Foresight Ventures: Breaking Down the "Walled Garden", Web3 Reshapes the Social Paradigm
Written by: Alice, Foresight Ventures
Abstract
- Web3 social needs more crypto-native innovative approaches, rather than Web2 copycats. The transformation of social paradigms will be a social renaissance shifting from "platform-centric" to "user-centric." The new narrative includes five key themes: social graph, decentralized identity, privacy protection, composability, and tokenization. We are still in the early stages of this social paradigm shift.
- The social landscape can be divided into four layers from the ground up: data layer, protocol layer, privacy layer, and application layer. Among them, the protocol layer is the most critical. In the long run, the protocol layer is expected to continuously attract users to generate new relationships, identities, and honors through social protocols and foundational data networks. The application layer is expected to form sustainable tokenomics for social applications. Additionally, social relationships formed by Soulbound Tokens (SBT) may balance composability and weak financial attributes, returning the core value of on-chain social tokens to the proof of relationships themselves, becoming truly effective social credentials.
What Should a Decentralized Social Network in Web3 Look Like?
Many Web3 social products still follow Web2 business models, but such solo efforts are challenging. What we need are not copycats like Web 3 Twitter or Web 3 Facebook, but more native innovative approaches.
A Discussion on the Transformation of Web3 Social Paradigms
In Web2, everyone lives in the "walled gardens" created by social giants. The longer users stay within these "walls," the better the creators understand them. However, once they move to another garden, they must abandon all social relationships and data, leaving empty-handed. In Web3, it will become possible to shape a more just, free, and equal internet environment.
Just as the European Renaissance brought about a transformation from "God" to "man" in humanistic thought, the evolution from Web2 social to Web3 social will also be a grand social renaissance shifting from "platform-centric" to "user-centric."

The author believes that the new narrative of social paradigm transformation will include five key themes: social graph, decentralized identity, privacy protection, composability, and tokenization.
Relationship Transformation: Returning the Social Graph to Its Owners
In the narrative of Web3, user social graphs will no longer be monopolized by a single company but will be fully stored on-chain.
Web3 social may resemble social interactions in the metaverse: you can see your friends from WeChat in World of Warcraft, maintaining friendships across different scenes like the protagonist in the movie "Ready Player One," and even algorithmically find a soulmate.

In reality, obtaining social graph data is not easy.
Creating a complete social graph requires strong multi-source data cleaning, correlation, and aggregation algorithm capabilities. Moreover, user relationships cannot be purely analyzed from on-chain behavior; much social information is still stored on off-chain servers. Finally, managing social graphs often involves not just managing existing data but also guiding users to form their own relationship network data through product functionality development.
Identity Transformation: Traceable, Proofless Decentralized Identity
What exactly is Web3 social? The following image answers this question clearly.
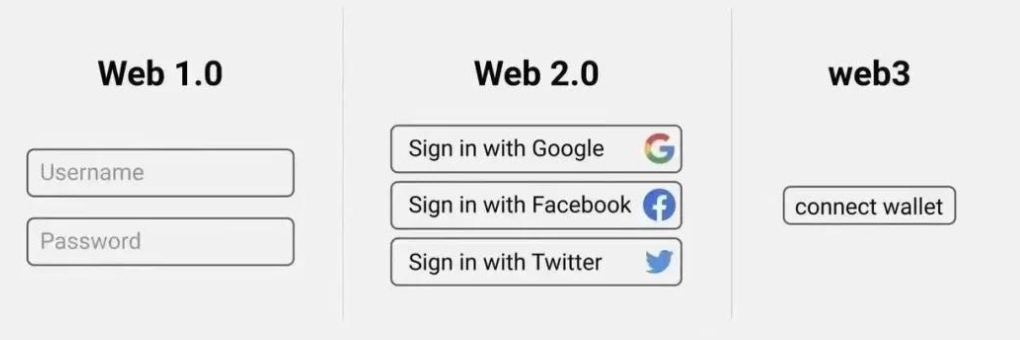
In the Web1 and Web2 eras, we needed to go through cumbersome processes to prove we were the account holders. In Web3, simply signing a string with a wallet private key can prove address ownership.
Decentralized Identity (DID) may become the most important asset for Web3 users. The transparency and immutability of on-chain data establish the foundation of identity trust, while cross-project data reading and invocation ensure the universality and composability of identity. Whether it’s personal reputation, NFT ownership, financial lending, tickets, identity certificates, licenses, or passports, all can be transformed into unique on-chain information that users have complete control over, accessed through a single identity protocol.
