Cross-Chain Discussion: In-Depth Analysis of 16 Cross-Chain Solutions Trade-offs
Author: DODO Research Institute
Cross-chain bridges are not a new topic; articles on the market have comprehensively classified and interpreted cross-chain bridges based on their basic elements, cross-chain technologies, and more. However, the current classification of cross-chain bridges can be overwhelming, hindering a macro understanding of their performance.
Dr. DODO aims to analyze and compare various performance aspects of 16 cross-chain bridges based on research. Through comparison, people can more intuitively perceive the differences between bridges and the problems they aim to solve, reflecting the future development trends of cross-chain bridges. This article focuses on comparing the performance of cross-chain bridges rather than providing an in-depth explanation of cross-chain technology itself; readers can refer to the cited references in the text for knowledge about cross-chain technology.
1: Literature Review
The Emergence of Cross-Chain Bridges
According to Blockchain Comparison, there are currently 115 public chains. Different blockchains have different communication protocols, consensus rules, and governance models. Haseeb Qureshi, managing partner at Dragonfly Capital, compares each public chain to a city; no matter how many skyscrapers (Rollups) can be built on Ethereum, they still need to connect with other cities. In this view, the emergence of cross-chain bridges becomes a natural necessity. Meanwhile, the booming DeFi, NFT, and Gamefi on emerging public chains encourage users to transfer funds across different public chains, making cross-chain bridges an inevitable product.
As a bridging tool between chains, cross-chain bridges enable users to transfer assets and information between chains, facilitating communication and compatibility within a multi-chain ecosystem.
According to data from DeFi Llama, as of March 2022, the total cryptocurrency locked in cross-chain bridges reached $21.8B, with Wrapped Bitcoin holding the largest market share at a TVL of $10.2B, followed by Multichain with a TVL of $7B. Arbitrum is the bridge with the highest TVL in the Ethereum ecosystem, accounting for about $6B, followed by Polygon at about $5B.
However, while cross-chain bridges have become a necessity during the proliferation of public chains, they have also become prime targets for hackers. On March 23, Ronin Bridge was hacked, losing 173,600 Ethereum and 25.5M USDC, with a total value exceeding $600M. Ironically, the team discovered this significant loss only six days later. Shortly after, the popular LayerZero project Stargate cross-chain bridge was found to have a major security vulnerability in its underlying protocol while its stablecoin TVL reached $3.6B.
These events raise concerns, and not everyone is optimistic about cross-chain bridges. Vitalik Buterin expressed on Reddit:
The future will be "multi-chain," but not "cross-chain," because the security of bridges crossing multiple "sovereign areas" has fundamental limitations.
How cross-chain bridges will develop in the future and whether there will be a competition between multi-chain vs. multi-bridge is worth further exploration. However, at this stage, the necessity of cross-chain bridges stems from three aspects: improving asset utilization, expanding the boundaries of protocols, and developing new functionalities, unlocking more possibilities for users and developers.
Next, let’s take a closer look at what cross-chain bridges are and how they meet the above three needs.
What is a Cross-Chain Bridge
In most cases, when a user wants to transfer assets from Chain A to Chain B, they first need to deposit the assets into a designated address of the bridge on Chain A. Next, when the bridge's detector receives this information, it will mint an equivalent amount of wrapped assets on Chain B or convert the cross-chain assets into native assets of the target chain by establishing a liquidity pool on the target chain, finally transferring the funds to the user's account on Chain B.
Based on the above description, a cross-chain bridge is a tool that helps users transfer assets between blockchains with different protocols. Current cross-chain technologies involve two different dimensions: asset and data cross-chain, but this article will focus on the explanation of asset cross-chain. Next, let’s understand several important roles and steps in the asset cross-chain process:
Detector: Who detects the status of the source and target chains and is responsible for information transmission? This could be a single validator or a group of validators, or a relayer/light-client, sometimes referred to as an oracle.
Consensus Mechanism: How do validators reach consensus? How do they cryptographically sign the assets that need to be transmitted to the target chain? Is it through multi-signature or a higher security MPC threshold signature mechanism?
Reward and Punishment Mechanism: What is the mechanism that incentivizes validators to transmit information correctly? Some cross-chain bridges reward validators with a portion of transaction fees, or require validators to stake governance tokens, with penalties for transmitting incorrect information.
Are User Assets Custodied by the Bridge? When users deposit assets into the designated address on the source chain, this address may be monitored by the bridge's validators or controlled by a smart contract (thus excluding human intervention). Additionally, cross-chain bridges may also achieve asset cross-chain by deploying liquidity pools on the target chain. When assets are controlled or stored by smart contracts or liquidity pools, this article refers to them as non-custodial assets.
Asset Cross-Chain Models: Since each public chain has its own accounting ledger for native assets, how do users make assets flow across different accounting systems? In an article by 0x76@BlockBeats discussing whether assets truly transfer during the cross-chain process, it points out that what is actually transferred is not the assets themselves, but the value represented by the assets. This article refers to the asset cross-chain model as the "money transfer mechanism."
