Etherscan: Taking the example of Ukrainian fake airdrop tokens, discussing the implementation methods and prevention measures of deceptive tokens
Source: Etherscan Official Blog
Compiled by: Gu Yu, Chain Catcher
Fake or "spoof" ERC-20 token transfers are not a new phenomenon in Ethereum. However, the widespread adoption of blockchain last year has led to a sharp increase in these cases. This is a common issue, and we provided a brief answer in our newsletter two months ago, but the growing number of cases and a recent high-profile incident warrant a deeper investigation.
In this article, we will cover:
- What is "spoofing"?
- How to detect it?
- How to avoid it?
Imagine hearing rumors of an upcoming token airdrop from a highly publicized DeFi product. You are the perfect trader, and you search the blockchain for any signs of this happening.
Lo and behold, you notice a newly minted token with a name and symbol very similar to that DeFi product. More importantly, you see it being sent to an address you privately marked as belonging to a well-connected whale/influencer.
Then that address transfers it. "This must be it!" you think, wanting to get in on this token before anyone else. You buy a large amount of tokens from the freshly created Uniswap V2 liquidity pool. An hour later, the LP runs out of ETH, and you realize you've been played.
Where did it go wrong?

These tokens were not actually sent from the Ukrainian Crypto Donation address.

These OpenSea tokens were also not transferred from the OpenSea: Registry address.
The mistake you made was assuming that the token transfer involving your trusted influencer was actually initiated by that address. This "spoofing" deceives unsuspecting users by leveraging the following advantages:
- ERC-20 standard design
- Transparent data display by block explorers
The ERC-20 standard allows tokens to have a transferFrom function, which enables the transfer of tokens from an address different from the one initiating the transaction.
For ERC-20 token transfers, block explorers like Etherscan display the address transferring the tokens, not the address of the initiator. Due to the nature of block explorers, the data is not scrutinized by default.
In most cases, the damage is limited to tokens of zero value. However, there can be more dangerous scenarios, such as tokens with misleading error messages that point to phishing sites to steal user private keys. ERC-721 and ERC-1155 tokens (NFTs) can also encounter the same issues.
How can this be detected?
The answer is quite simple. For any of these token transfers, click on the exact transaction hash and check its details. The From address initiating the transaction is clearly different from the From address of the token transfer.
To dig deeper, look for the spoofed From address in the transaction input data or contract source code. It is usually included in either location.
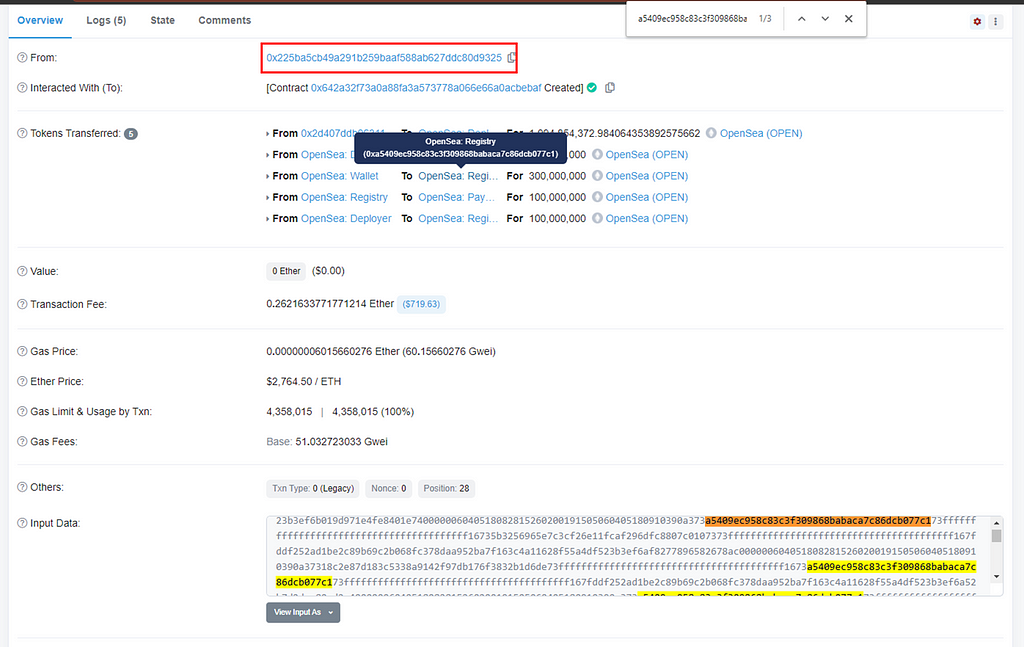 The forged OpenSea token appears to have been transferred by OpenSea: Registry in this transaction.