- For project teams, it becomes easy to find the core airdrop audience during the cold start phase.
- For social Dapps, decentralized identity can inherently establish social and group relationships. Specific entry thresholds can be automatically judged by reading asset information and historical proofs on-chain, without the need for additional verification.
Privacy Transformation: Multiple Accounts, Information Authorization, Privacy Computing, Privacy Trading
On-chain data belongs to each individual, and it is also readable by everyone. You might think that such openness leaves no privacy?

Data privacy issues can be broken down into three levels: social application layer, interaction layer, and data storage layer.
- In the social application layer, the solution is: multiple accounts and information authorization. Multiple accounts mean that different wallets can have different circles and identities. However, if a DID can correspond to multiple wallet addresses, a more robust solution is to allow users to choose which parts of their data can be publicly read in the social graph and DID protocol.
- In the interaction layer, introducing privacy computing protocols allows data to circulate securely in a "usable but invisible" manner while ensuring data privacy and security.
- In the data storage layer, the immutable and public nature of blockchain data contradicts privacy, making privacy issues more complex. Since data cannot be changed once it is on-chain, encrypting all accounts and transactions is very costly and time-consuming. A mid-way solution might be to allow users to choose which parts of their data need privacy protection in advance, storing non-public data off-chain.
For more on Web3 privacy, I recommend reading this in-depth article: Foresight Ventures: Understanding the Other Side of Web3 "Privacy", where I won’t elaborate further.
Composability: Composability in Software is Like Compound Interest in Finance
Composability will place cryptocurrencies at the forefront of financial and other industry revolutions, fundamentally changing industries like the internet and opening up a world of infinite possibilities.
We believe that "composability" includes several key elements:
- Software composability: the ability to "directly access assets or data generated by other protocols and then combine them with another protocol." This continuous combination and recombination allows each innovative outcome to become the starting point for the next round of innovation, giving rise to more powerful models within software combinations. For example, the combination of lending protocols and social protocols can form "social credit."
- Data composability: new products no longer need to accumulate user data from scratch; decentralized databases store user identity information, social graphs, social history, etc., in a unified data model (e.g., Ceramic), allowing Dapps to access and interoperate natively.
- Identity composability: Dapp data can be read and invoked across projects, unlike Web2, where it is isolated on centralized servers, ensuring the universality and composability of user identities in the on-chain world.
- Detachability: users should have the right to choose to authorize only specific personal information to certain application protocols and can revoke third-party access at any time.
Tokenization: Coming for Profits, Staying for the Network
If Web2 was "coming for tools, staying for the network," then Web3 will be "coming for profits, staying for the network."
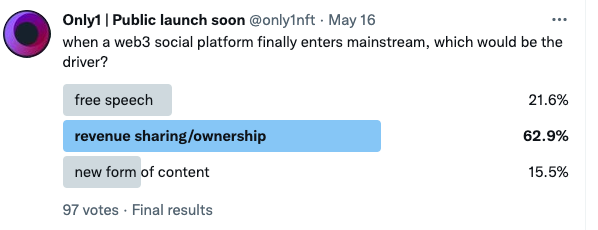
Web3 social applications have introduced many interesting shared profit models worth long-term attention:
- Fan economy: Rally helps creators issue fan tokens, eliminating intermediaries' cuts. As creators gain popularity, the value of the tokens also rises, allowing creators and token-holding fans to share in this profit.
- NFT-izing creative content: Mirror helps authors mint an article as an NFT and initiate DAO crowdfunding. Each article NFT can be understood as a fund, where everyone can hold a certain share, and the main profit for holders comes from the dividends of NFT resale fees and the appreciation of their shares.
- NFT-izing social relationships: Lens Protocol mints users' social relationships as NFTs, which will appreciate alongside content NFTs, creating a subtle symbiotic relationship between creators, users, and content; this provides a fertile ground for communities. Atem Network connects communities through NFTs, allowing users to discuss, trade, and govern together within the NFT community.