Classification Methods for Cross-Chain Bridges
Current articles on the market classify cross-chain bridges based on the following methods:
Research partner of @1kxnetwork Dmitriy Berenzon categorizes cross-chain bridges into four types based on their service purposes: those focused on asset cross-chain, those for cross-chain between specific two chains, those focused on application cross-chain, and universal cross-chain bridges.
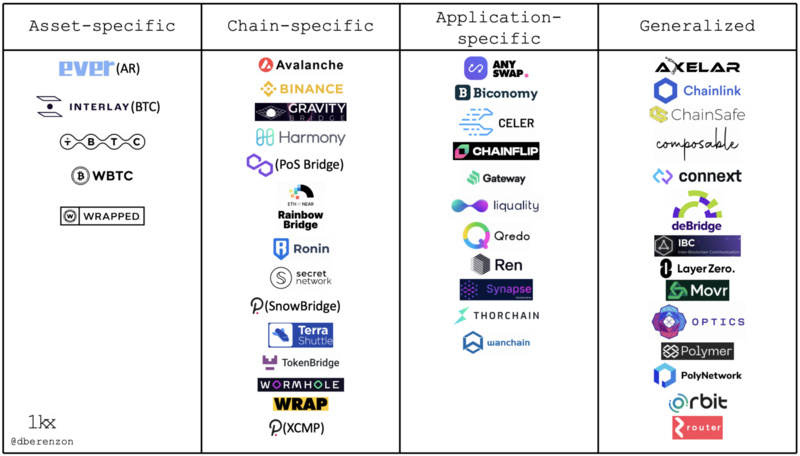
Dmitriy also categorizes based on asset cross-chain verification mechanisms/technologies: single-point multi-point verification, relayer + light-client/native verification, liquidity networks.

Articles on the market have various classifications for the money transfer mechanism; this article selects the explanations of the money transfer mechanism by Arjun Chand and Andre Cronje:
Arjun Chand categorizes money transfers into three types:
Lock + Mint: This type of cross-chain bridge locks assets on the source chain and mints an equivalent amount of assets on the target chain.
Burn + Mint: This type of cross-chain bridge burns assets on the source chain and mints an equivalent amount of assets on the target chain.
Atomic Swap: Achieves asset exchange through self-executing smart contracts, with atomic swaps being the most trustless of the three.
According to Andre Cronje, the money transfer methods are divided into four categories:
Balance Change: After users lock assets in the smart contract on the source chain, oracles notify the cross-chain contract on the target chain, allowing the target chain to transfer assets to the user's receiving address.
Lock + Mint/Burn: When users lock assets in the designated address or smart contract of the cross-chain bridge, the bridge will mint an equivalent amount of assets on the target chain and transfer them to the user's account on the target chain.
Liquidity Swap/Bi-directional Liquidity Pool Model: Utilizing the liquidity pool established by the bridge on the target chain to complete cross-chain transactions, for example, USDC (Ethereum) > anyUSDC swapped for USDC (Fantom).
Pack + Mint/Burn: Utilizing the liquidity pools established by the bridge on both the target and source chains to perform two swaps, completing cross-chain transactions, for example, USDC swapped for anyUSDC (Ethereum) > anyUSDC swapped for USDC (Fantom).
To unify the classification of money transfer mechanisms, this article summarizes the technical documents of cross-chain bridges and divides the money transfer mechanisms into three types: liquidity swap (which requires deploying a liquidity pool), lock + mint/burn (which does not require deploying a liquidity pool), and atomic swap.
- Bridge Security: According to Dmitriy Berenzon's article, "trustless" bridges refer to those whose security is based on the underlying public chain, representing the highest security bridges, such as Arbitrum and BOBA, which are essentially scalability solutions on Ethereum - Optimistic Rollup. "Insured" bridges are the second highest in security, compensating users with the staked funds when validators make mistakes. This mechanism provides users with a better experience compared to "bonded" bridges that only destroy the validators' staked assets without compensation. Finally, "trusted" bridges usually involve centralized verification of transactions and management of user assets.
This article ranks bridge security from high to low: trustless bridges > insured bridges > bonded bridges > trusted bridges.
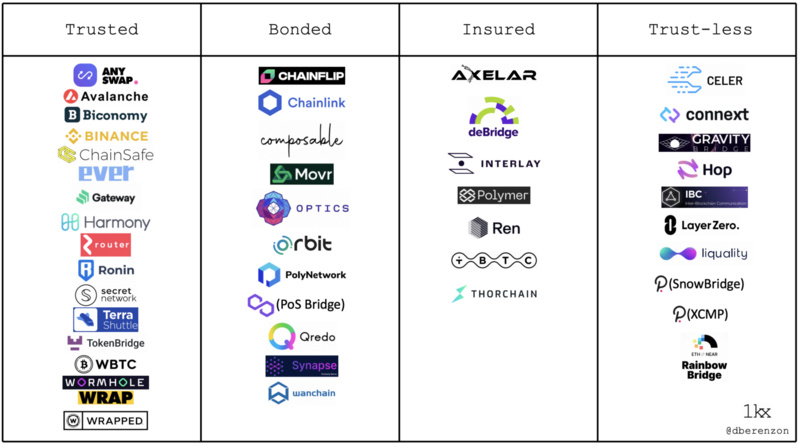
- Others: Regarding other classification methods for bridges, Arjun Chand further subdivides based on the functions of the bridges, but this article will not elaborate further.
