Analysis of the Harmony cross-chain bridge hacking incident with a loss of nearly 100 million dollars
Author: CertiK Chinese Community
On June 23, 2022, at 19:06:46 Beijing time, the CertiK audit team detected that the cross-chain bridge between the Harmony chain and Ethereum experienced multiple malicious attacks.
CertiK team security experts analyzed that this attack event may have originated from hackers obtaining the owner's private key— the attacker controlled the owner of the MultiSigWallet to directly call confirmTransaction() to transfer a large number of tokens from the Harmony cross-chain bridge, resulting in the theft of assets worth approximately $97 million on the Harmony chain.
Attack Steps
Taking the first exploit transaction of 13,100 ETH as an example:
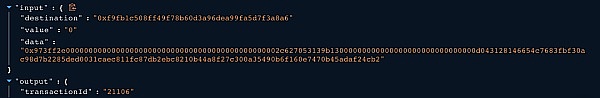
① The owner of the MultiSigWallet contract, 0xf845a7ee8477ad1fb446651e548901a2635a915, calls the submitTransaction() function to submit a transaction with the following payload, generating transaction ID 21106.
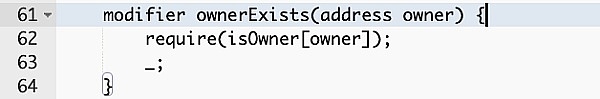
② To confirm the transaction, the caller must be the contract owner.
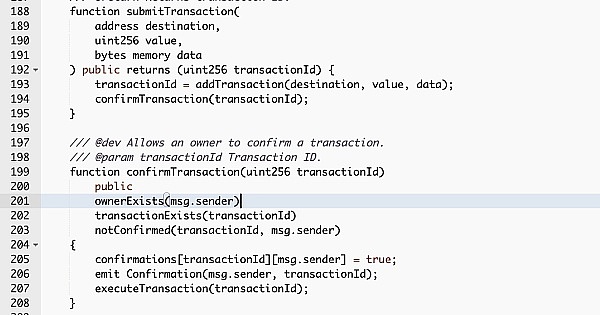
③ In the subsequent attack, the MultiSigWallet contract owner (0x812d8622c6f3c45959439e7ede3c580da06f8f25) calls the confirmTransaction() function, with the input transaction ID being 21106.

④ To successfully execute the transaction, the caller must be the contract owner.
⑤ The executeTransaction() function makes an external call using the input data, which triggers the unlockEth() function on the Ethmanager contract.

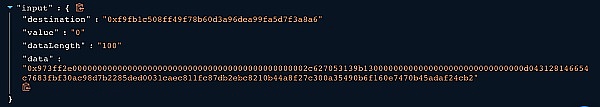
⑥ The input data for the unlockEth() function specifies the amount, recipient, and payer.
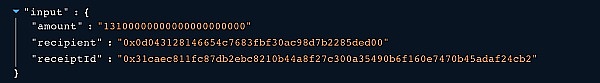

⑦ Since the attacker somehow controlled the owner's permissions, the attacker was able to execute the transaction with ID 21106, which transferred 13,100 ETH to the attacker's address 0x0d043128146654C7683Fbf30ac98D7B2285DeD00.
⑧ The attacker repeated the previous process on other ERC20Manager contracts using different transaction IDs to transfer large amounts of ERC20 tokens and StableCoin.
Asset Destination
As of the time of writing, approximately $97 million of stolen assets are still stored at address 0x0d043128146654C7683Fbf30ac98D7B2285DeD00.
Vulnerability Transactions
In the following transaction, the attacker stole 13,100 ETH, worth approximately $14,619,600 (using the current price of ETH: $1116): https://etherscan.io/tx/0x27981c7289c372e601c9475e5b5466310be18ed10b59d1ac840145f6e7804c97 [13,100 ETH]
In the following transaction, the attacker stole 41,200,000 USDC:
https://etherscan.io/tx/0x6e5251068aa99613366fd707f3ed99ce1cb7ffdea05b94568e6af4f460cecd65
In the following transaction, the attacker stole 592 WBTC, worth approximately $12,414,832:
https://etherscan.io/tx/0x4b17ab45ce183acb08dc2ac745b2224407b65446f7ebb55c114d4bae34539586
In the following transaction, the attacker stole 9,981,000 USDT:
https://etherscan.io/tx/0x6487952d46b5265f56ec914fcff1a3d45d76f77e2407f840bdf264a5a7459100
In the following transaction, the attacker stole 6,070,000 DAI:
https://etherscan.io/tx/0xb51368d8c2b857c5f7de44c57ff32077881df9ecb60f0450ee1226e1a7b8a0dd
In the following transaction, the attacker stole 5,530,000 BUSD:
https://etherscan.io/tx/0x44256bb81181bcaf7b5662614c7ee5f6c30d14e1c8239f006f84864a9cda9f77
In the following transaction, the attacker stole 84,620,000 AAG, worth approximately $856,552:
https://etherscan.io/tx/0x8ecac8544898d2b2d0941b8e39458bf4c8ccda1b668db8f18e947dfc433d6908
In the following transaction, the attacker stole 110,000 FXS, worth approximately $573,100:
https://etherscan.io/tx/0x4a59c3e5c48ae796fe4482681c3da00c15b816d1af9d74210cca5e6ea9ced191
In the following transaction, the attacker stole 415,000 SUSHI, worth approximately $518,750:
https://etherscan.io/tx/0x75eeae4776e453d2b43ce130007820d70898bcd4bd6f2216643bc90847a41f9c
In the following transaction, the attacker stole 990 AAVE, worth approximately $67,672:
https://etherscan.io/tx/0xc1c554988aab1ea3bc74f8b87fb2c256ffd9e3bcadaade60cf23ab258c53e6f1
In the following transaction, the attacker stole 43 WETH, worth approximately $49,178:
https://etherscan.io/tx/0x698b6a4da3defaed0b7936e0e90d7bc94df6529f5ec8f4cd47d48f7f73729915
In the following transaction, the attacker stole 5,620,000 FRAX, worth approximately $5,608,096:
https://etherscan.io/tx/0x4ffe23abc37fcdb32e65af09117b9e44ecae82979d8df93884a5d3b5f698983e
Final Thoughts
In the "2022 Q1 Web3.0 Security Status Report" compiled by CertiK, it shows that the main culprit of the exorbitant attack losses in Q1 2022 is centralized risk, with cross-chain bridges being particularly vulnerable.
This attack event could have been identified through an audit that discovered the risk factor of "centralized risk." In addition to audits, the CertiK security team recommends that newly added code also undergo timely testing before going live.