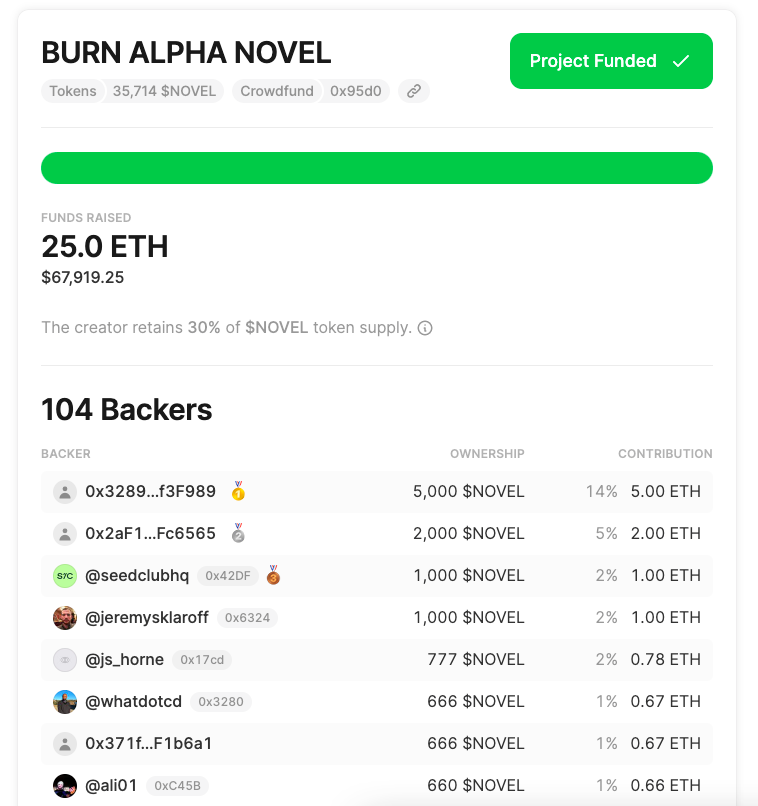 Mirror article crowdfunding
Mirror article crowdfunding
However, we can observe several common issues:
- The vast majority of creators do not receive sufficient incentives due to a lack of fans. Most tips or NFT crowdfunding flow to top projects, where those who are already well-funded can secure more funds.
- The gas fees for NFT minting are too high, and the profits for small and medium creators and users minting NFTs may not even cover the gas fees. Future solutions for NFT-driven applications are likely to involve moving to Layer 2 or creating Appchains on other public chains to reduce costs.
Web3 Social Panorama
 The author believes that social can be divided into four layers from the ground up: data layer, protocol layer, privacy layer, and application layer.
The author believes that social can be divided into four layers from the ground up: data layer, protocol layer, privacy layer, and application layer.
Data Layer
The data layer includes decentralized data networks and databases, such as Arweave, IPFS, Ceramic, Kwil, etc., used to store users' on-chain identity data, social relationships, and communication content.
Due to incomplete on-chain data and low access efficiency, some data is still stored on centralized servers like AWS. As more user data goes on-chain, decentralized databases will have vast development space.
Ceramic
Ceramic is a decentralized, cross-chain database service built on IPFS that can manage dynamic content data.
- Ceramic solves the dynamic storage problem by storing data streams and also provides a powerful built-in authentication mechanism with 3ID DID and IDX cross-chain identity protocols. Several social projects are already developing on Ceramic, such as the social graph CyberConnect, Web3 Twitter Orbis, and instant messaging platform The Convo Space.
- In December last year, a massive influx of CyberConnect users caused Ceramic to crash, and its high concurrency solutions await time to test.
Protocol Layer
The protocol layer mainly includes decentralized identity and social graph protocols, which the author believes will be the core layer of the social track. The main reasons are as follows:
- It has strong universality; regardless of which social Dapp users use, they will need social graphs and DIDs.
- The protocol layer has strong scale effects, and it is likely that one or several universally applicable protocols will emerge in the future.
- Both the social graph and DID tracks are in the early stages of development; on one hand, there is no unified standard formed within the industry, and on the other hand, user awareness is shallow, and the competitive landscape is not mature, presenting high investment value.
From a broader perspective, to build a truly free speech internet environment, we need protocols, not platforms. As discussed in the article "Protocol, Not Platforms," creating protocols at least gives us the possibility of freedom, while creating platforms traps us in the old discourse system of walled gardens.