Performance of Cross-Chain Bridges
Now that we understand the basic elements of bridges and the classifications based on service purposes, verification methods, money transfer methods, and security, we can see that different cross-chain bridges have different development cores. Dmitriy Berenzon evaluates the performance of cross-chain bridges from the following perspectives:
Security: This article determines that security decreases from relayer, multi-point verification to single-point verification; among multi-point verification, bridges that require validators to stake (PoS) are more secure than those without staking; additionally, when assets are custodied by the bridge, security decreases.
Speed: Refers to the latency of completing transactions and the guarantee of finality. Some bridges focus on cross-chain transactions between specific ecosystems (such as the Hop bridge supporting cross-chain transactions between layer-2), facilitating faster cross-chain transactions.
Scalability: The varying levels of difficulty for developers to integrate additional target chains.
Capital Efficiency: Refers to the capital required to ensure system security and the transaction costs of asset transfers, for example, the upgrade of cBridge 2.0 aimed to lower the threshold for liquidity provision and improve liquidity depth.
Statefulness: The ability to transfer specific assets, more complex states, and/or execute cross-chain contract calls.
2: Review of Cross-Chain Bridges
- Cross-Chain Bridge Product Research
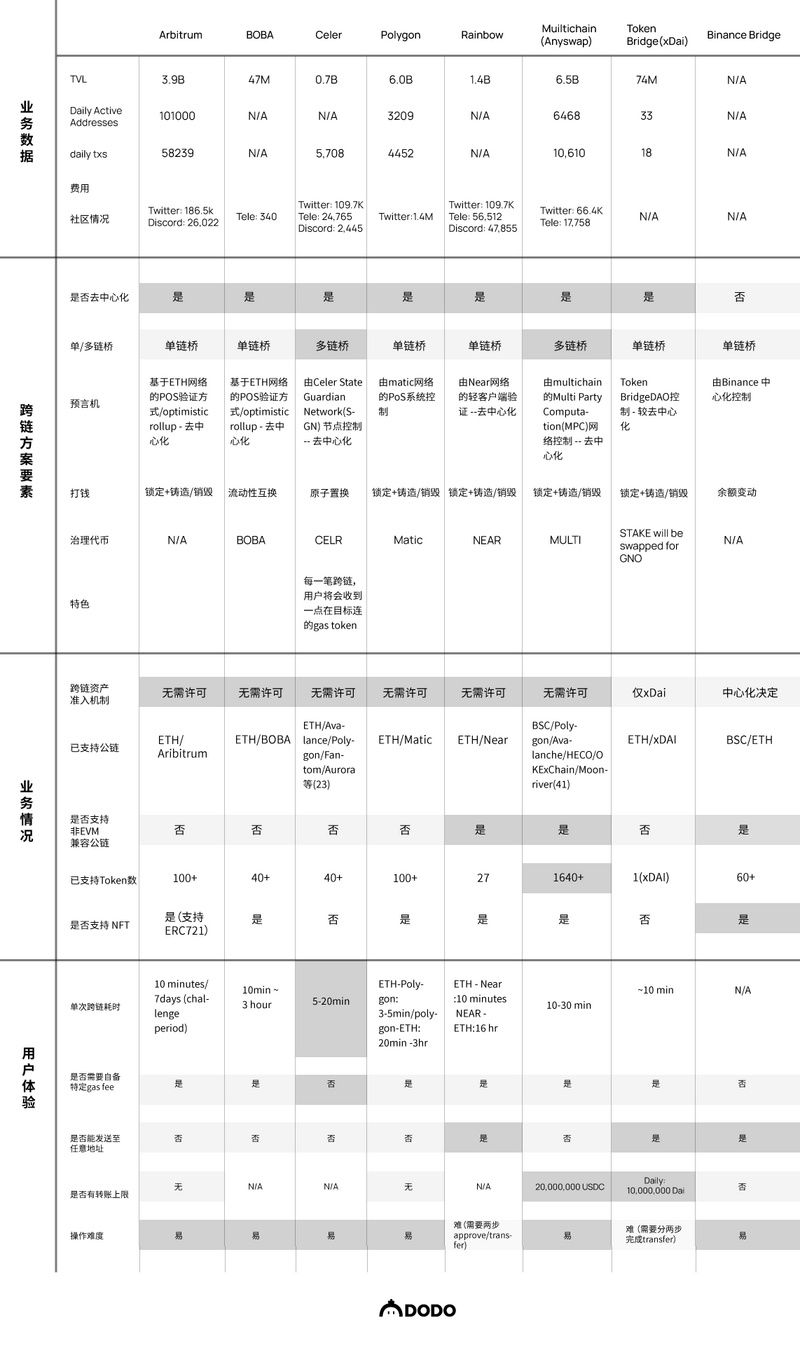
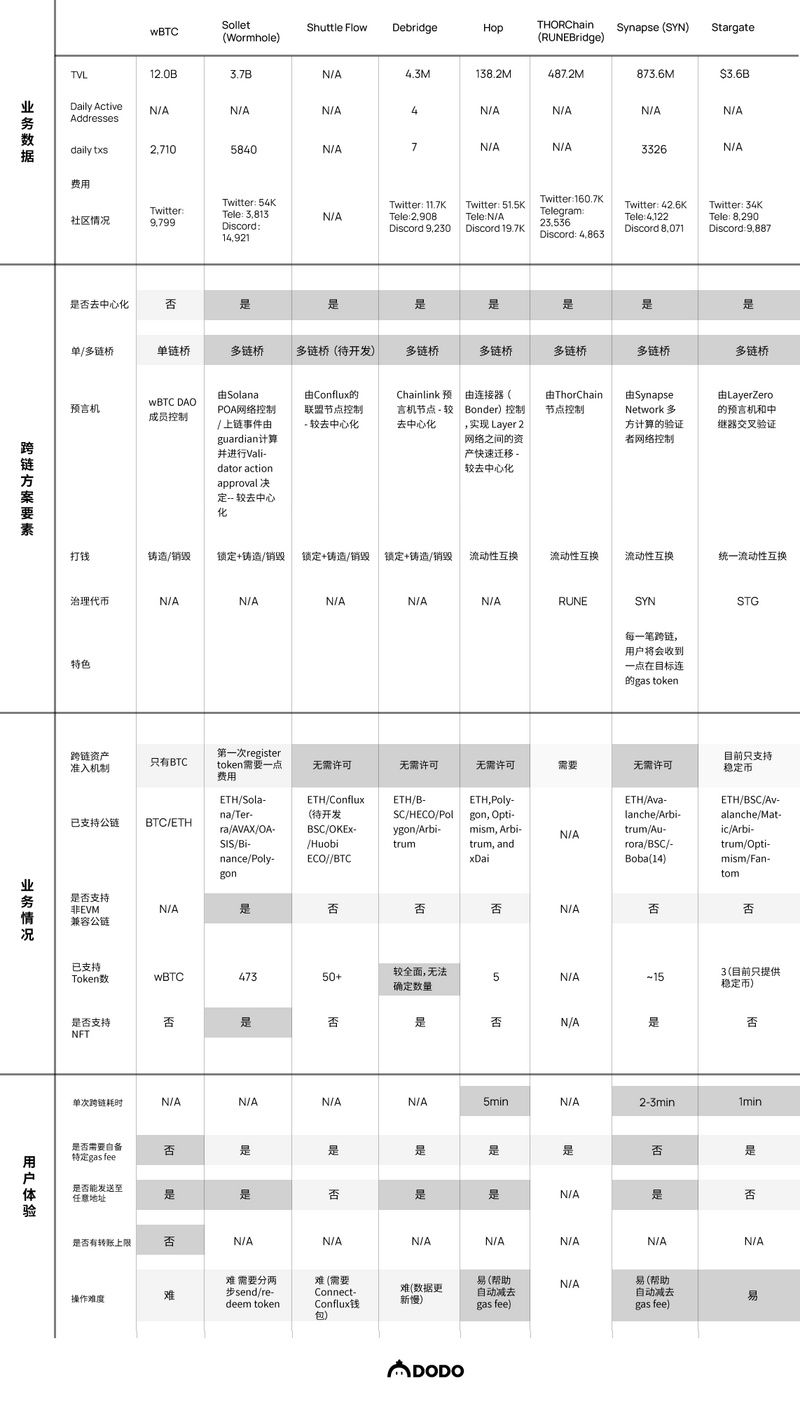
Through research on the official documents of cross-chain bridges, this section will summarize the commonalities of the 16 bridges studied and compare the performance between them. It is important to note that anyone reading the whitepapers and documents of the bridges should do so with a critical mindset; sometimes a newly launched cross-chain bridge project may use more complex language to describe existing technologies and mechanisms to highlight its "features." This section aims to filter out complex language and directly compare the characteristic differences between cross-chain bridges.
Synapse: Currently operates with multi-point verification, where validators running multi-party computation (MPC) achieve consensus through threshold signatures (TSS). Anyone or any project can apply to become a validator in the Synapse community, and the next phase will introduce a PoS staking mechanism to further enhance security. In the money transfer process, the Synapse bridge ensures users receive native assets by deploying liquidity pools on the target chain. Assets are controlled by Synapse's smart contracts, making them non-custodial.
