Popular Science: What is Zero-Knowledge Proof and what are its use cases?
Author: Captain Hiro, Babit
Perhaps you have heard of ZK Proof or zero-knowledge proofs. But you seem to have never quite understood what it is? What are ZK-rollups? What are ZK-SNARKs? In this article, all your questions about zero-knowledge proofs will be answered, so buckle up, and let’s start our journey to learn about zero-knowledge proofs together!

What is a Zero-Knowledge Proof?
A zero-knowledge proof is a method of proving that allows one party (the prover) to prove to another party (the verifier) that they know a secret or that a statement is true, without revealing any actual information.
The term "zero-knowledge" itself is a proof of the fact that no information is disclosed, yet the second party (the verifier) has every reason to believe that the first party (the prover) knows the secret or that their statement is true.
So, why do we need zero-knowledge proofs? When we do not trust others to disclose information but want to convince them that we know the secret or that our statement is true.
There are two types of zero-knowledge proofs:
- Interactive
- Non-interactive
1️. Let’s first look at an example of an interactive zero-knowledge proof
Suppose you need to prove in zero-knowledge that you are an adult, but you cannot actually disclose your specific age. We need a third-party authority to verify your age, and their trick is as follows:
"Thank you for providing a copy of your birth certificate; we already know you are 21 years old. Here is a secret number, please store it secretly and keep it safe. You may need it later."
"Your secret number will be hashed 22 times to create a final age hash code (yes, the system's default operation is to hash your age +1 to make it work). Therefore, there are 22 hash steps between the secret number we give you and this final age hash code."
"We will package this using your name, a timestamp, and this final age hash code. This is the proof you will provide to others."
Now, whenever you want to prove to someone that you are over 18 years old, you must effectively demonstrate that there are more than 18 hash steps from your secret number to your final age hash code.
To do this, you only need to show them the last 18 hash steps; you need to first perform the first 4 hash steps yourself (hashing your secret number 4 times) and then give them the result; that is, the result of the fourth hash.
Then they will perform 18 more hashes on the result you provided (because the authority has now hashed your secret number a total of 22 times), and they will ultimately get the final age hash code and can verify whether you are an adult, as this information is all contained in your proof package.
In fact, the verifier will say: "Give us a value, and we can hash it 18 times to get a value that matches your final age hash code. If you are not 18 years old, then your final age hash code will not have 18 hash steps, and we cannot properly authenticate your true age."
Isn’t this a nice example?
A good example of a zero-knowledge proof - MathOverflow
However, this interactive method also has some limitations:
- Every time they perform verification, the entire lengthy process is required. And this process is actually quite simple hashing; imagine what it would be like to perform actual cryptographic algorithm calculations?
- Additionally, both parties need to meet at the same time and place (network platform), whether online or offline.
2️. Let’s look at non-interactive proofs
In 1986, Fiat and Shamir invented the Fiat-Shamir heuristic (non-interactive zero-knowledge proof), thus becoming the first digital signature algorithm based on interactive zero-knowledge proofs.
The Fiat-Shamir heuristic can be transformed into a non-interactive zero-knowledge proof through a commitment scheme, thus producing ZK-SNARKs or zero-knowledge succinct non-interactive arguments of knowledge.
To make the Fiat-Shamir heuristic more powerful, we use a commitment scheme. A commitment scheme is a fundamental component of many cryptographic protocols. It allows the committer to publish a value (called a commitment) and bind that value to a message (binding) without revealing it (hiding).
The two most prominent commitment schemes currently used for zero-knowledge proofs are Pedersen commitment and polynomial commitment.
However, it wasn't until around 2013 that ZK-SNARKs became practically effective, allowing developers to implement and use them in real-world applications.
I recommend reading this excellent article by Vitalik Buterin, which provides an overview of why ZK-SNARKs are usable and explains how they are implemented. It may not be possible to grasp everything at once, but read it several times, and once you understand the content, you will grasp the principles behind it.
