we interviewed do indeed have this feature on their roadmaps, although no release dates were confirmed. Further work in this direction appears to be very important for the ecosystem, and integrating with one of these solutions is likely to be at the core of Dark Crystal Web3's future work.