Multichain: Multi-point verification, consensus is guaranteed by multi-party computation (MPC) running threshold signatures (TSS). Currently, there is no staking mechanism; the money transfer mechanism is lock + mint/burn, and assets are non-custodial. Additionally, the Multichain V3 version has introduced a cross-chain method with multi-chain routing, completing asset cross-chain by deploying liquidity pools across multiple chains.
deBridge: Multi-point verification, consensus is achieved through multi-signature (multi-sig), utilizing a staking mechanism to further ensure security; the money transfer mechanism is lock + mint/burn; assets are locked in deBridge's smart contracts, deemed non-custodial.
ShuttleFlow: Multi-point verification by alliance nodes, consensus is achieved through multi-signature; the money transfer mechanism is lock + mint/burn; assets are stored in a receiving address monitored by alliance members - deemed custodial.
Warmhole: Multi-point verification by 19 guardians, consensus is achieved through multi-signature and secured by the reputation of the guardians; the money transfer mechanism is lock + mint/burn; assets are deemed custodial.
cBridge: Multi-point verification (Celer State Guardian Network), consensus is achieved through multi-signature and staking; the money transfer mechanism is atomic swap; based on the atomic swap mechanism, assets are deemed non-custodial.
ThorChain: Multi-point verification, consensus is achieved through multi-signature, validators need to bond a sufficient amount of governance token RUNE to run nodes, and validators are regularly replaced to ensure security; asset transfer is achieved through liquidity pools, using RUNE as an intermediary asset; assets are non-custodial.
Hop: Multi-point verification operated by Bonders, who need to stake assets to participate in validating transactions; the Hop bridge ensures users receive native assets by deploying liquidity pools on the target chain; assets are deemed non-custodial.
Polygon/Matic PoS bridge: Multi-point verification, consensus is achieved through multi-signature, implementing staking to ensure security; the money transfer mechanism is lock + mint/burn; user assets are monitored by Polygon's Predicate Contract - deemed custodial.
Rainbow: Completed by light clients + relayer verification, with security guaranteed; the money transfer mechanism is lock + mint/burn; user assets are stored in the TokenLocker contract, making them non-custodial.
BOBA: As an Optimistic Rollup, transaction verification is executed by smart contracts, and the money transfer method is liquidity swap, with security equivalent to the underlying network - Ethereum; user assets are custodial at addresses monitored by the BOBA network.
Arbitrum: Arbitrum is one of Ethereum's scalability solutions - Optimistic Rollup, with transaction verification executed by smart contracts; its security is equivalent to the underlying network - Ethereum; user assets are custodial at addresses monitored by Arbitrum.
xDai bridge: Controlled by TokenbridgeDAO members, consensus is achieved through multi-signature; the money transfer mechanism is lock + mint/burn; assets are custodial.
Binance bridge: As a centralized exchange, Binance can transfer user assets to different chains through balance changes, requiring users to custody their assets with Binance.
wBTC: wBTC, as a DAO focused on wrapping BTC, centralizes the verification of user information and execution of transactions; the money transfer method is lock + mint/burn; user assets are custodial with wBTC.
Stargate: A cross-chain bridge built on LayerZero, where "validators" are represented by two roles: oracle and relayer. When the information provided by both matches on the target chain, it indicates successful verification/cross-chain; the money transfer method is liquidity swap through a unified liquidity pool; assets are non-custodial.
Performance Comparison of Cross-Chain Bridges
Everyone's interpretation of cross-chain bridge technical documents may vary slightly, so this article's classification of cross-chain bridges differs somewhat from Dmitriy Berenzon's table. However, the logic for determining the verification mechanisms of cross-chain bridges is consistent, and readers can step by step determine the verification mechanisms and security of the bridges based on the following questions:
1) First, is the cross-chain bridge centrally managed, multi-point verification, or does it use relayer + light-client to verify cross-chain information?
2) If it is multi-point verification, do validators need to stake to provide services? Additionally, if a validator acts maliciously, are the staked assets destroyed, or are they compensated to users to protect them from loss?
3) Are the assets deposited by users on the source chain custodied at an address monitored by the cross-chain bridge, or are they stored in a smart contract or liquidity pool?