Recommended reading: "Protocols, Not Platforms: A Technological Approach to Free Speech" ------ MIKE MASNICK
Social Graph
Popular projects in the social graph track include CyberConnect, Lens Protocol, and 5 Degree, summarized as follows:
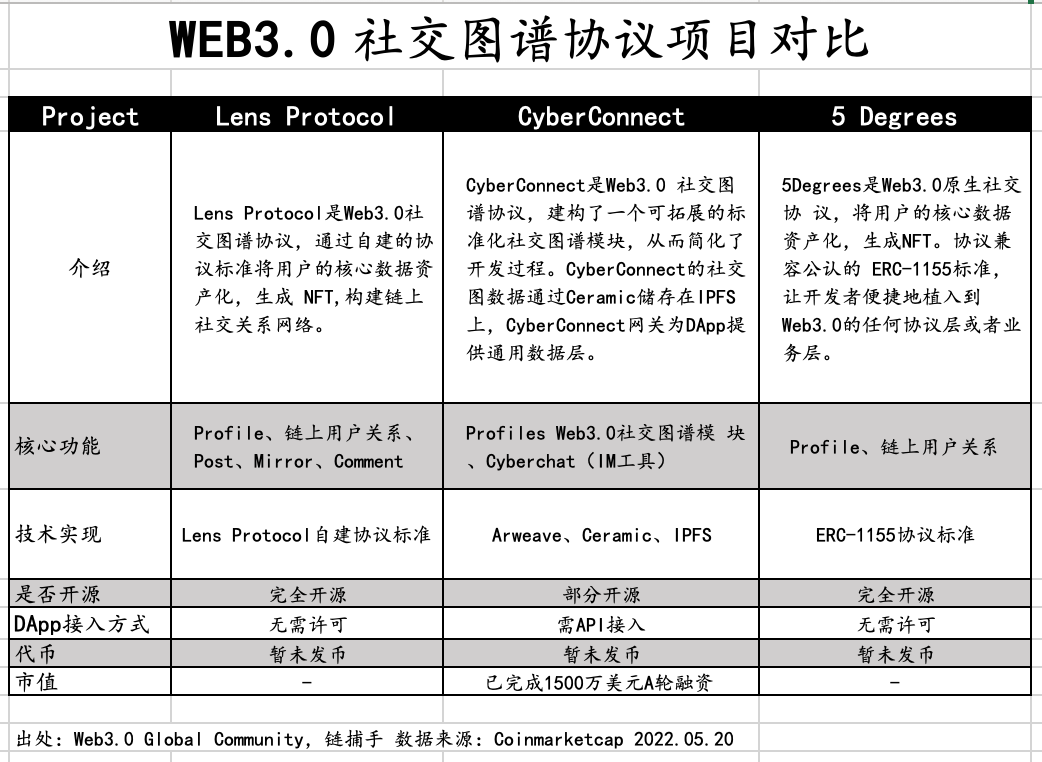
The three core products support profiles and on-chain social relationships, while Lens Protocol and CyberConnect have extensions in content and communication. Let's compare the two:
CyberConnect
CyberConnect aims to aggregate on-chain and off-chain data, providing a standard data layer. Developers can achieve invocation through APIs. All DID relationship data and Dapp usage data will be stored on IPFS via the Ceramic Network.
The advantage of this solution is its lightweight and pluggable nature; CyberConnect has registered over 1.4 million users, with more than 70 projects already implementing API access.
The downside is that the current functionality of the social graph is limited. Additionally, cost-free read/write of social graphs can easily generate redundant data during access. Previously, Facebook's social graph was troubled by Zynga, requiring more balance in handling and accessing data.
Lens Protocol
Lens aims to become an open-source social infrastructure, minting all social relationships within the ecosystem as NFTs to form a social graph. Lens has also established protocol standards to attract developers to build functional modules and applications, resembling the approach of public chain ecosystems.
Advantages of Lens:
- It is a smart contract on Polygon, with strong composability between modules, allowing applications within the ecosystem to share social content, relationships, and module components; CyberConnect, based on IPFS, has slightly lower composability.
- Lens mints personal profiles, content, and fan relationships as NFTs, offering strong monetization potential and imagination; for example, the floor price of Lens personal profile NFTs increased 10X within a month, and more NFT issuance activities are expected in the future.
- Compared to the Deso social network public chain, Lens's ecosystem and economic system are more open, which is crucial for social networks. All social apps in the Deso ecosystem require the use of the $DESO token, leading to noticeable liquidity issues and a smaller user base.
Limitations of Lens:
- In terms of implementation, Lens has only established social connections and still has some distance to go in building the graph; developers need to capture on-chain data themselves (most developers currently use The Graph).
- Of course, Lens also faces another issue; every interaction requires invoking the MetaMask wallet to pay gas fees, which does not provide a smooth user experience, while CyberConnect stores content in IPFS, offering a better user experience.