In a post-quantum world, we need to ensure that the cryptographic functions we choose for ZK-SNARKs cannot be forcibly broken by quantum computers. That’s why improvements are underway to achieve post-quantum security. If you want to learn more about this, you can watch this ACM lecture:
Improved Non-Interactive Zero-Knowledge and Applications of Post-Quantum Signatures
Now that we know what zero-knowledge proofs are, what are they used for?
Conceptually, they have two main use cases:
- Scaling blockchain transaction capacity
- Privacy—such as protecting personal data security in fields like healthcare
Scaling Blockchains—ZK Rollups
A rollup is a blockchain scaling solution that works by executing transactions outside the first layer network while publishing transaction data on the first layer. This allows rollups to scale the network while still gaining security from Ethereum consensus.
By moving computation off-chain, more transactions can be processed because only a portion of the rollup's transaction data needs to be included in Ethereum blocks.
To achieve this, rollup transactions are executed on a separate chain and can even run a specific version of the Ethereum Virtual Machine (EVM) for the rollup.
The next step after executing transactions on the rollup is to batch them and publish them to the Ethereum main chain.
The entire process essentially involves executing transactions, obtaining data, compressing data, and rolling it up to the main chain in a single batch, hence the term "rollup."
How does Ethereum know that the published data is valid and not submitted by malicious actors trying to profit themselves?
Each rollup deploys a set of smart contracts on the first layer that are responsible for handling deposits and withdrawals and verifying proofs.
Proofs are also the main distinction between different types of rollups.
Optimistic rollups use fraud proofs, whereas ZK rollups use validity proofs.
In ZK rollups, each batch of files published to the first layer includes a cryptographic proof called a ZK-SNARK. When the transaction batch is submitted, the proof can be quickly verified by the first layer contracts, and invalid batches can be directly rejected.
There is much more to learn about zero-knowledge proofs and optimistic rollups, such as their implementation methods and limitations. This article only covers some basic concepts, and you will need to learn more related content.
Many projects are developing ZK rollup-based scaling solutions for Ethereum. Some notable projects include dYdX, Loopring, Polygon Miden, and Polygon Hermez.
Privacy—Applications in Daily Life
Suppose two companies, A and B, want to use blockchain as a medium to operate and communicate.
A transfers assets to B, and they want to keep these assets internal. Yes, blockchain brings transparency, interoperability, data security, integrity, and other benefits, but why would a company publicly share their internal logistics information? This is where zero-knowledge proofs come into play.
For example, you want to privately transfer some money to your overseas friend but do not want the government to monitor the transaction. What would you do? Zero-knowledge proofs can help.
In several other fields, zero-knowledge proofs can also have a profound impact, such as in healthcare, insurance, electronic voting, and identity management.
For instance, in healthcare, ensuring the security of DNA data, personal information, medical records, basic medical history information, drug traceability, clinical trials, healthcare supply chains, and organ transplants.
In insurance, ensuring digital forms of insurance certificates and policies, personal information, vehicle information, and settlement claims.
Using blockchain and ZKP for identity management has far-reaching implications. Every application related to KYC (Know Your Customer), schools, universities, and payment applications requires providing our ID images, such as driver's licenses, passports, voter IDs, and national IDs. Our sensitive personal data is actually out there, and we may not even realize that the information could be at risk of leaking at any time. With zero-knowledge proofs, we can protect all this identity information, revealing only the necessary information to vendors, applications, and the government. In fact, we can completely transform the way this identity information is disclosed using zero-knowledge proofs.
We can apply zero-knowledge proofs to all of this, so whenever certain information is needed, users can selectively approve and provide the required information while the rest of the details remain hidden.
It is only after 2013 that the efficiency of ZK-SNARKs became sufficient for practical implementation and use by developers, which is why there is significant room for different applications using zero-knowledge proofs to emerge in the future.
Launched in 2016, Zcash is currently the only prominent product that has successfully implemented ZK-SNARKs and provides privacy transactions between users.