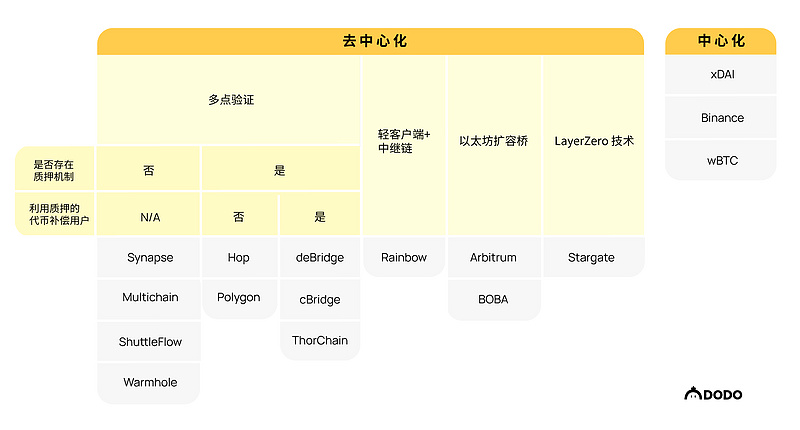
*Based on the above questions and thoughts, this article will now provide performance reviews and comparisons of the 16 cross-chain bridges:
Among these 16 bridges, Synapse, Multichain, deBridge, ShuttleFlow, Warmhole, cBridge, ThorChain, Hop, and Polygon PoS bridge all utilize multi-point verification. It is noteworthy that in the consensus mechanisms of multi-point verification, the difference between multi-party computation (MPC) and multi-signature (multi-sig) lies in the formation of the "private key."
The multi-signature mechanism requires several validators to possess the complete private key to sign transactions, while multi-party computation eliminates the concept of a single private key, requiring validators to jointly form a private key to complete transaction verification. This way, validators do not independently own the complete private key, thus ensuring security. A comparative diagram in Alice Klocko's article visually demonstrates the differences between the two mechanisms.
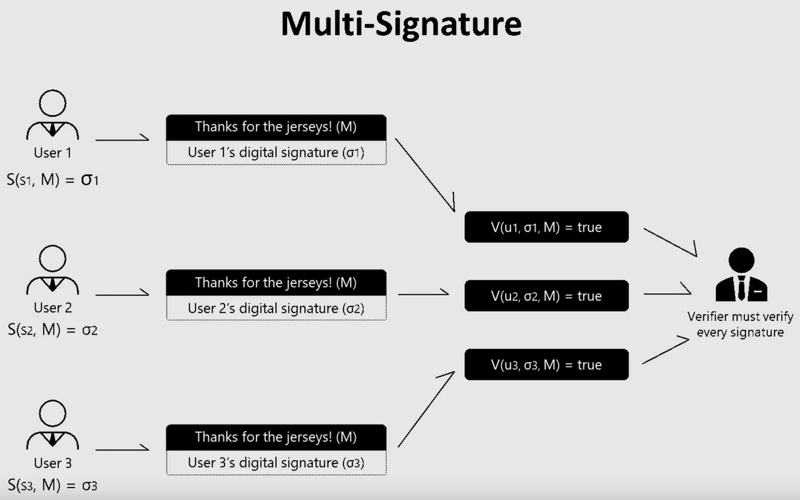
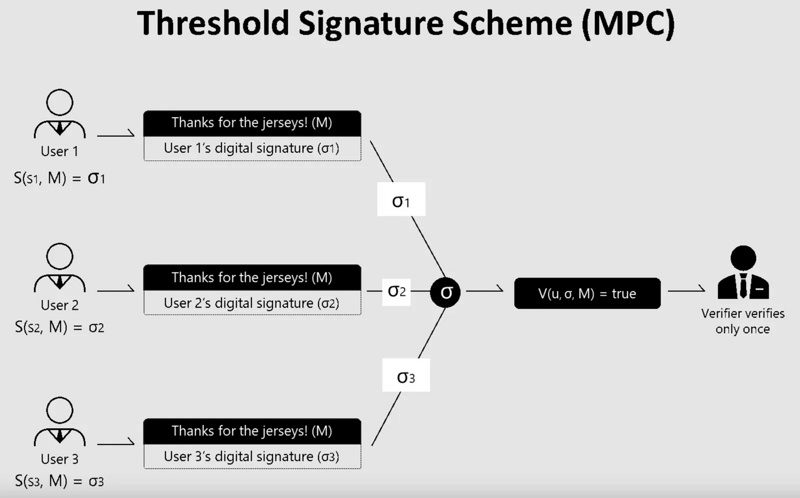
Among these 9 bridges, deBridge, cBridge, ThorChain, Hop, and Polygon require validators to stake to run nodes and provide transaction verification services, which gives them relatively higher security compared to others without staking mechanisms or those relying on validators' "reputation" for guarantees.
To further enhance user experience and ensure user assets are not lost, cBridge, deBridge, and ThorChain are referred to as "insured" bridges. This means that when a node acts maliciously, the staked funds of validators are not destroyed but returned to users as compensation. From the user's perspective, this mechanism provides a more reassuring cross-chain experience compared to bridges where the staked funds are merely destroyed when validators act maliciously.
In contrast to multi-point verification, where users still need to trust validators, the Rainbow bridge employs light clients + relayer chains to achieve decentralization perfectly. However, in achieving decentralization, the Rainbow bridge sacrifices scalability. Due to the high development costs of deploying light clients on each chain, Rainbow currently can only serve asset cross-chain between Ethereum and Near.