The forged OpenSea token appears to have been transferred by OpenSea: Registry in this transaction.
A key warning: Not all token transfers initiated by different addresses are necessarily fake or spoofed. A common example is dApps that batch send multiple token transfers. These usually have a public name label added by the Etherscan team—if there are any unlabelled, please let us know!
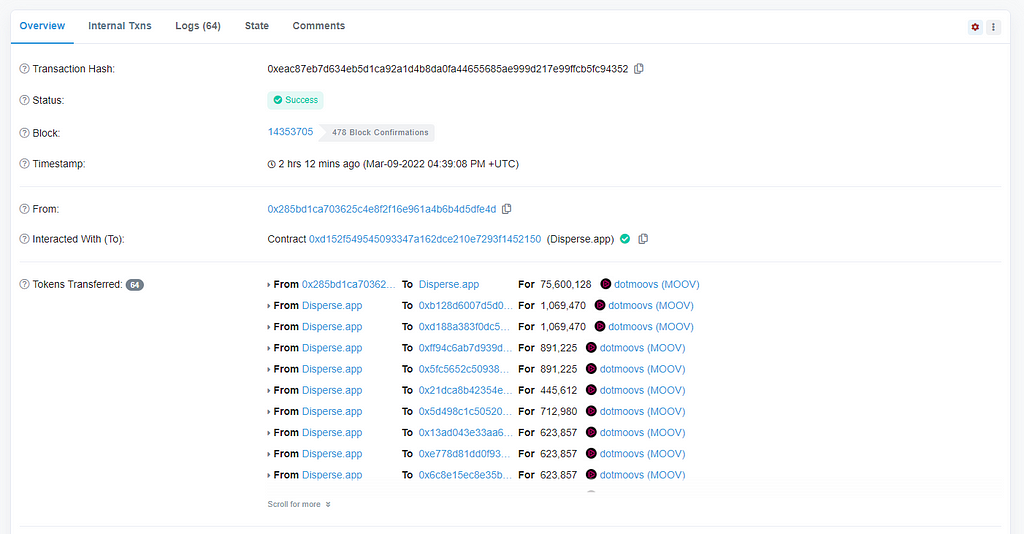 Transaction of batch sending tokens
Transaction of batch sending tokens
A close relative of spoofed tokens is spam tokens. While these do not pretend to be sent from an influencer's address, they are sent in large quantities to that address, making reading the token labels of the address a miserable experience.
 Filtering Pranksy token transfers is not fun… many of those tokens are clearly fake too!
Filtering Pranksy token transfers is not fun… many of those tokens are clearly fake too!
What can be done to avoid this?
For the average user, there is no need to do anything, as this issue is unlikely to affect you significantly. For the gamblers, it is wise to stop and ask yourself if something seems too good to be true. Then check the transaction details page.
By default, Etherscan does not scrutinize the data, but we are exploring ways to help mitigate this issue. The first step is to expand the functionality of our Token Ignore List. Current features include:
- Automatically hiding token transfers in the ERC-20, ERC-721, and ERC-1155 tabs, and hiding them in address balances and token holdings.
- Including a simple option for users to ignore all tokens marked as suspicious or worse by the Etherscan team.
We hope this expanded functionality helps protect users from spoofing while providing a cleaner user experience on the site.