Lens's ecosystem construction model is relatively heavy, requiring high market expansion capabilities from project teams. Backed by the Aave team, Lens is currently in the internal testing phase but has made good overall progress, with leading projects including Phaver (a share-to-earn social application) and Lenster (a decentralized forum), allowing Dapps to rely on Lens's precise traffic for rapid cold starts. The potential for collaboration between Lens and Aave's business in the future is also worth long-term attention.
Decentralized Identity DID
Amber Group outlined the DID ecosystem in November 2021. DID is located at Layer 3, serving as a hub within the entire ecosystem.

DID projects can be roughly divided into four tracks: off-chain identity authentication, on-chain identity aggregation, on-chain credit scoring, and on-chain behavior authentication. It is worth emphasizing that the mature form of DID is not yet clear and lacks strict definitions; some projects are identity protocols, while others are credential networks or identity applications, focusing on different application scenarios. In the future, DID may likely be a whole with various components.
a. Off-chain Identity Authentication
Suppose a person graduated from Stanford University, previously worked as an engineer at Google, and owns two houses in Silicon Valley. If the above information can be verified and bound to an address held by this person, it will enhance their social, lending, and other activities on-chain.
BrightID
BrightID is a representative project for real identity verification, building a social identity network with over 57,000 users. Users need to schedule a Zoom video meeting, ensuring identity uniqueness through facial recognition and verification officer review.
Verite
Verite was launched by Circle, the issuer of USDC, on May 10, with KYC being one of its key identity verification components; specific details await further disclosure from the project team.
b. On-chain Identity Authentication
These DID projects do not focus on off-chain situations but achieve on-chain identity information aggregation management through the concept of "digital identity."
Unipass
Unipass is a representative of this type of project, focusing on on-chain identity aggregation management: through a Unipass ID, users can bind email, multiple ETH addresses, and connect to social graphs (CyberConnect), information aggregation platforms (RSS3), and other protocols, becoming a "One Pass" for users in Web3.
Spruce
Spruce is a digital identity authentication system that supports users' identity verification, credentials, and storage, providing decentralized access control and interoperability between Web2 APIs and Web3. Binding to existing Web2 platform accounts is a great identity enhancement solution for those who already have some influence in Web2.
c. On-chain Credit Scoring
The intention of these projects is straightforward—expanding the scenarios for DeFi lending by finding some implementation of the credit mechanisms from the financial industry in the real world within Web3.
ARCx
ARCx issues "DeFi Passports," quantifying users' credibility based on each DeFi Passport's credit score. Compared to the first two types of DID projects, on-chain credit scoring projects focus more on users' "digital financial identities," primarily using on-chain transaction data rather than their social data.
d. On-chain Behavior Authentication
The core logic of these projects is to guide users to participate in activities and behaviors required by certain partners and issue on-chain certifications.
Project Galaxy
Project Galaxy is not strictly an identity protocol but a credential network. Users can generate a "Galaxy ID" after connecting their wallets, automatically tagging them with certifications like "Uniswap Trader" or "OpenSea Trader" based on their address's historical behavior. Project teams interacting with Galaxy will incur fees, while Galaxy will reward corresponding curators (data providers) with tokens.
Privacy Layer
Privacy computing protocols aim to allow data to circulate securely in a "usable but invisible" manner. This mainly includes zero-knowledge proofs, secure multi-party computation, federated learning based on modern cryptography, trusted execution environments (TEE), and other technologies. Currently, well-known blockchain privacy computing networks include Oasis Network, PlatON, Phala Network, ARPA, Aleph Zero, Findora, and Deeper Network.
- The actual application scenarios of privacy computing networks are currently quite limited, as they are rarely adopted by industrial projects, and some technologies are still immature.
- The future explosion of social demand may win more users for privacy computing, but the investment priority of the privacy layer may not be as high as other layers. This is because a user may only need privacy processing for a small amount of data, and three prerequisites must be met: the popularization of Web3 social demand, the awakening of user privacy protection awareness, and the willingness to pay for it.