BOBA and Arbitrum are relatively special "bridges" because they are both Layer-2 scalability solutions on Ethereum - Optimistic Rollup, so their underlying security is equivalent to Ethereum. While these bridges have higher security, when users want to cross-chain from Layer-2 back to Layer-1, they must undergo a 7-day challenge period.
In contrast, xDAI, Binance, and wBTC differ from the other 13 bridges in their centralization: from transaction verification to custody of user assets. While it is hard to believe that Binance would intentionally act maliciously against its reputation, centralized management somewhat contradicts the pursuit of decentralization in Web 3.
Stargate has become a popular cross-chain project based on the LayerZero protocol since March. To make readers more familiar, in terms of verification methods, Stargate is similar to the Rainbow bridge, completing asset/information cross-chain through deploying light clients and utilizing relayer chains. However, Stargate's innovation lies in introducing two verification entities: oracle and relayer, where consensus between them does not need to be subjectively reached but is objective - when the transaction information provided by both matches, it indicates successful cross-chain.
At the same time, its proposed "super light client" greatly reduces deployment difficulty and costs. Furthermore, 0xivecott explains that Stargate provides users with native assets through deploying a unified liquidity pool, addressing the pain point of users receiving wrapped assets and enhancing capital efficiency.
From the above summary, it can be seen that the advantages and disadvantages of cross-chain bridges cannot be judged from a single perspective. Some bridges focus on security and decentralization, which may relatively lower the requirements for transfer speed and cross-chain scalability, while others prioritize transfer speed and the number of public chains accessed to serve users with small transfer needs.
3: Development of Cross-Chain Bridges
The development of cross-chain bridge projects may revolve around the "impossible triangle of interoperability," or they may optimize based on the five performance aspects mentioned earlier: security, speed, scalability, capital efficiency, and statefulness. However, it should be noted that the development goals of cross-chain bridges are not uniform. For example, Multichain focuses on scalability, currently connecting to as many as 33 public chains, and on this basis, Multichain V3 has optimized the money transfer mechanism by deploying liquidity pools, allowing users to receive native assets on the target chain instead of wrapped assets.
On the other hand, the Hop bridge focuses on asset transfers between Layer 1 and Layer 2, rather than competing with Multichain on scalability. This article believes that each bridge has its own development core, and after establishing development goals, will further optimize aspects such as security, speed, and capital efficiency.
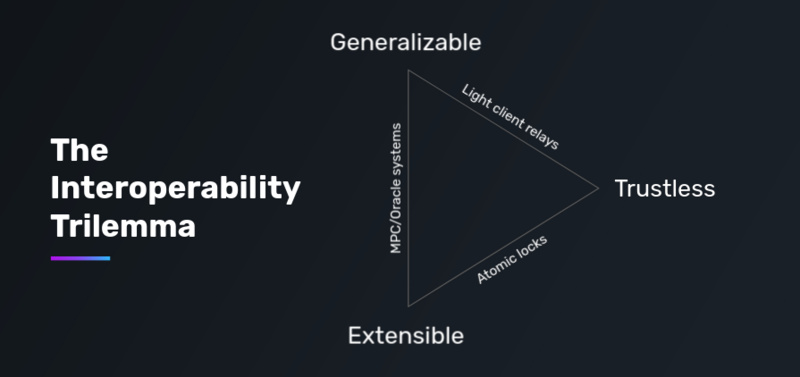
As mentioned at the beginning of the article, Vitalik's concerns about the future of cross-chain bridges stem from security issues when crossing sovereign areas. Indeed, regardless of how bridges make trade-offs in service purposes, security is an important direction that cross-chain bridge R&D teams want to continuously optimize and upgrade.
For example, the Synapse bridge has proposed that as the project enters its second and third phases, it will require validators to stake to enhance security; additionally, cBridge 2.0 processes node information through a decentralized validator network (SGN), improving security compared to the single Gateway role in version 1.0.
Enhancements in security can also be optimized through money transfer mechanisms: Most asset cross-chain models adopt lock + mint/burn, so the assets users receive on the target chain are usually cross-chain assets (wrapped tokens), such as deBridge's deUSDT. Since the issuance of wrapped assets involves three stages, the risk factors are compounded by the native asset, the security of the cross-chain bridge, and the stability of the wrapped asset. In this view, users who receive wrapped assets bear more risks and face lower asset liquidity.