ZK-SNARKs vs. ZK-STARKs
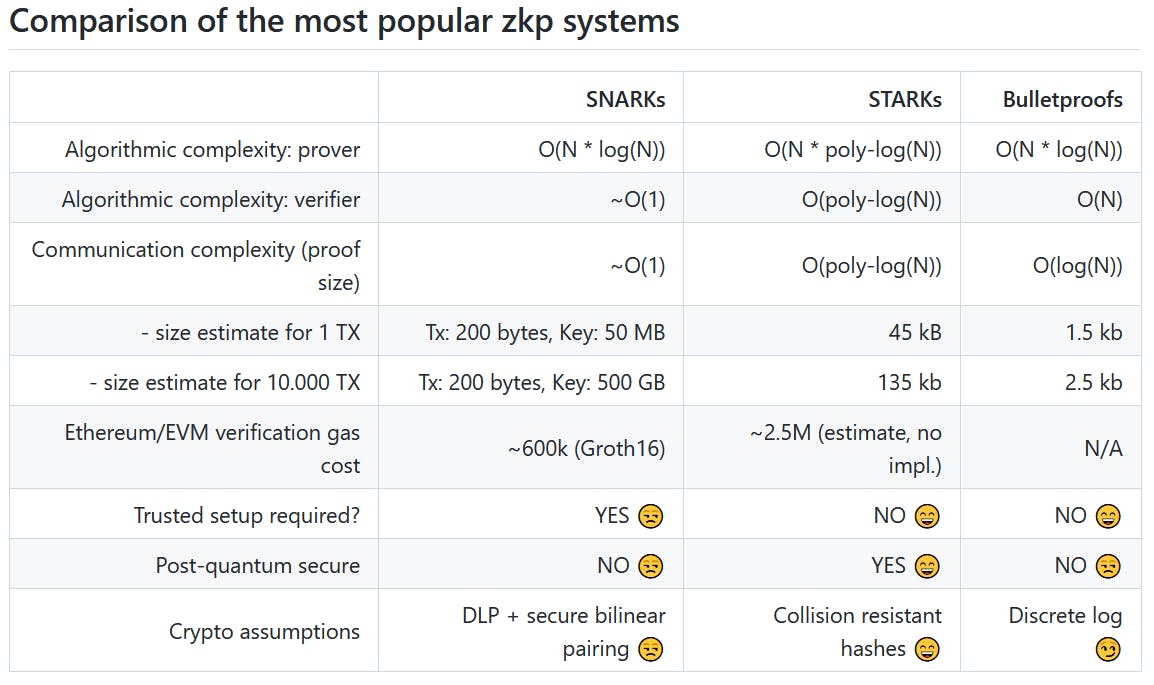
Image Source: Matter Labs GitHub Repository
ZK-STARK stands for zero-knowledge Scalable Transparent Argument of Knowledge, while ZK-SNARK stands for zero-knowledge Succinct Non-Interactive Argument of Knowledge.
Both of these zero-knowledge technologies are essentially non-interactive, which means the code can be deployed and act autonomously.
ZK-SNARKs rely on the security of elliptic curves. The fundamental assumption of elliptic curves in cryptography is that finding a random elliptic curve element's discrete logarithm relative to a known base point is infeasible.
Trusted setup refers to the initial creation event of the keys required to create proofs for private transactions and the verification of those proofs.
If the secrets used to create these keys during the trusted setup event are not destroyed, then these secrets could be used to forge transactions through false verification.
Another limitation of SNARKs, as we already know, is their feasibility in a post-quantum world.
On the other hand, starting to use STARKs in a network does not require a trusted setup. These are also referred to as quantum-resistant. However, the proof size of STARKs is significantly larger than that of SNARKs.
However, STARKs are still in their infancy, and currently, there is not much support for developers, so we have a few more years before we see products based on ZK-STARK.
This concludes the article. This is a preliminary introduction to what zero-knowledge proofs are doing in the web3 world, and I believe you now have a certain understanding of zero-knowledge proofs.
