Application Layer
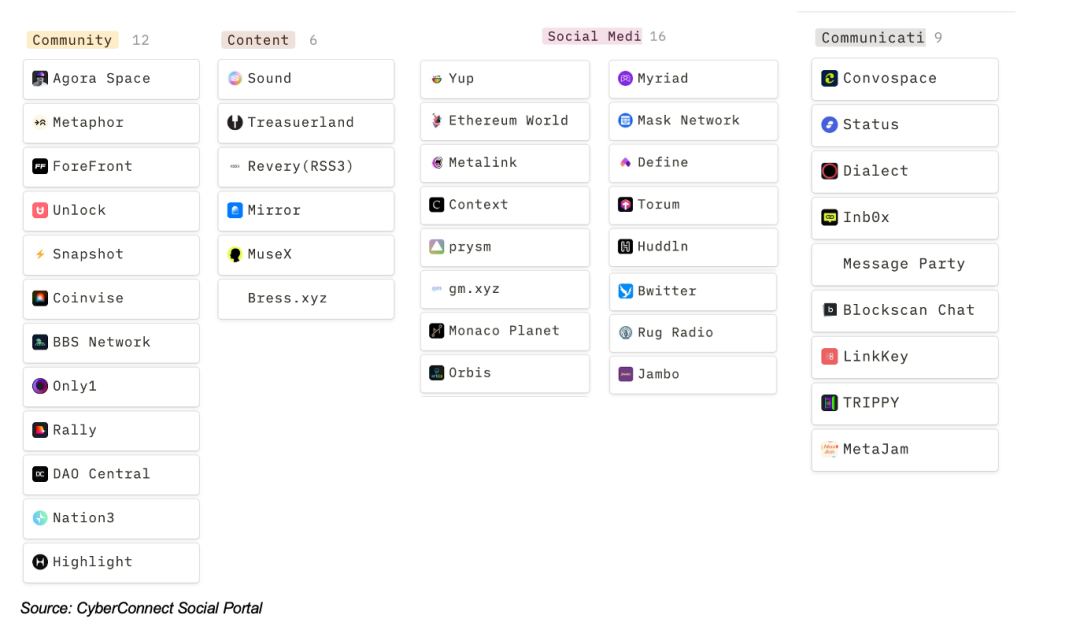
Web3 Social Application Map - Classified by Social Form
Low-threshold social applications may become an attempt for ordinary people to enter the vast ocean of Web3.
There has yet to be a phenomenal product in the social track, primarily due to the fact that many applications only have token acquisition scenarios, lacking consumption scenarios. Users habitually "mine, withdraw, and sell," failing to form network effects; unrestricted token flow to secondary markets also leads to continuously declining prices.
The author believes that possible social product forms include:
- NFT-based social applications. NFT holders can join holder groups, and users with high credit scores can directly find NFT buyers and sellers for P2P trading, swaps, and lending. A typical example is Atem Network, which aims to form communities through NFTs, allowing users to discuss, trade, and govern together within the communities they hold NFTs.
- Cross-platform and cross-chain IM applications. Users can manage friend relationships within Gamefi, DAO communities, and NFT groups in one Dapp, and can also update statuses to see which games their friends are playing and what NFTs they have acquired.
- Gamefi gold mining gameplay. A typical example is Phaver, a leading share-to-earn application in the Lens ecosystem. Users can earn token rewards by improving others' experiences (publishing quality content, discovering quality content, verifying information) and spend tokens to enhance their own experiences (content staking, purchasing traffic, subscribing to paid content, minting NFTs, etc.).
- A community of big V based on DeFi experiences or personal investment achievements, similar to Xueqiu. Users can showcase their personal mining experiences and investment achievements on their profile pages, while big Vs can output quality content to earn token rewards and issue fan tokens.
- DAO-based content social applications. Relying on DAO to achieve community autonomy and content review, all profits generated by the application will also be distributed to DAO members based on governance proposals.
Investment Directions
The Web3 social track is in its early stages, and the competitive landscape is not yet clear; emerging business models such as social relationship NFT-ization and fan economy are worth long-term attention.
Opportunities in the application layer: We are optimistic about social applications that can form good economic cycles and shared benefits, such as Mirror. The core is to assess whether the product has sufficient wealth creation effects and sustainable tokenomics to retain core users and quality creators, forming an endogenous economic cycle.
Opportunities in the protocol layer: We are optimistic about protocols and data networks that can attract users to generate new relationships, identities, and honor badges in the long run. These products serve as the infrastructure for social data and also as entry points for C-end traffic.
Exploration of social networks based on SoulBound Tokens: Currently, the main solutions for social protocols revolve around NFTs or off-chain databases. The former has overly strong financial attributes, while the latter suffers from weak composability due to not being on-chain. Social relationships formed based on SoulBound Tokens may balance composability and weak financial attributes, returning the core value of on-chain social tokens to the proof of relationships themselves, becoming truly effective social credentials.



