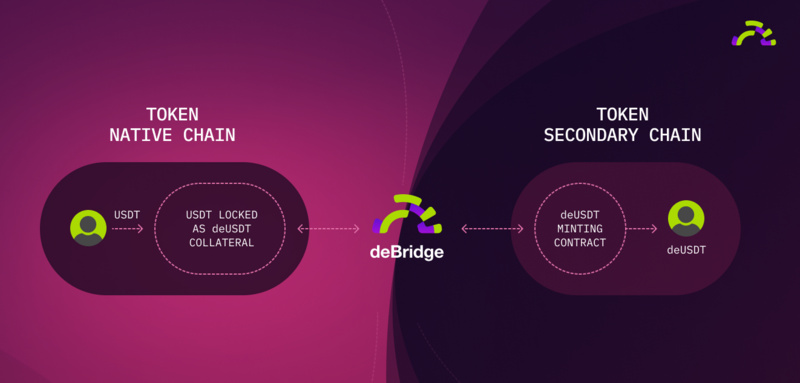
Achieving asset cross-chain through liquidity pools can be understood as adding an extra step compared to the lock + mint/burn model, namely deploying liquidity pools on the target chain to convert the bridge's wrapped assets into native assets of the target chain. This mechanism bypasses the efficiency issues in the locking and minting mechanism, improving cross-chain speed. For example, the Hop bridge helps users convert wrapped assets (Hop ETH) into native assets (L2 ETH) by deploying liquidity pools on Rollup.
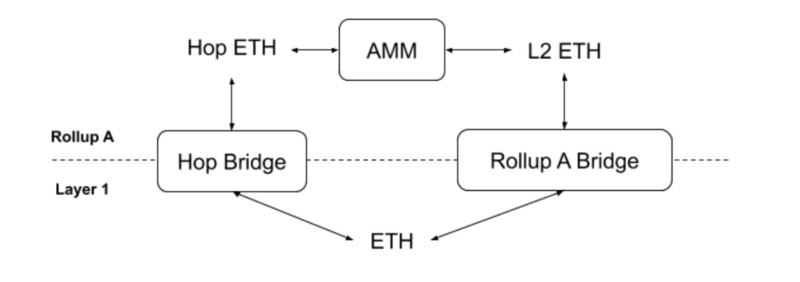
While transferring assets through liquidity may seem convenient, it also presents certain issues. The potential problems with asset transfers through liquidity pools may lie in liquidity depth and the fragmentation of liquidity pools. For instance, in the upgrade of cBridge 2.0, liquidity providers do not need to run nodes themselves but can delegate their funds to the SGN verification network and earn cross-chain transaction fee revenue. This mechanism lowers the threshold for liquidity provision, thereby enhancing capital efficiency.
From the user's perspective, the ultimate optimization of cross-chain bridges hinges on whether they can provide a smooth cross-chain experience, such as whether the cross-chain speed is fast enough, whether there is a transfer limit, whether one-click cross-chain is achievable, whether it helps users reserve/calculate gas fees, and whether the received assets are native assets of the target chain, etc. By reviewing the cross-chain bridge product comparison chart, users can choose the appropriate cross-chain bridge based on their cross-chain needs.
So, what does the future development of cross-chain bridges look like? Rather than getting caught up in remedying the shortcomings of cross-chain bridges, it may be more forward-thinking to consider the user's purpose for asset cross-chain:
Cross-Chain Aggregation: Imagine if you want to transfer assets from Ethereum to Arbitrum. Through the cross-chain bridge product comparison chart, you know that both deBridge and Synapse have connected to Arbitrum, but you cannot determine which cross-chain bridge has lower real-time cross-chain costs and faster speeds. Therefore, cross-chain aggregators may have great prospects - helping users avoid DYOR (Do Your Own Research) and providing services to filter out the optimal cross-chain paths and costs within seconds. Dr. DODO's next article will provide a detailed comparison of cross-chain aggregator products, so stay tuned.
Developers can also consider embedding other financial services into cross-chain bridges, such as what Li.Finance is doing with cross-chain + trading, and the leading DeFi protocol Aave's proposal for cross-chain + lending in its V3 version, or Sushi's proposal to integrate the cross-chain bridge Stargate launched by LayerZero. This way, users can complete DeFi-related activities while cross-chaining without having to switch to third-party platforms.
Additionally, the recently launched anyCall feature by the cross-chain project Multichain also appears quite practical and eye-catching. anyCall is a universal cross-chain messaging transmission protocol that enables sending cross-chain messages from Chain A to Chain B by calling native contracts on the target chain. In practical applications, Curve has seized this opportunity by integrating anyCall to more effectively help veCRV holders on different blockchains allocate CRV reward rights. Specifically, when Curve integrates anyCall, it can promptly calculate the user's reward weight on the target chain and mint the corresponding rewards. This way, there is no need to pre-deploy liquidity pools for CRV rewards, greatly enhancing capital efficiency.
In summary, although Vitalik holds a negative attitude towards cross-chain bridges, we believe that cross-chain bridges will continue to be a focus for users and developers. After all, if closed public chain ecosystems are established due to security issues, they will inevitably lead to contraction. Furthermore, judging by the enthusiasm users have shown for the cross-chain infrastructure project Stargate launched by LayerZero (with a current TVL of $2.5B), cross-chain bridges may evolve towards Layer-0, serving as a robust foundational layer for public chains with strong integrability while providing users with native assets and timely cross-chain transactions through unified liquidity pools.



























